Configure 3 lan in pfsense
-
@akuma1x It is only configured there for internet access, because it does not have internet access anymore, mmm something is wrong here :o :( Thanks for your help
-
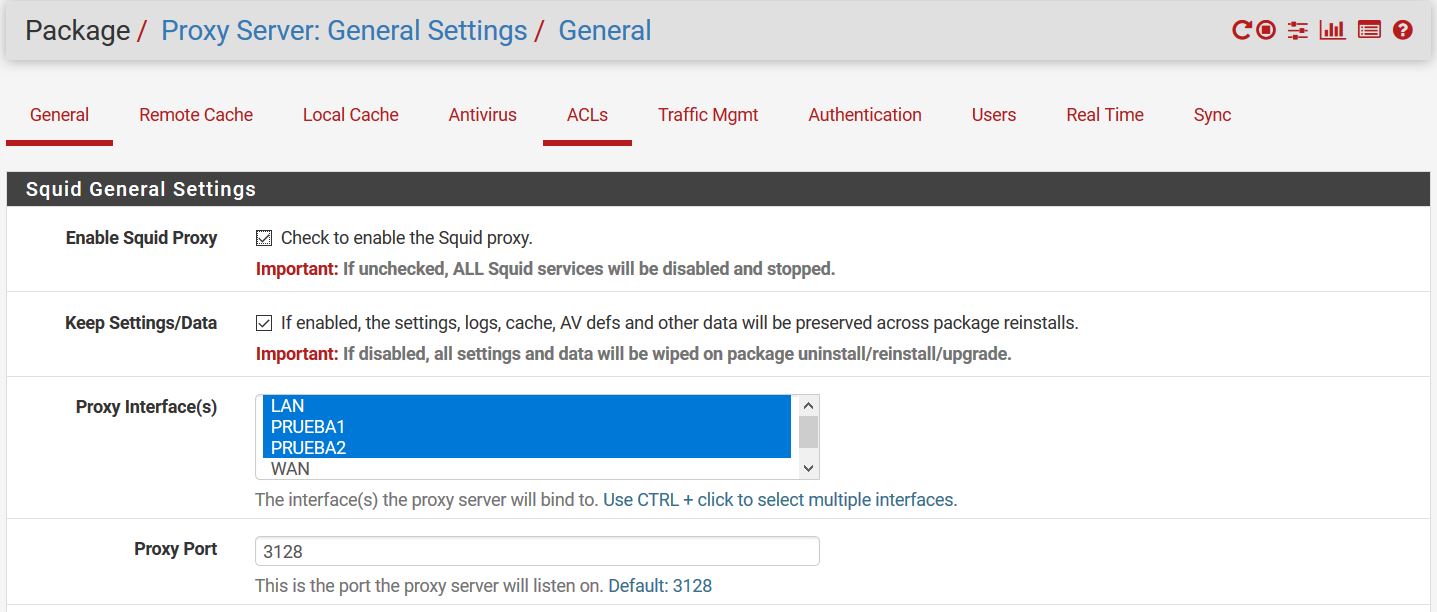
Do you have Squid set to listen on those new interfaces?
Steve
-
@stephenw10 I did it like that
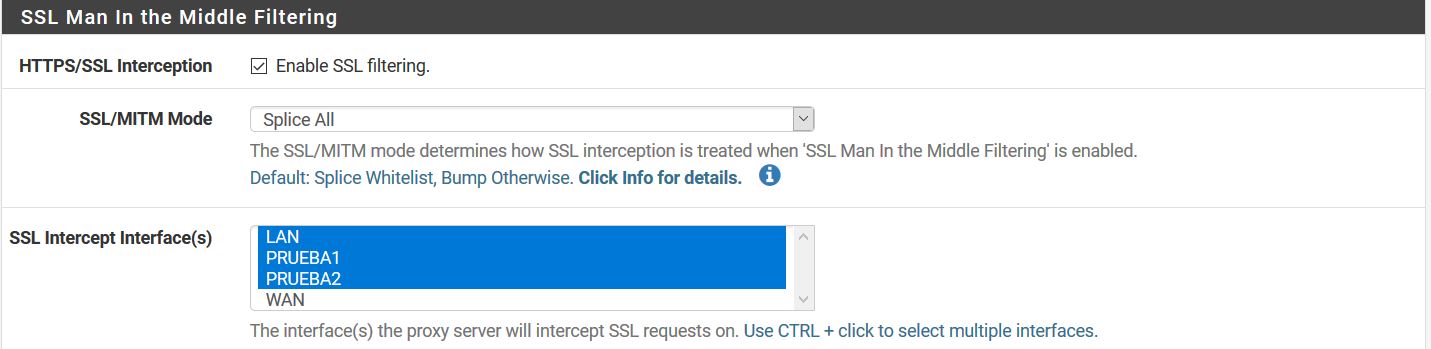
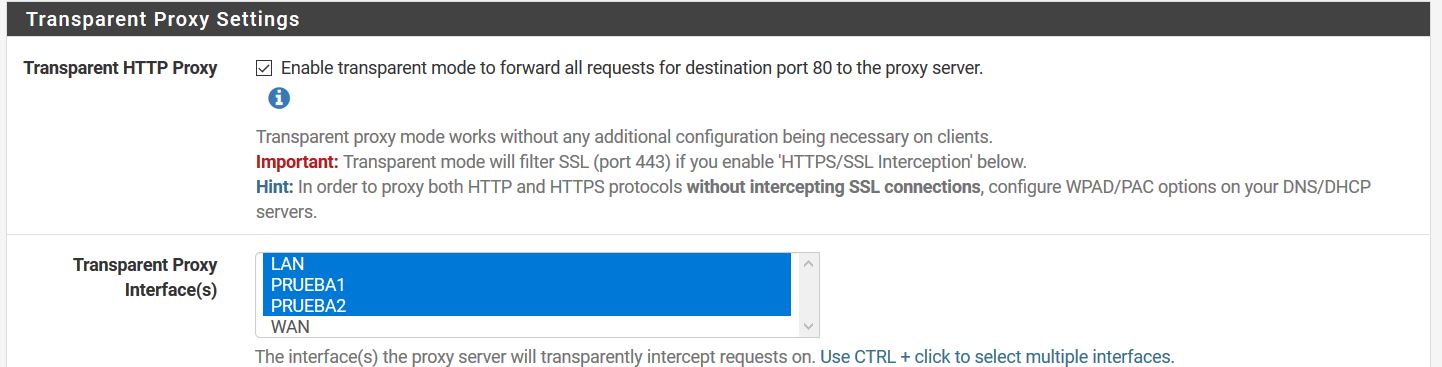
-
Hmm, OK do you see hits in the squid access log from clients on all 3 interfaces?
