Can't work out why this firewall rule isn't working
-
I've got PFSense setup with 6 interfaces, WAN, LAN and the rest don't matter for this issue. I've made a firewall entry to allow a single machine on the LAN to connect out to specific servers for an app. Initially I had DNS names only in the firewall alias but to rule out any resolution issues I changed it to an IP range block. For some reason the logs still indicate my default deny rule (Last entry on the list) is the rule that's being hit and the traffic denied but I've gone through everything multiple times and cannot work out why.
This occurred the other day for a different rule I had setup and is the first time I have seen this issue. I can't remember if the issue was present only after the update to 2.4.4-p3 or if the issue is what prompted me to try updating from p2. The rule the other day was only needed for a single occasion so I put a temporary destination * into the rule and it worked fine.These are the firewall logs showing destination UDP 5.188.110.11:5056 and UDP 5.188.110.7:5056 being blocked at 23:40
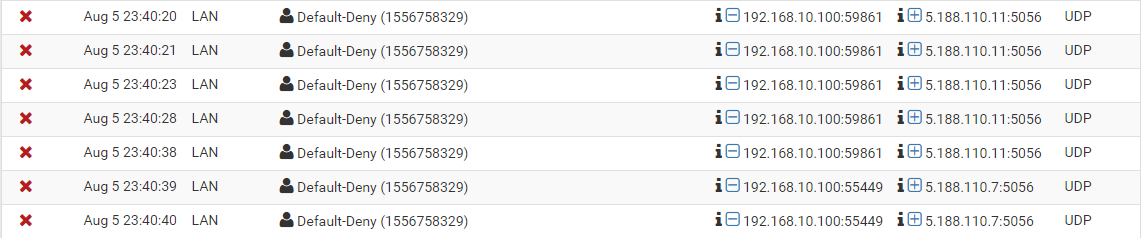
These are the rules (The app is partly working hence the data transferred against the rule, it's a specific function I am trying to get working that is failing)

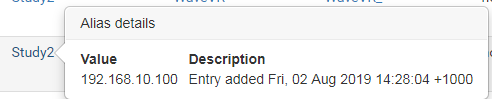
Study2 alias is set correctly
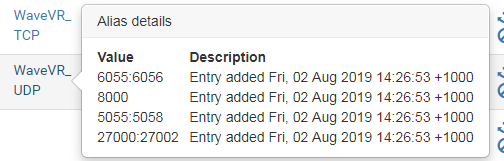
UDP port 5056 is covered in the port alias range
Both IPs that are being blocked are definitely in the alias list as of 23:33 (When I changed from a DNS entry to an IP range). I cleared all states to make sure it wasn't a state that was being reused in the deny rule.

The deny rule is the absolute last rule so should only be reached if it hasn't matched earlier rules. I put this in over keeping the default rule as it was allowing some traffic out at times where it shouldn't have been. Due to running secure servers for work and needing multiple areas of isolation between networks it was needed.
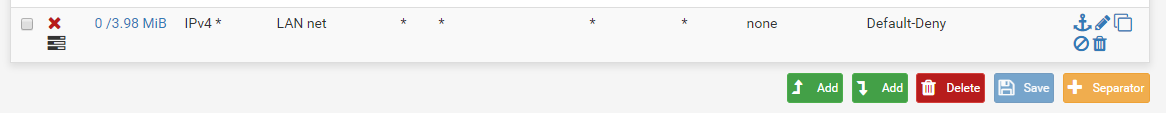
Have I missed something glaringly obvious? I can't work out what's not right here as it looks correct to me and the rule up to the 5.188 block is working correctly as no logs are generated.
-
Did you validate the stuff you put in the alias are actually in the table - under diag, you can view the actual details of a table.
-
@johnpoz said in Can't work out why this firewall rule isn't working:
Did you validate the stuff you put in the alias are actually in the table - under diag, you can view the actual details of a table.
No I didn't. Have just checked that now (Haven't ever had to use that before) and it's missing most of the entries.
