XG-7100 rule failing to match traffic on LAN ingress
-
We have been having a long term issue with the system. It's been random, so it took us a while to believe it was real, and then to track it back to the firewall device. Yes, it is completely random. One moment traffic will be allowed, the next it will be blocked. I know this is not possible. That doesn't solve my problem.
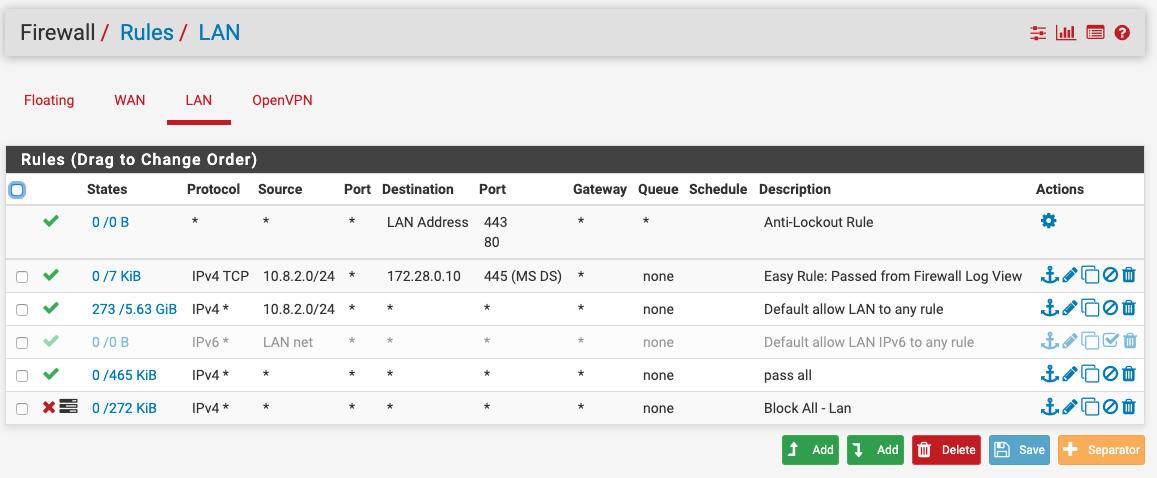
The basic issue is ingress traffic to the LAN port is being blocked, and it should not be. I have tried everything to get it to stop, but it still continues. We originally had a simple default pass rule to allow anything on the LAN subnet to pass. The firewall is running an almost fresh config.
We tried creating two new rules. The first matches all traffic to pass. The second matches all traffic and blocks it then logs it.
We continue to find traffic matching the second rule.
Sample block event:
48,,,1558475967,lagg0.4091,match,block,in,4,0x0,,128,17847,0,DF,6,tcp,164,10.8.2.120,172.28.0.10,60354,445,124,PA,4089409933:4089410057,342856039,254,,
1558475967 is the Block all-Lan rule in the above screen shot.
We have also tried switching to conservative mode, resetting states, fully patching to current, and rebooting.
-
48,,,1558475967,lagg0.4091,match,block,in,4,0x0,,128,17847,0,DF,6,tcp,164,10.8.2.120,172.28.0.10,60354,445,124,PA,4089409933:4089410057,342856039,254,,
1558475967 is the Block all-Lan rule in the above screen shot.
TCP:PA
Your pass rule will pass TCP:S(YN) and associated in-state traffic.
Your block rule will block out-of-state, asymmetric, etc traffic.
https://docs.netgate.com/pfsense/en/latest/firewall/troubleshooting-blocked-log-entries-for-legitimate-connection-packets.html#troubleshooting-blocked-log-entries-for-legitimate-connection-packets