OpenVPN and Gateway group
-
Hi,
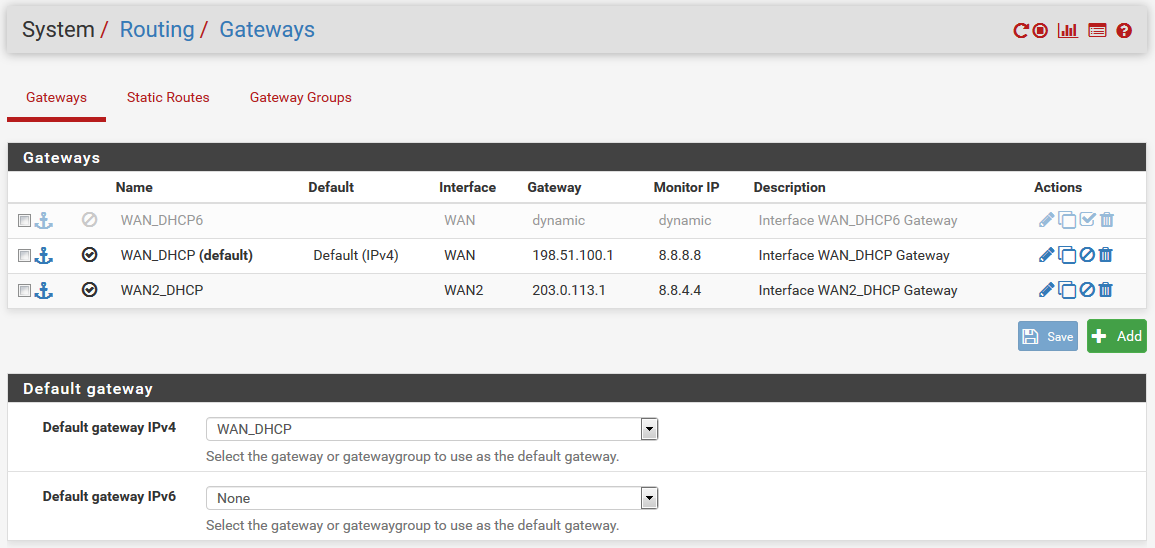
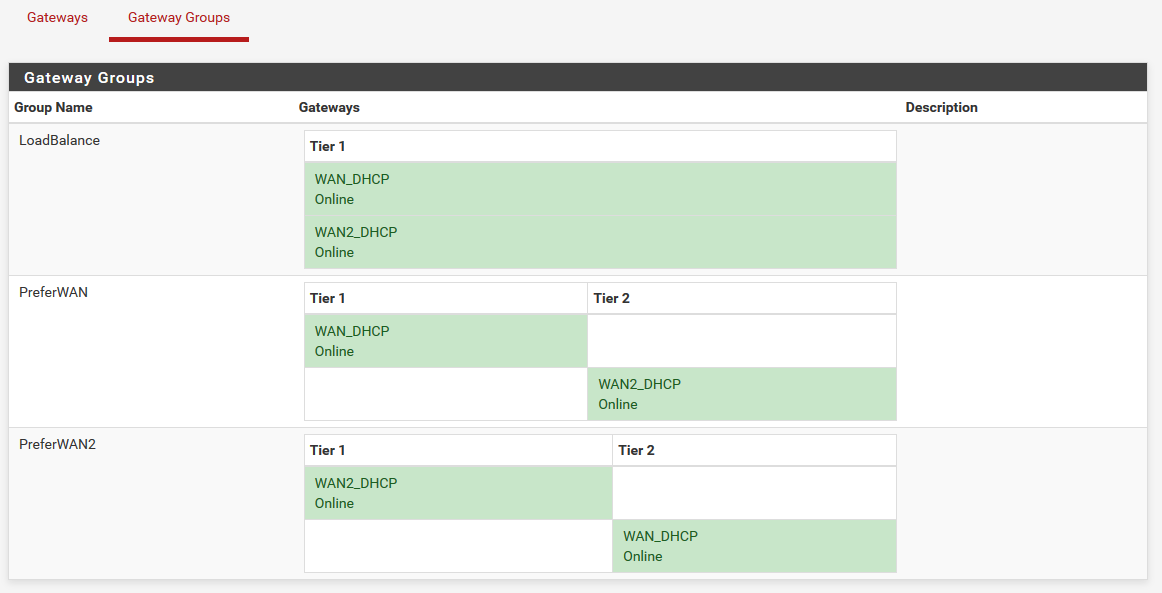
I've been struggling with a problem getting my OpenVPN client to choose the gateway group instead of the default gateway.Here is the configuration for system gateways and gateways groups. The gateway group itself seems to work fine and using it in a firewall rule provides failover between WAN and 4G as expected. (I've set the 4G connection to tier 1 at the moment for testing.)
