Prohibit communication between VLANs
-
Hi guys, I'm setting up five VLANs piggybacking on a single physical LAN interface.
I am trying to stop the VLANs from talking to each other as well as being able to reach the LAN (management) network. For example:
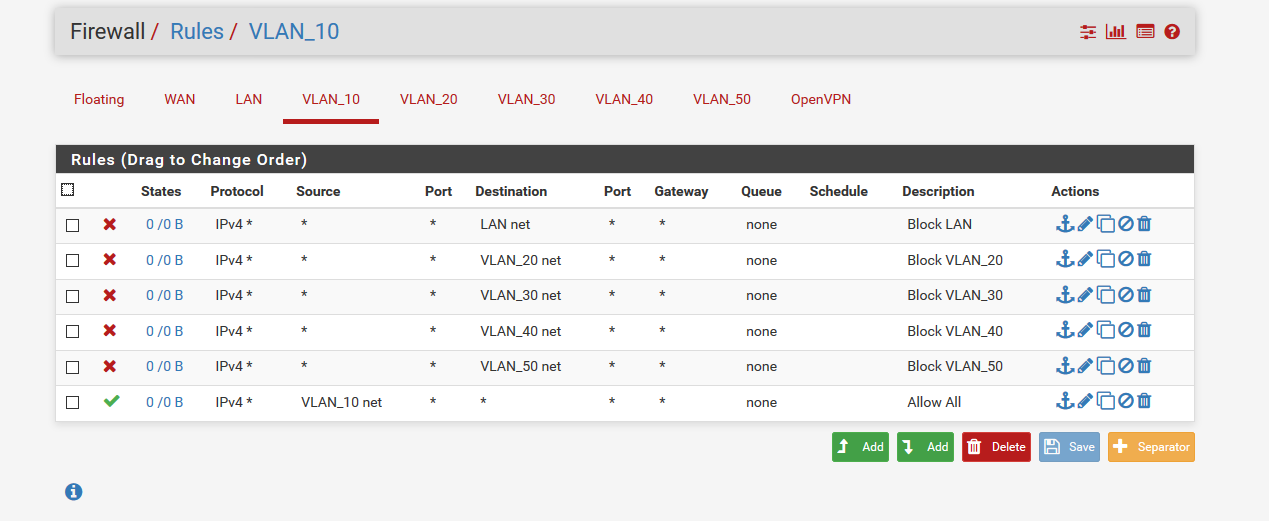
Now sadly at this point I haven't got any devices available to connect to one of these networks so I am only using the ping function of pfSense Diagnostics. And although the rules appear to be fine, I can still ping the LAN address 172.16.40.1 from a VLAN source address.
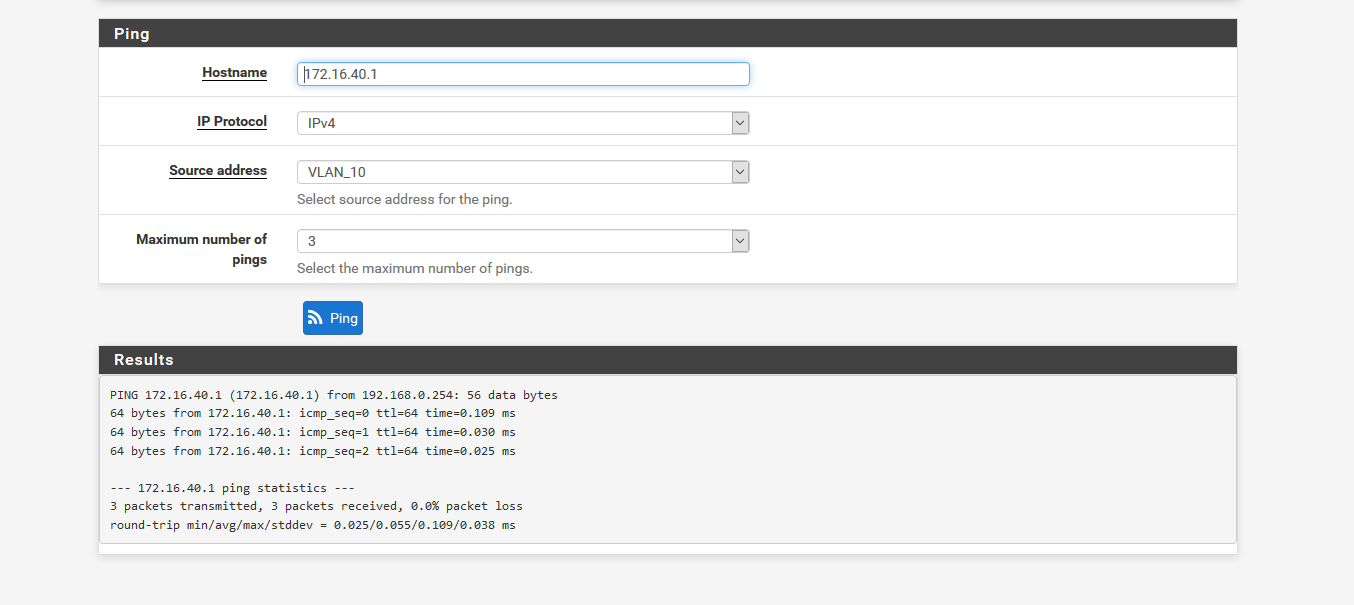
What am I doing wrong?
BTW. I followed this guide to sert up the VLANs and rules:
https://www.youtube.com/watch?v=b2w1Ywt081o -
No user rule can block traffic from pfSense itself. That is to say, you cannot test your rules with the ping function of pfSense.
Instead of adding a filter rule for each unique of your networks you can add all network to a single alias and use this at destination in a single block rule.
Best practice is to add an alias and add all RFC 1918 networks to it and use this one. So you're save as well, if you add a VLAN or change a network. -
@viragomann said in Prohibit communication between VLANs:
No user rule can block traffic from pfSense itself. That is to say, you cannot test your rules with the ping function of pfSense.
Ha! So I am not going mad then!
@viragomann said in Prohibit communication between VLANs:
Instead of adding a filter rule for each unique of your networks you can add all network to a single alias and use this at destination in a single block rule.
Best practice is to add an alias and add all RFC 1918 networks to it and use this one. So you're save as well, if you add a VLAN or change a network.Yes, that would have saved me a lot of work lol. I have been setting the rulesets manually for each VLAN!
-
Another way to save time when roll out similar rules on multiple interfaces is to use the copy function:
Just hit the button, a copy of the rule will be opened. Then change the interface. Together with the RFC1918 alias that's all you have to do to add the rules to another interface.
-
@viragomann Excellent! Thanks!
-
Yet another way to save time would be to put your networks in an alias and use that in a single rule vs multiple rules.
I have an alias with all of rfc1918 space in it, so if I want to block a specific vlan from talking to other vlans I just use that as the destination..
There are multiple ways to skin a cat ;)