VLAN OVER VPN
-
HI everyone
I got one pfsense with one WAN on NIC 1 and two lan on NIC 2 separated by VLAN :
LAN 1 - 192.168.12.0/24 - VLAN ID 100
LAN 2 - 192.168.2.0/24 - VLAN ID 200Both LAN are manage by a Layer 2 Switch .
The Switch VLAN management is on 200.
I got one VPN acces to pfsense with route to both LAN
I succeed to get acces to pfsense box but not on devices located on each LAN . I suppose is because via my openvpn tunnel i don't push VLAN id on my packet .
I would like to know if someone succed to implement such design ??
Is there a way to push vlan id via openvpn ??KR
-
Hi! Did you add local networks to openvpn server settings?
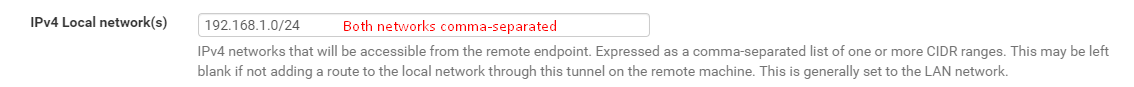
I don't think VLAN is different from physical LAN access. VLAN id is not to be translated to VPN tunnel. -
@max33 said in VLAN OVER VPN:
I would like to know if someone succed to implement such design ??
Normal tunnel VPNs do not support VLANs, as VLANs are layer 2 and VPNs carry layer 3 traffic. The only thing you can do is run the VPN in TAP mode, which is essentially a bridge.
-
It is planned to be included into version 2.5:
https://community.openvpn.net/openvpn/wiki/StatusOfOpenvpn25
https://github.com/OpenVPN/openvpn/pull/76 -
@Pippin said in VLAN OVER VPN:
It is planned to be included into version 2.5:
What's to be included???
-
Vlan capability, but I think I was too quickly, it's for tap mode, not tun.
-
@Pippin said in VLAN OVER VPN:
Vlan capability, but I think I was too quickly, it's for tap mode, not tun.
That's curious. As TAP mode is supposed to be equivalent to a bridge, there should be no difference between handling VLANs and any other type of Ethernet frame. The only difference between a VLAN frame and any other is the contents of the Ethertype field and the additional 4 bytes. A TAP VPN should be able to handle any Ethernet frame, including VLAN.
Ethernet bridges represent the software analog to a physical ethernet switch.
-
Please read here:
https://sourceforge.net/p/openvpn/mailman/message/34991937/ -
@Pippin said in VLAN OVER VPN:
Please read here:
https://sourceforge.net/p/openvpn/mailman/message/34991937/First off, I have no experience with TAP. My take on that is adding VLAN support to the TAP interface, as would be done on an Ethernet interface. Is that correct? Does TAP support bridging from a physical interface? If so, it should be transparent to VLAN tags.
-
@JKnott said in VLAN OVER VPN:
First off, I have no experience with TAP. My take on that is adding VLAN support to the TAP interface, as would be done on an Ethernet interface. Is that correct? Does TAP support bridging from a physical interface? If so, it should be transparent to VLAN tags.
Neither do I but yes, it's about adding VLAN support to TAP interface.
But I think it's OT here...
-
@max33 I'd like to clarify your request.
What do you need?:- translate VLAN id to client-side network (i don't know the reason)
- just need to access to devices behind VPN tunnel from your client device
If 2nd - just give access on VPNserver settings page. You don't need to translate VLAN IDs to tunnel.
