OpenVPN slow AES-NI
-
Hey people,
I have bought some days ago an net qotom device with an i7-7300u specialy for the pfSense.
My purpose was to create a perfect pfSense with a higher output of OpenVPN trough the aes-ni suport.After days of testing I run out of ideas. The output remains at 90k down and the strange thing is... the up is sometimes at 180k o.O
The CPU usage remains always at max 8%.I tried to activate the aes-ni crypto under Miscellaneous and so on. The folowing options did I already tested.
- AES-NI CPU-based Acceleration
- BSD Crypto Device (cryptodev)
- AES-NI and BSD Crypto Device (aesni, cryptodev)
Without significant improvements. On the Internet a lot of people has those problems and couldnt find an solution that helped me.
My normal connection is at 500k / 200kI tried it from the internal(LAN) interface:
www --- ISP --- Router1 --- Qotom(pfSense) --- Device(Win10)Shell Output - openvpn --show-engines
OpenSSL Crypto Engines
Intel RDRAND engine [rdrand]
Dynamic engine loading support [dynamic]Shell Output openssl engine -t -c
(rdrand) Intel RDRAND engine
[RAND]
[ available ]
(dynamic) Dynamic engine loading support
[ unavailable ]Shell Output dmesg | grep AESNI
Features2=0x7ffafbff<SSE3,PCLMULQDQ,DTES64,MON,DS_CPL,VMX,SMX,EST,TM2,SSSE3,SDBG,FMA,CX16,xTPR,PDCM,PCID,SSE4.1,SSE4.2,x2APIC,MOVBE,POPCNT,TSCDLT,AESNI,XSAVE,OSXSAVE,AVX,F16C,RDRAND>
Features2=0x7ffafbff<SSE3,PCLMULQDQ,DTES64,MON,DS_CPL,VMX,SMX,EST,TM2,SSSE3,SDBG,FMA,CX16,xTPR,PDCM,PCID,SSE4.1,SSE4.2,x2APIC,MOVBE,POPCNT,TSCDLT,AESNI,XSAVE,OSXSAVE,AVX,F16C,RDRAND>
Features2=0x7ffafbff<SSE3,PCLMULQDQ,DTES64,MON,DS_CPL,VMX,SMX,EST,TM2,SSSE3,SDBG,FMA,CX16,xTPR,PDCM,PCID,SSE4.1,SSE4.2,x2APIC,MOVBE,POPCNT,TSCDLT,AESNI,XSAVE,OSXSAVE,AVX,F16C,RDRAND>
Features2=0x7ffafbff<SSE3,PCLMULQDQ,DTES64,MON,DS_CPL,VMX,SMX,EST,TM2,SSSE3,SDBG,FMA,CX16,xTPR,PDCM,PCID,SSE4.1,SSE4.2,x2APIC,MOVBE,POPCNT,TSCDLT,AESNI,XSAVE,OSXSAVE,AVX,F16C,RDRAND>Shell Output openssl speed -evp aes-256-gcm
Doing aes-256-gcm for 3s on 16 size blocks: 73271905 aes-256-gcm's in 3.01s
Doing aes-256-gcm for 3s on 64 size blocks: 43419016 aes-256-gcm's in 3.01s
Doing aes-256-gcm for 3s on 256 size blocks: 19236696 aes-256-gcm's in 3.01s
Doing aes-256-gcm for 3s on 1024 size blocks: 7259618 aes-256-gcm's in 3.15s
Doing aes-256-gcm for 3s on 8192 size blocks: 1021731 aes-256-gcm's in 3.03s
OpenSSL 1.0.2o-freebsd 27 Mar 2018
built on: date not available
options:bn(64,64) rc4(16x,int) des(idx,cisc,16,int) aes(partial) idea(int) blowfish(idx)
compiler: clang
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes
aes-256-gcm 389768.47k 923866.44k 1637267.67k 2361123.20k 2761243.83kServer Config
dev tun
persist-tun
persist-key
cipher AES-128-GCM
ncp-disable
auth SHA256
tls-client
client
resolv-retry infinite
remote 192.168.1.1 1197 udp
verify-x509-name "OpenVPN-Server" name
auth-user-pass
pkcs12 pfSense-UDP4-1197-vpn.p12
tls-auth pfSense-UDP4-1197-vpn-tls.key 1
remote-cert-tls serverDuno what the problem could be... Any idea?
