Please help... WAN & Dual LAN - Trouble routing LAN2 to tinterweb
-
Evening All,
Wonder if anyone can help me before i go grey, pull my hair out (whats left) or worse yet throw this darn PFSense build out the bleep window.
Im trying to create a 2nd LAN (GUEST) as a guest network on a second interface card, however i cant get internet connection.
My setup is as follows;
WAN --> MODEM --> PFSENSE --> re1=LAN & re2=GUEST
WAN=re0 =192.168.0.1
LAN=re1 =192.168.1.1/24
GUEST=re2 =192.168.2.1/24LAN is routed via a VPN connection with the following rules;
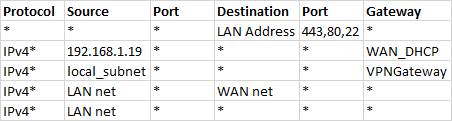
Everything is working fine from the LAN side of things, although and this isnt my main issue; 192.168.1.19 directed to the WAN decided to stop working??
GUEST problem;
So ive created the interface, static IPv4 as 192.168.2.1/24
Enabled DHCP Server, range 192.168.2.100 / 192.168.2.254
setup a guest subnet of 192.168.2.1/24Firewall rules as;
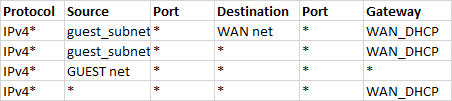
I can ping everything on the 192.168.1.x subnet, and can access it (for instance i have a NAS and can access that) however i cant for the life of me get
on the internet.May be worth noting, i have also added some additional rules to the NAT but that doesnt help either, NAT details below;
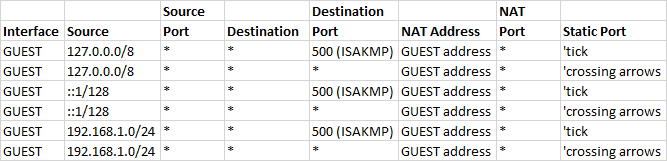
Obviously its going to be a guest network so i dont want them to have access to any other subnet, or even go through the VPN tunnel. Just want them to have
regular internet connection when i can later pipe the traffic in & out. I would of thought id just need a pass rule from guest_subnet to the WAN_DHCP gateway?
But seems im wrong?Can anyone help me out, perhaps im missing something obvious but for 2 days ive been trying. :(
Thanks in advance
-
So a little update, just incase anyone has same issues.
Ive fixed it, i needed to create a NAT WAN rule that allowed access from Guest Lan
Thanks
-
That doesn’t sound quite right...
Jeff
-
Yeah none of that is correct..
That your creating nats on your lan side interfaces (lan and guest) is just wrong out of the box..
You shouldn't be forcing anything out a gateway unless you want to do policy routing, ie out a vpn or something.. If you don't want guest to access lan, then just put a rule on guest to block access to lan net.
Rules are evaluated top down, as traffic enters an interface from the network the interface is attached too. First rule to trigger wins, no other rules are evaluated.
Why would you not just post up screenshots of your actual firewall interface rules? For example here is my dmz network 192.168.3/24 it has no access to lan
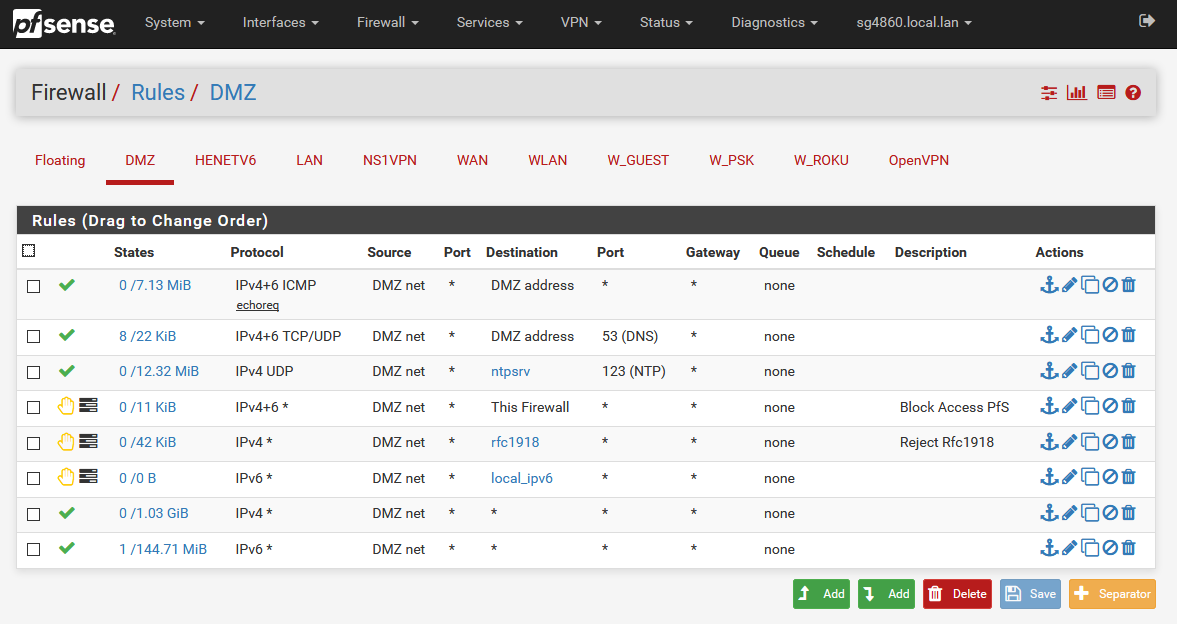
-
Right OK, sorry didn't add images i was that much in a pickle on the first post.
