Site to site VPN always forcing itself as default route in pfsense as VPN Client to CentOS VPN Server.
-
OpenVPN server running on CentOS, client on pfsense.
Setup as we would normally for site to site connection with the exception being one side is vanilla openvpn on centos, but whenever the connection comes up pfsense just attempts to route all traffic through the connection (as default gateway) and I cannot figure out what's causing the behaviour.
Even --pull-filter ignore "redirect-gateway" or any additional custom options to try and stop the behaviour is just ignored and pfsense to keeps adding the gateway as the default route.
I'm assuming is something on the centos side that causing the route change to be force but can't figure it out.
If I change from topology subnet to anything else then it doesn't change the default route but then that's causing a route issue on the centos box as its using .6 not .2 but the routes still persisting as .2 for 192.168.3.0/24
regards
DaveOpenVPN on CentOS config.
cat /etc/openvpn/server.conf
port 1194
proto udp
dev tun0
user nobody
group nobody
persist-key
persist-tun
keepalive 10 120
topology subnet
server 10.8.0.0 255.255.255.0
route "192.168.3.0 255.255.255.0"
dh none
ecdh-curve prime256v1
tls-crypt tls-crypt.key 0
crl-verify crl.pem
ca ca.crt
cert server_XXXXXXXXXX.crt
key server_XXXXXXXXXX.key
auth SHA256
cipher AES-128-GCM
ncp-ciphers AES-128-GCM
tls-server
tls-version-min 1.2
tls-cipher TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256
status /var/log/openvpn/status.log
verb 3
comp-lzo noPFSense
dev ovpnc4
verb 5
dev-type tun
dev-node /dev/tun4
writepid /var/run/openvpn_client4.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp4
cipher AES-128-GCM
auth SHA256
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
local x.x.x.x
tls-client
client
lport 0
management /var/etc/openvpn/client4.sock unix
remote add.domain.com 1194
ifconfig 10.8.0.2 10.8.0.1
route 10.8.0.0 255.255.255.0
ca /var/etc/openvpn/client4.ca
cert /var/etc/openvpn/client4.cert
key /var/etc/openvpn/client4.key
tls-crypt /var/etc/openvpn/client4.tls-crypt
ncp-ciphers AES-128-GCM
compress
resolv-retry infinite
topology subnet
--comp-lzo no
--push "comp-lzo no"
--pull-filter ignore "redirect-gateway" -
Can't find any setting in the server config that's liable for that.
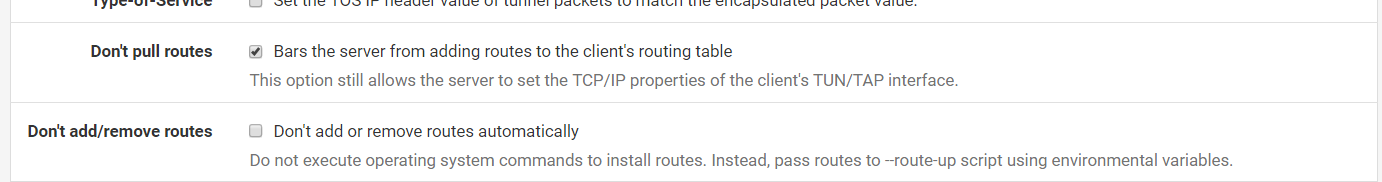
However, on pfSense you can check "Don't pull routes" to avoid adding routes pushed by the server.
-
Yes you'd think that but it does nothing unfortunately still forces itself in as the default route.
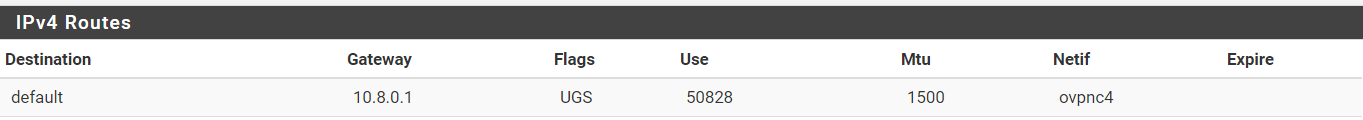
Regards
Dave -
Have you messed up the config or have you set some custom options?
I think, each setting you need here can be set by the help of the GUI. There is no need for custom options, so you'd better delete these.
