FRR OSPF + route map + ACL = no routes being redistributed
-
If I disable the route map but leave the ACL, the ACL seems to have no effect. if I leave the route map with the ACL, no routes get advertised.
-
Crap. I just noticed a typo in my visio diagram. pfsense 1 is acting as the openvpn server over 2 different WAN interfaces:
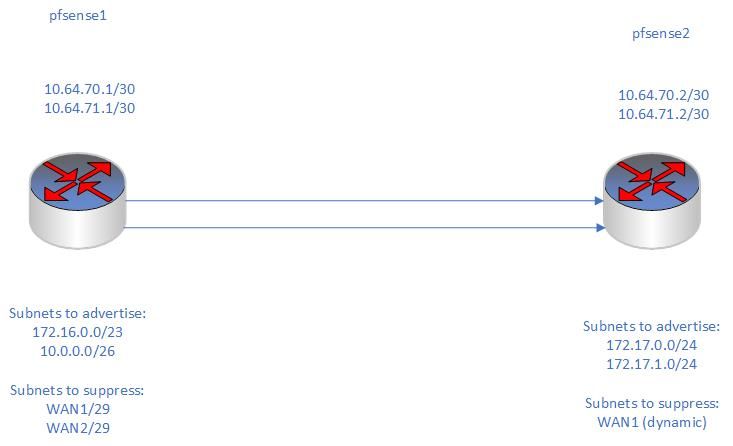
-
Oh and here is the web config page for FRR OSPF settings:
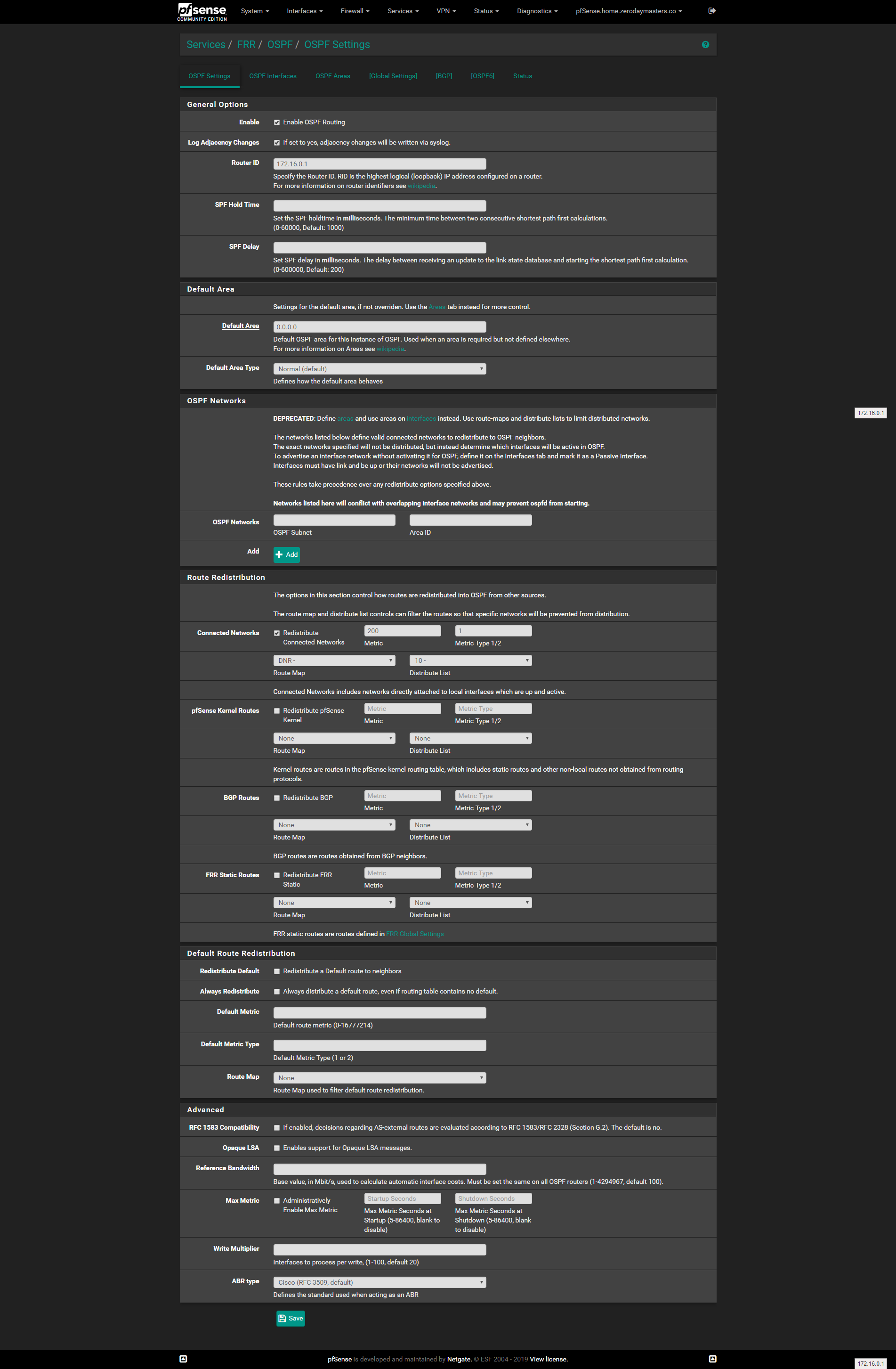
-
I don't see anything in your route map that is matching anything, only setting the metric. Or is the config above from a time you removed the ACL from the route map?
Also I don't see the route table info/zebra status/ospf status that would show for sure what is being sent/received from the peers.
-
@jimp The route map missing the ACL is a leftover from me trying make things work. Here is the route map with the ACL in place:
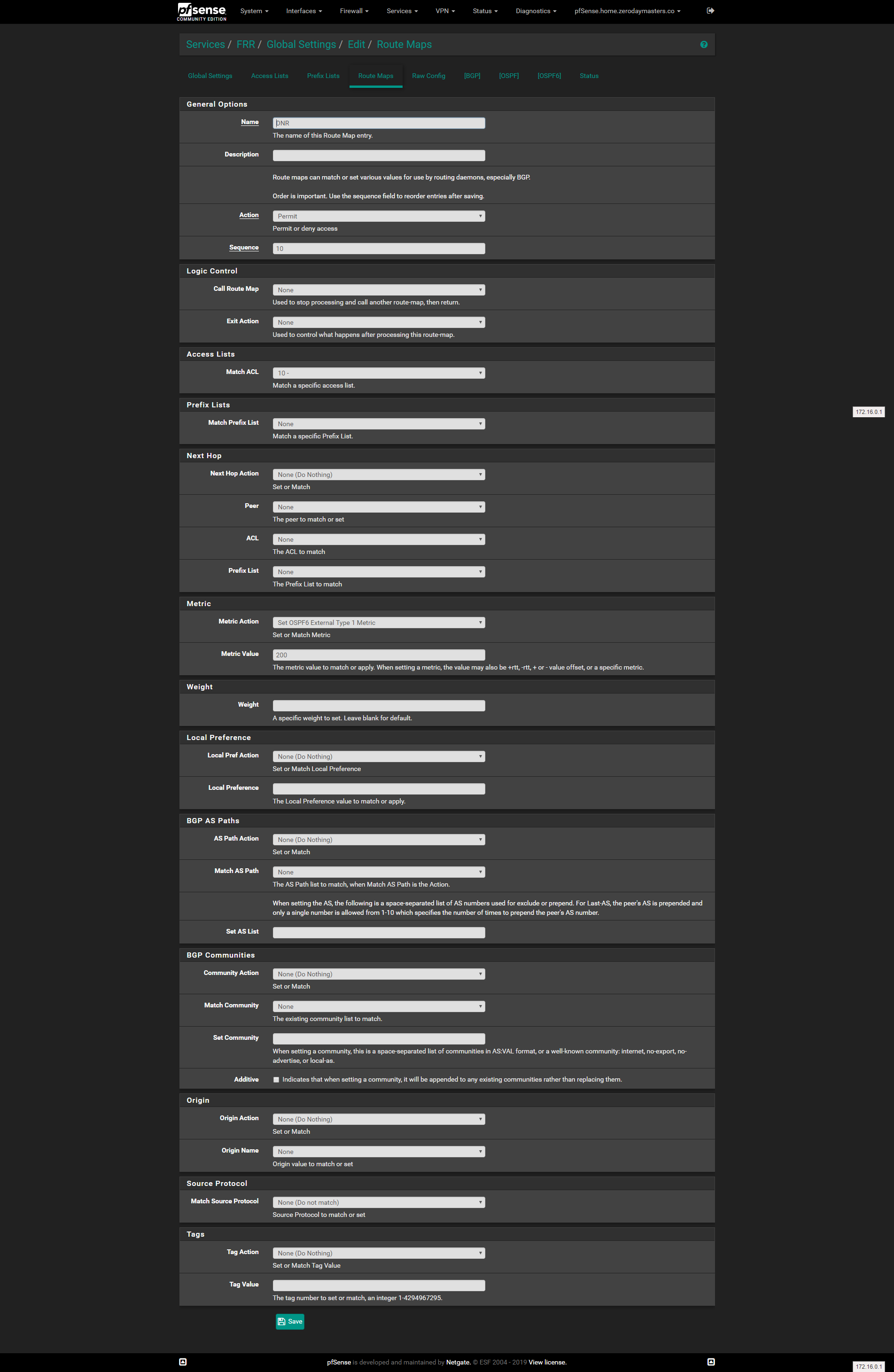
OSPF settings:
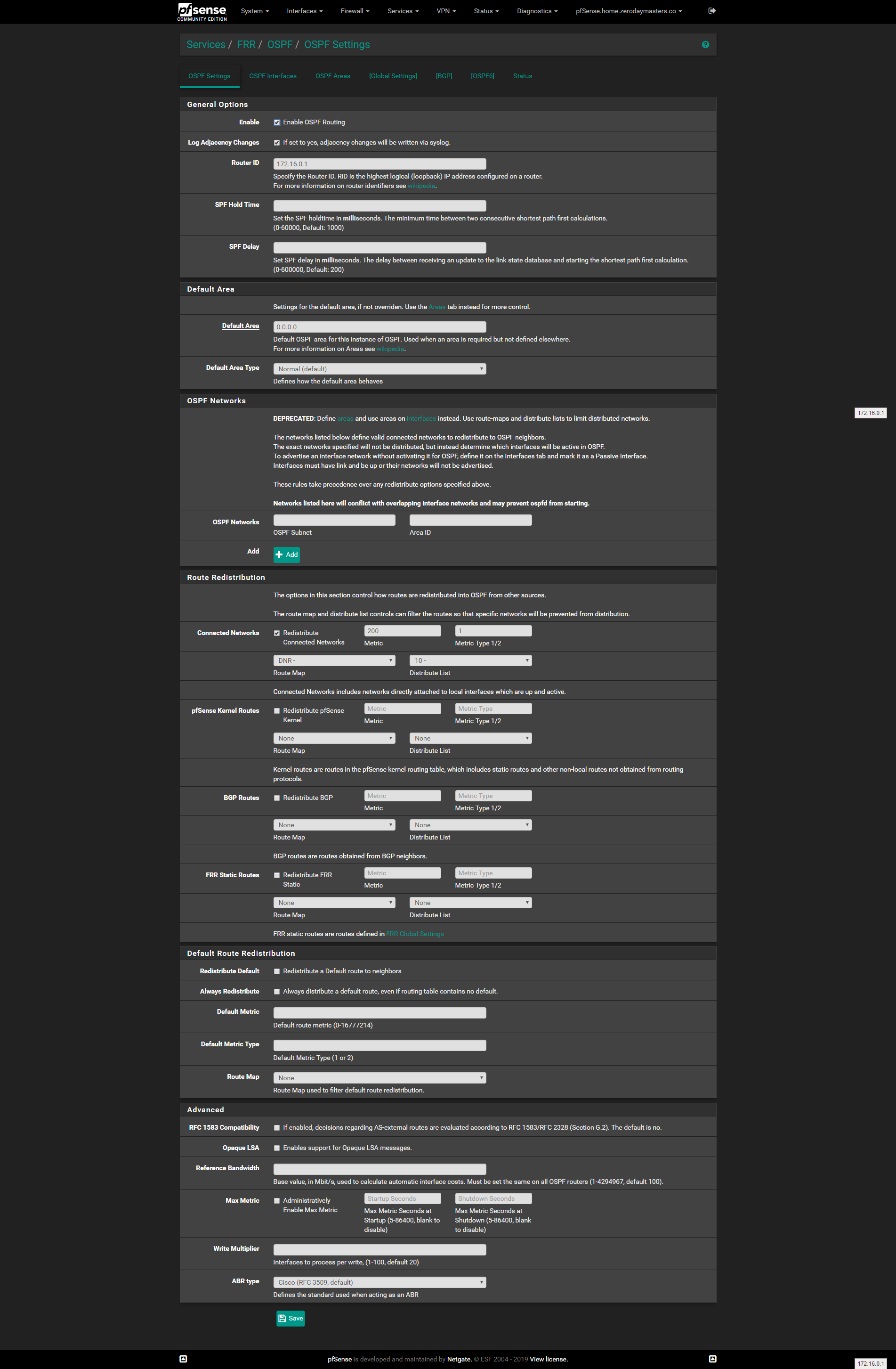
Zebra.conf
##################### DO NOT EDIT THIS FILE! ###################### ################################################################### # This file was created by an automatic configuration generator. # # The contents of this file will be overwritten