Below are screen shots of each of my rules, and everything works as expected now:
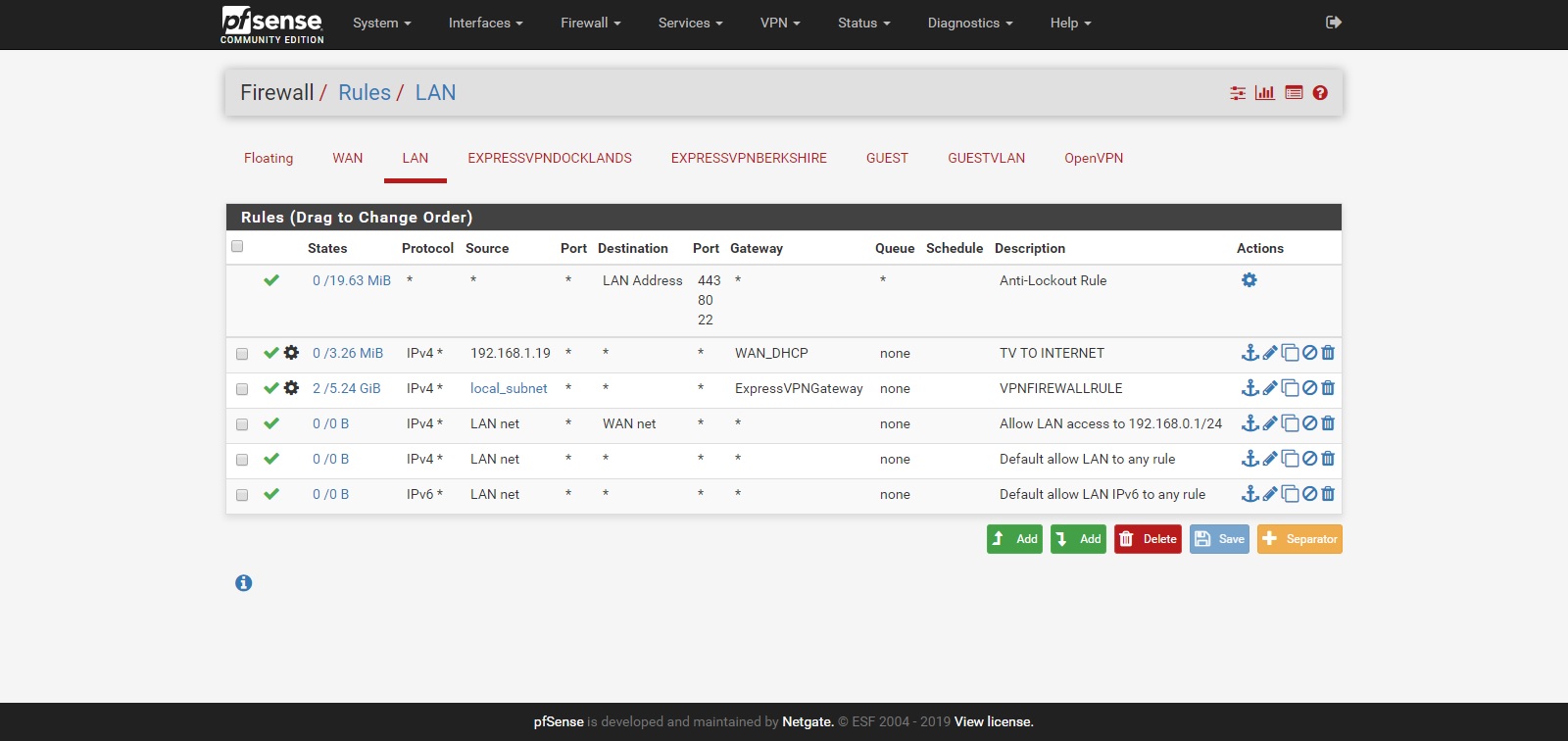
- LAN can access all subnets and traffic routed via VPN
