Setting up IPsec VPN pfsense to dsr dlink-1000 router
-
Hi please help I'm a newbie in setting up VPN,, And I need to set up an IPsec VPN from pfsense to dsr dlink-1000 router the parameters that I'm using:
Setup:
PFSENSE (WAN)= 125.5.78.228 (GW) = 125.5.78.227
DLINK ROUTER (WAN)= 202.175.233.250 (GW) = 202.175.233.249(PFSENSE)
For Phase1
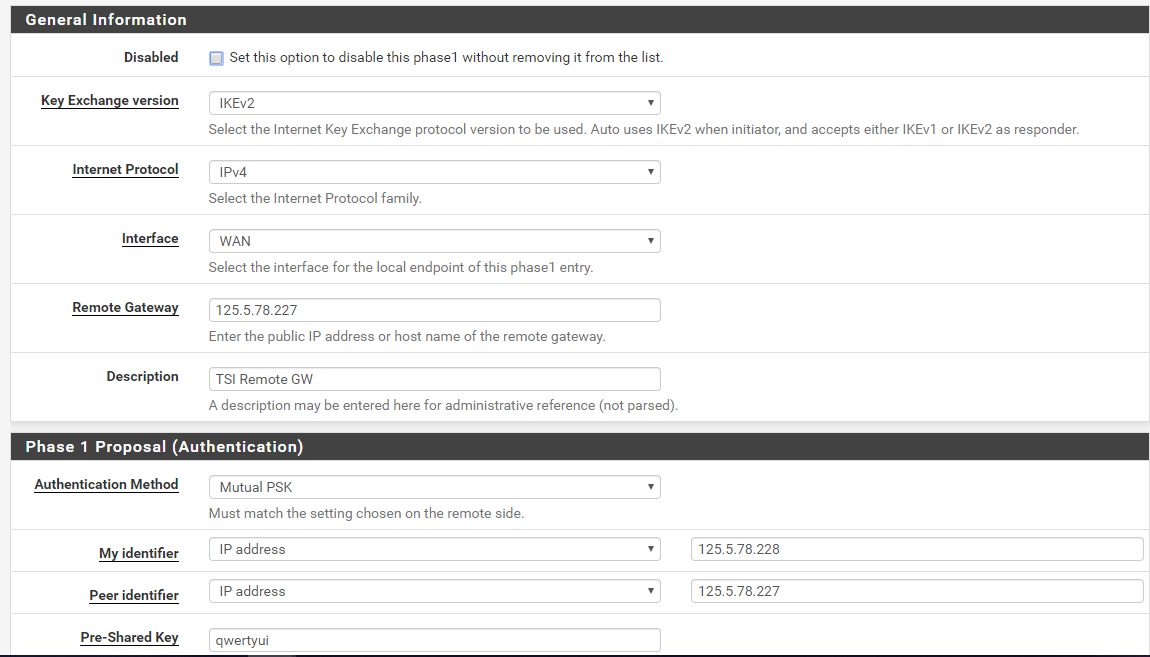
Remote Gateway: 202.175.233.250
My Identifier: 125.5.78.228
Peer Identifier: 202.175.233.250
Proposal (Authentication)
Key Exchange protocol: IKEv2
Authentication Method: Mutual PSK
Negotiation Mode: Main
Pre-shared Key: 12345678
(Encryption Algorithm)
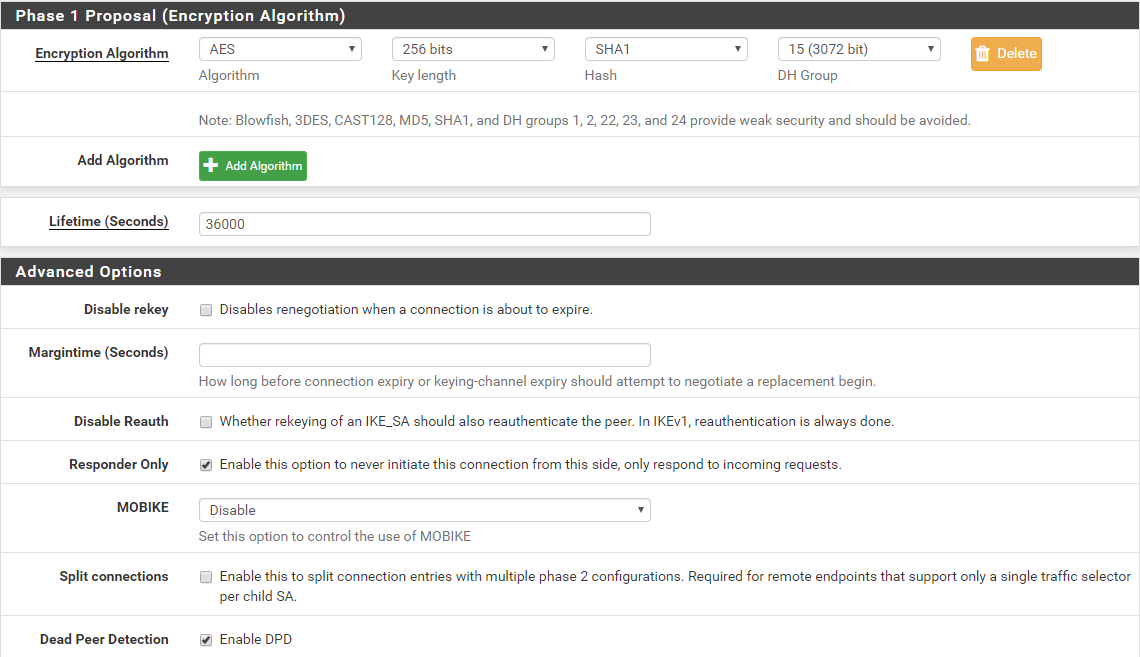
Encryption: AES 256
Hash: SHA384
DH Group: 15(3072)