without warning! # ################################################################### password **** log syslog # Access Lists access-list 10 deny 96.78.149.24 0.0.0.7 access-list 10 deny 108.211.142.80 0.0.0.7 access-list 10 permit any access-list 10 remark # Route Maps route-map DNR permit 10 match ip address 10 set metric 200 set metric-type type-1 # Accept Filters ip prefix-list ACCEPTFILTER deny 10.64.70.0/30 ip prefix-list ACCEPTFILTER deny 10.64.70.1/32 ip prefix-list ACCEPTFILTER deny 10.64.71.0/30 ip prefix-list ACCEPTFILTER deny 10.64.71.1/32 ip prefix-list ACCEPTFILTER permit any route-map ACCEPTFILTER permit 10 match ip address prefix-list ACCEPTFILTER ip protocol ospf route-map ACCEPTFILTERospfd.conf
##################### DO NOT EDIT THIS FILE! ###################### ################################################################### # This file was created by an automatic configuration generator. # # The contents of this file will be overwritten without warning! # ################################################################### password **** log syslog interface ovpns1 ip ospf network point-to-point ip ospf cost 5 ip ospf authentication message-digest ip ospf message-digest-key 1 md5 **** ip ospf area 0.0.0.0 interface ovpns3 ip ospf network point-to-point ip ospf cost 10 ip ospf authentication message-digest ip ospf message-digest-key 1 md5 **** ip ospf area 0.0.0.0 router ospf ospf router-id 172.16.0.1 area 0.0.0.0 shortcut default area 0.0.0.0 authentication message-digest redistribute connected route-map DNR metric 200 metric-type 1 distribute-list 10 out connected ospf abr-type ciscoZebra routes
Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP, T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP, F - PBR, > - selected route, * - FIB route K>* 0.0.0.0/0 [0/0] via 96.78.149.30, bce0, 00:09:11 K>* 1.1.1.1/32 [0/0] via 108.211.142.86, bce1, 00:09:11 K>* 8.8.8.8/32 [0/0] via 96.78.149.30, bce0, 00:09:11 C>* 10.0.0.0/26 is directly connected, cxl0.10, 00:09:11 K * 10.0.5.0/24 [0/0] via 10.0.5.2 inactive, 00:09:11 C>* 10.0.5.0/24 is directly connected, ovpns2, 00:09:11 K * 10.0.6.0/24 [0/0] via 10.0.6.2 inactive, 00:09:11 C>* 10.0.6.0/24 is directly connected, ovpns6, 00:09:11 O>* 10.0.8.0/24 [110/205] via 10.64.70.2, ovpns1 onlink, 00:09:00 C>* 10.1.0.0/23 is directly connected, cxl0.54, 00:09:11 C>* 10.1.10.0/24 is directly connected, bce0, 00:09:11 C>* 10.2.0.0/24 is directly connected, cxl0.20, 00:09:11 C>* 10.4.0.0/24 is directly connected, cxl0.99, 