If so the Squidguard ACLs are probably not set for all three subnets as sources.
Steve
-
@stephenw10 And why does not squidguard block the list that I have assigned :( ?? and how do I configure that?
-
See my last question ^. Is squid showing it's proxying that traffic?
Is Squidguard configured to filter traffic from all three subnets?
Steve
-
@stephenw10 Yes I do it
-
-
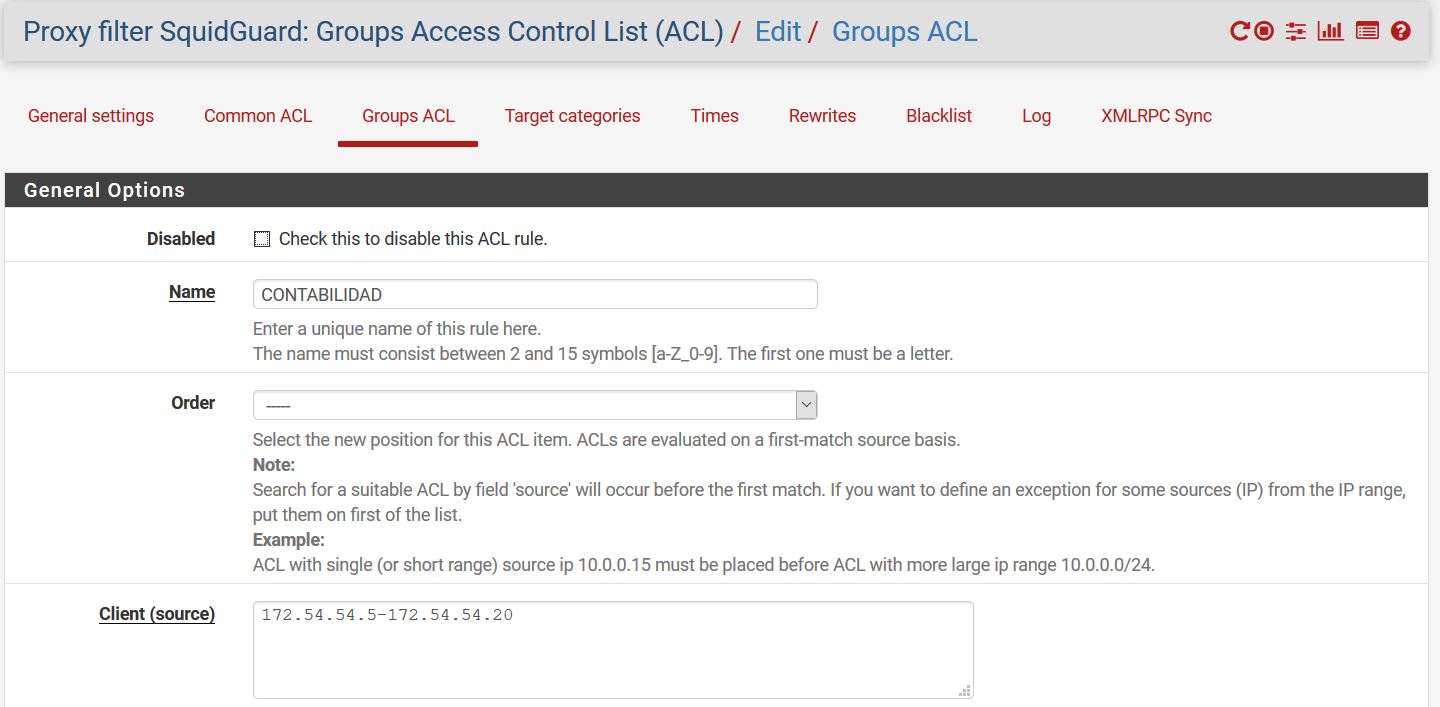
Your group ACL there only contains 15 IPs. Is that the group that should be allowed access to any site?