Take a look this:
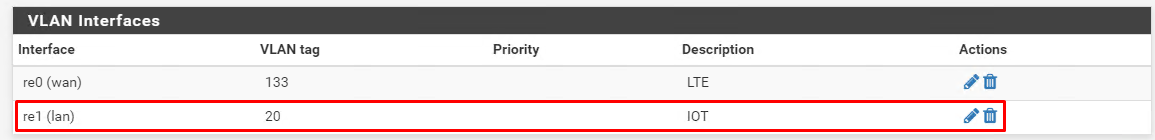
OpenVPN server settings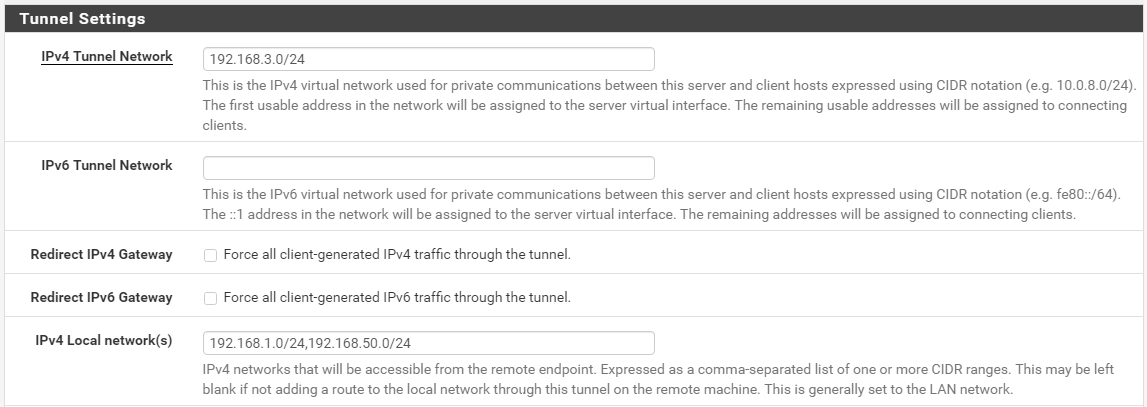
As a result VPN client doesn't even know about tags, vlans etc.
ping from VPN client to VLAN20 gateway (packets between VPN client and VPN server are untagged)
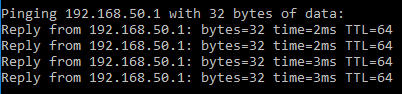
-
Is VLAN over VPN even necessary? VLANs are normally different IP address ranges. Why not just route the traffic from the VLANs to the other end according to address? Similarly, the other end will then forward to the appropriate VLAN.
-
Thanks to all for taking time to respond
I think my question was not clear so i will try to explain : I just want to connect to my switch via vpn client.
I confirm that i correctly set my open vpn (the IVP4 local network range) but unable to reach web interface of the switch .
Currently schema is :
NIC 1 of PFSENSE connected to WAN
NIC 2 of PFSENSE connect to Switch Layer 2Two VLAN interface declared on PFSENSE NIC 2
VLAN 100 for TELEPHONY - 192.168.10.0/24
VLAN 200 for PC - 192.168.0.0/24Switch are on VLAN 200 (Management VLAN 200) on IP 192.168.0.253
PC are connected to Phone devices (YEALINK T46) and phone connected to Switch.
Phone Device tagged packet in order to manage VOIP traffic on VLANN 100 and PC traffic on VLAN 200
All works when i am on local network (connected to switch) but when i am outside in order to manage the network i implemented OPENVPN on pfsense and set the two network on IPV4 Local Network.
I got acces to web interface of phone but not on web interface of switch so i am asking myself if it could be due to vlan.
I will try to perform more test tonight and come back later.
-
Looking at that VLAN feature it sounds like it will be in the OpenVPN tap process - sort of like iroutes in the tun process. If it also integrates with, say, tagged VLANs on an OpenVPN assigned interface that would be...interesting.
All works when i am on local network (connected to switch)
I got acces to web interface of phone but not on web interface of switch so i am asking myself if it could be due to vlan.
Is the default gateway on the switch's management interface set properly?
-
@Derelict
I think this answers that question:
https://github.com/OpenVPN/openvpn/pull/76#issuecomment-493688410 -
Yeah. that would be interesting.
-
One question, what's at the other end of the VPN? With a TAP VPN, the network will have to be in the same subnet as this end.
-
HI
Thanks a lot Derelict you got the point , the issue was coming from wrong gateway setting on the switch.
A stupid simple config......By the way thanks a lot to all people whose taking time to respond....
Have a good day all............
-
@max33 great! have a nice day)