00:09:11 C>* 10.4.1.0/30 is directly connected, cxl0.99, 00:09:11 C>* 10.4.1.4/30 is directly connected, cxl0.99, 00:09:11 C>* 10.6.0.0/24 is directly connected, bce2, 00:09:11 C>* 10.6.1.0/30 is directly connected, bce2, 00:09:11 C>* 10.6.1.4/30 is directly connected, bce2, 00:09:11 O 10.64.70.1/32 [110/205] via 10.64.70.2, ovpns1 inactive onlink, 00:09:00 C>* 10.64.70.2/32 is directly connected, ovpns1, 00:09:11 O 10.64.71.1/32 [110/205] via 10.64.70.2, ovpns1 inactive onlink, 00:09:00 C>* 10.64.71.2/32 is directly connected, ovpns3, 00:09:11 C>* 10.64.73.0/30 is directly connected, ipsec3000, 00:09:11 C>* 10.99.99.1/32 is directly connected, cxl0.50, 00:09:11 K>* 64.62.134.130/32 [0/0] via 96.78.149.30, bce0, 00:09:11 O>* 67.180.160.0/22 [110/205] via 10.64.70.2, ovpns1 onlink, 00:09:00 K>* 68.185.85.2/32 [0/0] via 96.78.149.30, bce0, 00:09:11 K>* 71.92.250.42/32 [0/0] via 96.78.149.30, bce0, 00:09:11 K>* 72.52.104.74/32 [0/0] via 108.211.142.86, bce1, 00:09:11 C * 96.78.149.24/29 is directly connected, bce0, 00:09:11 C * 96.78.149.24/29 is directly connected, bce0, 00:09:11 C * 96.78.149.24/29 is directly connected, bce0, 00:09:11 C * 96.78.149.24/29 is directly connected, bce0, 00:09:11 C>* 96.78.149.24/29 is directly connected, bce0, 00:09:11 