Lifetime(Seconds):10800
Dead Peer Detection: ONPhase 2
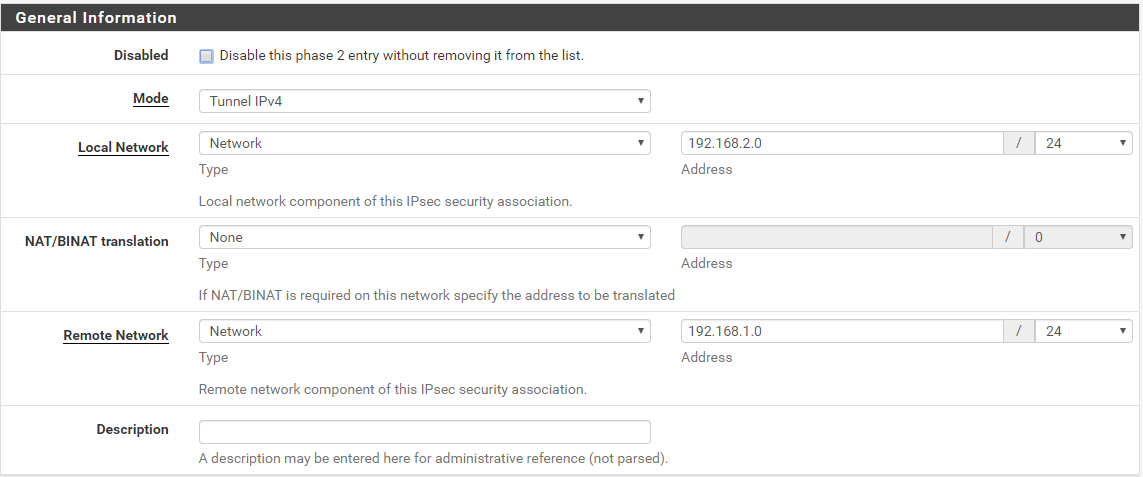
Mode: Tunnel IPV4
Local Network: 192.168.1.0/24
NAT: N/A
Remote Network: 192.168.2.0/24
Protocol: ESP
Encryption Algorithm: AES 256
Hash Algorithm: SHA384
Lifetime: 10800
PFS Key Group: offAnd for the
DLINK DSR-1000 router
I also put desame parameters.And the Error that getting from DLINK logs is:
"Racoon 1922- -phase 1 negotiation failed due to time up for 125.5.78.228(500)"
"Racoon 1922- -invalid SA protocol type:0"
"Racoon 1922- -phase 2 negotiation failed due to time up waiting for phase1." -
Does your Dlink support IPSec v2?
-
Hi periko thanks what do you mean IPSEC v2? the IKE v2? if thats what you mean its a yes my dlink supports IPSec v2.
