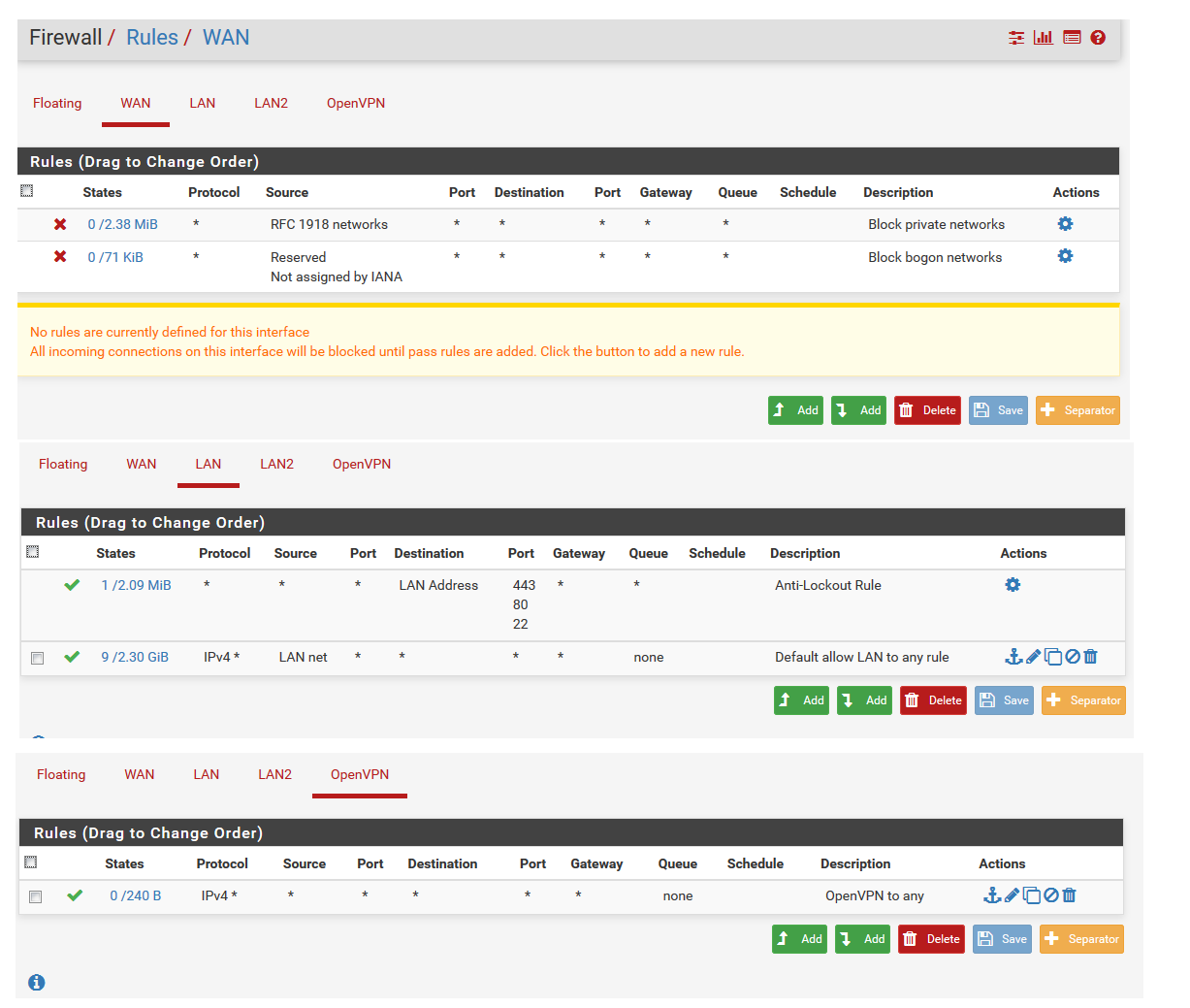
Site2Site-OpenVPN Tunnel routing wont work on one of two tunnels
-
I created the Tunnel following this guide.