-
@ShinigamiLY said in OpenVPN slow AES-NI:
My normal connection is at 500k / 200k
And what is the remote end? And what exactly is k suppose to mean do you mean your connection is only 0.5mbps down and 0.2mbps up? So your on some sort of EDGE sort of connection? 500kbps is horrible.. You sure wouldn't need any sort of offload/engine to handle those sorts of speeds.
-
Hy and ty for the response.
You are the first one that is asking me what k means :)
k = 1000 that means near 500 Mbps
Here a picture from speedtest
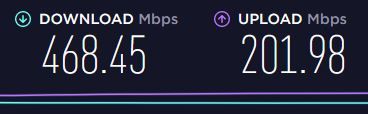
What do u mean with remote end? It are thest from the local connection over the openvpn of the box so it is on lan and the output is over the box to the speedtest page.
-
@ShinigamiLY said in OpenVPN slow AES-NI:
k = 1000 that means near 500 Mbps
Yeah I agree k means 1000, but you do not represent 500mbps with 500k unless you also kbps with that, etc..
500/200 mbps would been clearer ;) or mb even and left of the ps part
How are you testing - you could have 10gig up down on your end, doesn't mean shit if the remote client is only got 10/2 mbps connection.
-
@ShinigamiLY said in OpenVPN slow AES-NI:
AES-NI CPU-based Acceleration
On both sides ?
This might be a stupid question, I was just wondering. -
ty for the taken time.
@johnpoz
To dont bother with this problem I did it like this.
Im connectin intern(LAN) directly to the pfsense and then i go out trough it.
The oposit site is just the www.speedtest.netIn my opinion, if I'm able to reach the maximum speed without OpenVPN, it should work the same way with vpn.
Or am I wrong?So... Win10 from LAN directly connected to the OpenVPN Box and then go out directly to speedtest.net
So I dont need any device on the oposite site that can handle the encription.Here a picture of the constelation. This is only for the testing purpose to exclude all other sources of error. Later on it will be reachable from the WAN
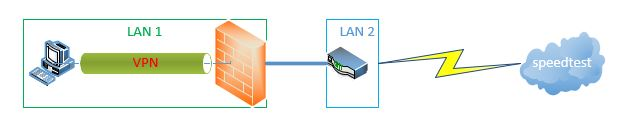
-
You are using the OpenVPN Server for a so called Road Worrier access ?
Or you are using the OpenVPN client - so you are connecting to a VPN access supplier ?In both case : the other side (an OpenVPN connection has TWO sides) also need very descent hardware and/or AES-N support.
Example : you are using a low-bud portable or phone to connect to your pfSense-OpenVPN-server : it's the slowest device that will dictate the speed. If you are using roaming on lousy 4G connection, then it doesn't matter if you have a big 500 Mbirs/sec connection.
Or are you are using the VPN-client : VPN companies have only one goal : collecting a monthly fee from you. They will not (never) tell you that they over-rented the same VPN server, and that the real through-put is your traffic, shared with thousands of other people on a Gigabit connection (so you wind up having close to nothing ...)
So, what's it ?
edit : the VPN connection goes beyond your "Main Router Conected to ISP".
Or do you really have a VPN over this 3 feet long cable that never leaves your place ? (and if so, why ????) -
So who says in that test case the vpn services on the isp router are not the issue? That is not valid test..
-
I rly dont understand what the problem should it be... the only 2 devices that has to do the encription / handshake and so on is my computer that is asking the pfsense over lan for the encryption and the pfsense on my box. Now I see that I made the picture wrong... the encryption is only between my computer and the pfsense. the pfsense is just the represent one that is going over my other router outside.
PC and pfsense are connected to each other over a lan cable... So only those 2 devices are necessary for the encription.Edited the picture