proxy server is refusing connections - ICAP Error when Antivirus Enabled
-
not enought information, we realy need screenshot as most of the time people think to have done ABC and instead they do BCD
I replicated your configuration as you wrote it and it works for me without problems
there are no known bug that can do this so it must be some misconfigurationcompare with my screenshot
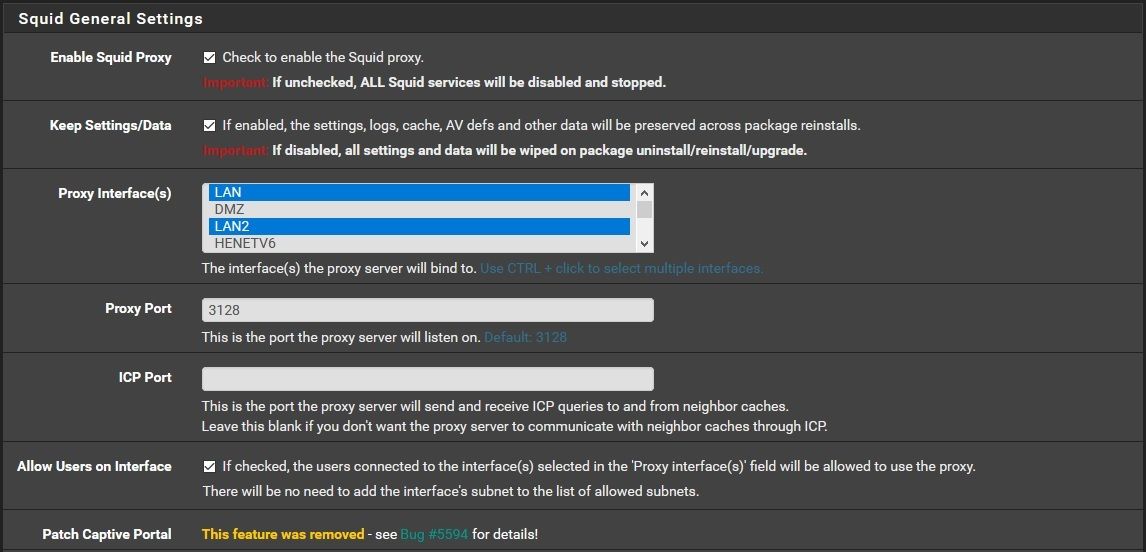
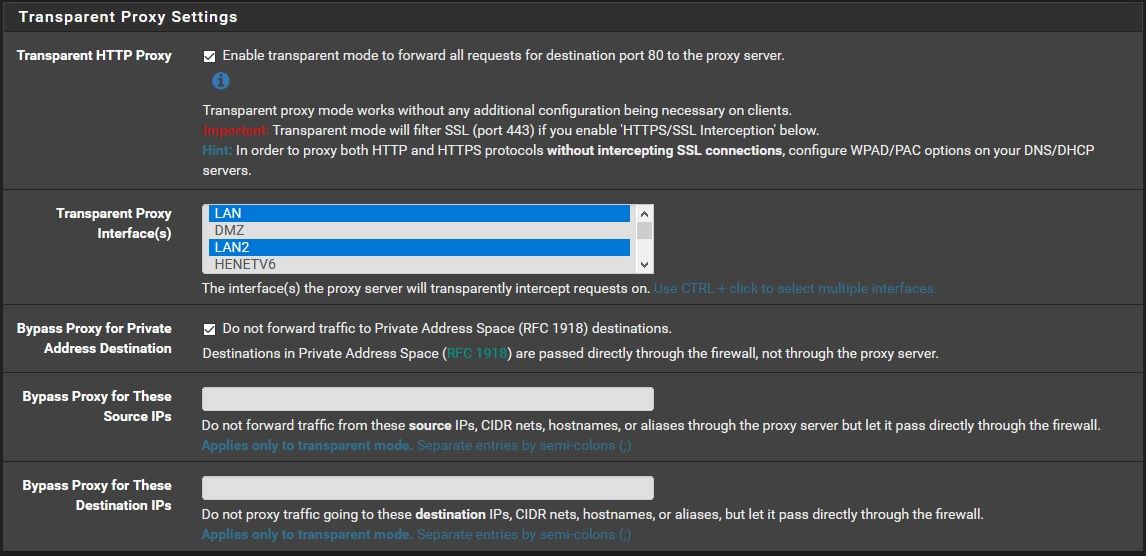
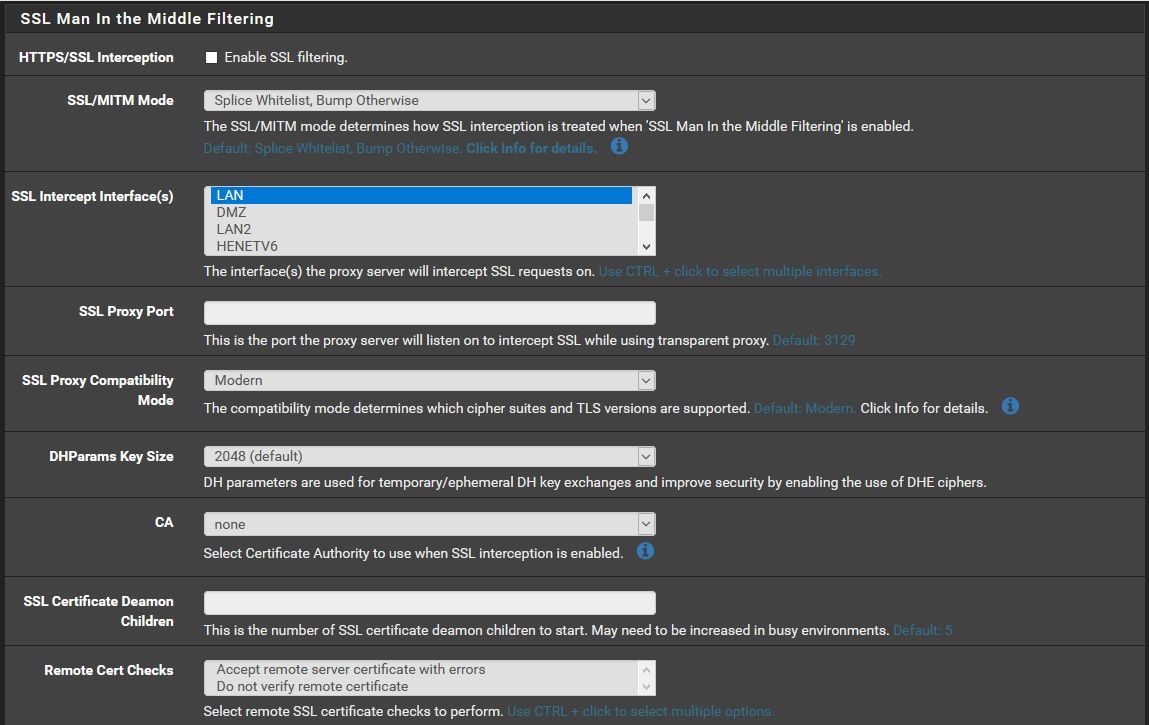
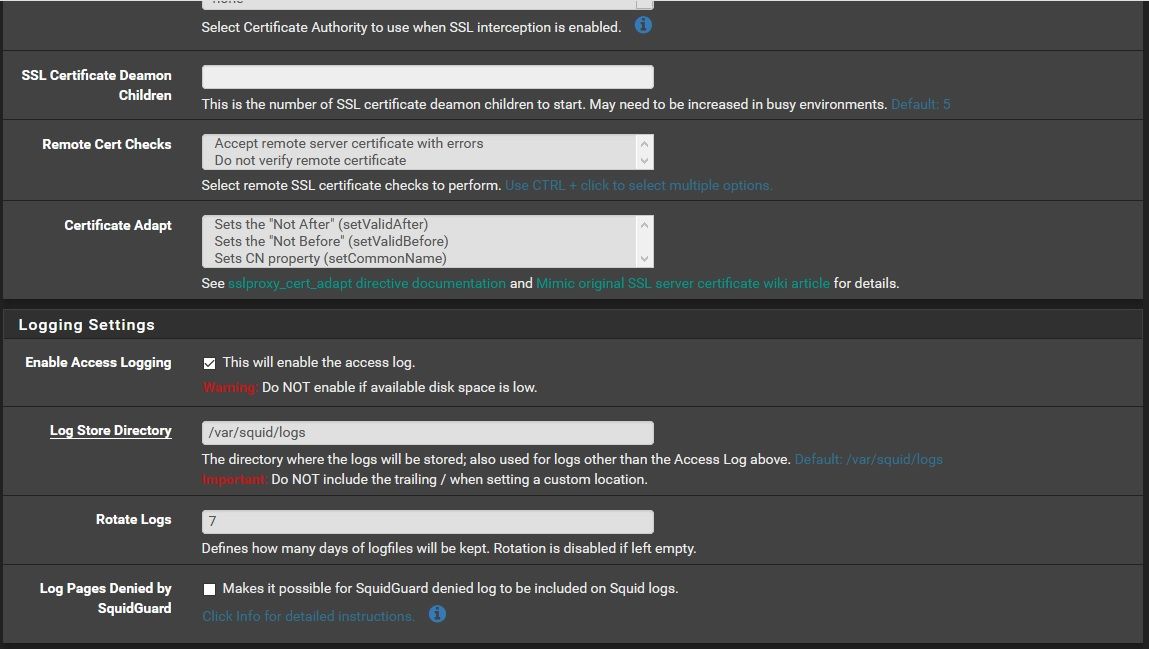
-
Example :
@gwaitsi said in proxy server is refusing connections:
I added a 3128/3129 to the allowed ports as a LAN rule
This is not needed.
