Deleting interface does not delete firewall rules
-
I deleted vlan interface and the firewall rules associated with the interface did not get deleted. I know this because I couldn't delete port and ip alias only used on a rule on deleted interface. Also I saw the rules still show up in config.xml. I manually deleted those rules from config.xml and rebooted and it seems to now let me delete the aliases. Note: I did try reboot before editing config.xml to see if it would allow me to delete aliases but no luck.
Another error in logs that popped up was:
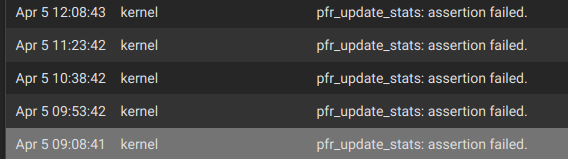
pfr_update_stats: assertion failed.spam like twice an hour. Not sure if related. Google says its issue with pfb-devel but I removed that package before deleting the interface and had no issues before deleting the interface. I reinstalled the package and setup bare minimum blocking (easylist) for dnsbl and no ip blocking and turned on suppression but the error still shows up. Not sure what the issue is, I have downloaded and restored config to see if that fixes the issue. Will report back. Edit: didn't fix it. I'll check the config.xml again to see if I missed any rules.Edit2: I just remembered, the rules were on a interface group (sorry I deleted both vlan and interface group and forgot)
edit3: just did a full reinstall, hoping this will fix the error
another edit: reinstalled with no pfblockerng and still seeing
pfr_update_stats: assertion failed.code is not very clear either: https://github.com/pfsense/FreeBSD-src/blob/a595f803281ea3b25079c9d04a3f5b9a3f0b8a52/sys/netpfil/pf/pf_table.c#L1988 -
viewing rules in console doesn't show any invalid rules. Ref: https://docs.netgate.com/pfsense/en/latest/firewall/viewing-the-full-pf-ruleset.html
edit: it could be another bug https://bugs.freebsd.org/bugzilla/show_bug.cgi?id=234874
-
this seems like the fix (mute the message): https://svnweb.freebsd.org/base/stable/12/sys/netpfil/pf/pf_table.c?r1=343289&r2=343288&pathrev=343289
-
bump
-
That error has nothing to do with deleting an interface or rules. Probably just a coincidence.
We could add that patch, though, open a request on https://redmine.pfsense.org/ and reference that error message, FreeBSD bug report, and the diff. Do not mention deleting the interface/rules though because that isn't related.
As for deleted interface rules, that's how it's always worked. I think there is already an open issue to change things there.
-
@jimp done https://redmine.pfsense.org/issues/9459
-
completely rebuilt pfsense in virtualbox, then deployed it on baremetal box. I don't see the issue anymore. Will update if it continues.
-
nevermind the issue is back. idk i tried everything to fix it.
-
alright so played around with more settings.
disabled nat reflection and port forward to plex manjaro box. No warnings in last hour. I still have another port forward to deluge with no issues. clearly some odd nat reflection issue.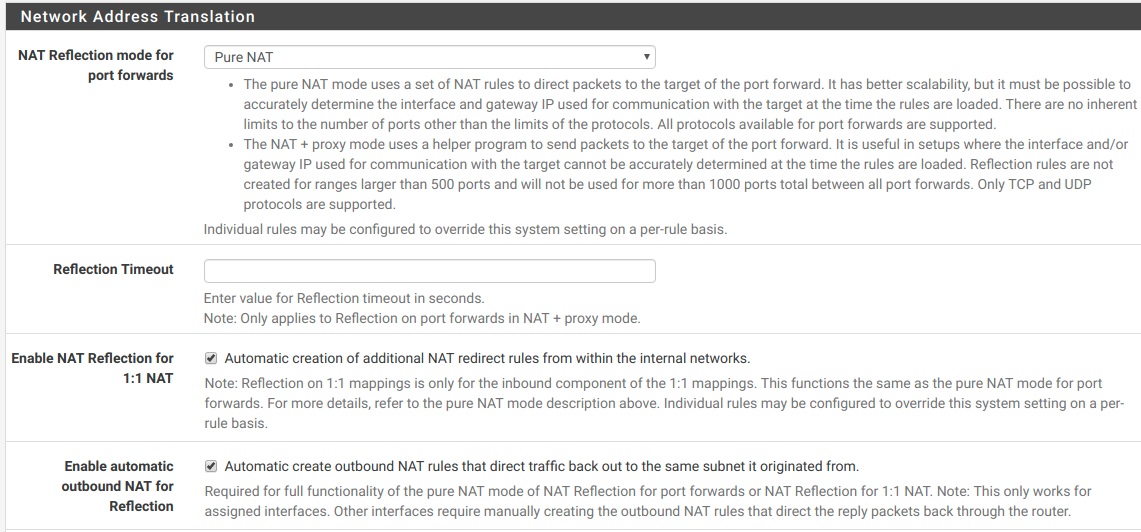
-
no warnings for 2 hrs. nat reflection is clearly the reason for this warning. possible bug.
-
no warning for past day.
-
So I was able to find another way to keep nat reflection turned on and stop the spam. I changed one of the port forward rules from tcp/udp to separate tcp and udp rules. It fixed the issue. tcp/udp port forward rule might be broken.