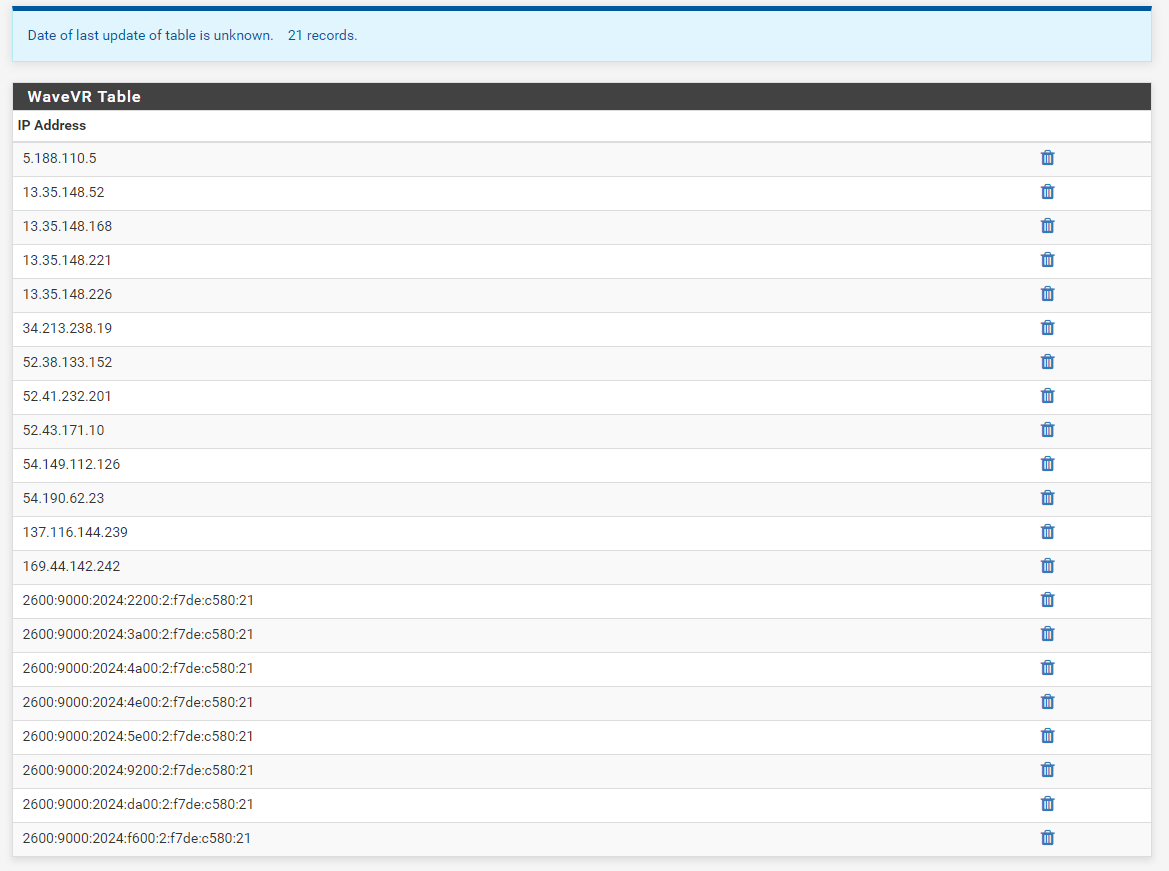
Why would that happen when it appears in the list of entries under the alias section?
Is it something I've done wrong or is that a bug or issue? -
Looks like its missing maybe the fqdn, not resolving? These only updates ever 5 minutes.. Maybe there is some issues typo? Or they don't resolve for some reason?
-
To rule any FQDN resolution issues I specifically added in an IP range that included all FQDNs it would have resolved
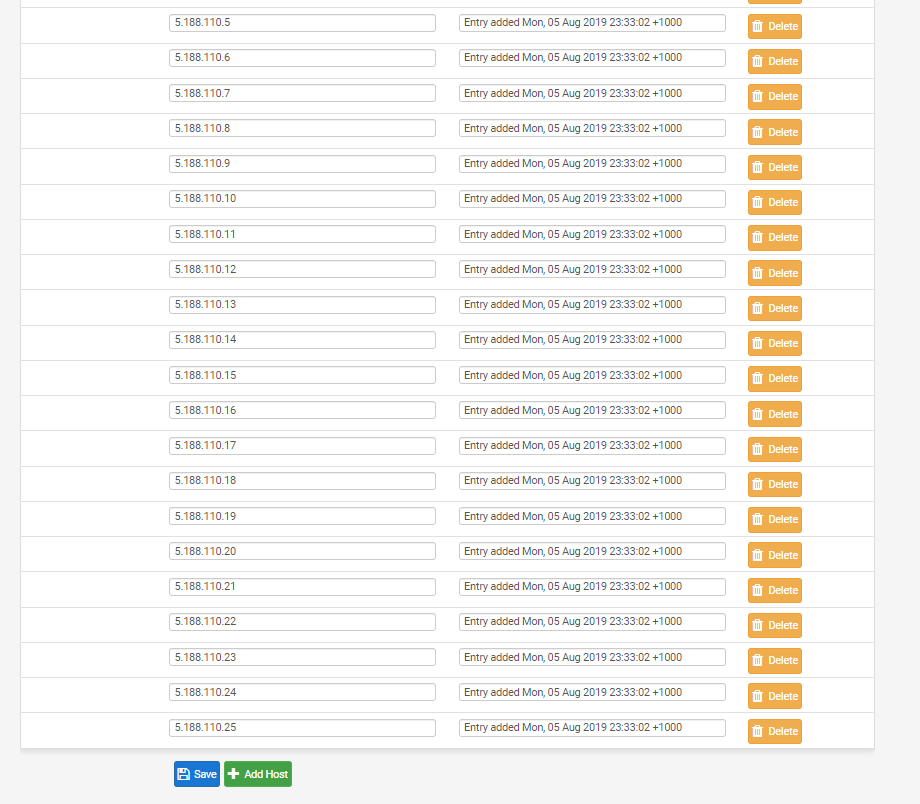
For some reason though they are not appearing in the diagnostics table view.