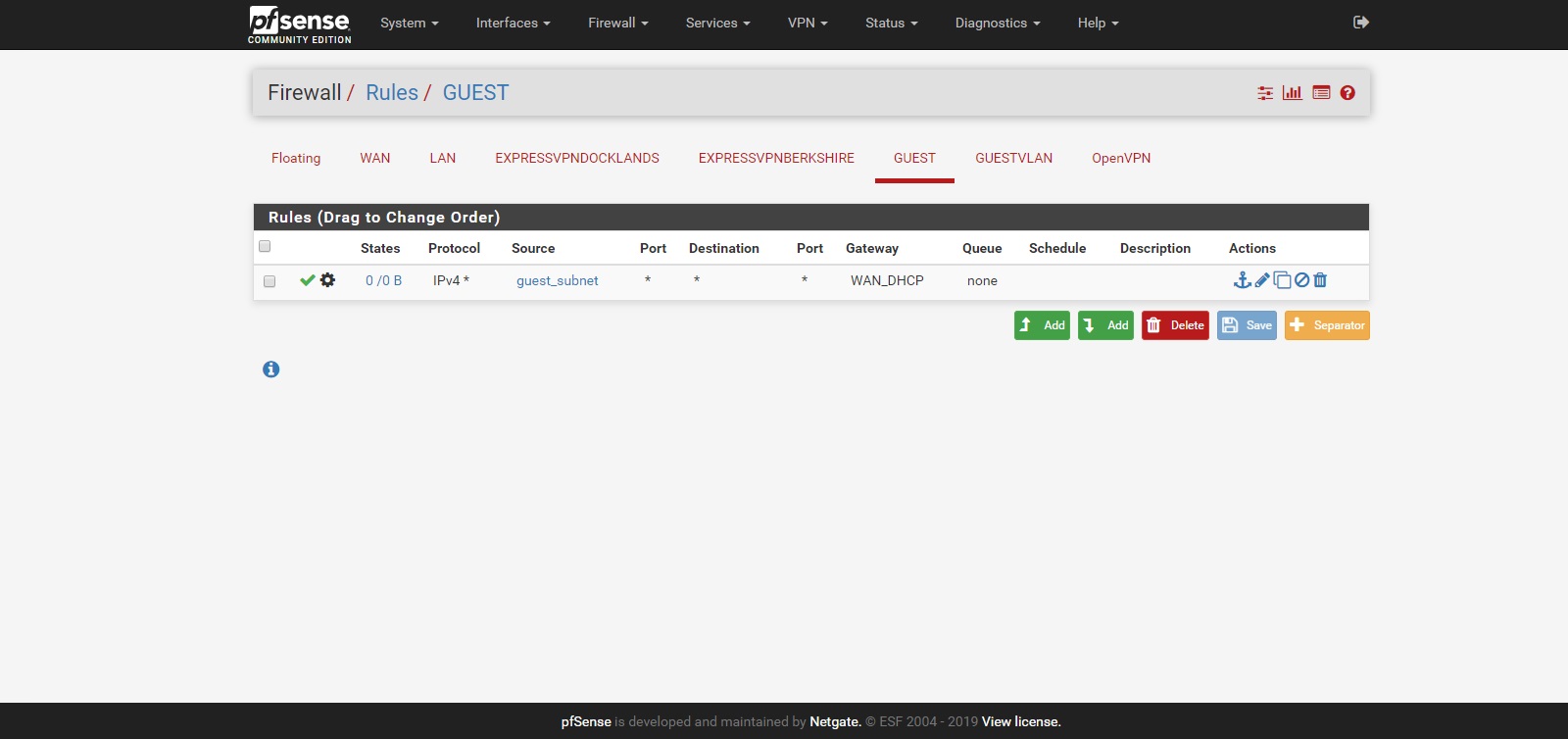
- Guest accesses normal internet
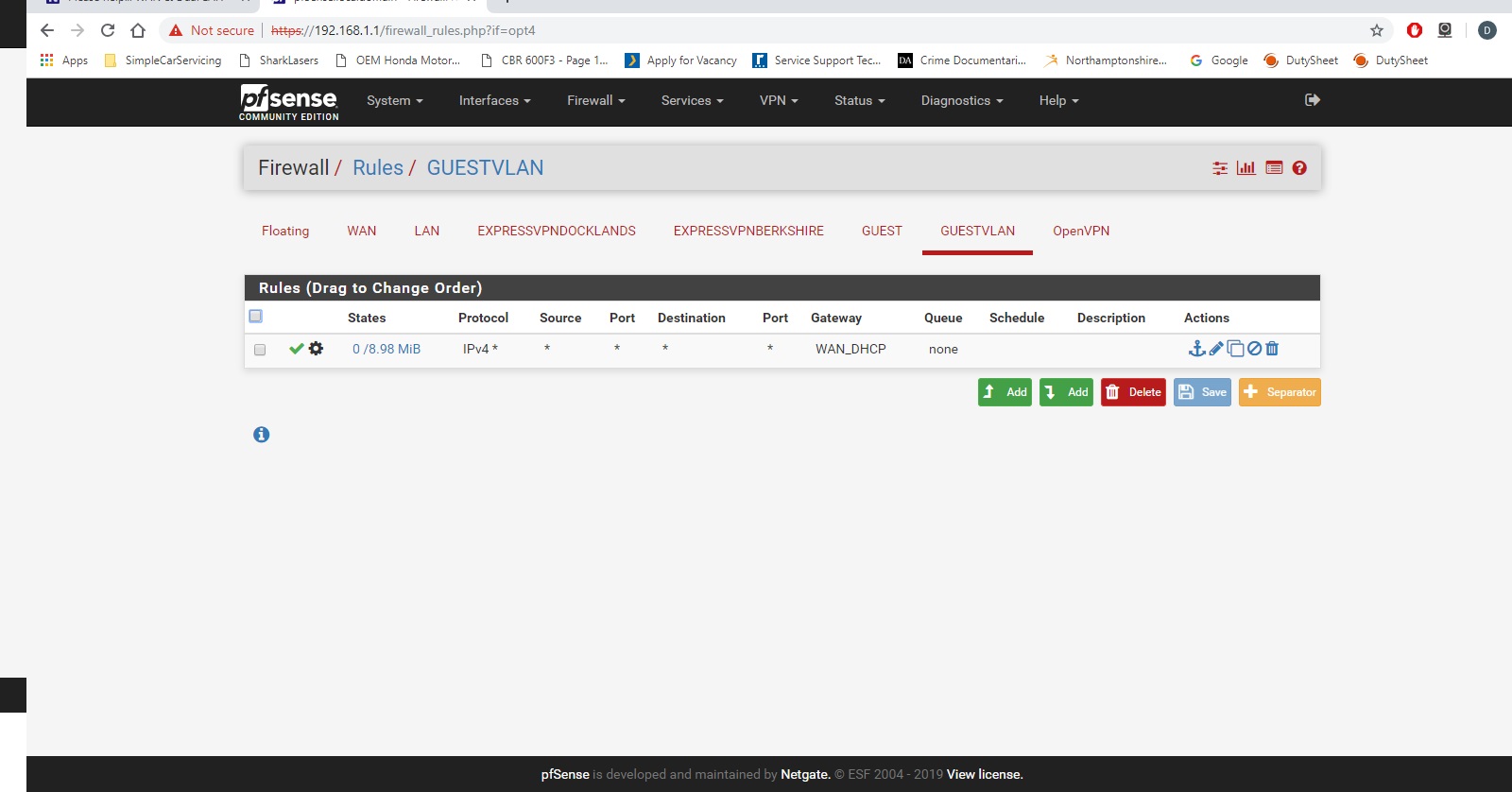
- GUSTVLAN accesses normal internet (A wireless AP tags '13' to devices connected to GuestWifi)
However if I've done something backwards, Im happy to take on board the advice and get it right.
