[solved]Not sure what this is
-
Hi,
I recently switched over from hyper-v to esxi and rebuilt my pfsense. Imported a backup I made from the hyper-v setup. On esxi I have passthrough set on my lan and wan interfaces using an intel i350v2t2. Its all working well, seems to be slightly faster for me then on hyper-v. The box has suricata and pfblockerng-dev running on it.
Since migrating over to esxi I keep seeing entries in the fw log such as the one here:
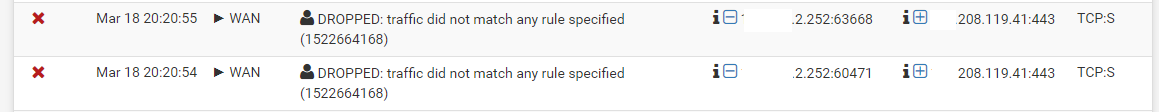
There are not much of them but enough for me to start scratching my head.. I cant figure out what the source of this traffic is.. It has this little "play" icon next to the interface it looks like the firewall self wants to send out data from the wan ip to an external ip as you can see in the picture (what does the play icon mean?).
Have looked up a few of the addresses and some seem to be from a regular consumer line in the US a few to cloudflare, theres also a few going to google dns and im pretty sure I have not set 8.8.8.8 as dns anywhere since im using dns-tls (there are a few android devices on my network but the ips/dns are provided by dhcp). Is there a way I can find out what the source of this traffic is (suricata isnt picking up anything) ?
-
Looks like something is tying to start an HTTPS session with you but it's being blocked on WAN as expected. The Internet is full of bots constantly scanning for vulnerable services to exploit.
-
This traffic is originating from pfsense. The rule it is being blocked by is my cleanup rule, got a few more:
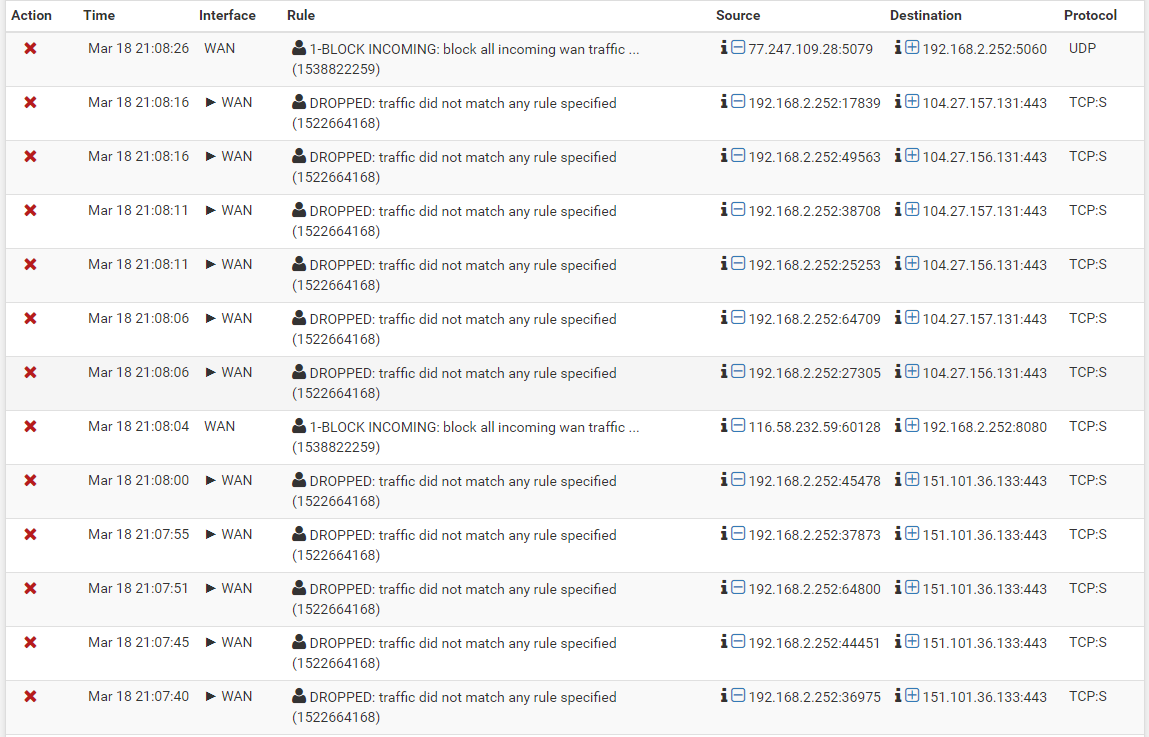
-
Do you have any NATs defined?
