[SOLVED] logs shows 224.0.0.1 being dropped ALOT.
-
Hello everybody.
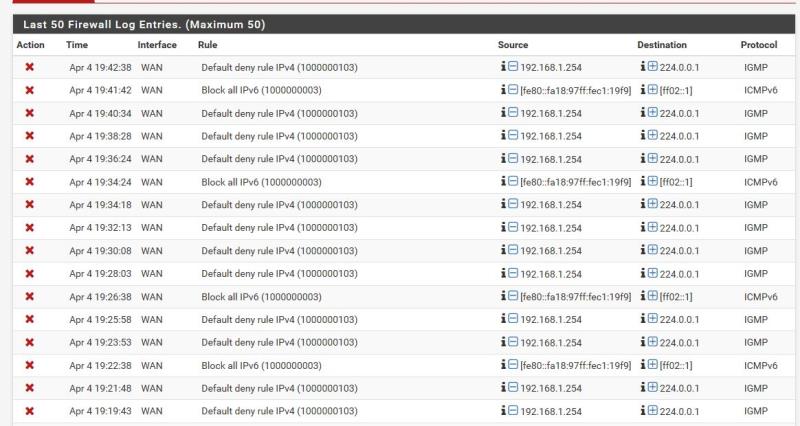
snapshot of Multicast address being dropped.
My firewall log rules dirty filled up with 224.0.0.1 How can I avoid it.
If I Click on block action detail it says--> @9(1000000103) block drop in log inet all label "Default deny rule IPv4"
Thanks
-
I'm kinda guessing here, maybe one of the networking pros can chime in, but it looks to me like you're double NAT'ed behind your ISP modem, since that source IP address in an RFC1918 private network address. That just might be your modem blasting out all that IGMP traffic and your pfsense is dropping it with the default deny rule.
How is your network setup - ISP, type of service, modem is handing out addresses in what scope (dhcp or static), bridging your modem directly into your pfsense, etc?
Jeff
-
Thankyou akuma1x.
yes seems like my Mikrotik router is trying to do something
attached is my network diagram
Thanks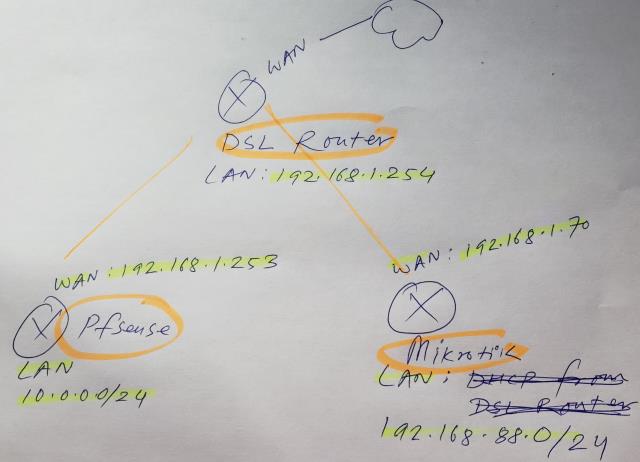
-
If that is traffic you do not want, then setup a rule to block it without logging.
If that is traffic you do want, then setup a rule to pass it, and since it's IGMP, tick the box in advanced options to allow packets with IP options to pass.
-
@jimp said in logs shows 224.0.0.1 being dropped ALOT.:
If that is traffic you do not want, then setup a rule to block it without logging.
If that is traffic you do want, then setup a rule to pass it, and since it's IGMP, tick the box in advanced options to allow packets with IP options to pass.
Thankyou jimp,
I got it now I can configure the firewall accordingly as per your instructions
but I still have one question, I don't know this is a proper place to ask.
If I block the 224.0.0.1 Traffic what will be the downside ? Will I miss any thing from other devices on network like not being able to communicate with them I hope one of the senior member will enlighten me.
Thanks -
It is multicast. Unless you have something on pfSense that needs to see it, like igmpproxy, then it's harmless to block. It can't route outside of the subnet, so it's of no use to a firewall in most cases.
-
Thanks jimpp,
Now Everything is clear with 224.0.0.1.
The firewall is now noiseless as it's dropping without logging. -
@whitekalu how can you do it? I mean clear 224.0.0.1. Can you show me?