It appears that I already found my mistake. I saw that my DLINK PFS cant handle DH 15 my only options are DH 1, 2, and 5. On phase 2.
-
Just adding this system logs on my pfsense please help. my problem still not fixed.
Jul 24 11:19:00 charon 05[JOB] <80> deleting half open IKE_SA with 125.5.78.227 after timeout
Jul 24 11:19:00 charon 05[IKE] <80> IKE_SA (unnamed)[80] state change: CONNECTING => DESTROYING
Jul 24 11:19:02 charon 14[CFG] vici client 1118 connected
Jul 24 11:19:02 charon 14[CFG] vici client 1118 registered for: list-sa
Jul 24 11:19:02 charon 14[CFG] vici client 1118 requests: list-sas
Jul 24 11:19:02 charon 05[CFG] vici client 1118 disconnected
Jul 24 11:19:03 charon 11[NET] <82> received packet: from 125.5.78.227[500] to 125.5.78.228[500] (432 bytes)
Jul 24 11:19:03 charon 11[ENC] <82> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_D_IP) N(NATD_S_IP) V V V V ]
Jul 24 11:19:03 charon 11[CFG] <82> looking for an IKEv2 config for 125.5.78.228...125.5.78.227
Jul 24 11:19:03 charon 11[CFG] <82> candidate: %any...%any, prio 24
Jul 24 11:19:03 charon 11[CFG] <82> candidate: 125.5.78.228...125.5.78.227, prio 3096
Jul 24 11:19:03 charon 11[CFG] <82> found matching ike config: 125.5.78.228...125.5.78.227 with prio 3096
Jul 24 11:19:03 charon 11[ENC] <82> received unknown vendor ID: 81:0f:a5:65:f8 14:36:91:05:d7:06:fb:d5:72:79
14:36:91:05:d7:06:fb:d5:72:79
Jul 24 11:19:03 charon 11[ENC] <82> received unknown vendor ID: 90:cb:80:91:3e:bb:69:6e:08:63:81:b5:ec:42:7b:1f
Jul 24 11:19:03 charon 11[ENC] <82> received unknown vendor ID: 4a:13:1c:81:07:03:58:45:5c:57:28:f2:0e:95:45:2f
Jul 24 11:19:03 charon 11[ENC] <82> received unknown vendor ID: af:ca:d7:13:68:a1:f1:c9:6b:86:96:fc:77:57:01:00
Jul 24 11:19:03 charon 11[IKE] <82> 125.5.78.227 is initiating an IKE_SA
Jul 24 11:19:03 charon 11[IKE] <82> IKE_SA (unnamed)[82] state change: CREATED => CONNECTING
Jul 24 11:19:03 charon 11[CFG] <82> selecting proposal:
Jul 24 11:19:03 charon 11[CFG] <82> proposal matches
Jul 24 11:19:03 charon 11[CFG] <82> received proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536
Jul 24 11:19:03 charon 11[CFG] <82> configured proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536
Jul 24 11:19:03 charon 11[CFG] <82> selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536
Jul 24 11:19:03 charon 11[ENC] <82> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(MULT_AUTH) ]
Jul 24 11:19:03 charon 11[NET] <82> sending packet: from 125.5.78.228[500] to 125.5.78.227[500] (376 bytes)Jul 24 11:18:45 charon 15[CFG] <81> selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536
Jul 24 11:18:45 charon 15[ENC] <81> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(MULT_AUTH) ]
Jul 24 11:18:45 charon 15[NET] <81> sending packet: from 125.5.78.228[500] to 125.5.78.227[500] (376 bytes)
Jul 24 11:18:50 charon 11[CFG] vici client 1116 connected
Jul 24 11:18:50 charon 11[CFG] vici client 1116 registered for: list-sa
Jul 24 11:18:50 charon 15[CFG] vici client 1116 requests: list-sas
Jul 24 11:18:50 charon 07[CFG] vici client 1116 disconnected
Jul 24 11:18:56 charon 08[CFG] vici client 1117 connected
Jul 24 11:18:56 charon 10[CFG] vici client 1117 registered for: list-sa
Jul 24 11:18:56 charon 10[CFG] vici client 1117 requests: list-sas
Jul 24 11:18:56 charon 08[CFG] vici client 1117 disconnected -
I really dont get why im getting this.
