Linking multiple subnets with pfsense and VMware Workstation (RESOLVED)
-
Hi all,
I have spun up a VMware Workstation home lab environment with the following two networks: 172.16.16.0/24 (Custom: VMnet 10) and 172.16.17.0/24 (Custom: VMnet 11).Currently I have two Windows hosts that I am trying to get to communicate together using pfsense on FreeBSD. They are as follows:
172.16.16.10/24 (Network adapter is Custom: VMnet 10) and 172.16.17.10 (Network adapter is Custom: VMnet 11)My question may be simple, but I cannot figure out how to get pfsense to get these two subnets to communicate. The pfsense router is installed and I configured LAN1 with 172.16.16.1/24 which is accessible via Web GUI from 172.16.16.10/24. There are three virtual network adapters on this pfsense host for bridged, Custom: VMnet 10, and Custom: VMnet 11. I also configured an optional interface on pfsense with 172.16.17.1/24, but have had no success getting this interface to work properly.
The weird part is I can only access the web gui through 172.16.16.10 and not 172.16.17.10 (If I remove VMnet 10 and only have bridged and VMnet11, then I can access the web gui through 172.16.17.10. I also can ping from 172.16.16.10 to 172.16.16.1 & 172.16.17.1 & 172.16.17.10. For some reason I cannot ping from 172.16.17.10 to 172.16.17.1 or 172.16.16.1 & .10. It is only one way from the first LAN interface configured on pfsense and not back the other way on the 2nd LAN interface.
Is there something I am missing with the virtual network, virtual network adapters, or configuration with pfsense itself? I would be so grateful if someone could help me out with this. Please let me know if there is anything else needed! :)
-
If you only have 1 interface in pfsense, then the anti lock out goes there to allow you to access the gui, if you add another interface "lan" then no you can not access from wan any more.. The antilock out will be on the lan interface.
There is nothing to do for multiple vlans to talk to each other once connected to pfsense, other than make sure you firewall rules allow. LAN will be the only interface that has default any any, when you fire up a new interface there will be no rules.
Your going to have to call out what interface is what in pfsense if you want help.. And what your doing on your workstation as far as bridged to your physical network or just a vm network doesn't mean anything in the context of pfsense and doesn't matter.
If your having a problem with vm A talking to vm B on some other interface - its more than likely in your vm networking setup.. As long as you actually created rules on the new interfaces you added.. Do a simple sniff is pfsense seeing the traffic on your other lan interfaces? Do your vms get an IP from dhcp running on pfsense?
Moving this to virtual section - this isn't multi wan routing..
-
Hi John,
Thank you for the quick reply and sorry I posted in the wrong section. I did not know about the anti-lockout on pfsense. It makes sense now that it can only be accessed on one interface. Currently my setup does not have any VLANs, I am just trying to route traffic as follows: 172.16.16.0/24 <=> 172.16.17.0/24 so far it seems to only be going from 172.16.16.0 to 172.16.17.0, but not the other way around.When it comes to sniffing, I am not too familiar with packet sniffers such as Wireshark, nor do I know how to use them. My VMs are not running from DHCP and I am manually assigning an IP to each device. Each device is a domain controller in each subnet with a few other servers, but the DCs are my main concern right now. Here is a picture of my interfaces on my pfsense server (Leaving IPs since it is all internal):
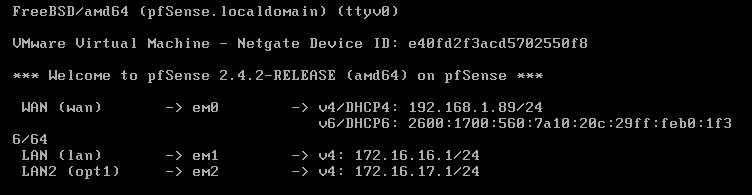
Virtual Network:
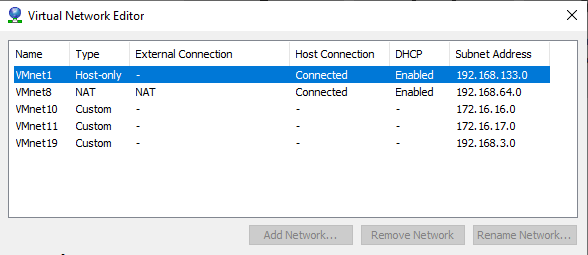
Pfsense Server VM settings:
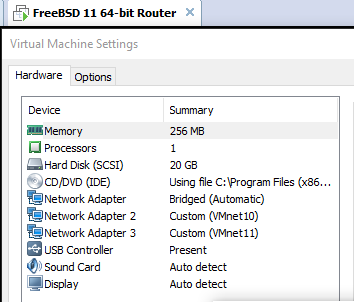
If I left anything out, do let me know. Also, I am not as adept in networking, so please bare with me, and thank you so much for sharing your information to me.
