Certificate Issue
-
I've created a self-signed root CA certificate for my network using OpenSSL v1.1.1 on Linux.
I have successfully imported this cert to my Linux server, several Windows systems and FreeNAS (which runs on FreeBSD, same as PFSense). However, when I attempt to install the cert on PFSense by pasting the .pem into the Web GUI form I get an error saying that the cert doesn't appear to be a CA cert.
Has anyone encountered this issue? Any workaround or suggestions?
-
Not sure why wouldn't have just used the gui cert manager in pfsense to create your CA and all your certs.
If your trying to use cert as you webgui, you wouldn't import it in the CA section.. So yeah its going to yell at you if your in the CA section trying to import a server cert.
What exactly are you trying to do with this cert you created? Why would pfsense need to trust your CA? I would think you would create server certs for your different web based guis, like psfense and use the server cert you signed with your ca, and then trusted by your browser.
If you did create a CA, then yeah the certs can be installed in pfsense.
-
I didn't use the PFSense cert manager because I'm actually generating two self-signed certs - a root CA cert and a server cert with multiple SANs. As far as I can see, the Web GUI is somewhat limited and doesn't include the ability to add SANs to a cert. Also, I'm familiar with using OpenSSL to generate certs in my daily work, although this cert is for my family network.
I did attempt to import it to the CA section - otherwise I wouldn't have the error I described "This doesn't appear to be a CA cert" that I mentioned in the original post.
The cert is to allow all my servers to be trusted in the network. Which means a single self-signed root cert and a self-signed server cert for each of my servers. That's why I'm using a multiple SAN server cert. By installing the CA cert in each of the family's systems, the servers will be trusted in network.
I have validated both my generated certs by using them on Linux and FreeNAS servers with Windows clients. My PFSense boxes (primary and failover) are the only places that are problematic because they will not import the CA cert.
-
Anything in the System log?
-
@maldemer said in Certificate Issue:
As far as I can see, the Web GUI is somewhat limited and doesn't include the ability to add SANs to a cert.
Not sure where your looking.. All of my certs I create have multiple SANs on them - for IPs and name, etc..
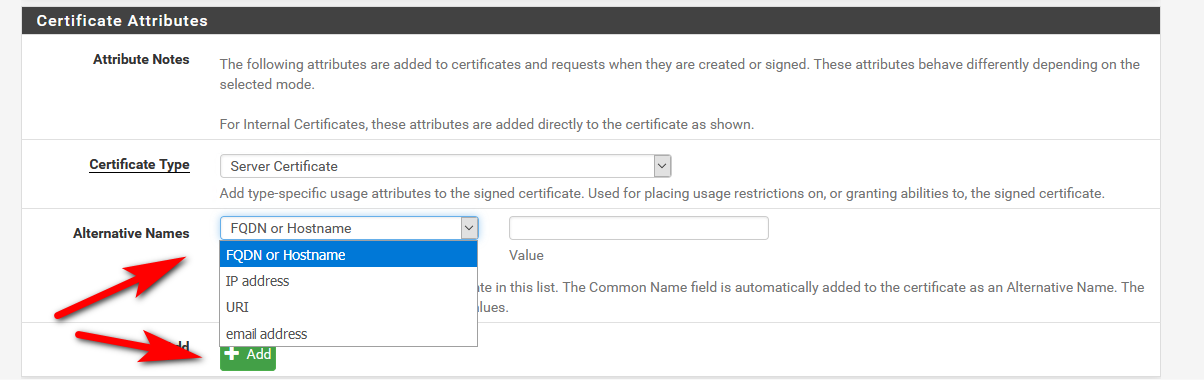
You would create the CA on pfsense, and then sign whatever sort of certs you want -- all in the simple to use gui.
How did you create your CA - what is the exact command you ran, and I will try and duplicate your issue here.. I have imported many a CA cert into the manager without any issues.
Which means a single self-signed root cert and a self-signed server cert for each of my servers.
No not really... You sure do not need to install the CA on any box that is just using your cert for its https services.. I have certs installed on my cisco switches so my browser trusts them - they don't have the CA certs installed on them.
