Firewall rule not matching fragmented UDP packets
-
Hi everyone,
PfSense Version is 2.4.4-RELEASE-p3
We have an issue where Firewall rules on our IPSEC interface dont match fragmented packets but work fine with unfragmented packets.
The firewall rule consists of an alias list of subnets in the Source field, and a alias list of LAN-Side IP addresses in the Destination field. See below:
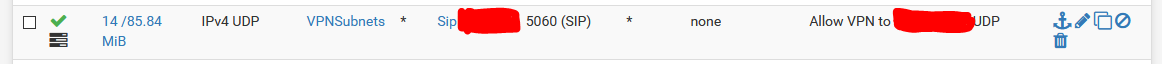
I have also tried the rule without the Alias lists (specifying the problematic source subnet and destination addresses directly) and it makes no difference to the behaviour.
When we have an allow all IPv4 rule at the bottom the firewall reassembles the fragmented packets and sends them out as a single packet on the LAN side and everything works fine (observed with packet caputres on PfSense IPSEC interface and on the target host).
We would prefer not to have to rely on a Allow All rule to pass this traffic and would like to remove it. But if we do the fragmented packets get blocked.
Packets without the IPv4 fragmentation flag match the more specific rule and pass fine.
Packets WITH the IPv4 fragmentation flag only match to the Allow All IPv4 Rule.
Sample from Firewall Logs below:
1426368194 = Allow All IPv4 Rule (notice the + flag for fragmentation) matches:
Jun 25 16:45:26 gateway1 filterlog: 120,,,1426368194,enc0,match,pass,in,4,0x60,,63,4299,0,+,17,udp,1020,10.B.B.13,10.A.A.5,5060,5060,1443
Jun 25 16:46:12 gateway1 filterlog: 120,,,1426368194,enc0,match,pass,in,4,0x68,,63,60835,0,+,17,udp,1020,10.B.B.10,10.A.A.5,5060,5060,1437
Jun 25 16:46:54 gateway1 filterlog: 120,,,1426368194,enc0,match,pass,in,4,0x68,,63,60845,0,+,17,udp,1020,10.B.B.10,10.A.A.5,5060,5060,14381556931289 = Specific Subnet / Address / Ports Rule - no frag flag matches:
Jun 25 15:56:07 gateway1 filterlog: 103,,,1556931289,enc0,match,pass,in,4,0x60,,63,4141,0,none,17,udp,853,10.B.B.13,10.A.A.5,5062,5060,833
Jun 25 16:45:41 gateway1 filterlog: 103,,,1556931289,enc0,match,pass,in,4,0x60,,63,4300,0,none,17,udp,1184,10.B.B.13,10.A.A.5,5062,5060,1164
Jun 25 20:20:06 gateway1 filterlog: 103,,,1556931289,enc0,match,pass,in,4,0x68,,63,45980,0,none,17,udp,497,10.B.B.11,10.A.A.5,5060,5060,477
Jun 25 20:20:08 gateway1 filterlog: 103,,,1556931289,enc0,match,pass,in,4,0x68,,63,51683,0,none,17,udp,834,10.B.B.17,10.A.A.5,5060,5060,81410.B.B.0/24 is the source subnet on the other side of the IPSEC tunnel.
10.A.A.0/24 is the LAN subnet.Is there any way to get the more specific rule to match the fragmented packets as well?
Thanks,
Nic. -
I can confirm this behaviour on 2.4.4-RELEASE-p3. It was working with 2.4.4-RELEASE-p2 before.
Some rules do not match anymore, which is not cool...BR
Steffen