-
Yes, I do have a few port forward and outbound nat rules:
port forward:
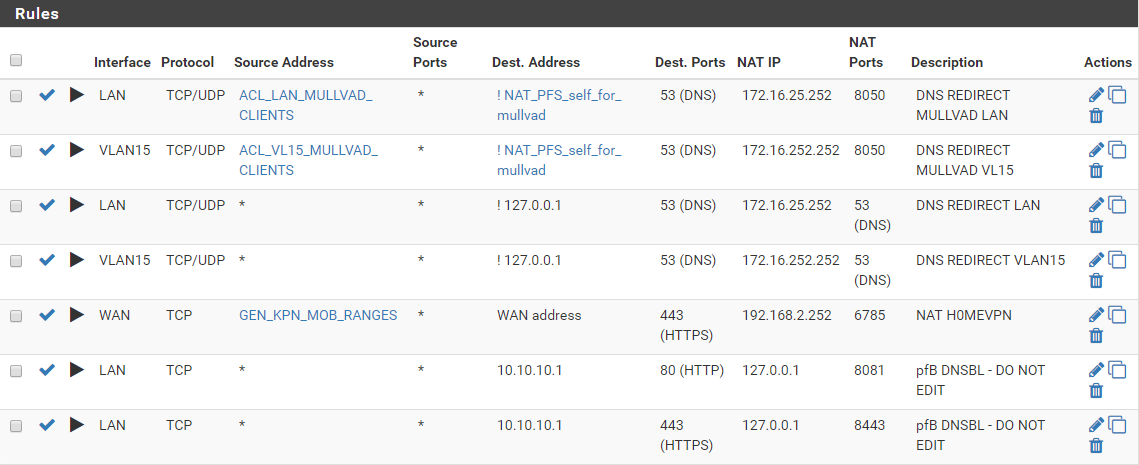
outbound NAT:
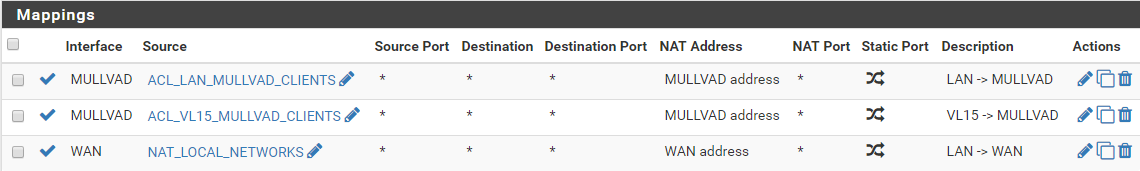
I will look into the VPN got more entries when connected to it with my phone
-
I suspect it's either suricata or pfB blocking these. No reason otherwise for incoming traffic to your NAT'd address to be blocked. It's hard to know for sure without seeing your WAN rules.
-
Only have 2 wan rules, 1 is the port forward in the picture of my previous post and the other is block all in (floating rule). From what ive seen with suricata (inline) blocked traffic doesnt show up on the fw log, i will disable suricata and pfblocker and check the results to see if the blocks dissappear. Thanks for your replies!
-
Think I found the cause, there was a floating rule with source this firewall which had a port alias configured with port 443 at the near top of the rule list.