Once you create a CA, you can sign off on certs from that CA... In your browser you would trust anything signed by that CA, so now any https/tls gui you access would be trusted by that browser, etc.
-
So i just created a CA with openssl 1.1.1 and imported it into pfsense cert manager just fine.
user@clean18:~$ openssl version OpenSSL 1.1.1 11 Sep 2018 user@clean18:~$Did this
openssl genrsa -out rootCA.key 4096then
openssl req -x509 -new -nodes -key rootCA.key -sha256 -days 1024 -out rootCA.crtThen copied the rootCA.crt to pfsense web gui for importing CAs
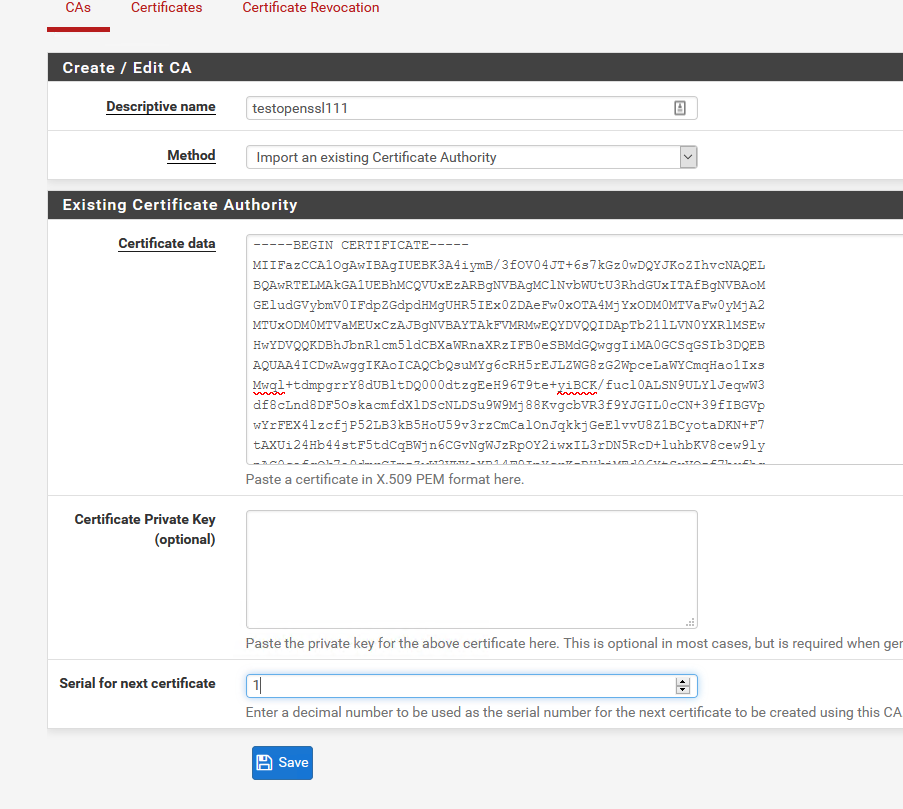
Bob's Your Uncle!
-
While I'm sure he could do it all with in the GUI, I'm curious as to why certs that works elsewhere don't work here.
-
No idea - because he has provided no info to go on.. Once he says how he created his CA in openssl I can try and duplicate.
But I have imported many a CA into pfsense via the gui, never an issue... Could be something as simple as bad copy past.. He not grabbing the last line or missing the first line, etc.
As you can see, created a CA, imported it into pfsense in like 2.3 seconds with zero issues.
That he thinks he even needs to install his CA into pfsense.. He doesn't need to do that to use an SSL for the web gui.. Not sure what he thinks its getting him installing the CA into pfsense.. Doesn't make any sense from what I can make of his use case.
-
Last time I did it was 2 weeks ago when I spun up an IPSec site to site. I had no problem importing each site's CA cert into the other end. I wonder if this is another stupid LF/CR type thing.
-
I just did another test with making sure to do the V3 ext when creating the ca cert..
-reqexts v3_req -extensions v3_ca
imported just fine as well.. Maybe he encrypted the damn thing? No idea what he is doing wrong.. Or maybe he is doing something odd?? Simple enough for him to show us his openssl command so we can try and duplicate it.