LAN Rules
GUEST Rules
GUESTVLAN Rules
NAT Rules
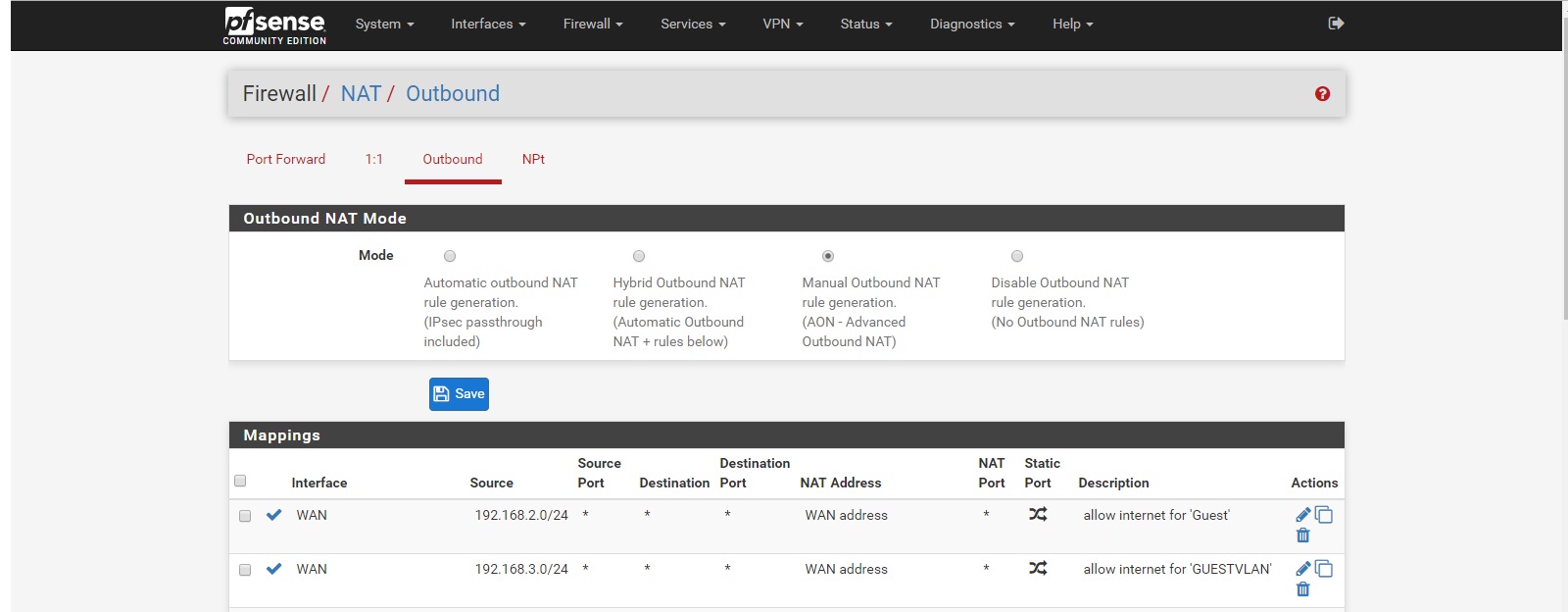
A note on the NAT rules, there is more rules but they are the ones that are created as standard, to which I've copied and amended for the VPN.Will probably make sense to your guys, but as i said before if they are wrong im happy to learn.
Thanks
-
The nst rules are NOT needed.
And only reason your guest can not get to lan is your forcing it out your wan... Not really good way to do it..
With those rules your clients can not even use pfsense for dns..
Why are you using some alias "guest_subnet" vs the built in alias "guest net" for your source?
And that rule on your lan to let it go to wan net? For what reason? When you have a rule below that allows everything..
And your lan would not be able to get to guest with those rules?
