Can someone please explain the difference between interface vs source when it comes to the firewall rules?
-
Hi everyone, not sure if I'm just dense but I cant seem to figure out what the difference is between the interface and the source when creating a firewall rule. I was hoping someone could please explain it. Every post or article I've read has not put this in a way that I can understand.
When creating a firewall rule, in what situation is the interface different than the source? If you am using (for example) Guest LAN as the interface then wouldn't all traffic come from the Guest network LAN as the source?
Destination makes sense to me. That's where the traffic is going. But being able to select the interface separately from the source is not clicking in my brain as to why that would be useful.
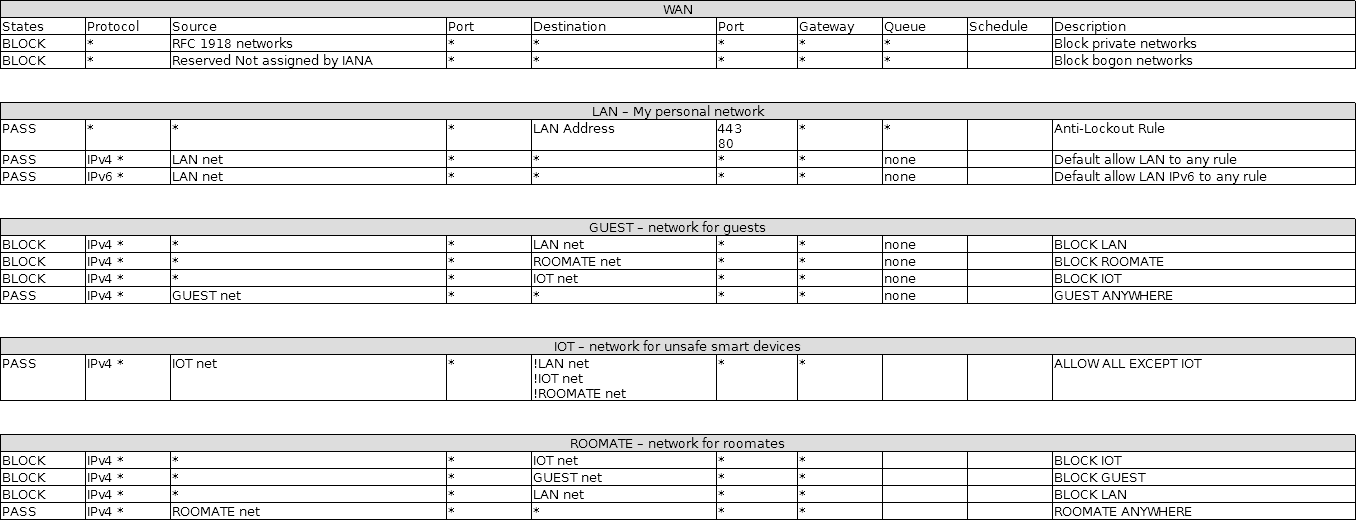
Here are my firewall rules so far. Any input would be greatly appreciated
-
The interface is the interface the traffic would arrive into.
The source is the source address in the IP header.
You can have traffic arrive on an interface that is not sourced from the network of that interface.
Imagine a downstream router (that does not perform NAT) with several subnets behind it. The transit network to that router would be the TRANSIT network subnet, but if you put that as the source network that would not cover source addresses that were routed through that downstream router so that traffic would be blocked.
In general you are correct. Any traffic coming into LAN from LAN hosts should be sourced from LAN net and, in general, it is best to limit traffic to those source addresses that are expected on an interface (blocking everything else) which is why the default is to only pass traffic from LAN net sources. But that is not always going to be the case, so flexibility exists in crafting pfSense rule sets.
I personally despise using pass ! rules to "block" traffic. Some smart people disagree. Your rule set is a perfect example as to why I feel the way I do. You are passing to ! LAN net, then ! IOT net, then ! ROOMMATE net. The first pass rule to ! LAN net will pass traffic to IOT net and ROOMMATE net and processing will stop. Those "pass to !" rules will not be processed because ! LAN net matched the traffic to IOT and ROOMMATE so it was passed. This brings us back to "If you want to block traffic, block it. Don't just pass everything but (!) that." Simple really - don't use pass rules to block specific traffic. If you want to block it, then block it. If your rules blocked destination LAN net then IOT net then ROOMMATE net it would behave as you expect it to and would be much more clear to the next person reading it.
You don't really have to worry about blocking traffic to destinations on the interface network because that traffic is same subnet and shouldn't be using the firewall anyway. The only time that might make any sense is in certain NAT reflection designs which I wouldn't recommend in the first place.
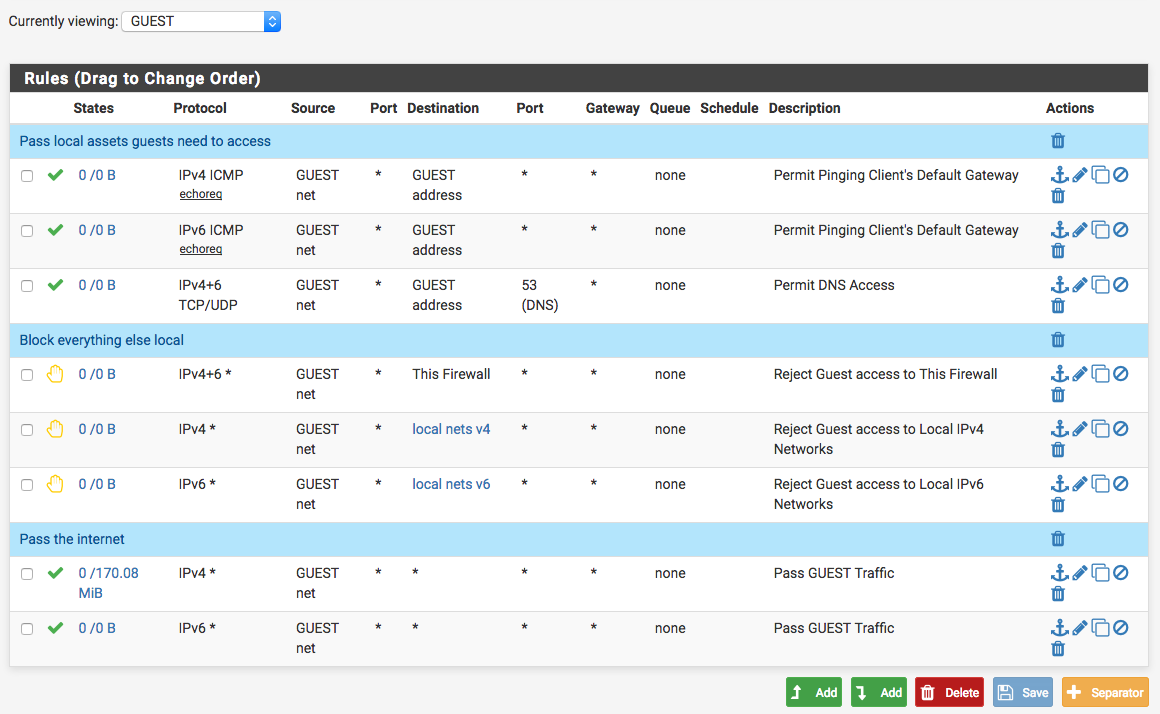
When creating a GUEST network, it is best to simply do this:
Pass traffic to local assets they need like DNS servers
Block traffic to any local assets that you don't want them to access
Pass traffic to any (The Internet)Basic guest network rule set:
-
This post is deleted! -
Thank you for taking the time to explain the difference to me. It was really helpful and I finally understand the difference! I really appreciate it!