Allow LAN to LAN, not routing
-
I'm struggling on this so thought I should ask at this point before breaking something.
I have one LAN on the firewall of 10.0.0.1/24 and this is also the gateway.
I need to reach devices on another LAN 10.100.100.x that has its own gateway.I added a virtual IP to one of the devices, 10.100.100.12 on the LAN and I can now ping that device but most everything else fails. The device is an NFS server but while I can ping it, I cannot see or mount or do much else with the device.
I've been looking to see if I also need to add some rules or something but this is now beyond my skill level and no idea what I'm missing.
Can anyone help.
-
The devices in LAN 2 will send responses to their default gateway, since they don't have a route to LAN 1.
So either add a route to each device (properly per DHCP) or set up a transit network between the two routers (gateways) and set up static route on both for the networks behind them as @johnpoz has illustrated here: https://forum.netgate.com/topic/145513/firewall-routing-problem/7A dirty workaround here is to add an outbound NAT rule to the LAN 2 interface which translates source addresses in outgoing packets into the interface address. If this is practicable for you depends on your needs.
-
@lewis said in Allow LAN to LAN, not routing:
that has its own gateway.
Yeah that is going to be problem.. When you say you added another IP to a device... This sounds like your running 2 different L3 networks on the same L2 network... This is not optimal..
Could you draw up how you have everything connected and we can work out how to do what you want to do.
-
That won't work. Virtual IPs are used so that pfSense can pretend to be another host. What you ended up with was pfSense spoofing that IP address, so it wouldn't work like your real NFS server other then pinging it. Also, I'm not sure how you're expecting to get traffic from one network to another without routing it, regardless of whether they're LANs, WANs or whatever.
Add a static route via System - Routing - Static Routes by specifying the destination network and its gateway.
(Bah, I didn't notice John and viragomann slipping in first...)
-
Sure could do a source nat if required - but I want to make sure he is just not running both L3 on the same L2... That is never a good way to do anything.
But sure if his other network is actually different L2 then we could source nat if need be.
Prob better to put this other gateway on a transit connected to pfsense and route/firewall everything that way.
-
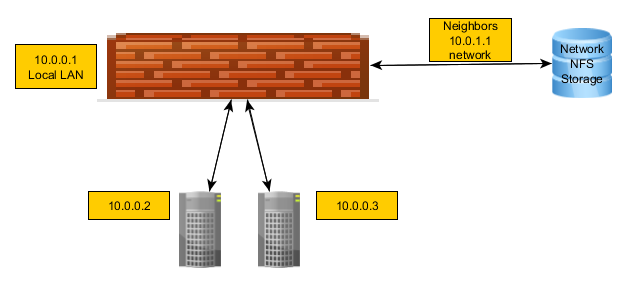
Very simplistic image but we have our own LAN, 10.0.0.1.
We have a neighbor in the data center that is going to share some data with us.
They have their own LAN at 10.0.1.1 for example and they have their our gateway on that LAN of course.
I don't want to route or be the gateway for that LAN, I just need to reach the NFS storage device on their LAN.Of course, I have no control over their LAN or what they use or how they use it. I only have the possibility of using this storage if I can reach it. The two servers I show would want to mount that NFS share.
-
-
@lewis said in Allow LAN to LAN, not routing:
I don't want to route
You have a routing issue...
So you have only to add a static route for your LAN 10.0.0.0/24 pointing to the pfSense IP in 10.0.1.0/?? on the NFS storage. That's all you need.
-
I don't want to route meant I cannot route their network, we aren't their gateway. Sorry that wasn't clear.
I basically just need LAN to LAN access from our own 10.0.0.1 LAN to devices on their 10.0.1.1 LAN network. -
You can most certainly route to their network, and if they're onboard with sharing data with you then surely they can add a static route on their end for the 5 second it would take?
-
Yes, our traffic is allowed, it's me that is not sure what to do on our end as I don't want to break something.
-
You need a working communication between the NFS storage and your LAN devices as you stated above. So you need a static route for your LAN on the device in the other LAN. The default route can still stay as it is and upstream traffic from the NFS may go out the neighbours gateway.
As I mentioned above, you may also do a workaround with NAT.
To do so go to Firewall > NAT > outbound. Switch into the hybrid mode, save and add a new rule:
interface: LAN2
Source: your LAN network or an alias with the two considered servers in your LAN
Translation address: interface addressIf you want you may also restrict protocol and port.
-
Adding a static route to them won't break anything unless you're really, really good.
-
So, not doubting anything since I'm already at a point where I'm not knowledgeable enough and had to ask but, I had added a virtual (alias) IP with the IP of the storage device. I wanted to point out that I can already ping the storage device on their LAN. I just can't mount it and get RPC errors.
-
But you're not really pinging that NFS server, are you? You're pinging pfSense which is pretending to be that IP address. That's what a Virtual IP - IP Alias is. I explained all this in my first post.
-
@lewis said in Allow LAN to LAN, not routing:
I had added a virtual (alias) IP with the IP of the storage device. I wanted to point out that I can already ping the storage device on their LAN.
The ping will not reach the device in the other network if the destination IP is on your own router!
Edit: Okay, KOM has the same idea and was faster.

-
Please guys, I appreciate the help, don't get impatient with me. I know you explained but this is not my network to break so am counting on you guys to help me do the right thing.
It makes sense that I can ping the IP if I added it on the local router. I had not thought about that.
Changing to hybrid won't break anything that is running now? I mean, will it require a reboot or something? Pfsense is always highly reliable and never need to reboot it but I'm asking since we are changing a 'mode'.
-
Changing the outbound NAT mode from automatic to hybrid does nothing. The automatically added rules are still in place and you're able to add manual rules.
-
NAT > outbound. Switch into the hybrid mode
Done.
save and add a new rule:
interface: LAN2The above is not clear to me. I've not create d a new interface and don't see one. I only see the usual WAN and LAN in Interface so I'm missing something before I can add rules next.
-
So the neighbours LAN is really not on an separate interface? It's connected directly to your LAN as John assumed?