C * 108.211.142.80/29 is directly connected, bce1, 00:09:11 C * 108.211.142.80/29 is directly connected, bce1, 00:09:11 C * 108.211.142.80/29 is directly connected, bce1, 00:09:11 C * 108.211.142.80/29 is directly connected, bce1, 00:09:11 C>* 108.211.142.80/29 is directly connected, bce1, 00:09:11 C>* 172.16.0.0/23 is directly connected, cxl0.50, 00:09:11 O>* 172.17.0.0/24 [110/205] via 10.64.70.2, ovpns1 onlink, 00:09:00 O>* 172.17.1.0/24 [110/205] via 10.64.70.2, ovpns1 onlink, 00:09:00 C>* 172.30.250.0/24 is directly connected, em0, 00:09:11 C>* 192.168.1.0/24 is directly connected, bce1, 00:09:11 K>* 192.168.10.0/24 [0/0] via 10.64.73.2, ipsec3000, 00:09:11OSPF routes:
============ OSPF network routing table ============ ============ OSPF router routing table ============= R 172.17.0.1 [5] area: 0.0.0.0, ASBR via 10.64.70.2, ovpns1 ============ OSPF external routing table =========== N E1 10.0.8.0/24 [205] tag: 0 via 10.64.70.2, ovpns1 N E1 10.64.70.1/32 [205] tag: 0 via 10.64.70.2, ovpns1 N E1 10.64.71.1/32 [205] tag: 0 via 10.64.70.2, ovpns1 N E1 67.180.160.0/22 [205] tag: 0 via 10.64.70.2, ovpns1 N E1 172.17.0.0/24 [205] tag: 0 via 10.64.70.2, ovpns1 N E1 172.17.1.0/24 [205] tag: 0 via 10.64.70.2, ovpns1 -
Hi I am facing same issue.