Default, all incoming connections on LAN are permitted. -
@Gertjan info i provided is exactly the same as in your screenshots and pass through is required because i block all ports on lan as well.
from squid.conf is the following
acl purge method PURGE acl connect method CONNECT # Define protocols used for redirects acl HTTP proto HTTP acl HTTPS proto HTTPS acl allowed_subnets src 192.168.0.0/23 http_access allow manager localhost http_access deny manager http_access allow purge localhost http_access deny purge http_access deny !safeports http_access deny CONNECT !sslports # Always allow localhost connections http_access allow localhost acl sglog url_regex -i sgr=ACCESSDENIED http_access deny sglog # Setup allowed ACLs # Allow local network(s) on interface(s) http_access allow allowed_subnets http_access allow localnet # Default block all to be sure http_access deny allsrc icap_enable on icap_send_client_ip on icap_send_client_username off icap_client_username_encode off icap_client_username_header X-Authenticated-User icap_preview_enable on icap_preview_size 1024 icap_service service_avi_req reqmod_precache icap://127.0.0.1:1344/squid_clamav bypass=off adaptation_access service_avi_req allow all icap_service service_avi_resp respmod_precache icap://127.0.0.1:1344/squid_clamav bypass=on adaptation_access service_avi_resp allow all -
how about this part?
shutdown_lifetime 3 seconds# Allow local network(s) on interface(s) acl localnet src 192.168.1.0/24 192.168.3.0/24 192.168.2.0/24 forwarded_for on httpd_suppress_version_string on uri_whitespace strip -
@kiokoman they are there
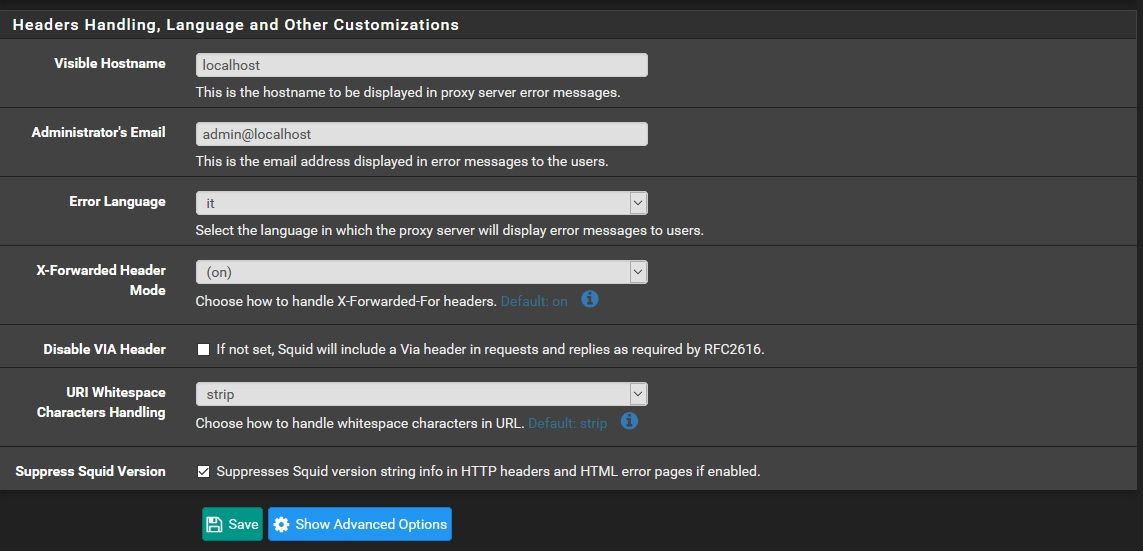
forwarded_for on
uri_whitespace stripbut i don't have this one
httpd_suppress_version_string onI don't understand it, because if i do the following on the pfsense box, i get
netstat -ln tcp4 0 0 192.168.0.1.3128 192.168.0.50.33796 ESTABLISHED tcp4 0 0 192.168.0.1.3128 192.168.0.50.33792 ESTABLISHED tcp4 0 0 192.168.0.1.3128 192.168.0.50.33788 ESTABLISHEDI have the network proxy manually set on linux mint, but firefox using no proxy when it works.
