Openvpn Client Specific IP Address
-
I have an openvpn server setup on a Pfsense router and it successfully allows remote access to my LAN. However, I am trying to restrict access for one user to a specific ip address on the network. I have searched and it looks like I need a client specific override but I have no idea how to set this up in Pfsense 2.4.4. I am using specific user certs and password credentials for the logins. From my searches, it looks like the client specific overrides gives a specific tunnel ip address to a client and then I can use openvpn firewall rules to make the LAN address restrictions. Can someone point me to the gui settings where I can make client specific overrides?? Thanks.
-
VPN /OpenVPN / Clients / Edit
Advanced Configuration
Custom options
Enter any additional options to add to the OpenVPN client configuration here, separated by semicolon.or
VPN / OpenVPN / Client Specific Overrides / Edit
-
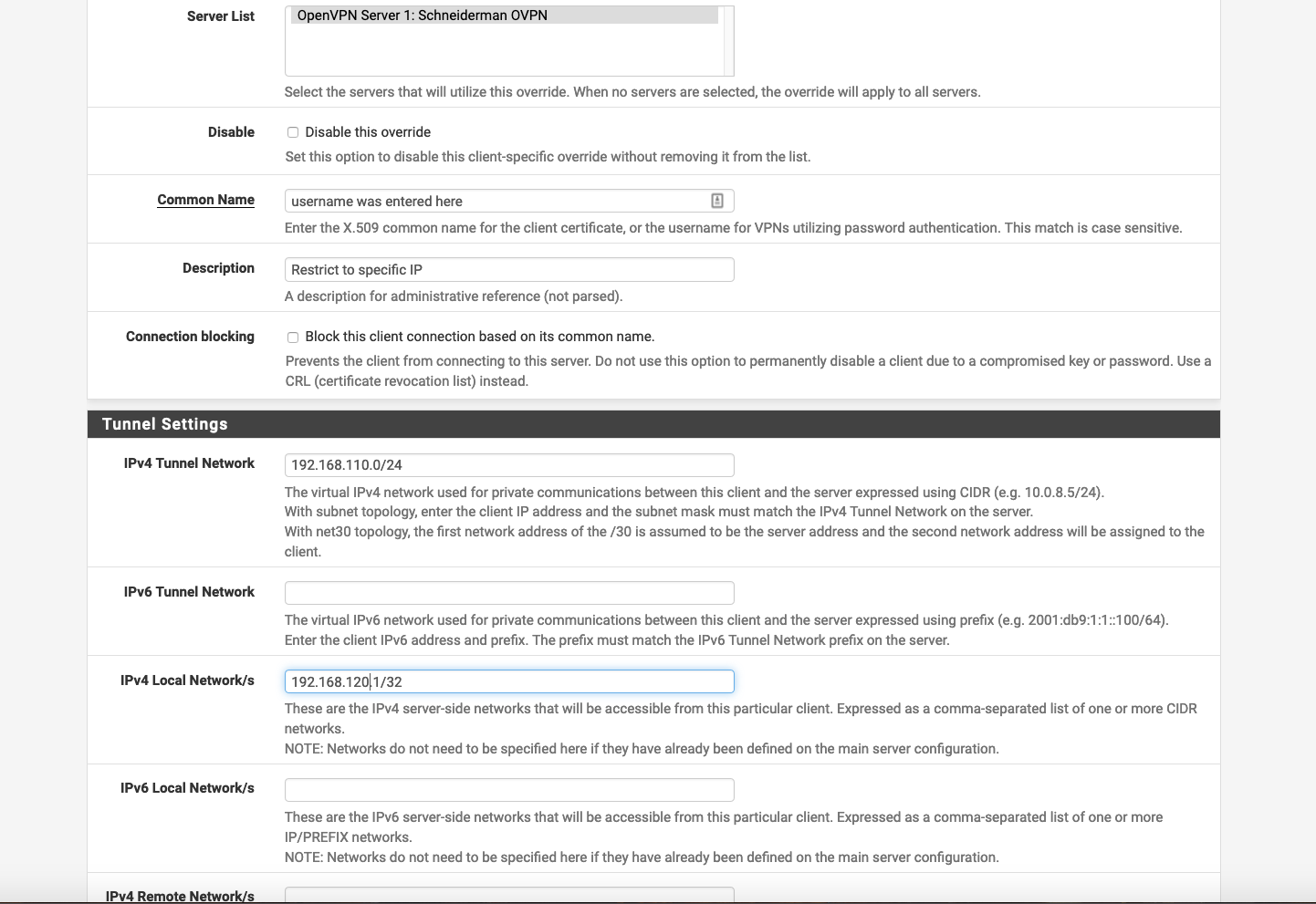
I did edit the client specific override under Openvpn but the user still had access to multiple ip addresses. See attached. I also checked the checkbox toward the bottom to route all traffic thru the tunnel.
Any firewall rules need editing?? Any ideas?
-
You could set a static ip for every clients with
ifconfig-push IP NETMASK
for example:
ifconfig-push 10.8.0.2 255.255.255.255
this way you can create firewall rules to block that specific ip inside the network -
@jeff3820 said in Openvpn Client Specific IP Address:
I did edit the client specific override under Openvpn but the user still had access to multiple ip addresses. See attached. I also checked the checkbox toward the bottom to route all traffic thru the tunnel.
Any firewall rules need editing?? Any ideas?The "Local Network/s" box is only for pushing routes to the client. For controlling the clients access you must add firewall rules by using the clients tunnel subnet as source network.
This requires that the specific clients tunnel network differs from the tunnel network of the other clients. -
@viragomann I got it. One more question. You mention that the client specific tunnel network and the other client tunnel network need to be different. The language on the client specific tunnel network says it has to be in the range of Openvpn server tunnel. I have the server tunnel as 192.168.110.0/24 and I made the client specific tunnel ip as 192.168.110.150/24 and this seems to work. I added a firewall rule on the openvpn section to address my needs.
Would it be better to make the openvpn server tunnel 192.168.110.0/25 so no chance of an ip duplication/overlap or would this cause problems as the client specific address of 192.168.110.150 is outside of the server range of 192.168.110.0/25??
-
As far as I know both models work, the CSO tunnel can be a part of the servers tunnel or outside. But your setting won't work as expected.
192.168.110.150/24 and 192.168.110.0/24 are exactly the same networks! So your specific client will get an IP out of the whole tunnel network. There is no sense.You may set the CSO tunnel to a part of the whole tunnel as /30, e.g. 192.168.110.152/30.
-
@viragomann So you are suggesting to change the client setting topology from Subnet to net30 or just change the CSO tunnel to 192.168.110.152/30??
-
No, you may leave the topology as it is. The /30 was just a save suggestion, no matter which topology you're using.
If you're server use subnet topology you may also set the CSO to a /32, so there's only one connection possible. With subnet topology and /30 CSO tunnel, the client could establish multiple connections. -
@viragomann Perfect...I got it. Makes sense now. Thanks for the assistance!
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on