https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/configuring-a-site-to-site-static-key-openvpn-instance.html
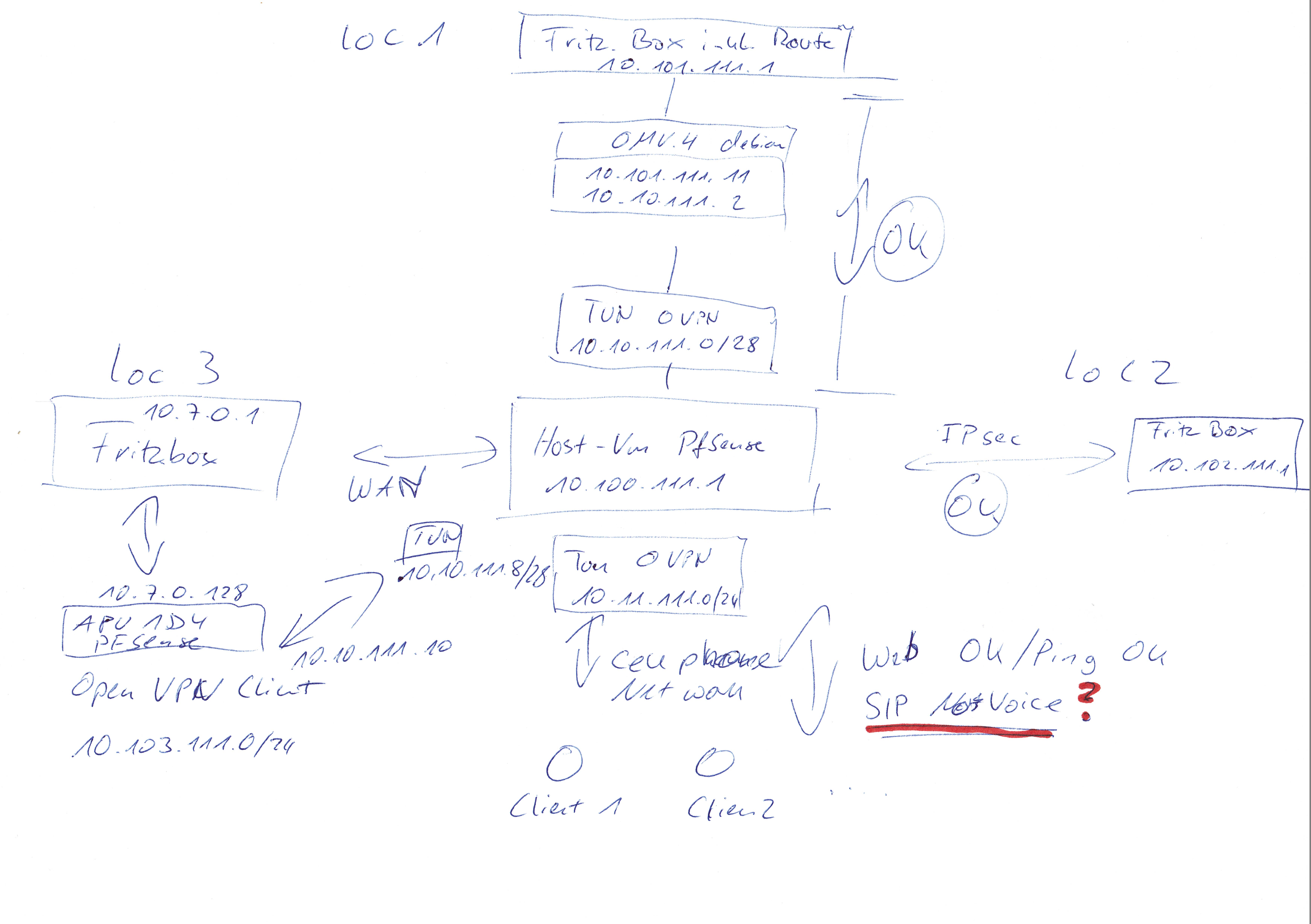
We have several sites and a host.