What targets do you have set there?
What do you have in the Common ACLs?
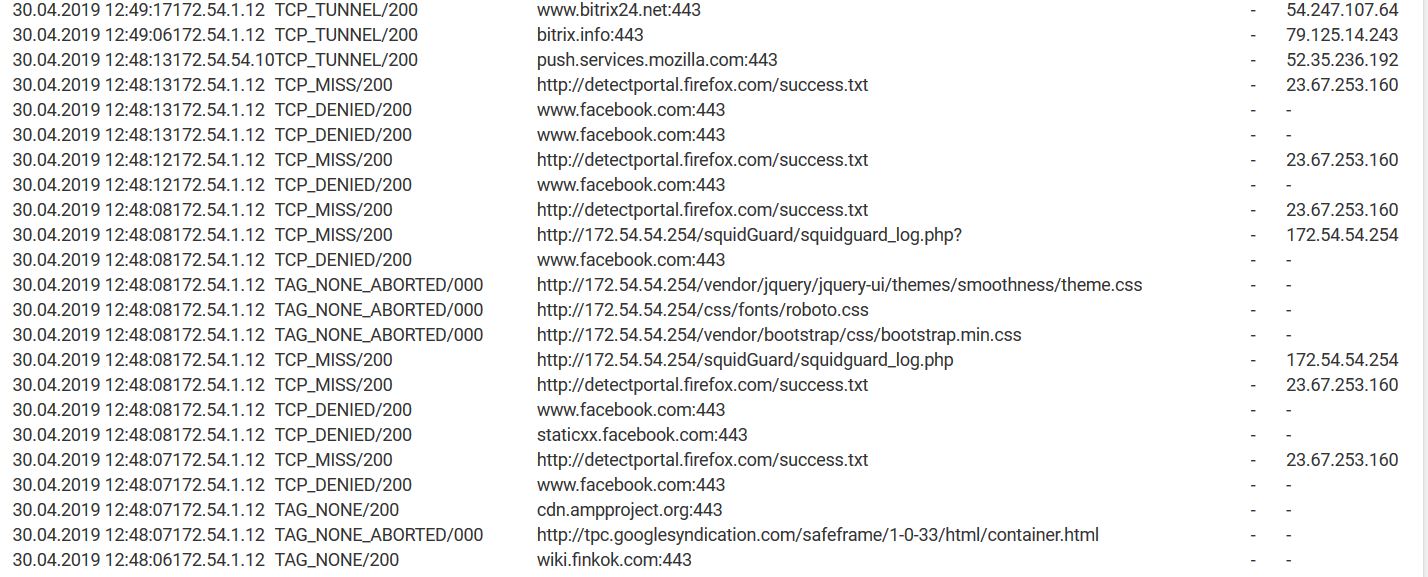
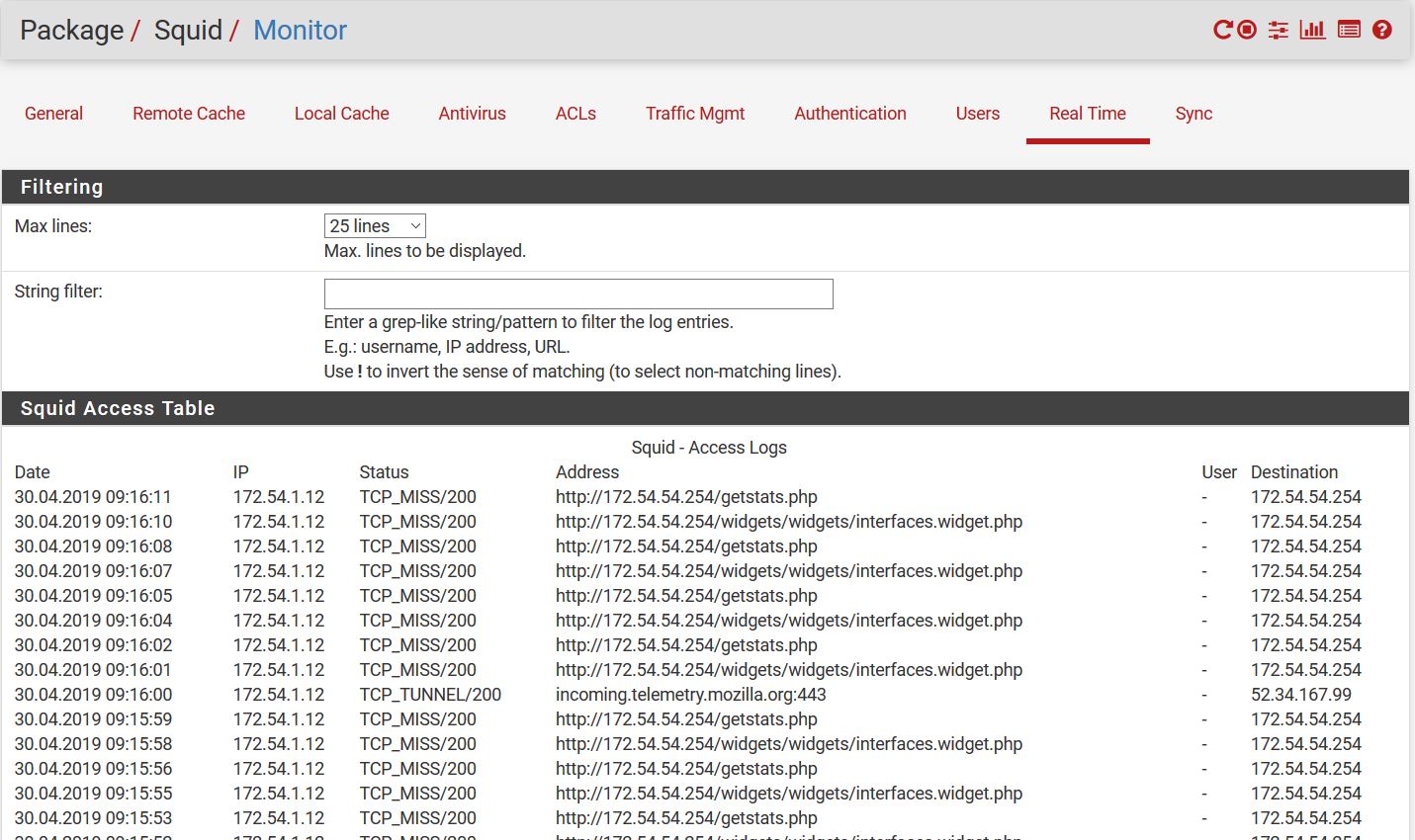
Do you actually see traffic from all three subnet in the Squid RealTime logs to show they are all being proxied?
Steve
-
@stephenw10 Your group ACL there only contains 15 IPs. Is that the group that should be allowed access to any site? R: That group of ips should be restricted some content and enable all
What targets do you have set there? R: I have a blacklist where I added the domains to block
What do you have in the Common ACLs? R: I deny the black list that I just created for the group of ips and I allow everything else
Do you actually see traffic from all three subnets in the Squid RealTime logs to show they are all being proxied? R: yes i have access logs
-
Ok, well if that's your blocked clients list do you have group ACLs for each subnet? That;s just one subnet listed there so it would not catch traffic from the other interfaces.
Is that one you have shown working?
Steve
-
@stephenw10 Ok, well if that's your block clients list do you have group ACLs for each subnet? R: Yes, for each one
Is that one you have shown working? R: Yes it is the one that works well
So how could I do it so that if I accept the block list? :O -
I don't understand the question.
If traffic from the other subnets is not being filtered then it is probably not matching the group ACLs for those interfaces. Check they are correct.
Steve
-
@stephenw10 my question was because it does not block correctly if I have already configured the squidguard?
Yes I have already checked and everything corresponds to each group in each list ! :O -
Ok can we see shots of that to check?
It is either not matching the group ACLs or those ACLs are not set to the correct target rules.
Or it could not be going through Squid at all but you have said that traffic appears in the Squid logs.
