Rules not working as desired on WAN interface
-
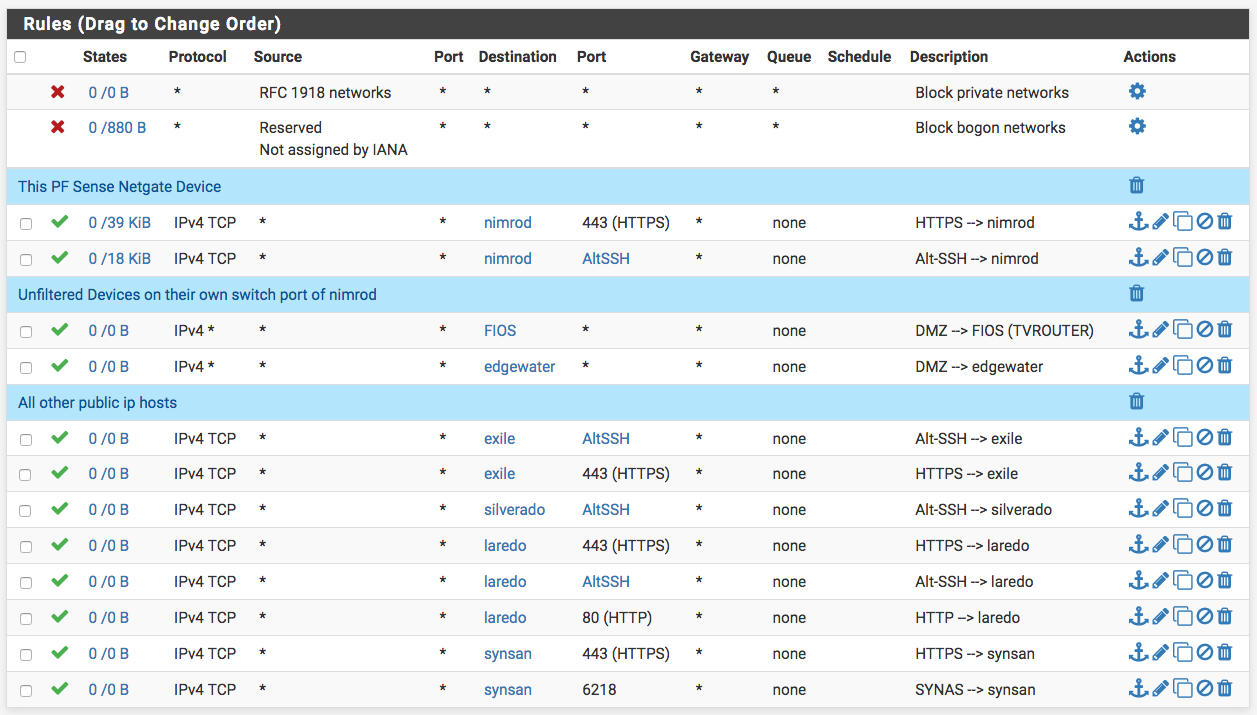
Greetings. The following is a shot of my WAN rules. Every host shown is a physical machine with a public IP in the same subnet as the firewall itself. You can see I am allowing certain traffic to certain machines, i.e. https and ssh on an alternate port (AltSSH) etc...
My issue is that the hosts here in each case are able to get traffic from the internet from any port. For example "laredo" should only ever get 443, 80 and AltSSH but it will see any traffic I sent it from the internet like 22,23, etc... The host will block it but the firewall will not.
"synsan" should see nothing but traffic on port 6218 but instead will answer on numerous other ports.
It seems to me the only IP the firewall is filtering now is its own.
What have I missed? I had an effectively identical setup on different hardware in the past (Soekris) that worked as desired. I am now using a Netgate XG-7100.
Any input is greatly appreciated.
Cheers, Mike.
-
Firewall rules control traffic at the point that it enters the firewall, not exits. If you want rules to control your LAN clients, you must put your rules on the LAN tab.
-
@KOM Yes, understood. These are on the WAN where I want them. These are public facing servers with specific services running that I want on the WAN side. I just want them filtered. I do also have a LAN that works as expected but this is my WAN side.
Cheers, Mike.
-
Why would you think this traffic would hit your pfsense wan to go to some other IP in the wan network??
"Every host shown is a physical machine with a public IP in the same subnet as the firewall itself."
Do you have pfsense setup as a bridge?
Lets say pfsense has public IP 1.2.3.100/24, and your other servers you say are in the same subnet as pfsense so like 1.2.3.101/24 -- why would pfsense see this traffic if going to .101 when it is .100?
-
@johnpoz I was under the belief that PFSense would filter (and by default block) all traffic that passed through it, until is was allowed. Like your example, PF is 100 but 101 traffic is still going through the pf device before it hits 101.
Cheers,
-
And how is it doing that exactly?? You have pfsense setup as a layer 2 BRIDGE??
You can not put devices in the same L3 network on 2 different sides of a router..
Please explain how you have this connected together and where are the public IPs coming from?
-
@johnpoz No, i do not have a bridge set up. For each of those machines other than PF that are publicly addressed, they are on switch ports that ore members of the same Port VID that the WAN (internet connection) is. PF, laredo, silverado, synsan are all on port vid 4090 (WAN).