With some sites, we have to use IPsec, as the remote hardware (fritz.box) only does IP sec and is very slow at it. So I changed one location from IPsec in Fritzbox to oVPN in OMV4. Works like a charm.
BUT:
I copied this to an other location, no luck. routing just wont work.
From Host, i can ping VPN IP on client, but not network behind it
From client remote network, i can ping VPN IP on client, but not network on hostHere is the network grid as pictrure and as a description:
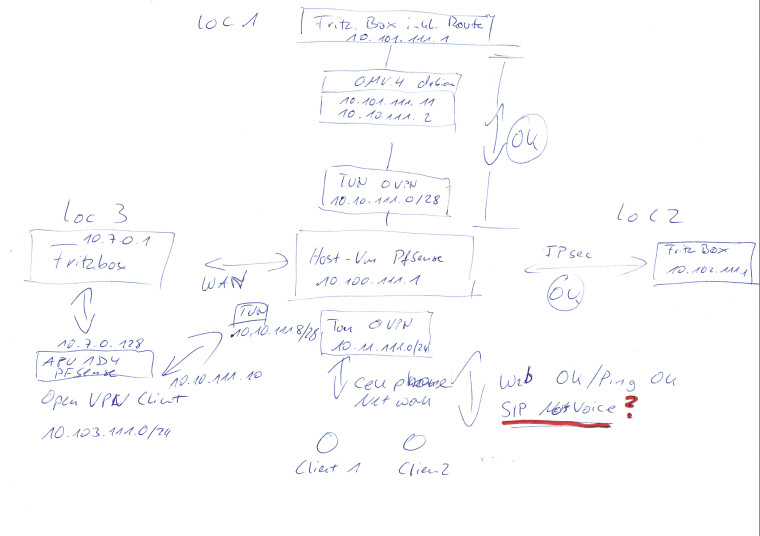
The host (a hetzner machine) does run a VM with pfSense.
host with the network 10.100.111.0/24 with pfSense being 10.100.111.1
loc1 (changed sucessfully from IPsec to oVPN) with the network 10.101.111.0/24 with the oVPN client being 10.101.111.11 (OMV4 debian server and static routs from Fritz.Box to .11 for the host network, not the tunnel) Tunnel is 10.10.111.0/28 while host is .1 and OMV client is .2 (works greate)
loc2 with the network 10.102.111.0/24 with IPsec to Fritz.Box (.1) (works greate while beeing slow, but ok for current use)
loc3 with the network 10.7.0.0/24 with IPsec to Fritz.Box (.1) is the one I want to change from FB(IPsec) to APU(pfSense oVPN)
For this I have a test hardware: pcengine.ch APU1D4 (i know, no crypto, but still 40% more power than the Fritbox) this is also a pfSense OS. I configured the FritzBox to have the APU1D3 (the one and onyl client on 10.7.0.0 net) as an exposed client, full port forward, no joy.
I want to have 10.103.111.0/24 as local net. every single hardware behind the APU. I have no inter site traffic, only site2host.
No matter what I try on the host or the remote system, i cant get through. It is a exact copy of the loc1 settings, only IP chagned to other tunnel and local net. routing just wonk work.