-
Thanks for the replies, everyone.
Here's how I created the root CA cert with OpenSSL - first creating the key, then the cert itself.
openssl genrsa -out rootCA.key 2048
openssl req -X509 -new -nodes -key rootCA.key -sha256 -days 3650 -out rootCA.pemThe resulting .pem fails to install on PFSense with the error "this does not appear to a CA cert". I also created a server cert which is a little more involved as it involved creating a config file for the SANs. That file installs as a server cert without any problems.
After posting my original message, I created a similar cert on a Windows server using PowerShell like this:
$Params = @{
DnsName = "Root CA Certificate"
FriendlyName = "Root CA Certificate"
KeyUsage = 'CertSign', 'CRLSign'
KeyLength = 2048
KeyAlgorithm = 'RSA'
HashAlgorithm = 'SHA256'
NotAfter = (Get-Date).AddYears(10)
KeyExportPolicy = 'Exportable'
CertStoreLocation = 'Cert:\LocalMachine\My'
}
$rootCA = New-SelfSignedCertificate @Params
Export-Certificate -Cert $rootCA -FilePath "C:\Users\xxxx\rootCA.crt"
Get-ChildItem Cert:\LocalMachine\my | where-Object { $_.Subject -match 'Root CA' } | remove-ItemI then converted the .crt file to a ,pem using
openssl x509 -inform DER -in rootCA.crt -out rootCA.pem
The output .pem file also fails to install on PFSense with the same error message.
I failed to notice the option on the server cert page in PFSense to include SAN addresses - my mistake. But since the server cert installs without an issue that's not relevant here.
I can create another CA file on PFSense and then a server cert and install the CA cert on the two systems that might be used for access to PFSense. That will work around the issue, but it's still an issue that should be root caused. I hope it's something I failed to include.
-
@johnpoz is using a 4096 bit-length. Try that and see if it makes any difference.
-
It's not an issue with the very LOW key length.. I just tested with that as well..
Is your browser dicking with the paste? How are you copy pasting the cert..
Can you create a new test CA and cert and post them here?
Example - here is my test CA can you import that?
-----BEGIN CERTIFICATE----- MIIFazCCA1OgAwIBAgIUKD7MuXi3jDRuXZCxXUV6bEIZ61AwDQYJKoZIhvcNAQEL BQAwRTELMAkGA1UEBhMCQVUxEzARBgNVBAgMClNvbWUtU3RhdGUxITAfBgNVBAoM GEludGVybmV0IFdpZGdpdHMgUHR5IEx0ZDAeFw0xOTA4MjYxOTIzMjJaFw0yMjA2 MTUxOTIzMjJaMEUxCzAJBgNVBAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEw HwYDVQQKDBhJbnRlcm5ldCBXaWRnaXRzIFB0eSBMdGQwggIiMA0GCSqGSIb3DQEB AQUAA4ICDwAwggIKAoICAQCbQsuMYg6cRH5rEJLZWG8zG2WpceLaWYCmqHao1Ixs Mwql+tdmpgrrY8dUBltDQ000dtzgEeH96T9te+yiBCK/fucl0ALSN9ULYlJeqwW3 df8cLnd8DF5OskacmfdXlDScNLDSu9W9Mj88KvgcbVR3f9YJGIL0cCN+39fIBGVp wYrFEX4lzcfjP52LB3kB5HoU59v3rzCmCalOnJqkkjGeElvvU8Z1BCyotaDKN+F7 tAXUi24Hb44stF5tdCqBWjn6CGvNgWJzRpOY2iwxIL3rDN5RcD+luhbKV8cew9ly nAC0cafgQk7a9dmrCImzZwW3VWYeXB14F9IpYcrKzRHkjMEd06YtSxVQzf7byfhg 4VwO2NJ0nO8jaYDSEJEaBgxMSiFQTDCCGMCEM9oncBMMHBGIo59UAj0AoM2ghfqP RadTjekk4nx4SEiHhpfjzPrxCWMjKZeT/q36xVXC5AtfqezZ1SOXK2AaSi7UkS3q 