Jul 24 11:46:08 charon 05[CFG] <83> configured proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536
Jul 24 11:46:08 charon 05[CFG] <83> selected proposal: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536
Jul 24 11:46:08 charon 05[ENC] <83> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(MULT_AUTH) ]
Jul 24 11:46:08 charon 05[NET] <83> sending packet: from 125.5.78.228[500] to 125.5.78.227[500] (376 bytes) -
it is better if you post screenshot of what you have done, both device
-
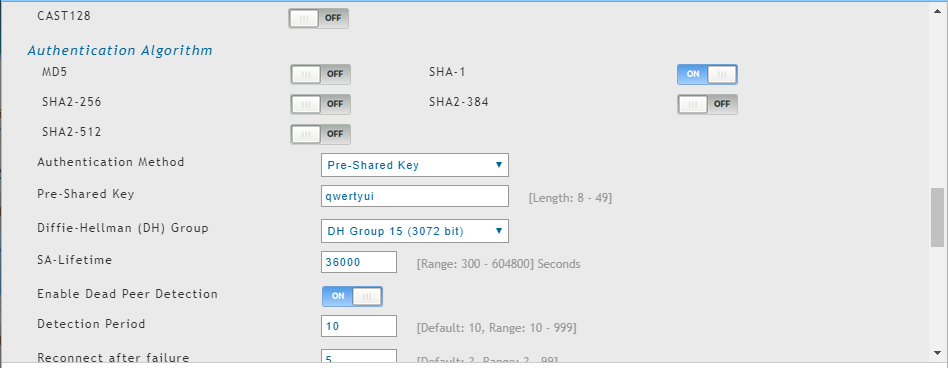
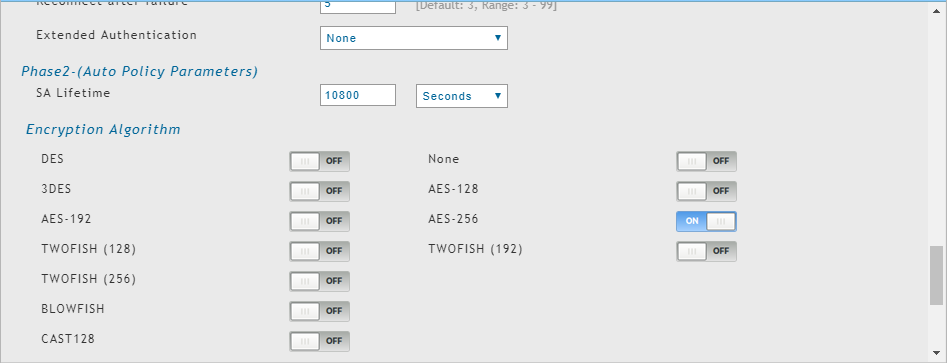
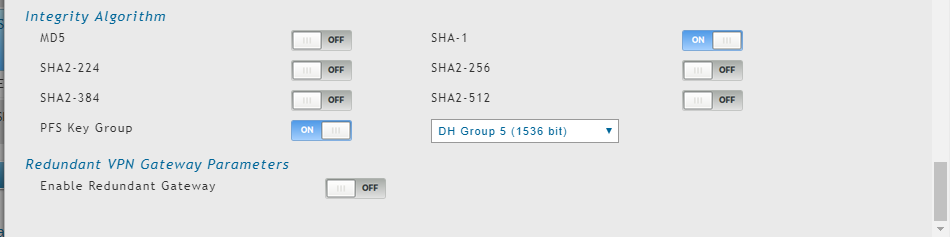
This is my config on pfsense:
phase 1:
phase 2:
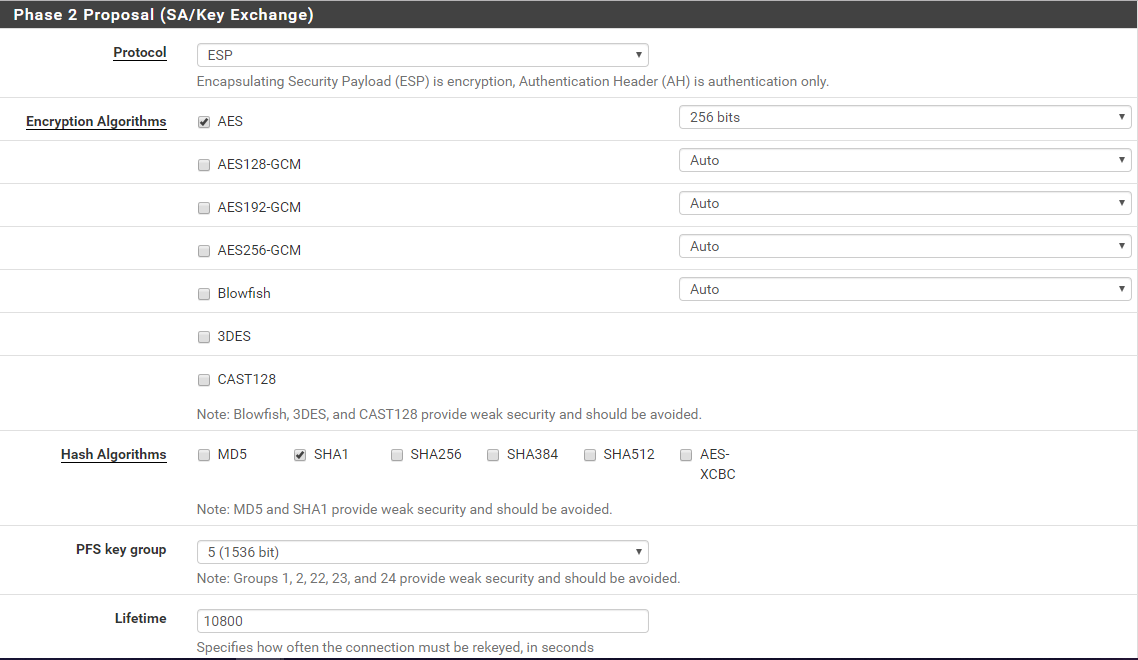
-
And here's my config on my dlink router:
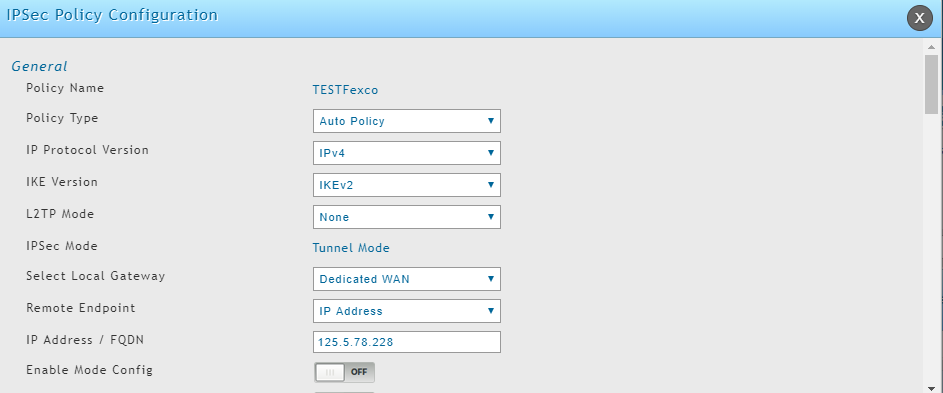
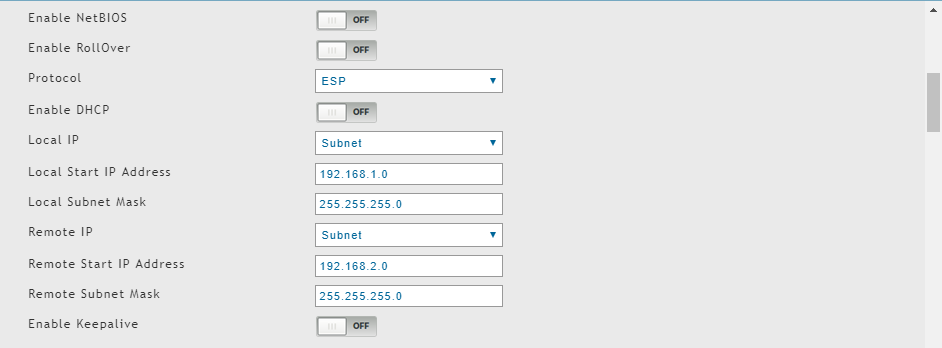
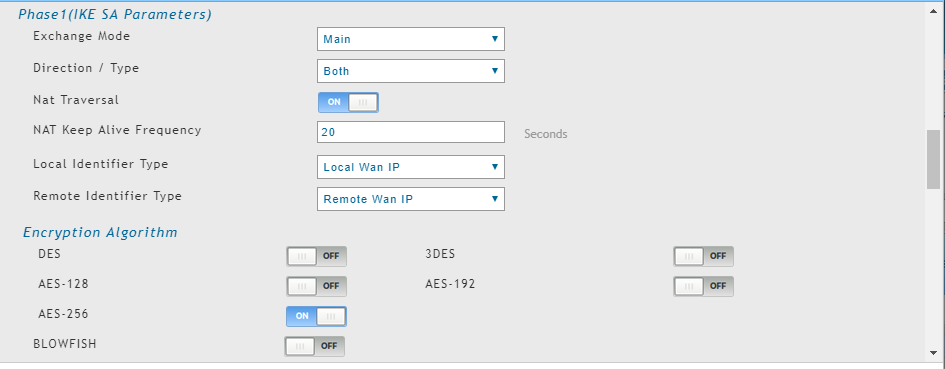
-
And when I'm initiating the VPN connection from dlink to pfsense this is what I get:
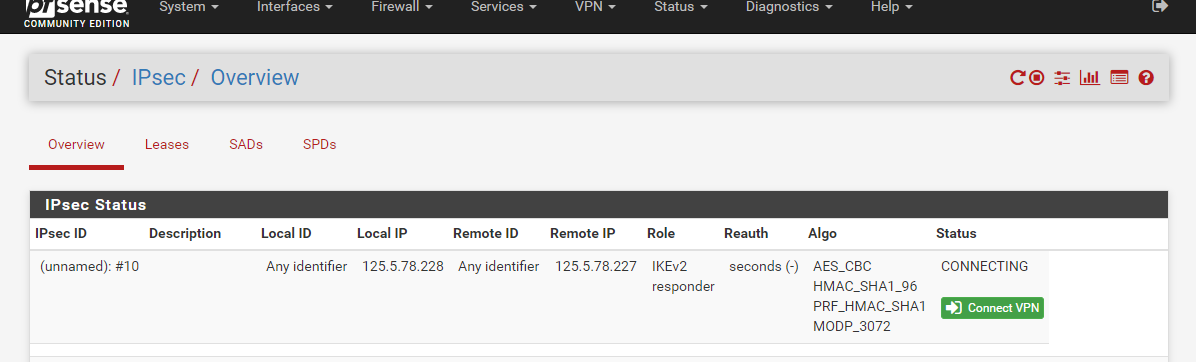
but when im initiating the vpn on pfsense to dlink this is what I only get:
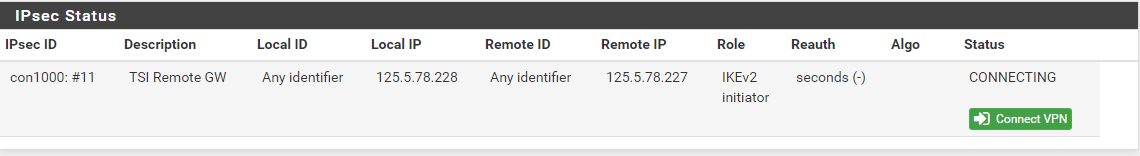
-
-
@Konstanti hi thank you but still it didnt work wait ill try to get the file that you wanna see.
-
i don't think you need to enable nat traversal on phase 1
-
@kiokoman hi yes i just left it on but i dont think thats the problem,, here's the file that you're asking I just improvised so forgive me haha.