-
is filterdns running? Could be related to this?
https://redmine.pfsense.org/issues/9296Could you just put those IPs in via a /cidr rule?
-
Possibly related to that. Two of the entries resolved to the same IP which possibly triggered the bug. I tried restarting filterdns, tried restarting the firewall, tried changing the resolution time to 30s as suggested by someone. Now multiple of my tables are empty including the one I was trying to get to load before

Unfortunately for some of my rules I can't use a CIDR rule as the IP address changes due to the way cloud providers allocate IPs to servers in a cluster coming online and offline and the possibility that it might change to a different network thus rendering the CIDR rule unworkable. AWS seems to be notorious for that from what I can tell.
-
Yeah they can be problematic ;)
-
So it appears to be that bug. As soon as I remove any FQDNs then the table updates correctly. Surely this bug needs to be addressed before 2.5, it seems pretty critical to have the firewall table function as intended.
-
Is there a limit to an alias manually entered size? I have tried creating a CIDR networks alias with 4 entries in it, a /20, a /21 and two /24 but it does not even appear in the list of tables under diagnostics.
Scratch that, it's not letting me create any tables now
-
Not sure what your doing, but you can create cidr alias just fine.. Are you wanting it to expand them? Not a good idea with a "host" type alias - just use the network alias type.
Here I have a alias for the cloudflare networks, which is huge amount of space..

As you can see the table contains the networks. They all there - just snipped the screenshot vs having to capture the scroll ;)
Also have a networks alias that contains all of rfc1918 space..
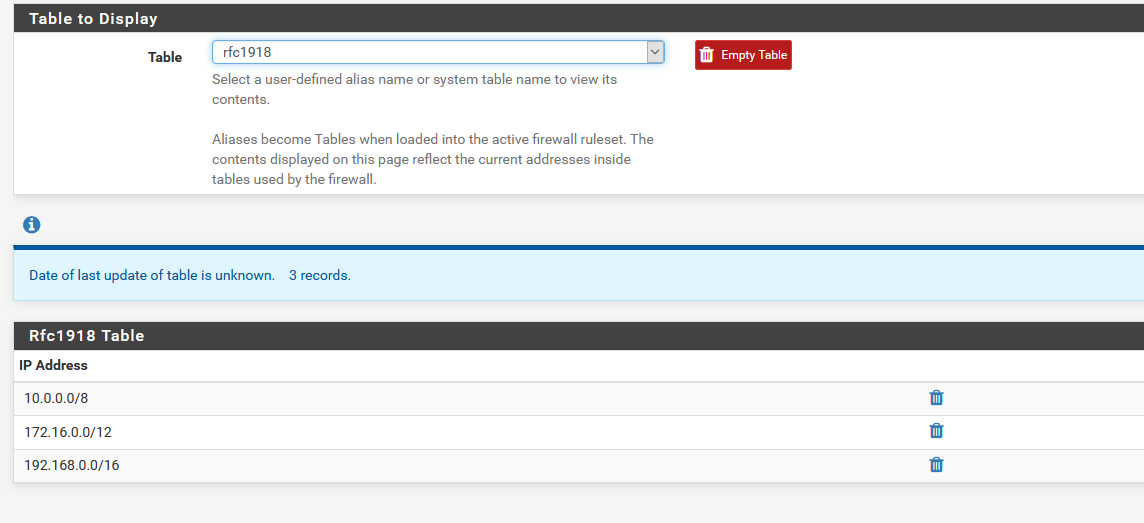
Mixing fqdn and IP or Networks, has never really been a good idea.. It says in the host name alias that when a /cidr is used it will expand that, etc.. Which could be problematic for sure if your using large /8 for example ;)
-
@johnpoz said in Can't work out why this firewall rule isn't working:
Not sure what your doing, but you can create cidr alias just fine.. Are you wanting it to expand them?
I worked out what I was doing wrong!
Because I haven't had to refer to the tables before (including from CLI) because I've never had an issue with 2.3x I was checking for them before applying them to a firewall rule which turns out is the point that they're created, not from after saving and hitting apply in the UI as I had expected.
So no issues with CIDR but unfortunately I am stuck with bug 9296 :(