The
--pull-filter ignore "redirect-gateway"option doesn't come from the GUI.
On the other hand, I'm missing
route-nopullwhich should be added to the config by checking "Don't pull routes".
The compression can be set in the GUI as well, and pushing the compression option from the client to the server is not possible anyway.
-
I have no idea if I have messed something up or if its a pfsense thing or a openvpn on centos thing.
It's been a while since I worked on a bare openVPN server without pfsense but there isn't much to set really vs using the web gui in pfsense.I have recreated the VPN twice and keep getting the same thing.
I have resolved it to some degree by telling pfsense which is the default gateway vs using the automatic option in the systems >routing >gateways page.
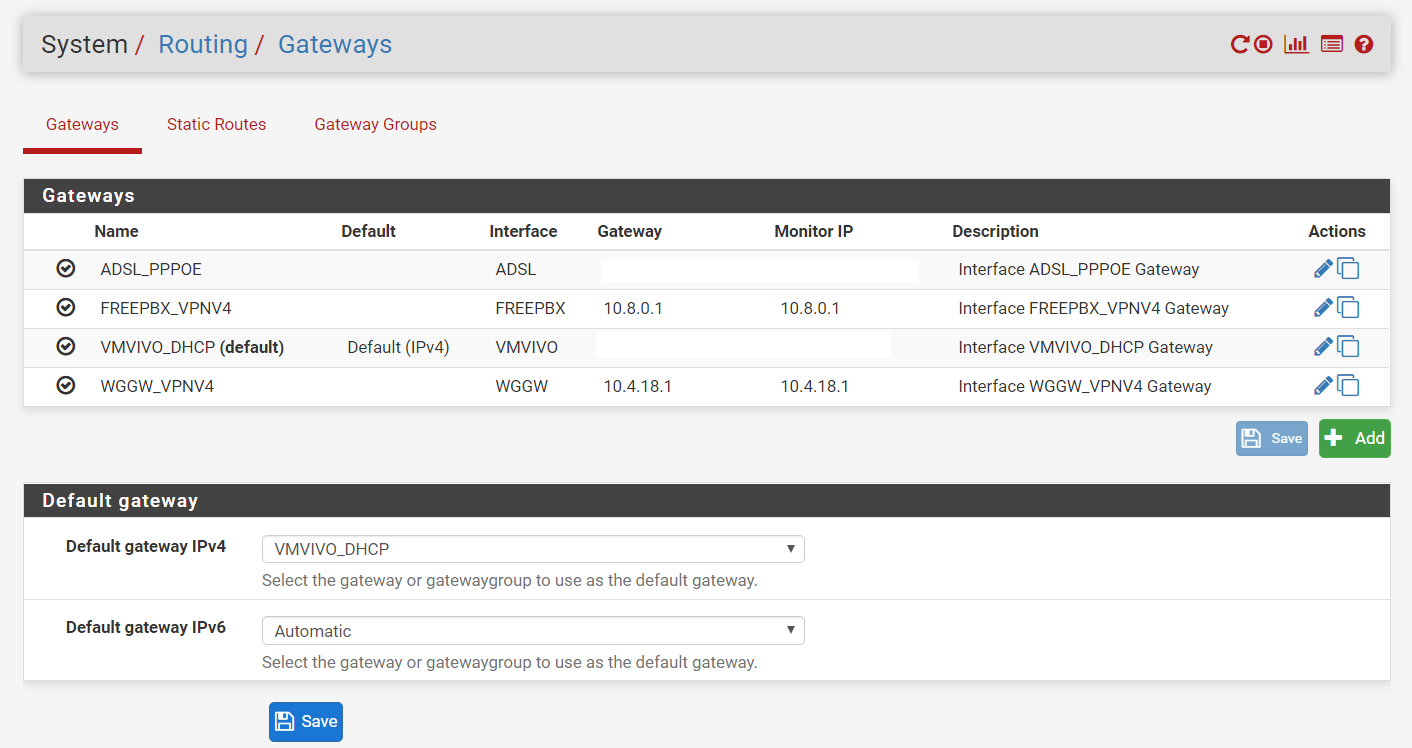
I've never had to do that before on a pfsense setup. But as I say I don't understand why the behaviour difference between this VPN and every other VPN I've ever created.Maybe I just need to sleep on it tonight. :)
Regards
Dave