As soon as i switch to the proxy on firefox, i get the refusing connections errors.Must be something with the ACLs, but authentication is set to no.
-
if you set transparent proxy you don't need to configure proxy on web browser, all the http traffic should be automatically intercepted by squid
httpd_suppress_version_string -> not important right now
-
@kiokoman both transparent and forwarding, give the same problem on both the test and production systems.
I've had some progress. I now have HTTP caching working without Antivirus.
I added custom patterns, and checked and re-saved each of the pages (had antivirus off) and it started working.have blocked HTTP on the WAN so it is definitely going via squid and i am now seeing
TCP_TUNNEL/200 and HITS in the real-time log.Problem starts when i enable antivirus now. If i continue to browse previously cache HTTP site, i get the following.
The following error was encountered while trying to retrieve the URL: http://www.xxx.xx/ ICAP protocol error. The system returned: [No Error] This means that some aspect of the ICAP communication failed. Some possible problems are: The ICAP server is not reachable. An Illegal response was received from the ICAP server.toggle antivirus on/off, and it works, or stops with antivirus on.
-
This has to be a bug with the Antivirus/ICAP config. I have duplicated the setup on the test environment and replicated the same behavior. Simply put,
- install Squid in either transparent or forward mode (start with only HTTP) to keep it simple.
- block HTTP from the WAN
- setup the proxy manually at one or both system and/or firefox
- browse HTTP only site
With antivirus enabled, it doesn't work.
With antivirus disabled, it does work.
Using latest pfsense 2.4.4_p3
/var/log/c-icap/server.log
ERROR clientip is null, you must set 'icap_send_client_ip on' into squid.confmade the following config changes;
Included "Loopback" in the Proxy Interface
X-Forwarded Header Mode - Transparent (was - on previously)
URI Whitespace Characters Handling - set to Encode (was - strip)It is now sort of working, but still gets the occasional ICAP error per above.
-
i don't have this problem even with antivirus enabled, did you set this option after enabling it?
and pressed "Update AV" ?
but i have 2.5.0 right now that i can test
-
@kiokoman below was the solution
- add Loopback to the Proxy Interfaces
- X-Forwarded Header Mode - Transparent (was - on previously)
and importantly, there is a bug with the "Allow Users on Interface" - it doesn't work!
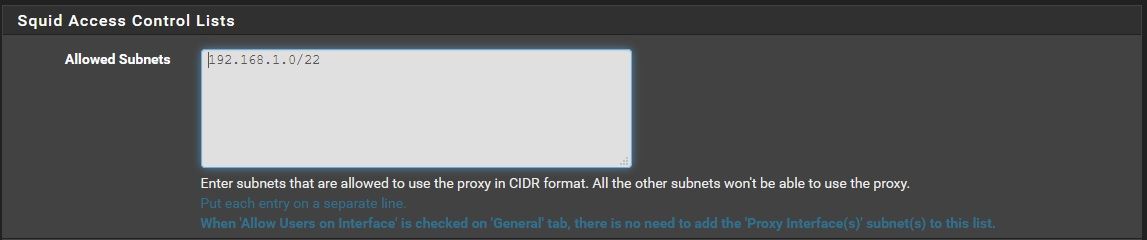
ACls - Allowed Subnet still needs to have the subnet plus the localhost
192.168.0.0/24
127.0.0.1/32another thing i found, switching from forwarding to transparent mode, it is necessary to reboot the router.
Not enough to restart the service, or the same ICAP error will occur.