This led me to assume each of those physical ports would be filtered the same as the WAN.
Cheers,
-
No.. If you have devices in the same network, lets call them 1.2.3.100, 101, 102, 103, etc..
What IP does pfsense use as its gateway to get to the rest of the internet? say 1.2.3.1??? or 1.2.3.254 for example... That is where filtering would have happen..
Im on say 4.5.6.100 and want to talk to your public IP 1.2.3.102... Why would I send traffic to pfsense on .100??
If you want to use pfsense as L2 bridge and physically put .102 and .103 behind pfsense then sure you could filter how your wanting too.. But you should put these devices behind pfsense.. Then you could route to this public L3 via pfsense wan IP that would be different than the public L3 behind pfsense..
so L2 bridge would be like this
public L2 where 1.2.3.0/? network is --- int0 pfsense (bridge) int1 --- switch --- rest of network 1.2.3.0/?
-
@johnpoz My IP are all leased from my provider, FIOS.
So, the way they have me set up is, I have 13 ip's. 1.2.3.242-254 (PF is 242)
My ISP gateway is 1.2.3.1.I understand your question on why would you ask 100 for traffic on 102. But that request for traffic on 102 is still passing through the PF device. Right?
Cheers,
-
NO!!! How would it - unless pfsense was a bridge..
internet --- switch --- pfsense
If your devices are connected to that switch... WHY would traffic be sent to pfsense IP??
If you want those device behind.. then
internet --- 1.2.3.242 (vip 243, vip 244) pfsense --switch rfc1918 192.168.1/24
192.168.1.243
192.168.1.244And do 1:1 nat or simple port forwarding...
-
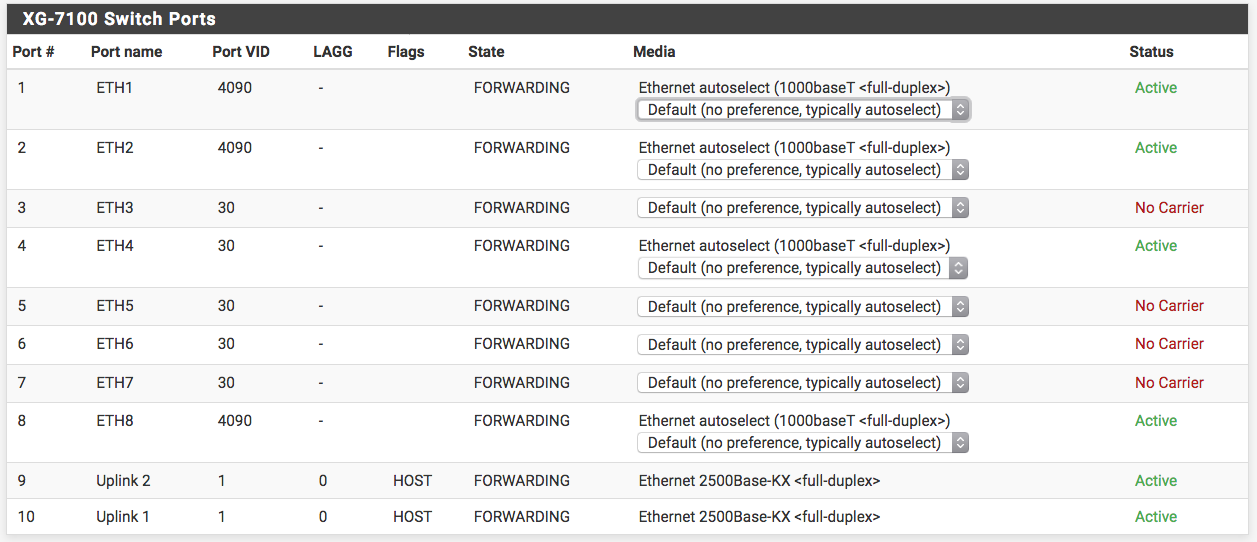
@johnpoz "If your devices are connected to that switch... WHY would traffic be sent to pfsense IP??"
The switch in this scenario is the PF device. In which case the ports with the WAN cable and all the public server cables are a mamber of the same WAN Port VID. See below for ETHs 1,2 & 8.
-
@njlinuxmike said in Rules not working as desired on WAN interface:
The switch in this scenario is the PF device.
Wether the switch is external or in the same physical casing as the firewall doesn't matter, it's still a switch and pfSense will not see/filter the traffic if it's in the same L2 as WAN.
-
^ exactly!!!
-
-
@johnpoz Gretings. I think I have found joy. I created a VLAN 20 and a bridge0 interface named WANPUB and made VLAN 20 and the WAN members of the bridge0.
Port 8 on the Netgate switch is PVID 20. and this port goes to my other switch with the public facing servers connected to it.
Now all the rules work as expected on the WAN rules page, allowing specified traffic to the WANPUB and nothing else.
Does this sound proper? I think it is working as expected.
Thanks again.
Cheers, Mike.
-
Yeah if you bridge you can control traffic that flows through the bridge.
So yeah if you have input on one switch port that is bridge to the rest of your switch ports - then sure you could filter at the bridge point.