-
Please post screens of your firewall rules for the two custom interfaces.
-
Hi Kom,
It seems you and John may be spot on here about the firewall rules. Here are my screenshots below: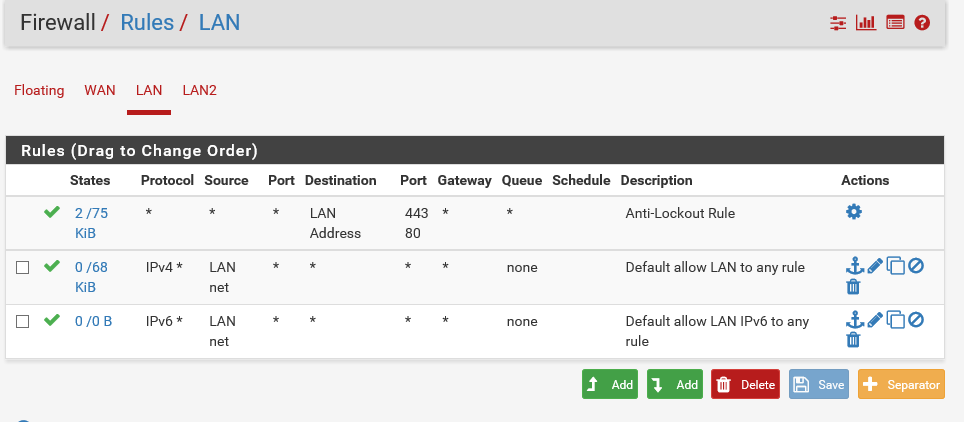
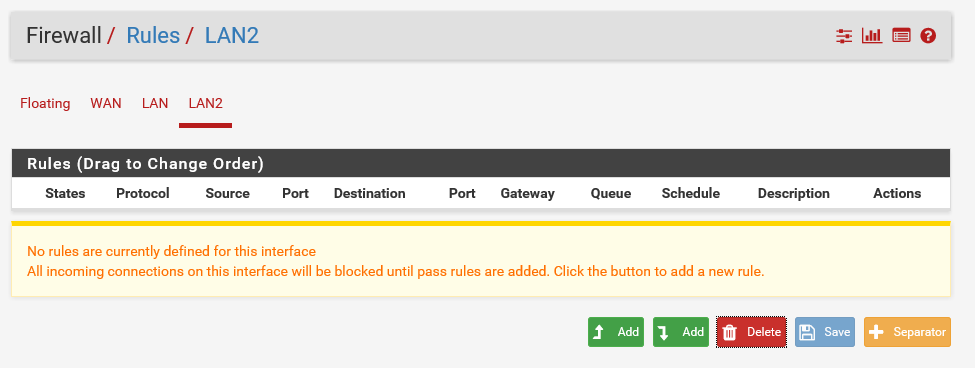
-
You need to add the same rules that you see on LAN to LAN2, other than the lockout rule.
-
Thanks, I will give that a shot soon. Is there a way to be able to reach the pfsense router via web gui from the LAN2 interface instead of just the LAN1 interface?
-
Hi Kom,
Looks like it worked even with anti-lockout configured on LAN1. Strange but it works, so thank you! Now I can continue to create a trust between my two active directory domains.

-
@johnpoz did mention that only the first LAN gets default rules, and that all other OPT interfaces have no rules by default and must be manually added or nothing can talk.
Glad you got it going. Get to work!

-
@johnpoz and @KOM Yes he did and thank you both for the very quick and informative assistance. This honestly slowed me down for a while and now I can continue to grind for the other projects I am doing for my virtual lab. I am a newbie to pfsense or firewalls in general, but is there a way I can close this thread out as solved?
-
You could edit the post title which is in your first post and prepend it with [SOLVED] or [RESOLVED], depending on your preference.