ip prefix-list ADMIN_VPN_PL seq 10 permit 192.168.27.0/24 ip prefix-list ADMIN_VPN_PL description # Route Maps route-map REDIS_CONNECTED_RM permit 10 match ip address prefix-list ADMIN_VPN_PL # Accept Filters ip prefix-list ACCEPTFILTER permit any route-map ACCEPTFILTER permit 10 match ip address prefix-list ACCEPTFILTER ip protocol ospf route-map ACCEPTFILTERFRR ospfd.conf
interface em1 ip ospf network broadcast ip ospf area 0.0.0.0 interface ovpns1 ip ospf network broadcast ip ospf area 0.0.0.0 router ospf ospf router-id 192.168.20.4 redistribute connected route-map REDIS_CONNECTED_RM metric 200 metric-type 1 ospf abr-type cisco passive-interface ovpns1pfSense.localdomain# show route-map ZEBRA: route-map ACCEPTFILTER, permit, sequence 10 Match clauses: ip address prefix-list ACCEPTFILTER Set clauses: Call clause: Action: Exit routemap ZEBRA: route-map REDIS_CONNECTED_RM, permit, sequence 10 Match clauses: ip address prefix-list ADMIN_VPN_PL Set clauses: Call clause: Action: Exit routemap pfSense.localdomaipfSense.localdomain# show ip route Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP, T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP, F - PBR, > - selected route, * - FIB route .... O>* 192.168.23.0/24 [110/101] via 192.168.20.3, em1, 00:01:49 O>* 192.168.24.0/24 [110/101] via 192.168.20.3, em1, 00:01:49 O>* 192.168.25.0/24 [110/1602] via 192.168.20.2, em1, 00:01:49 K * 192.168.27.0/24 [0/0] via 192.168.27.2 inactive, 00:01:49 C>* 192.168.27.0/24 is directly connected, ovpns1, 00:01:49 O>* 192.168.27.1/32 [110/10] is directly connected, ovpns1, 00:01:49 ....My goal is to advertise subnet, that is being used for Open VPN. I cannot find any straightforward solution. Now I try to redistribute the exact one subnet from directly connected networks. Without route-map all routes are redistributed just fine. With the route-map nothing is being redistributed.
Any ideas? Thanks.
-
I found a bug here, and a fix will be coming along shortly.
https://redmine.pfsense.org/issues/9640 -
If you are on CE or Factory 2.4.4-p3, the new package is up now. CE snapshots will have it whenever the next new build happens. Factory snapshots will get the new version a little later, there are some changes we need to make to accommodate the 2019Q3 ports branch merge yet.
-
Thanks @jimp. The new package is working as expected.
-
I also confirm. Package update solves the problem. Thanks @jimp.