Steve
-
@stephenw10 My configuration
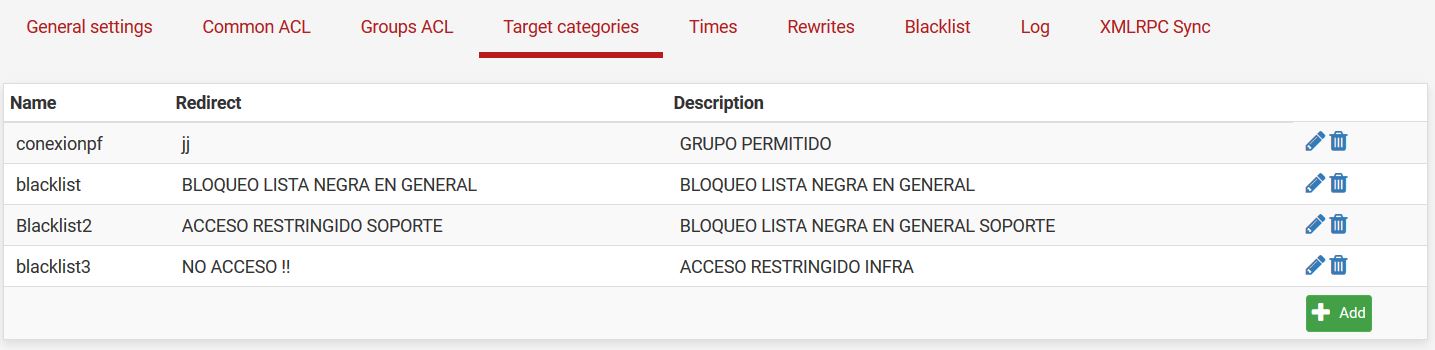
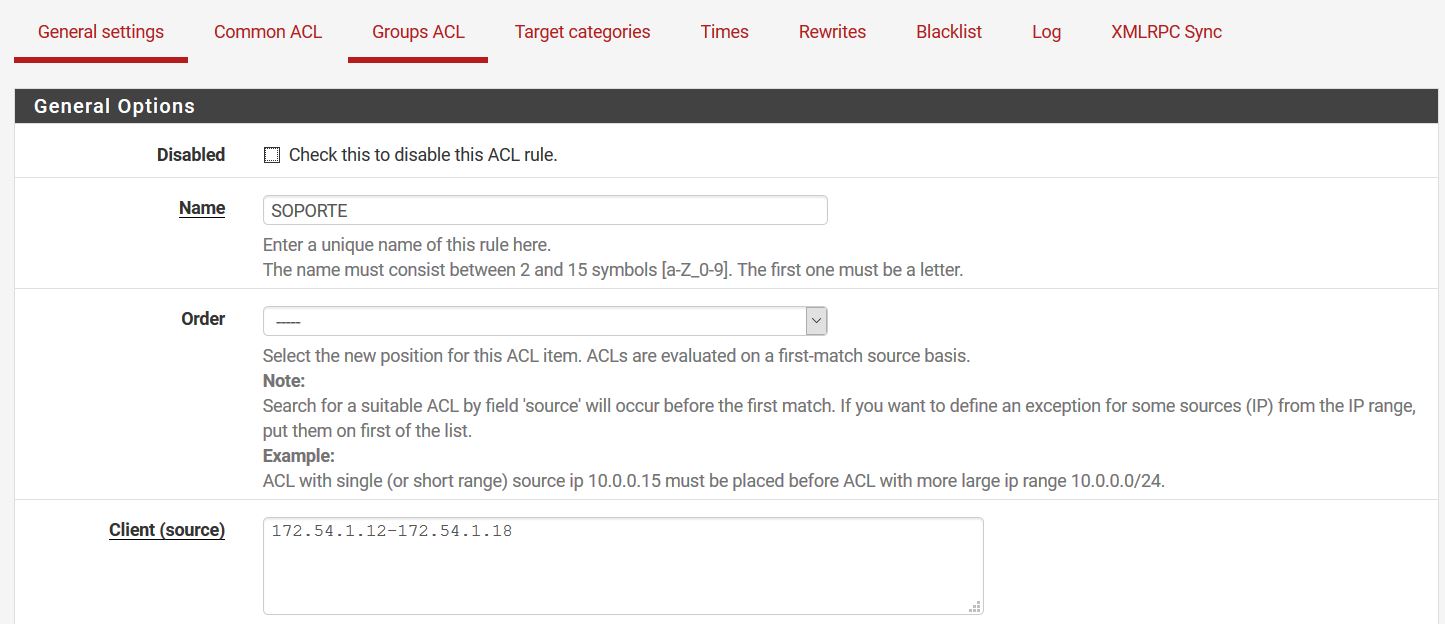
-
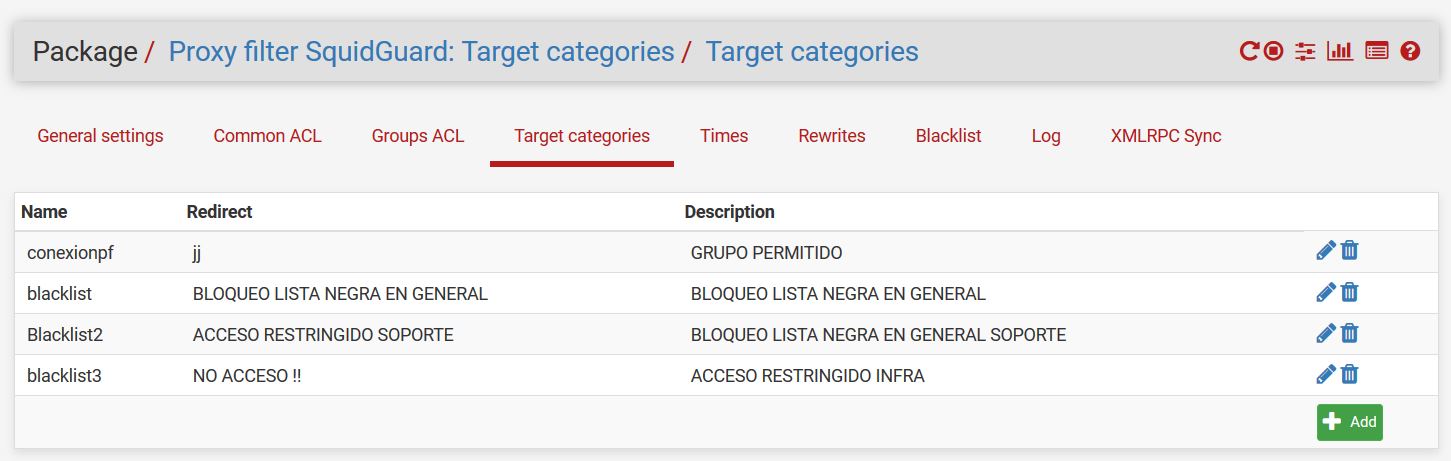
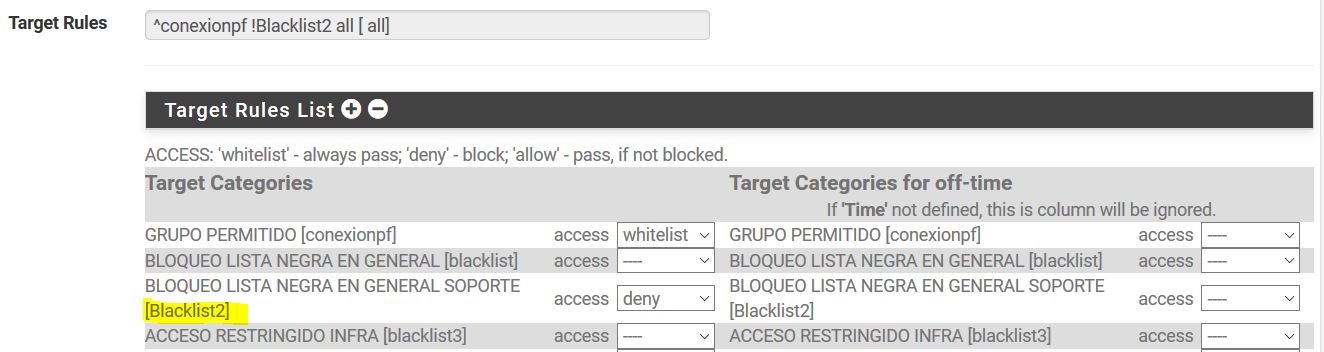
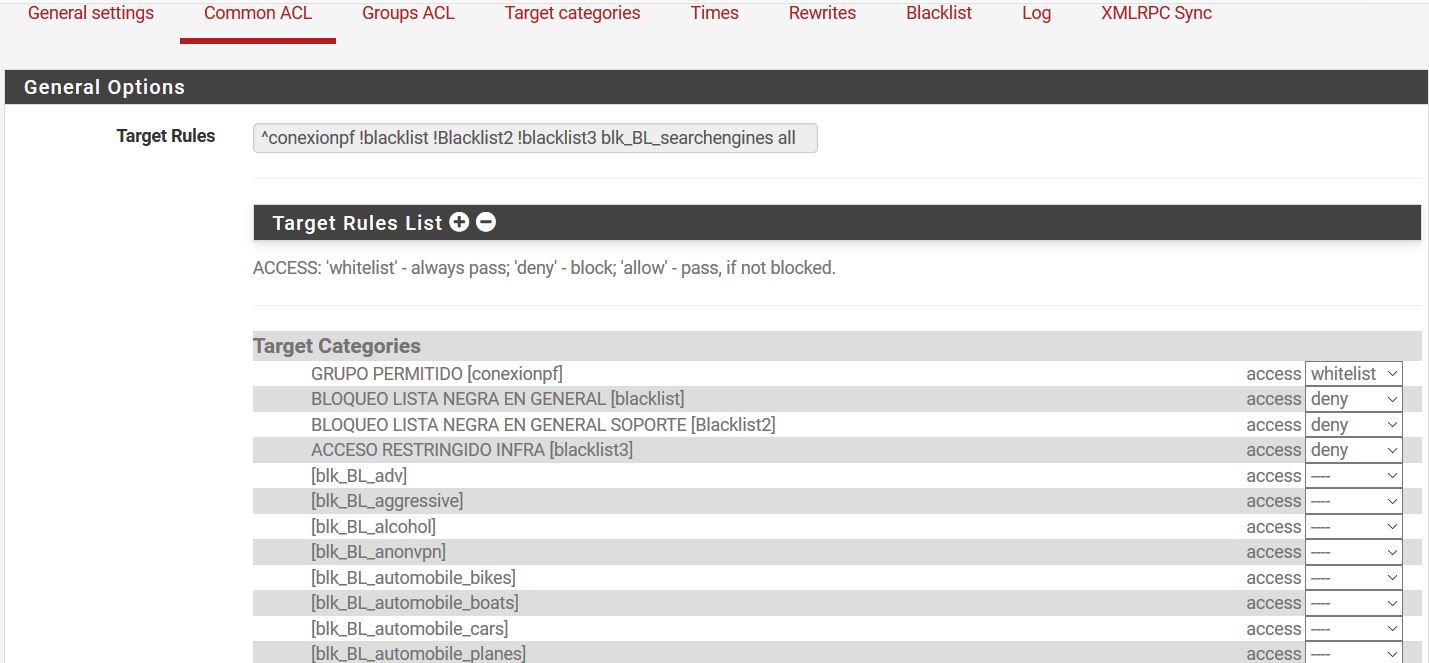
Ok, which of those is in Blacklist2 that should be being blocked?
And I assume it is not in conexionpf?
It should be blocked because 'Do not allow IPs' is checked?