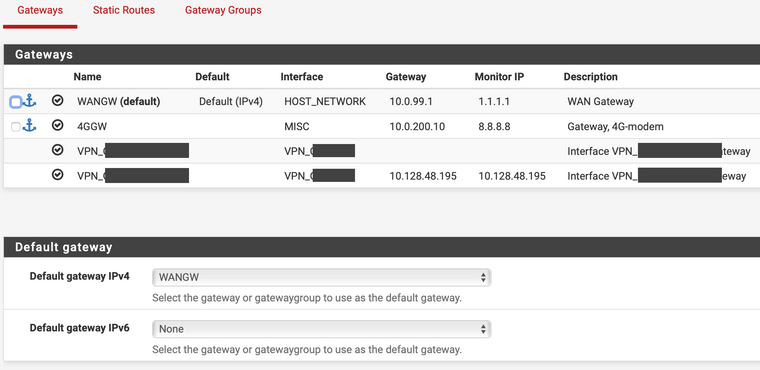
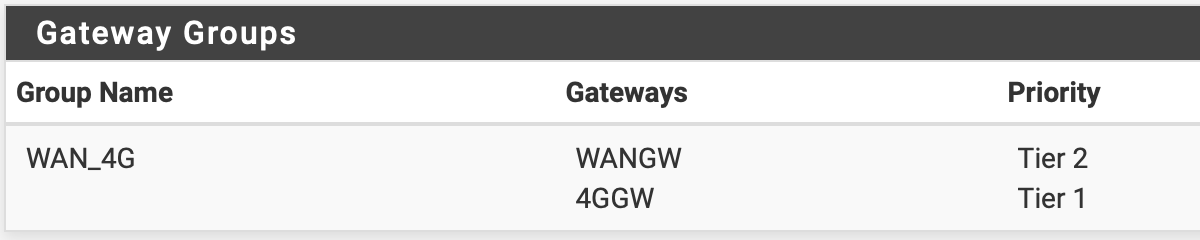
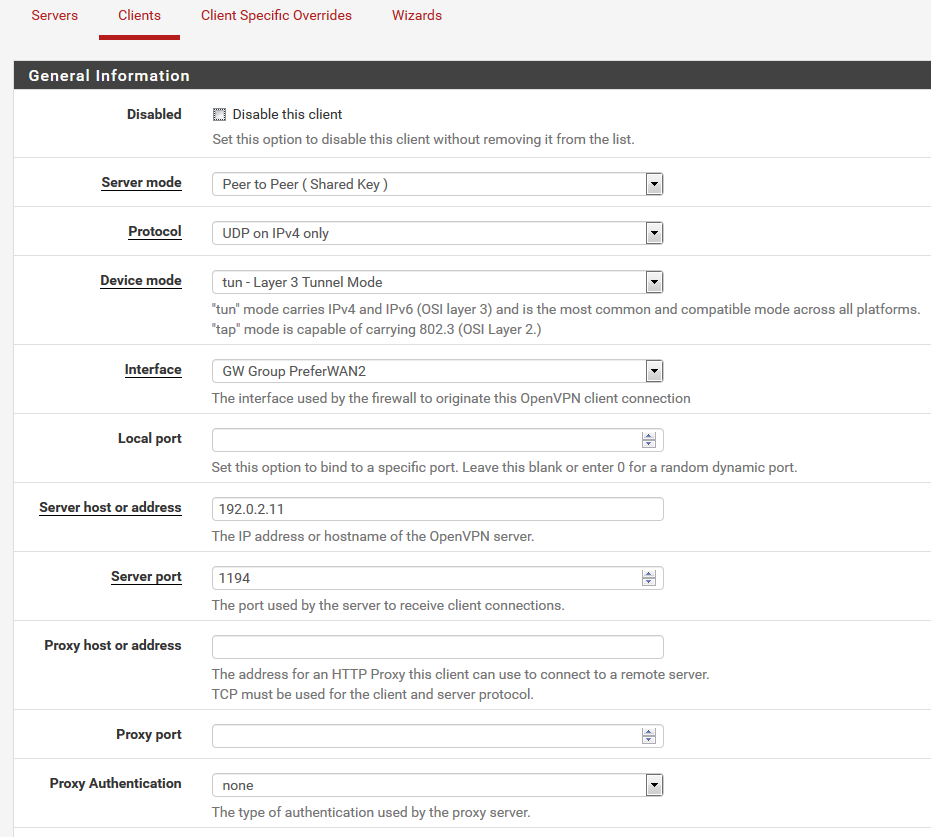
The OpenVPN client also works fine. Here is the topmost part of the configuration.