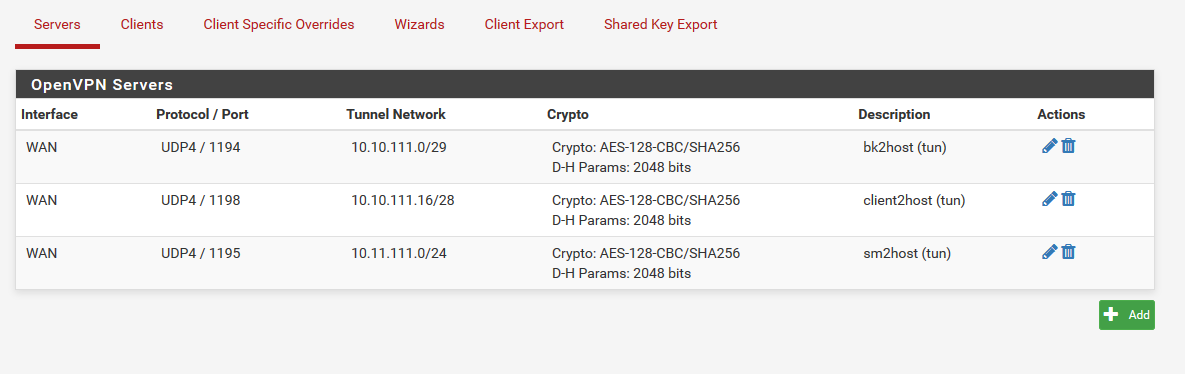
I even set 3 servers, to make sure the stuff wont get mixed up in the host. no joy.
I dont know what els I shold try.
I apriciate any advice.
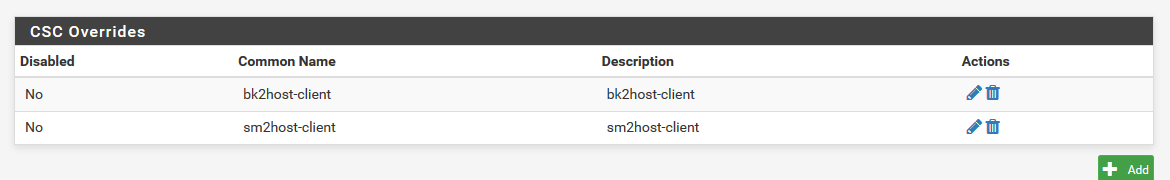
Pictures from server Settings:
3 servers, becaus the roadwarrios and the 2nd site the routing just wont work,