Steve
-
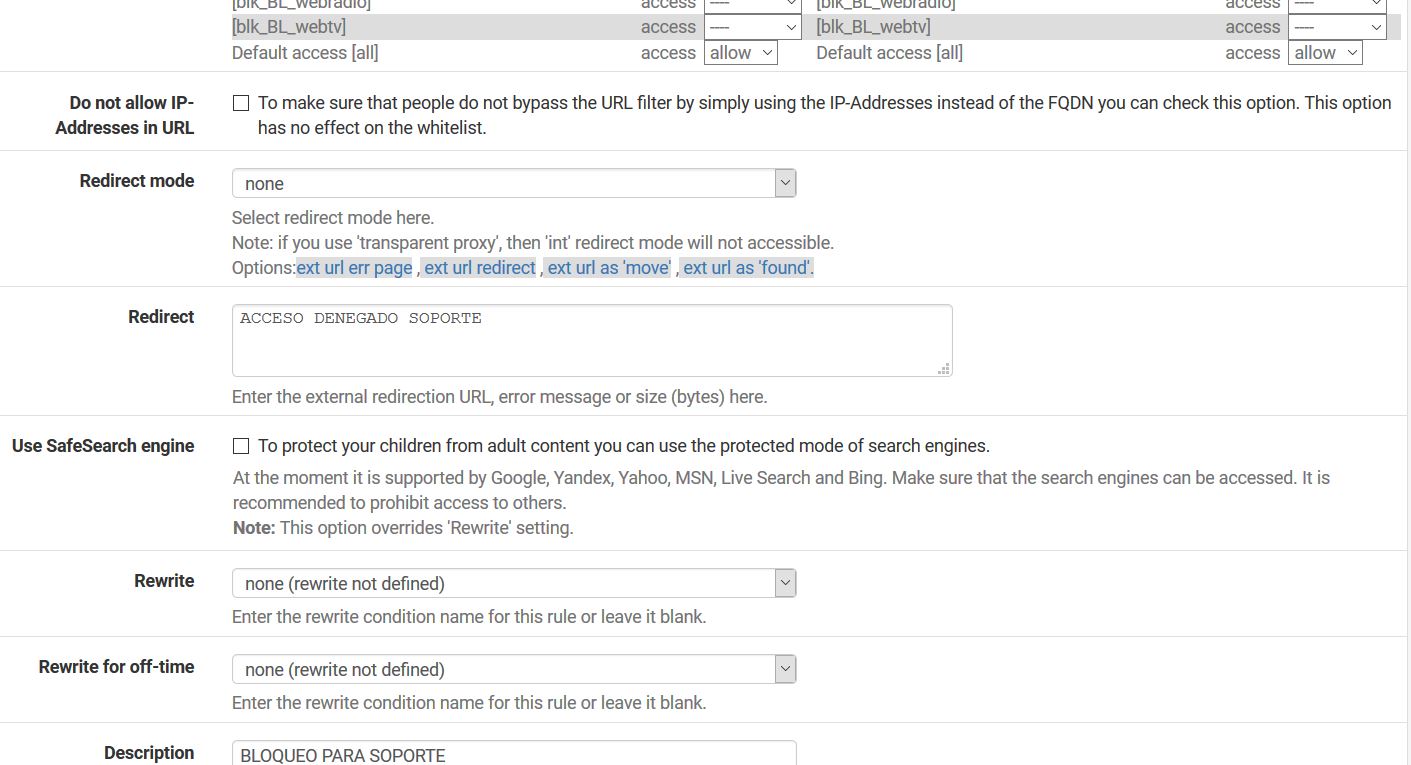
@stephenw10 Ok, which of those is in Blacklist2 that should be being blocked? R = blocked domains for the support area
And I assume it is not in conexionpf? R = Is the ip of the pfsense to ensure connection to internet
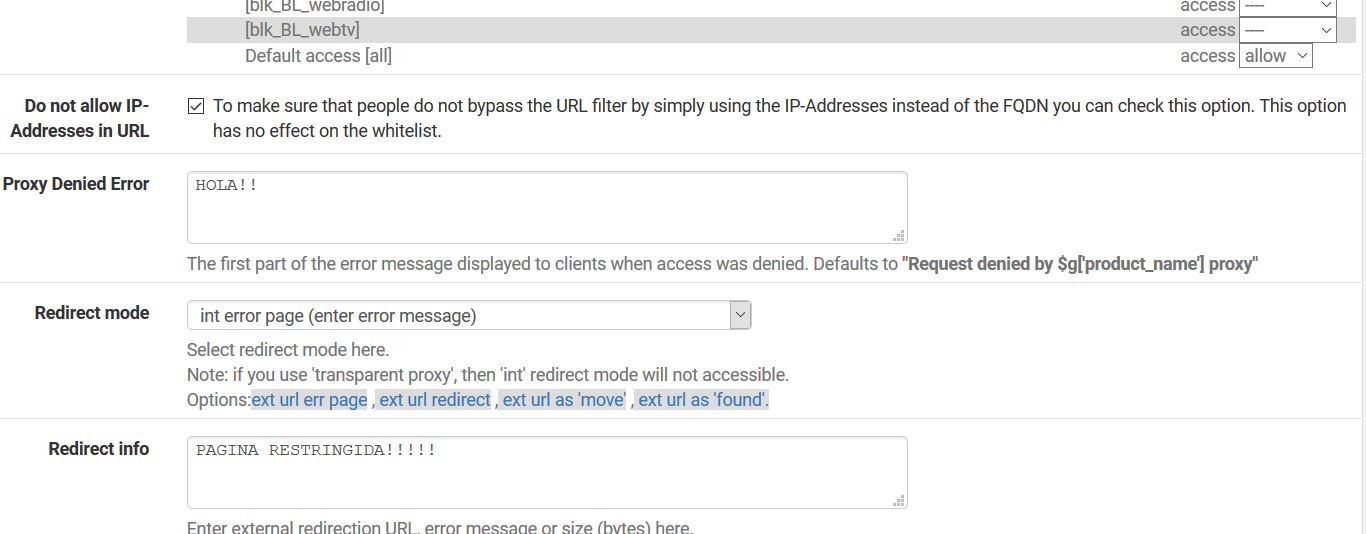
It should be blocked because 'Do not allow IPs' is checked?
R = Then I disable this option, I understood that it was so they could not place the ip
¨Do not allow IP-Addresses in URL
To make sure that people do not bypass the URL filter by simply using the IP-Addresses instead of the FQDN you can check this option. This option has no effect on the whitelist¨. in common ACL -
That option is to stop people using the IP directly.
I was asking if you expected that traffic to be blocked because the only thing I see in the log is the pfSense webgui at 172.54.54.254 and mozilla.org. I assume both of those should be passed?Incidentally 172.54.54.X is public IP space, it belongs to t-mobile. You should be using a private address there.
Steve
-
@stephenw10 Yes, mark the traffic and the ip is from my proxy jejejje