7mOmsGlSE1ldm1ggRRzXZRnyAkIABssqpPIRwWyrGVJScQayc19uKsFDoOCtF0O4 07bmUDVT6yj6FQMQEj7WUfvod68mGXWCRZfoNDCPDVPBBerLmAC0oep1h7BvuMxt 5kGy2BThZnxPjKtnkYInU3WV33ADJRIFUXlduIFtzQ0G0ktYp8y9yXyzj9reT0i4 gwIDAQABo1MwUTAdBgNVHQ4EFgQUw6ItKlScMposq/1b19RIUz8TSIowHwYDVR0j BBgwFoAUw6ItKlScMposq/1b19RIUz8TSIowDwYDVR0TAQH/BAUwAwEB/zANBgkq hkiG9w0BAQsFAAOCAgEAb7pNOhP3PHgBQ9TxX+ClxoBNlGNChCyvDZmsbmlpKTrA +Vouuwl7tUFELQHffHghdklRV1OI4HAxupd1HtdBpqMc2vTWXWi1+E9qiXuKUdWG RXVRZbpj3yalxPdX5BrJdeNDwp7+Yc3reudgBheZBQSKb8Pc1nmLTxj2f280A1vk rFBBJOB6Puo+KYr2EXpeROIqk0LKxmcfK5V9Hd2Ppr23z9Q3IrIRnYGC3097xLET hshN3XuzXNYBuYcoE4/C3XTXqzo8FBcrD13URi9MSeZrn8pjBlbcS+IjOV/4f0H9 zwzSutw7xAXhqYKYDf3jlJoOutpl9rIxwW74akh6NaZCKztykLL0FpUceJE5g0IB kBQDNuxxQ+eJDUVo/sNj9KaZ58+XpAwXExmc64rOZsGZUgoSMauo8bY09IaVIt0g HjMxvHQB/DLJtLTbGf+QNWcYRrhBHfYB8l46jmLunlC3gRjB6C/d7247gL29ZfXD GvkUSVmy+VVqes5gpcuATVTADfVzUu+z3uSWpj/NDKP4ZWukIxhtVoLykSfQSk1i 0sYCCbBqwm5jBB564AnsMNCrZCFi43k3PjVD3bB5AZS6dPd2nr53K3uk2UQP+BU0 6Ud1tECP2u3zUiUO1hH+OwncaZ+dC7ln0bW11Z9Xt3gPt90SbGJZUc0QznIfo0Q= -----END CERTIFICATE-----You are grabbing all of it right, the Begin and End Certificate lines for your paste?
-
Standard copy/paste from a Linux system into PFSense, so no CR/LF issues. Both the header and trailer are there.
Also, same result with 4096 bit key. incidentally, the key length only matters when the cert is used in a trust setting - not relevant here.
Going to rebuild PFSense box this evening, in case it's a weird corruption issue, now that I know others aren't seeing the same issue.
-
Can you copy paste the one I posted.
edit: as to the key length.. There is no real security issue for this use case no, but I normally make my CAs for 10 years or so min.. Since its not a issue with anything I am doing with them - I tend to go on the larger size..
But sure my use of cap low might of been a bit misleading ;)
You have something wrong that is clear - I doubt its a corruption sort of problem in pfsense, but if can not duplicate it going to be hard to point to what it actually is.
I would be curious for you to post up a test CA cert that I can try to import into pfsense, and would be curious if you can import the one I posted.
-
Issue resolved. I took my primary PFSense box offline and the failover box kicked in. I tried installing the cert I created on that box and it worked! Obviously I have a system problem rather than the software issue I thought I had.
My apologies to all, especially @johnpoz, for all the wasted time looking at the problem.
-
Looking into issues is never wasted time.. Something really odd for sure going on - have never seen such an issue before.. Which are always the fun ones!
Would be better to try and figure out what exactly is wrong with the install that could be causing such an issue - there are no errors in the log at all? Was this a clean install, or an update? Was it restored from a backup xml from a different or older system, etc.?
Let us know when you have your primary working again.