Outbounding traffic from LAN
-
Ok lets get some actual details..
You have a client and your trying to go to say https://www.google.com, does it resolve??? Can you ping www.google.com and it comes back with an IP?
What error do you get in your browser?
If your trying to go to https://www.somedomain.tld that resolves on the public to public IP 1.2.3.4, but hosted on your internal network... Then just create host override so www.somedomain.tld resolves to the local rfc1918 address - pfsense never talkked to for the actual connection only the dns lookup.
If your wanting www.somedomain.tld.. to resolve to your public IP while you on your own network then you would have to setup nat reflection... Which is really not the optimal solution... Just use host override.
-
@johnpoz said in Outbounding traffic from LAN:
Ok lets get some actual details..
You have a client and your trying to go to say https://www.google.com, does it resolve??? Can you ping www.google.com and it comes back with an IP?
What error do you get in your browser?
If your trying to go to https://www.somedomain.tld that resolves on the public to public IP 1.2.3.4, but hosted on your internal network... Then just create host override so www.somedomain.tld resolves to the local rfc1918 address - pfsense never talkked to for the actual connection only the dns lookup.
If your wanting www.somedomain.tld.. to resolve to your public IP while you on your own network then you would have to setup nat reflection... Which is really not the optimal solution... Just use host override.
Hi again,
if I go to httos://www.google.com I get
This site can’t be reached The connection was reset.
Try:Checking the connection
Checking the proxy and the firewall
Running Windows Network Diagnostics
ERR_CONNECTION_RESETPing will return 216.58.201.36 which I assume is correct.
Can you please tell me how to create the host override? As you can see I have added an entry to the DNS resolver, but this doesn't help.
Thanks,
D. -
so when your client pings whatever.com that you have pointing to 192.168.22.3 what IP returns? You sure your client actually using pfsense or its dns?
You sure your client is not using a proxy?
Without a proxy or ips... pfsense not going to do anything with your traffic other than allow it or deny it. Are you saying you can go to any http site just fine?
Please post your outbound nats - you just have them on automatic right? Your not using any sort of vpn client setup on pfsense, etc. etc.
-
@johnpoz said in Outbounding traffic from LAN:
so when your client pings whatever.com that you have pointing to 192.168.22.3 what IP returns? You sure your client actually using pfsense or its dns?
You sure your client is not using a proxy?
Without a proxy or ips... pfsense not going to do anything with your traffic other than allow it or deny it. Are you saying you can go to any http site just fine?
Please post your outbound nats - you just have them on automatic right? Your not using any sort of vpn client setup on pfsense, etc. etc.
When my client ping s mysite.com it returns the public IP address of the newtork. So I guess they are using their internal DNS?