I've selected the gateway group as interface and expects the client to use the gateway group for failover.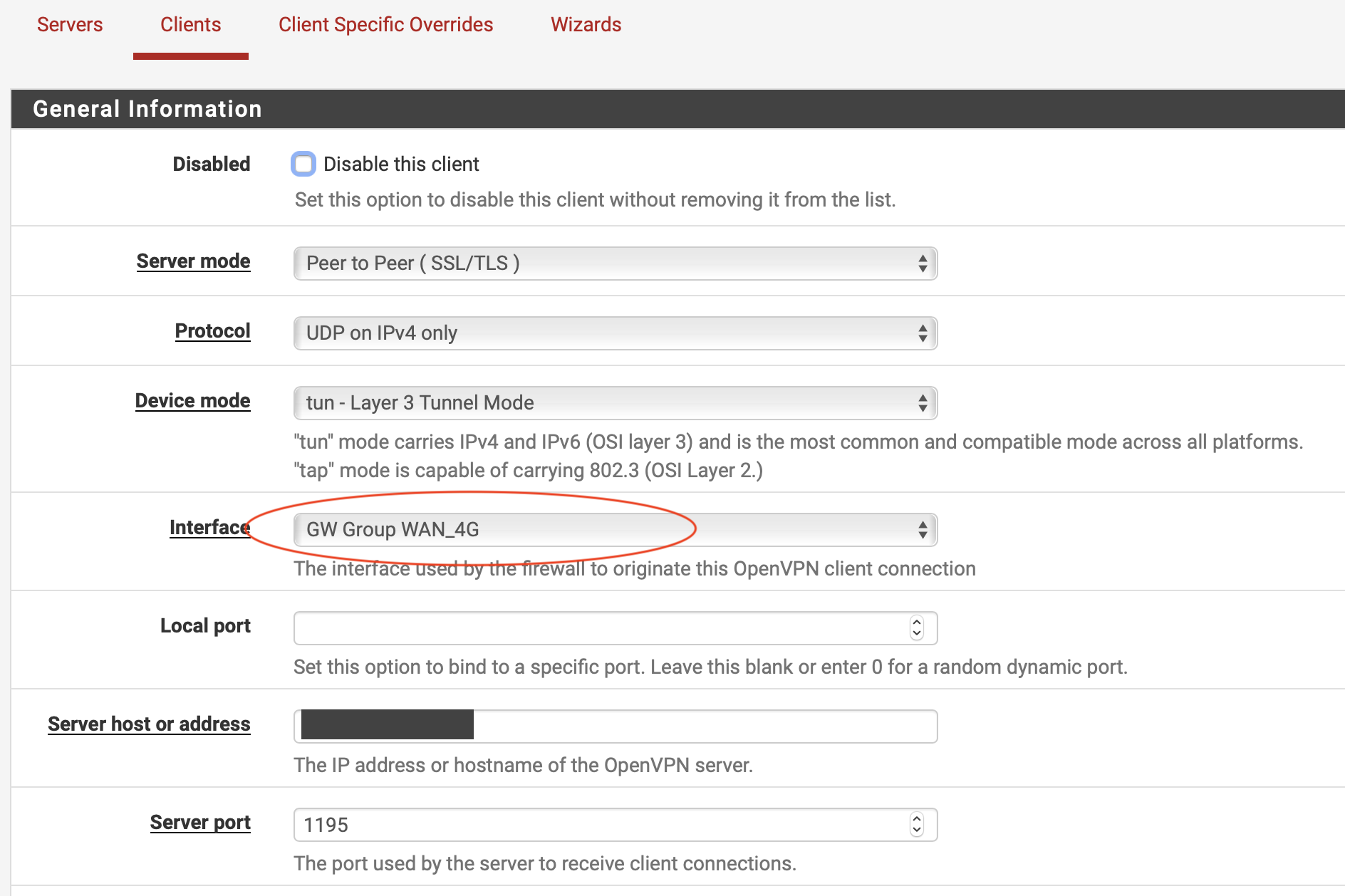
The problem is that it doesn't matter if I change the tiering of WAN and 4G in the gateway group or set any gateway as disabled. The VPN client still uses the WAN gateway to connect to the VPN server (verified by checking the IP in the VPN server log). I've even tried to remove the WAN gateway from the group with no change.