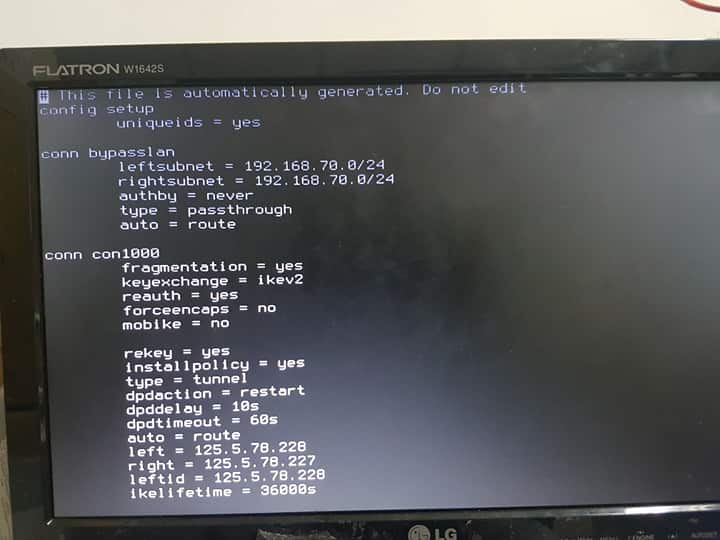
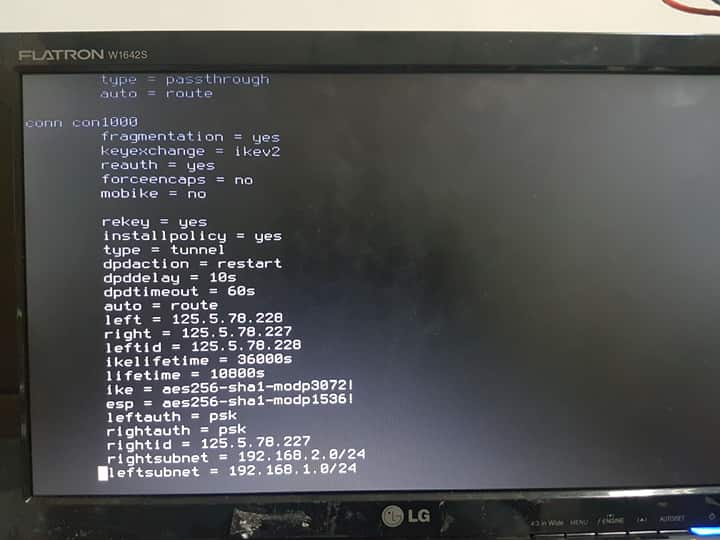
-
remote ip is 202.175.233.250
why do you have 125.5.78.227 on pfsense log? -
@kiokoman sorry the first part was my first config and right now I changed it. to make it simple.
-
are port udp 500 and 4500 open on 125.5.78.227 ?
228 is filtered but 227 result closed to me -
@kiokoman let me try hang on. I'm also confused about this dlink router.
-
Yeah from the first IPsec log it appears .227 is not receiving the traffic / allowing it in.
-
@kiokoman Hi sir I think I just need to open port 500 because I dont do NAT traversal and this port 4500 is for NAT traversal right?
-
@kiokoman right now I'm getting this logs from pfsense
09[NET] <10> received packet: from 125.5.78.227[500] to 125.5.78.228[500] (508 bytes)Jul 29 10:08:23 charon 09[ENC] <10> parsed IKE_SA_INIT request 0 [ SA KE No V ]
Jul 29 10:08:23 charon 09[CFG] <10> looking for an IKEv2 config for 125.5.78.228...125.5.78.227
Jul 29 10:08:23 charon 09[CFG] <10> candidate: 125.5.78.228...125.5.78.227, prio 3100
Jul 29 10:08:23 charon 09[CFG] <10> found matching ike config: 125.5.78.228...125.5.78.227 with prio 3100
Jul 29 10:08:23 charon 09[ENC] <10> received unknown vendor ID: af:ca:d7:13:68:a1:f1:c9:6b:86:96:fc:77:57:01:00
Jul 29 10:08:23 charon 09[IKE] <10> 125.5.78.227 is initiating an IKE_SA
Jul 29 10:08:23 charon 09[IKE] <10> IKE_SA (unnamed)[10] state change: CREATED => CONNECTING
Jul 29 10:08:23 charon 09[CFG] <10> selecting proposal:
Jul 29 10:08:23 charon 09[CFG] <10> proposal matches
Jul 29 10:08:23 charon 09[CFG] <10> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_3072
Jul 29 10:08:23 charon 09[CFG] <10> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_3072
Jul 29 10:08:23 charon 09[CFG] <10> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_3072
Jul 29 10:08:23 charon 09[ENC] <10> generating IKE_SA_INIT response 0 [ SA KE No N(MULT_AUTH) ]
Jul 29 10:08:23 charon 09[NET] <10> sending packet: from 125.5.78.228[500] to 125.5.78.227[500] (512 bytes)