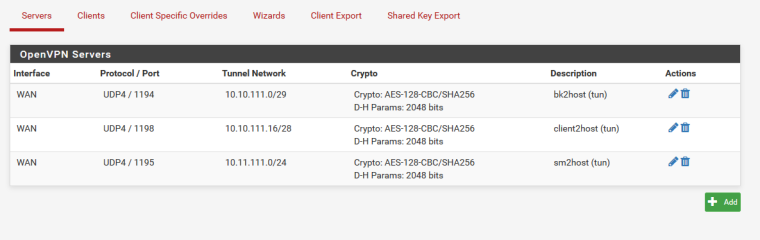
This is all client override for remote networks site2site (site1 and site 2)
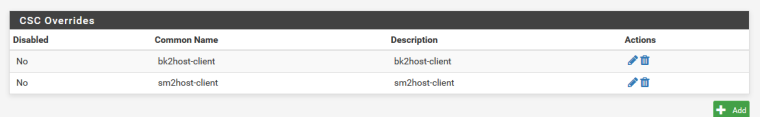
This is client override setting for remote network on site2site
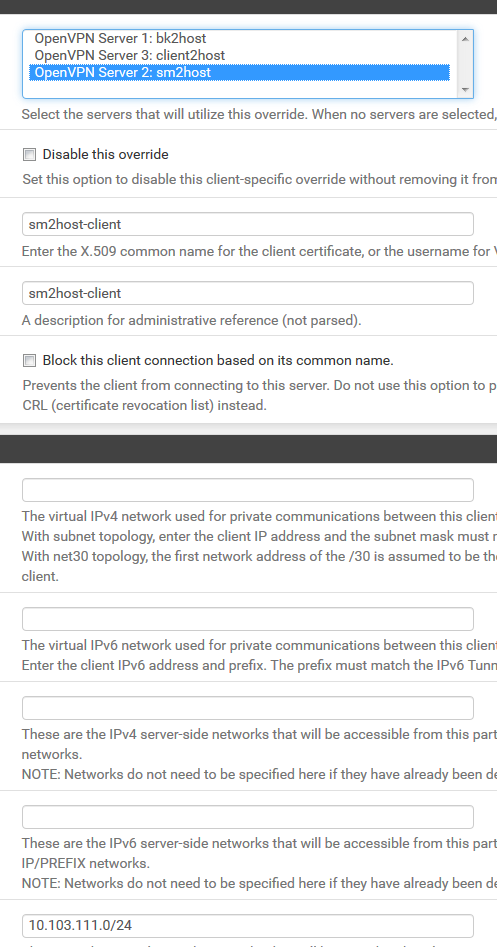
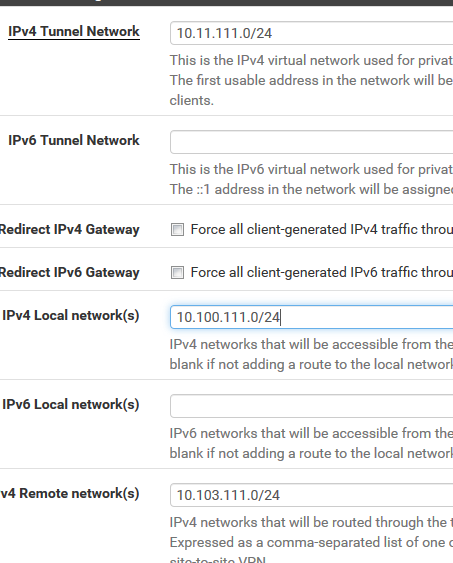
This is server3 setting for IP ragens