When checking the status of the OpenVPN tunnel, it does choose the correct interface/subnet for connection (10.0.99.6 for WAN or 10.0.200.1 for 4G) but the traffic still exits using the WAN gateway.
If I change the default gateway for pfSense the VPN client follows this change and connects using the expected gateway. If I set the default gateway to the gateway group everything works as expected, but we cannot have all traffic exiting through the 4G connection in case of a problem.Am I missing some part in my configuration or is this a known problem?
Best regards, Arfid
-
No one? :-)
Can this be a bug that should be reported or is it a configuration error on my part? -
Are you running 2.4.4-p3?
Is your OpenVPN Interface assigned?-Rico
-
I just tried this with a fresh 2.4.4-p3 Installation and it worked for me.
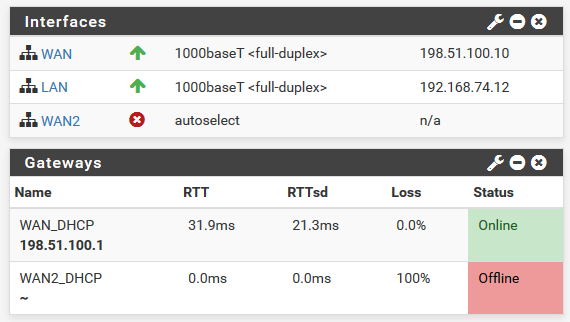
Client Overview: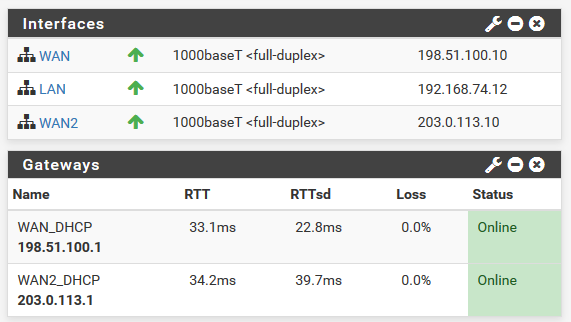
OpenVPN Log Server Side:
Jun 20 11:43:02 openvpn 55634 UDPv4 link local (bound): [AF_INET]192.0.2.11:1194 Jun 20 11:43:02 openvpn 55634 UDPv4 link remote: [AF_UNSPEC] Jun 20 11:43:12 openvpn 55634 Peer Connection Initiated with [AF_INET]203.0.113.10:35961As you see there is the Client WAN2 IP 203.0.113.10 connected.
Now let's cut off WAN2:
OpenVPN Log Server Side:
Jun 20 11:45:01 openvpn 55634 Peer Connection Initiated with [AF_INET]198.51.100.10:16517So there must be something wrong with your Configuration or Installation.
-Rico
-
@rico I'm having this same issue. My setup is very similar to your example. The problem is that I do not want my OpenVPN client to connect over WAN2 because it is an expensive 4G connection and I pay per GB used. There are only a few devices that I want to be able to fail over if the main WAN1 goes down. In your example your OpenVPN client did just that; it failed over to the alternate WAN. Is there anyway to prevent this from happening?
Right now I have my WAN group as the main gateway (with the failover option set on the group) and rules to allow some devices to use it and others to not. All that is working perfect, the only problem is that the VPN will reconnect on WAN2 and my bill goes through the roof. Adding even more pain, when WAN1 comes back online the VPN connection doesn't switch back.

-
@gremblin Hi, I'm sorry I can't help. But I don't have this setup in pfSense any longer.
-
P pigbrother referenced this topic on