-
Thanks johnpoz, ive made some changes based on your recommendations;
- NAT rules been deleted
- used built in alias for guest
- have deleted the LAN to wan rule
However the following occurs;
- All LAN is going through VPN but i have a DNS leak. (Turning DNS resolver on sorts this)
- Guest & GuestWifi no longer have internet
see rules below;
LAN
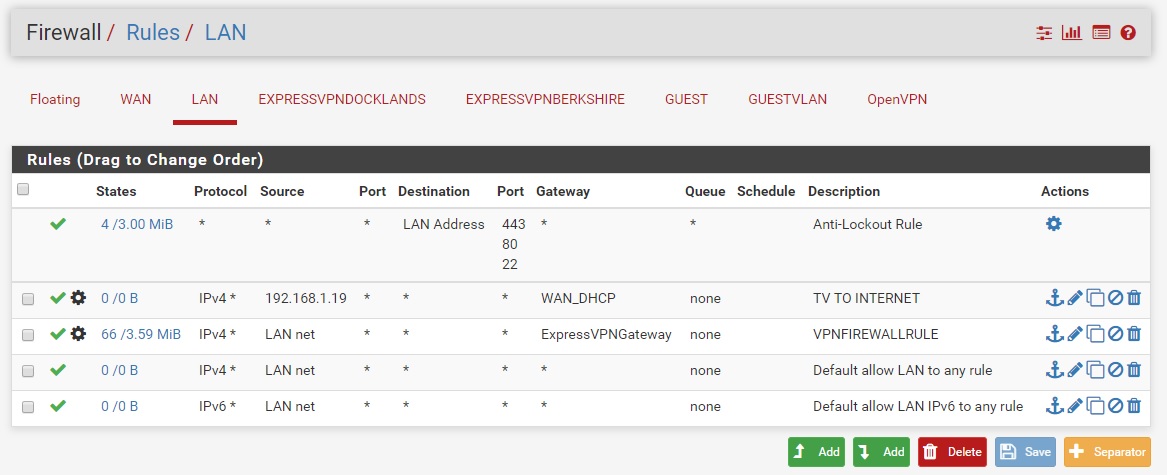
GUEST
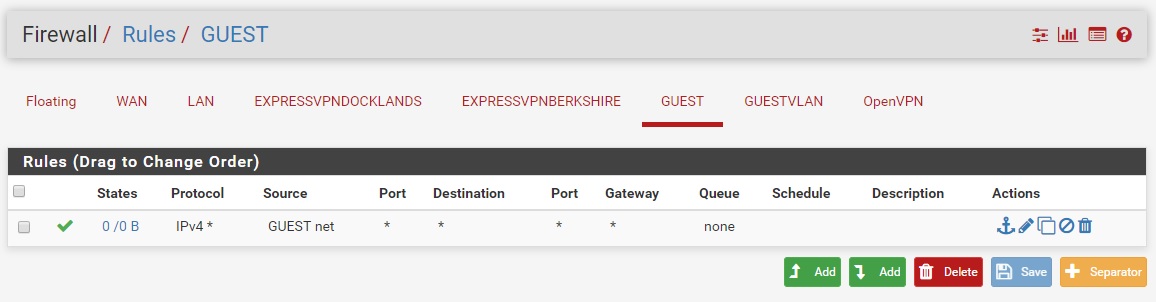
GUESTWIFI
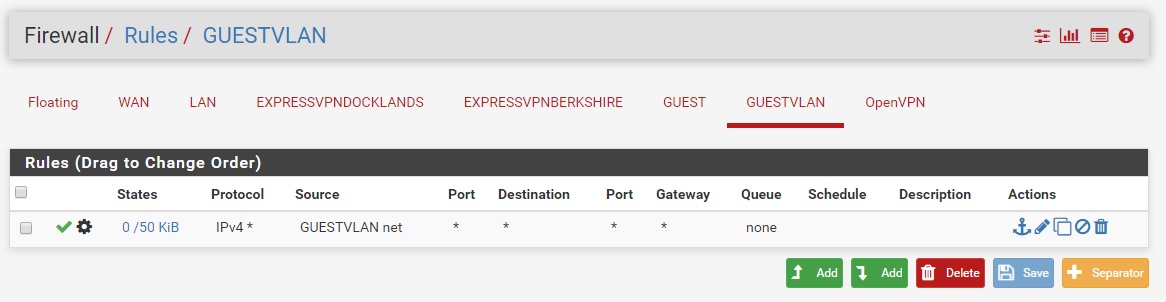
DNS Resolver
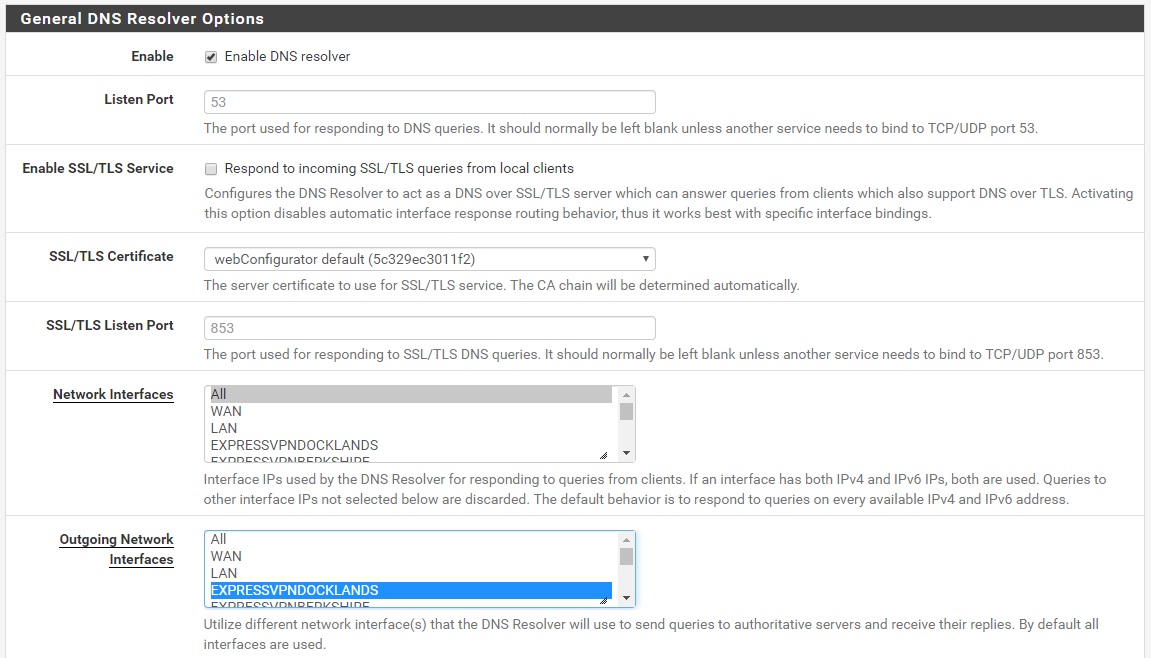
I'm getting myself in a right mess with this :(
