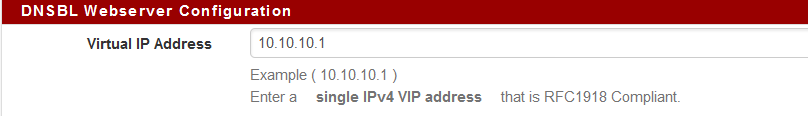
DNSBL Virtual IP: Address must be in an isolated Range that is not used in your Network.
-
Yeah....... but, what's a user to do? They offer wireguard, as well as OVPN, port forwarding, and the service is pretty stable.... I wish there was a way on the client side I could override?
-
Can you ask them why they are using a /16 - say it overlaps one of your local networks.
-
-
No problem, glad you got it worked out what it was ;) My way in finding it easier, but have to admit bbcan177 way more geeky - hehehe
Not sure why they would be even using normal rfc1918 space... Why would they not just use say part of 100.64.0.0/10 (https://tools.ietf.org/html/rfc6598), they should be sure it doesn't overlap with users local rfc1918 space that way.
-
With that now being brought to light and confirmed, is there anything to I, or other users, can do to avoid that and stick with your hard coded default?
Its just a default setting. There is no magic in using that IP or any other RFC1918 address.
-
Here is the response, not bad.
/16 was selected due to the fact that /24 is too small, and the 10 network was used primarily because it was the default (for OpenVPN) and also assigning in the 100.64/10 can create more conflicts with devices that use cgnat. That said, each OpenVPN server port uses a different /16, so a simple solution is to connect to for instance port 1194, which would then give you 10.8.0.0/16 range, and you would not have the conflict in your network. Here are the ranges used: tcp_1401_10.22.0.0 tcp_443_10.5.0.0 tcp_80_10.6.0.0 udp_1194_10.8.0.0 udp_1195_10.9.0.0 udp_1196_10.10.0.0 udp_1197_10.11.0.0 udp_1300_10.14.0.0 udp_1301_10.15.0.0 udp_1302_10.16.0.0 udp_1303_10.17.0.0 udp_1400_10.21.0.0 udp_53_10.7.0.0And of course




-
So they didn't answer about the /16 - so they have some 65k some clients connecting to the same server?
/24 yeah ok too small what about a /20 or 19, etc.. /19 would be 8k some IPs..
-
Nope! I did follow up, but haven't gotten a response yet.
-
@johnpoz said in DNSBL Virtual IP: Address must be in an isolated Range that is not used in your Network.:
So they didn't answer about the /16 - so they have some 65k some clients connecting to the same server?
/24 yeah ok too small what about a /20 or 19, etc.. /19 would be 8k some IPs..
Hello, To be fair, we are nowhere at that point, at most I've seen 200-300 users on servers that has the highest load (8 core 10GbE) Most servers have way below that and can use a /24 with no problem, however we do want to design in a way so we do not run into issues later on. Best regards -
So their servers or cluster at each pop can handle 65k users - yeah find that unlikely ;) This just a perfect example of how misuse of ipv4 space ran us into a shortage of ipv4 way before it should of ever happened..
Network space should be assigned appropriately for the amount of devices that will be using that space.. Even when inside rfc1918 space (which has limits as well) Sure you allow for growth and such.. But come on their 8 core 10ge box could handle anywhere close to even 8k users? That would leave you at most 1.25mbps each user ;) Let alone 64k users ;)