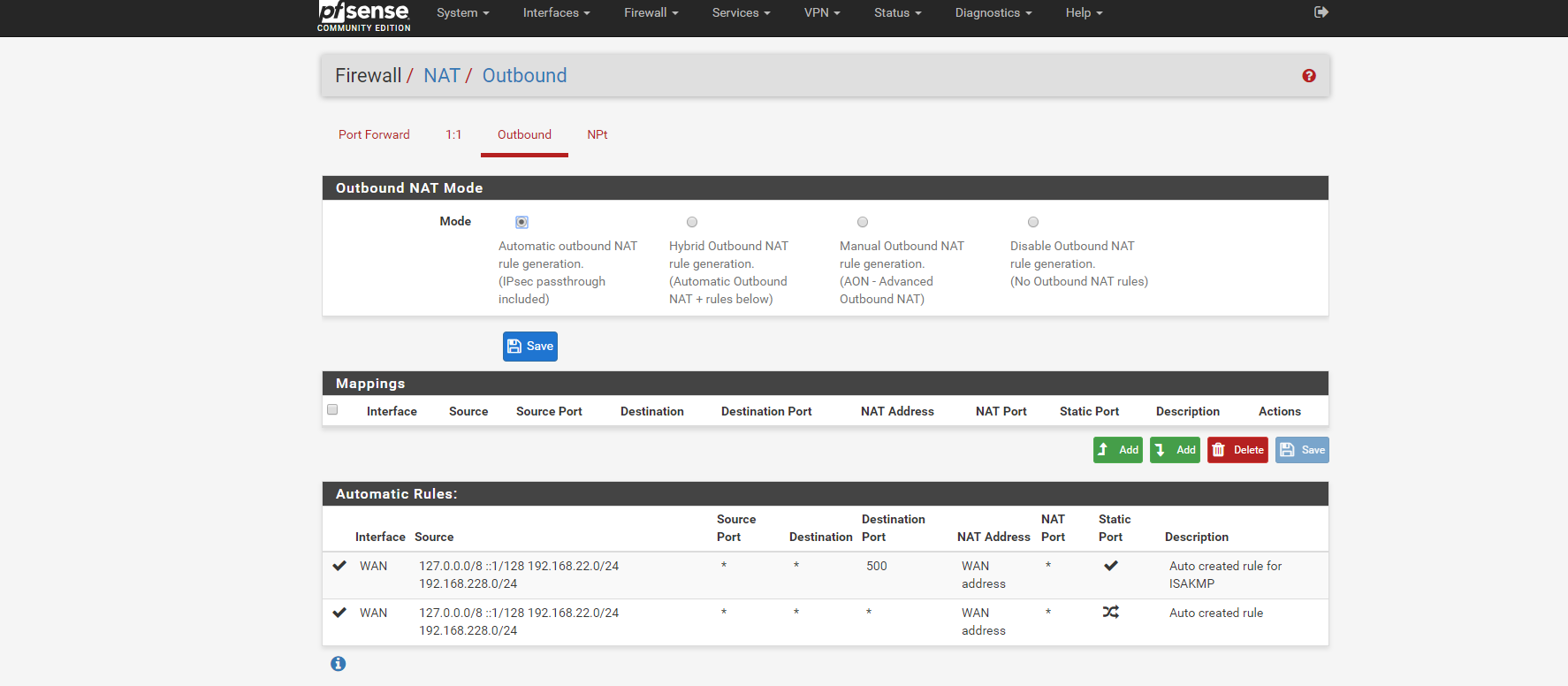
Attached the outbound NAT.
Thanks.!
-
@19Giugno said in Outbounding traffic from LAN:
When my client ping s mysite.com it returns the public IP address of the newtork.
Then your client is not using pfsense for dns.. Since you have the host override there - or you put it in the wrong place... If your using resolver the host overrides go in the resolver, if your using the forwarder, then the host overrides go in the forwarder section.
Ok your outbound look fine.. you have 2 networks 22 and 228? Or is 228 a vpn tunnel network you setup?
-
Ok your outbound look fine.. you have 2 networks 22 and 228? Or is 228 a vpn tunnel network you setup?
It is a VPN tunnel.
The overrides are in the resolver.
-
well then if your clients were asking pfsense for dns that is what would be returned.. I use overrides every day all day, add them and remove them all the time... Its almost impossible for that to get messed up... Unless you never actually applied them and unbound did not actually restart..
Common problem is client not actually ask pfsense for dns..
-
@johnpoz said in Outbounding traffic from LAN:
well then if your clients were asking pfsense for dns that is what would be returned.. I use overrides every day all day, add them and remove them all the time... Its almost impossible for that to get messed up... Unless you never actually applied them and unbound did not actually restart..
Common problem is client not actually ask pfsense for dns..
OK, how can I check this?
-
Do an ipconfig /all from your windows box and check if the dns is pointing to the proper IP of your pfsense box ( you should also check the interfaces pfsense dns is listening on on the resolver tab), try a nslookup www.yoursite.com <ip of your pfsense box> if it resolves correctly you should see a response:
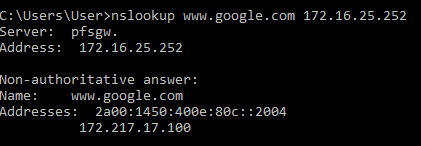
if your dns IP is anything other then your pfsense box, manually change it or check the dhcp settings on the pfsense box and set the correct dns IP to be distributed to your clients (dont know your setup but maybe you still have a dhcp from a isp/modem running giving out wrong dns ip ?)
-
@Actionhenk said in Outbounding traffic from LAN:
Do an ipconfig /all from your windows box and check if the dns is pointing to the proper IP of your pfsense box ( you should also check the interfaces pfsense dns is listening on on the resolver tab), try a nslookup www.yoursite.com <ip of your pfsense box> if it resolves correctly you should see a response:

if your dns IP is anything other then your pfsense box, manually change it or check the dhcp settings on the pfsense box and set the correct dns IP to be distributed to your clients (dont know your setup but maybe you still have a dhcp from a isp/modem running giving out wrong dns ip ?)
Thanks @Actionhenk , adding the pfsense as DNS to the machines make the job! Thanks a lot!
D.
-
@19Giugno said in Outbounding traffic from LAN:
adding the pfsense as DNS to the machines make the job!
Not adding - ONLY!! You can not point multiple dns that do not resolve the same stuff or your going to have a bad day.