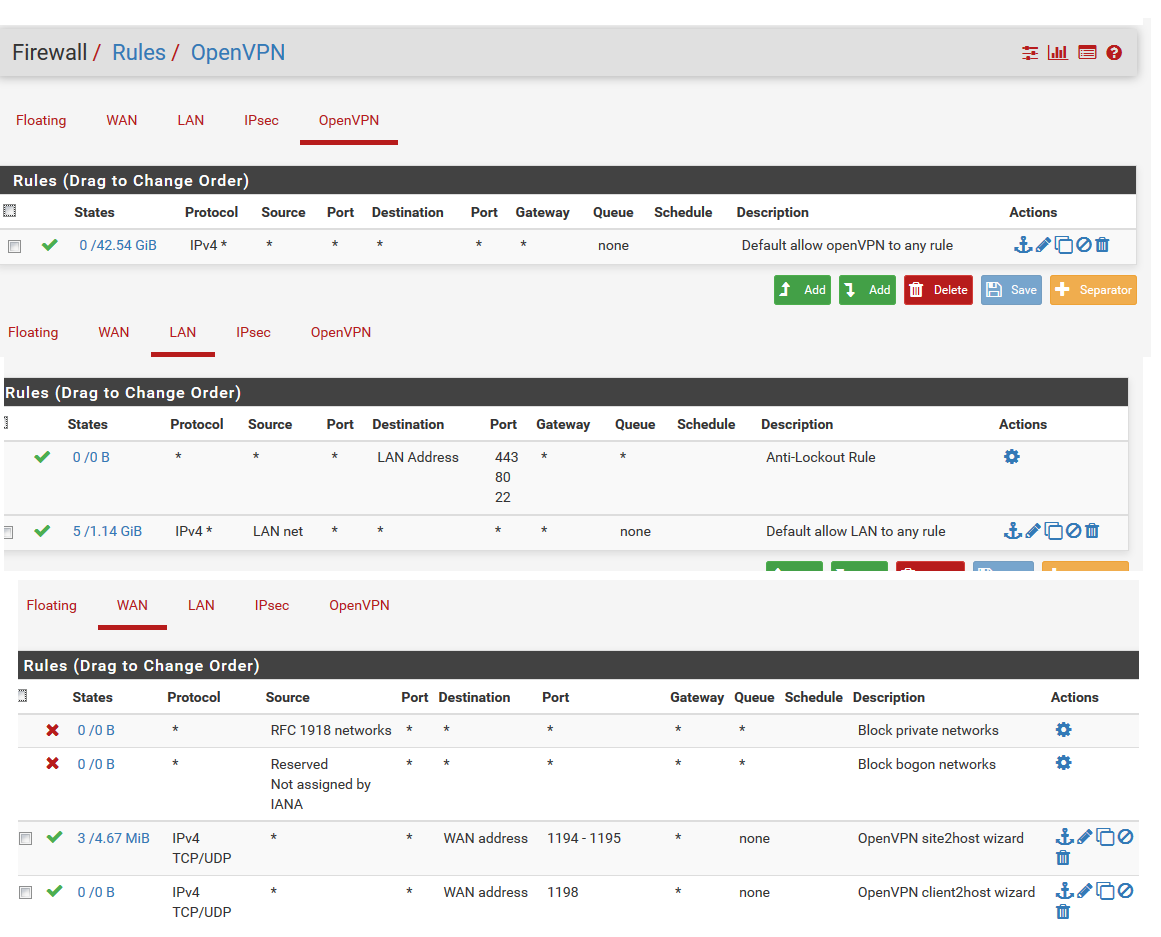
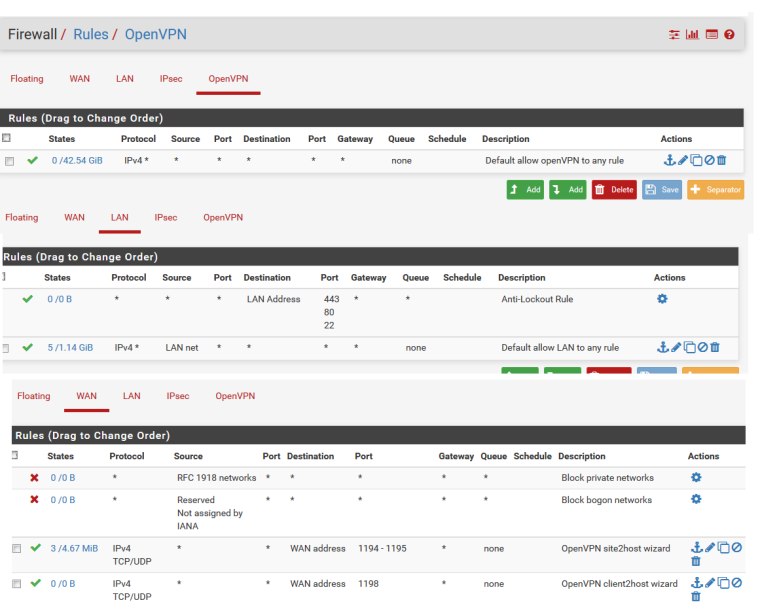
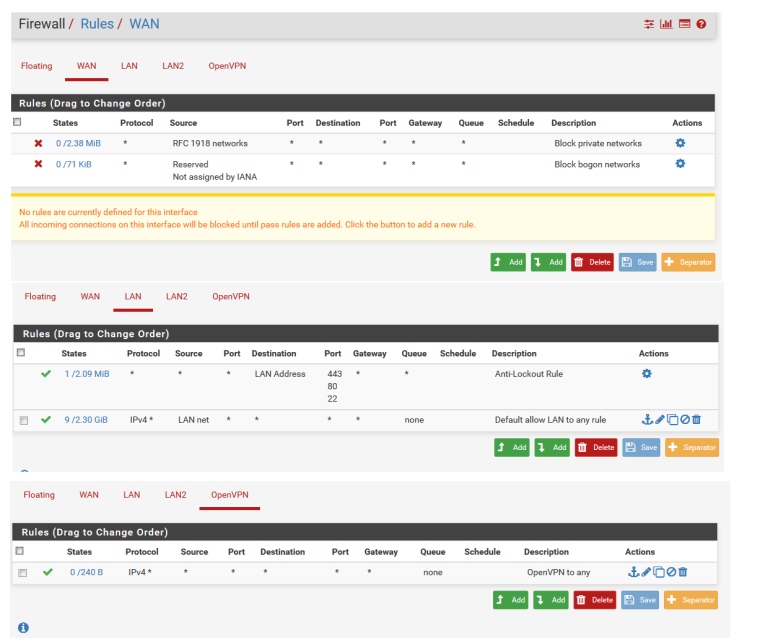
and Firewall rules
client site: (follows, need to change the computer :-))
VPN clint

tunnel is up and running (host network can ping ip of tunnel client (10.11.111.2), but not remote network.
