Winston Privacy Device - Which Technology?
-
@KOM said in Winston Privacy Device - Which Technology?:
Back to Winston, he did say that only small packets are routed through their network while data went direct so that may or may not affect who gets blamed for criminal activity.
Correct. Large data transfers continue to take place over local transports, not p2p. If customers are worried about this aspect, we do allow them to switch off p2p routing and make use of the other privacy protections only (which are not weak, by any means).
I am curious if anyone has suggestions that are not as "all-or-nothing" as this. For instance, we have been talking about the possibility of allowing users to specify sharing policies (and shipping with thoughtful default ones), such as streaming, pornography, illegal content and other blocklists.
Another highly requested feature is to allow users to set up their own private named networks that they can share with friends and family only.
Still another is the ability to dial down the amount of traffic sent out on the network and take advantage of traffic shaping (one research study I've read indicated that as little as 3% false traffic is sufficient to hinder IoT device identification).
I appreciate the thoughtful discussion!
-
There is what you think the AUP says and what they care about, and what it says... And what the ISP can do to their users - like just freaking kill their service when they see 1 users overall usage jump up because they are routing other traffic over their connection.
Or some other "privicacy device" does something against users ISP AUP and the ISP cracks the whip on the user, etc..
Once you have the OK from the isp to do what your doing, then you can hawk you boxes to those users... But until then... Its sure could be a huge disaster for a lot of users..
And targeting "non tech" users makes it worse if you ask me... Atleast if the person is technical they understand what they are doing - and what it means, etc. like running a tor exit node... Billy bob facebook user is not going to run a tor exit node out of the blue... But grandma could for sure buy your box and plug it in it seems ;) Or atleast that is your goal?
-
We are in active discussions with two ISPs. There is strong interest in reseller partnerships and my personal experience has been that they want to be perceived as being any more anti-privacy than is already the case.
We have been using the device internally for about 17 months and have had quite a few field units out there since September (8 months) with zero reported issues from ISPs. That should perhaps be expected, given that it's impossible to discern the source of specific traffic.
-
@WinstonPrivacy said in Winston Privacy Device - Which Technology?:
few field units out there since September
There is a huge difference between a few in the field and 1,000 if not 10's of Ks of them on a ISP network that figures it out and gets freaking pissed ;)
You want to hawk your "security" box to the masses that don't understand it that is fine - route their traffic to your network..
But meshing these things and routing billy's traffic over karen's connection is BAD JUJU just waiting to hit the fan if you ask me.. Especially first time kevin moves any sort of kiddy you know what about thinking he is "safe" behind your security device..
given that it's impossible to discern the source of specific traffic.
Any ISP can for sure tell that billy is going to alot of crazy places for a home of 2 people ;) And can for sure tell something is up and take a closer look when lets say 1000 of their users usage just went up by 30% and is just all over the place vs just karen's typical streaming netflix usage..
So how is you state
As an example, let's say your iSP wants to record your internet activity (most do)
But then you say you have ISP that are saying it going to be ok to put these boxes on their network - which will prevent them from tracking their own users..
-
Any chance we can get instructions how to load PfSense onto the HW we purchased?
-
Um..... that seems very unlikely? Especially since reading back they are using ARM (MIPS?).
Just a spam comment 2 years later?
-

-
@stephenw10 Woot
-
-
@jwt It was more the non standard ARM hardware

-
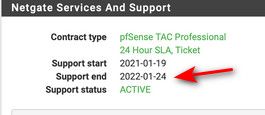
@stephenw10 man you need to update your support contract ;) its expiring soon..
-
@nogbadthebad it’s not that different from the 1100…
-
@kom Check out iot inspector to see what lurks in your home https://inspector.engineering.nyu.edu/
-
@parry said in Winston Privacy Device - Which Technology?:
https://inspector.engineering.nyu.edu/
Not a fan of doing arp spoofing.. The tool might be the greatest thing since sliced bread for collecting info.. But arp spoofing to get devices to send traffic to some device on your network other than where it should go could be seen as "bad" as well.
Why can not not just take a sniff of their traffic and load it into the tool? Is that an option? I don't see it anywhere. I also see that the linux version was suppose to be ready back in may of 2020, covid kill work on this project?
Or better yet ability to do a span port and let the tool see all the traffic, without having to spoof any macs..
-
@johnpoz
Hey John, you ever worked at a University ;) Er nothing is quite as fast as you want it to be. I agree some of that stuff needs to be updated, but if you like shoot him a note about your ideas. These folks actually listen to others. Ironically there is a company in Germany called IoT Inspector https://www.iot-inspector.com/ that has absolutely nothing to do with the academic work.