-
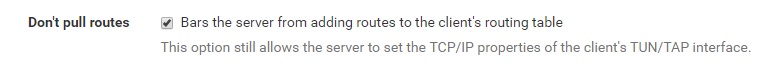
If your going to want to policy route with a vpn, then you need to make sure you DO NOT pull routes from our vpn service!!!
Can you guestvlan ping pfsense guestvlan IP? Can it do a dns query?
-
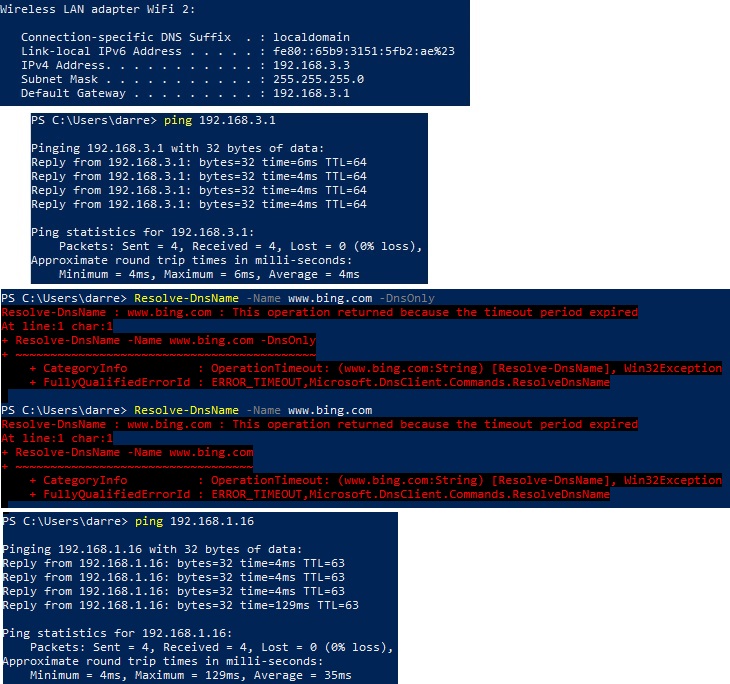
I've not got the VPN to pull routes;
I'm able to ping pfsense from guestvlan,
(As my NAS drive 192.168.1.16 which on my LAN side. This is right at the minute as I've not put a block rule in yet, but ill do that once the guest and vlan get internet)
Thanks for all your help so far