HAproxy custom ACL results in 503 error.
-
I created a custom ACL named ACL12 to check for the presence of a cookie with:
req.cook_cnt(organizrLanguage) gt 0The cookie is present when checking in developer tools in the browser. Generated HAproxy config shows:
acl ACL12 var(txn.txnhost) -m beg -i req.cook_cnt(organizrLanguage) gt 0 use_backend Fileshare_ipv4 if ACL12Anyone done something similar? Where am I going wrong?
-
@wontbeherelong
Looks to me like you chose "host begins with" instead of "custom acl" ? -
I did have another ACL with 'host begins' for that front end. I thought that ACL's with different names were combined as 'and' and not 'or' statements. I'm now very confused, because I removed that ACL and tried using only:
req.cook_cnt(mycookiename) -m foundAt this point, I get no 503 and can access the page. BUT, if I clear all cookies and go straight to the subdomain without the cookie being present, I can also access the page. Here's a screenshot of my frontend ACl:
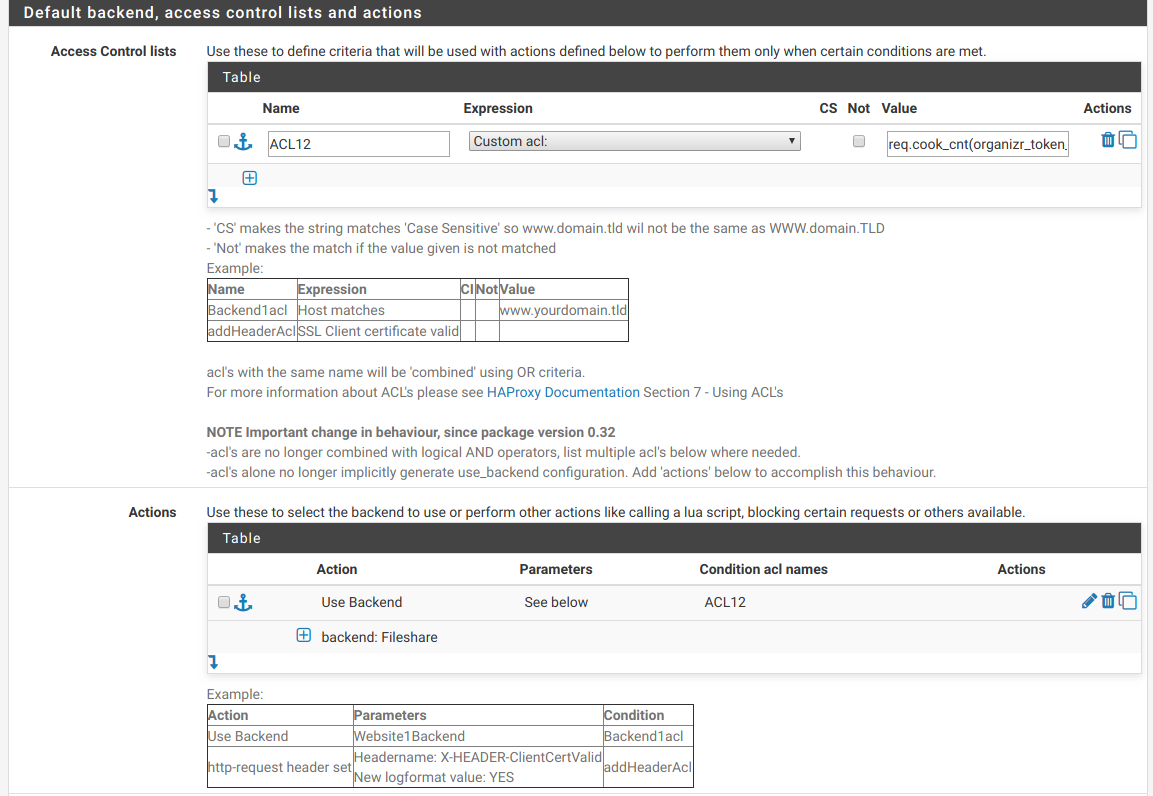
How is this connecting without ACL12 being satisfied as there is no cookie? My frontend settings clearly show 'Backend Fileshare if(ACL12)?
-
@wontbeherelong
To combine 2 acls with different names you do need to put both the names as acl's behind the action. They would indeed combine as 'AND' then. Unless specifically written with a "||" OR between the names.Can you share the complete haproxy.cfg ? The acl above looks like it should check for existence of the cookie. But i wonder if perhaps there are other acl's or other frontends or default backend that might point to the same server. Also are you sure the cookie isn't already returning automatically by only visiting a login page perhaps?
-
@PiBa
Attaching my config (minus a few unnecessary ssl params etc). Unfortunately, I can't post it directly as it was flagged as spam and I also can't send a P.M.
haproxy.txt -
@wontbeherelong
There seems no way around ACL12 to make it to the FileServer backend.I wonder now if '-m found' is the proper action for a fetch that returns the number of matches, probably it should be 'gt 0' instead like you had before.?
-
@PiBa
gt 0 gets me back to 503. Cookie name is copied from chromium developer tools and matches what I find in firefox. So, either i use -m found and anyone can access the subdomain, or gt 0 gives me 503. I have no idea where to go from here. Any idea what is happening? If -m found directs me is the cookie valid? But in which case, why is it accessible using a sub.domain without an ACL present? -
@wontbeherelong
The 'req.cook_cnt(' takes the NAME of a cookie to search for, not its value.So try with only the part before the = and see if that creates a positive match. b.t.w. i verified that this does work for me with regard to the acl actually matching with the 'gt 0' value, and a manually inserted cookie:
acl ACL12 req.cook_cnt(organizr_token_b112adac-dbcb-41c1-9ed6-e8eb190763f2) gt 0 http-request set-header ACL12cookieFound YES12 if ACL12 -
Thank you so much, I really appreciate you helping me out on this one - it needed a fresh set of eyes! The cookie length was so long that I hadn't noticed the = sign, so like you said I was using the value in addition to the name. Using my original gt 0 with the proper cookie name does indeed work, and it's behaving exactly as I'd hoped. Fantastic!
-
I know this is an older post/thread, but I am running into the issue with HAProxy and Organizr not getting along. I am new to HAProxy and not really sure how to implement the fix here. Would anyone be willing to explain it to me in detail?