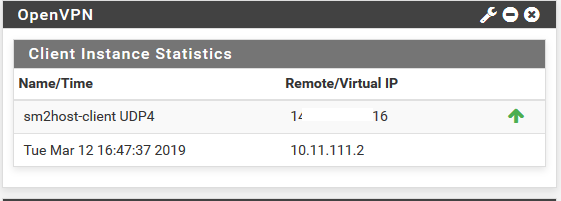 ^
^firewall settings on client
-
Post the server1.conf from the server and client1.conf from the client.
-
cleand server.conf pls pn me if I missed something.
openvpn-config-fw.intern-20190318083528.xmland the client conf
openvpn-config-pfSenseSM.fw.sm-20190318085809.xml -
@mannebk my apologies, please post the .conf files located here -> /var/etc/openvpn. You can get to it via the shell or Diagnostics -> Edit File in the GUI. The server-side will have a serverX.conf and the client-side will have a clientX.conf file. If it's the first server or client that was configured on the box, they should be server1.conf and client1.conf.
The .conf files are much easier to read than .xml (for me at least).
-
server2.conf
dev ovpns2 verb 1 dev-type tun dev-node /dev/tun2 writepid /var/run/openvpn_server2.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-128-CBC auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local ip-deleted tls-server server 10.11.111.0 255.255.255.0 client-config-dir /var/etc/openvpn-csc/server2 ifconfig 10.11.111.1 10.11.111.2 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'bk2host-server' 1" lport 1195 management /var/etc/openvpn/server2.sock unix max-clients 4 push "route 10.100.111.0 255.255.255.0" push "route 10.101.111.0 255.255.255.0" push "route 10.102.111.0 255.255.255.0" route 10.103.111.0 255.255.255.0 ca /var/etc/openvpn/server2.ca cert /var/etc/openvpn/server2.cert key /var/etc/openvpn/server2.key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server2.tls-auth 0 ncp-ciphers AES-128-GCM compress persist-remote-ip float topology subnet sndbuf 1048576 rcvbuf 1048576 -
client1.conf
dev ovpnc1 verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_client1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-128-CBC auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local 10.7.0.104 tls-client client lport 0 management /var/etc/openvpn/client1.sock unix remote deleted 1195 ca /var/etc/openvpn/client1.ca cert /var/etc/openvpn/client1.cert key /var/etc/openvpn/client1.key tls-auth /var/etc/openvpn/client1.tls-auth 1 ncp-disable compress resolv-retry infinite -
On the server-side (if that's the right config), looks like it's set up as a remote access server, which isn't what you want. You need to change the server mode to one of the Peer to Peer options and configure the server for either a shared key or PKI setup.
On the client-side, the client is not routing any networks over the tunnel.
So, there appear to be several issues:
- The server-side needs to be reconfigured for Peer to Peer mode
- The client-side is not routing any networks over the tunnel.
a. If the objective was shared key, here's one of your issues
b. If the objective was PKI, the server-side will need iroute statements for the client's network(s) in the CSO section - The client override screenshot posted in your OP is missing an entry in the "IPv4 Remote Network/s", which will autogenerate the iroute statements needed for the server to reach the client's network behind this connection. Assuming you went with a PKI setup.
- This is unlikely, but the client-side is double NAT'd behind an edge device, so if basic end-to-end IP communication still isn't working after making your corrections, it's possible that the client may need a static route on the edge device for the tunnel network.