smart devices not being stopped with rules
-
I have 4 smart plugs (tuya) which I have installed in a VLAN for IOT devices. I created an alias for them: TuyaDevices.
I set a rule in the IOT VLAN to prevent them from going to the WAN on all ports and ipv4 and ipv6 but I can still turn them on and off from my phone not on WiFi.I am trying to let them operate within the IOT VLAN but not to go to the web nor the local LAN. I can then VPN and turn them on and off via Home Assistant also on the IOT VLAN. I can currently do that with my other IOT devices which I do not need to block from using the web.
Any recommendations? I tried the same rule then on both LAN and IOT and then a rule on WAN to prevent access to that alias and they still work.
-
Rules are applied to the interface that the traffic enters, so if you want to control your IoT devices on VLAN X, then you need to put your rules on the VLAN X interface.
-
Thank you for the prompt reply.
I tried 2 different rules in the IOT interface. The first one was only ipv4 and then this:
Action: Block
Interface: IOT
Address Family: ipv4 +ipv6 (in case the devices ever send something in ipv6)
Protocol: Any (not sure if they only use one so I cover all)Source: Single Alias - TuyaDevices
Destination: WAN netThen Applied and reloaded.
I can still use them from my phone not on wifi
IOT can be seen by my LAN devices but it can't send traffic back unless it has been requested (cameras for example).
Any thoughts? What am I missing?
-
Your rule is wrong. Destination should be * (any). WAN net is literally the WAN subnet only. Also, if you're only using IP4 on your network then go to System - Advanced - Networking and uncheck the Allow IPv6 box. Now for Address Family you only need to select IP4 since IP6 is blocked already.
Make sure to reset your states for all IoT devices after you make a rule change via Diagnostics - States. Filter for your IoT subnet states and then kill them all. Now try your tests again.
-
@KOM thank you!
This definitely blocked it.
Now on my quest to allow it to bused via the IOT VLAN. This did also block that but at least is a step to my final goal.
Thanks
Unless you have another suggestion how to allow it to be used via the VLAN.
Thanks again.
-
@alfaro said in smart devices not being stopped with rules:
Now on my quest to allow it to bused via the IOT VLAN
Sorry, what? What are you trying to do exactly?
-
@KOM I want the switches to be active but not via the TUYA cloud.
I can see them already in Home assistant which is on the same IOT VLAN - I can control my smart devices that way.
I am trying to cut them off from the web (above mentioned switches) so I can still see them in VLAN and operate them with Home assistant. I VPN in and turn them on and off or setup automation. It all happens with no cloud access. This devices seem to not operate once the destination "any" is set. I figured by just blocking WAN net or WAN address they would operate within the VLAN but would be unable to get out to the cloud.
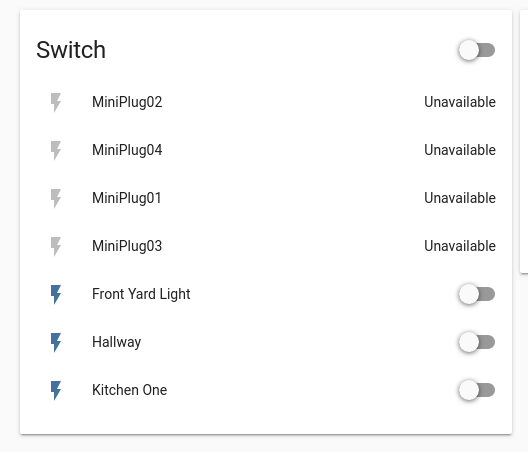
You can see that by blocking the "any" destination they are now unavailable. I am testing different rules as we are exchagning messages to see which way i can open it up just a bit while blocking the internet. -
@KOM when i block everything but "IOT net" as destination is the same thing as "any". When I block only anything but: "IOT address" it gives them internet access again
-
OK, first off the way networking works is that devices on the same network communicate directly with each other and do not involve pfSense at all. Only if the destination traffic is out of the local network will your device pass it to its default gateway and be routed out to the Internet.
If this switch thingy stops working as soon as you block its Internet access then it looks like it needs access to function. Look at the firewall log for block on your IoT interface. Do any have a source IP of your switch thingy?
Post a screenshot of your IoT rules so I can see what you're doing.
-
@KOM
i think you hit the nail on the head. I figured I could do with those devices what I did with the VLAN. My IOT VLAN can't look into my LAN where my LAN can look into the VLAN and request information such as vides streaming from security cameras. The IOT devices can't initiate traffic to the LAN which I was hoping to do with those switches/plugs.I see the thing sending a UDP packet to the gateway
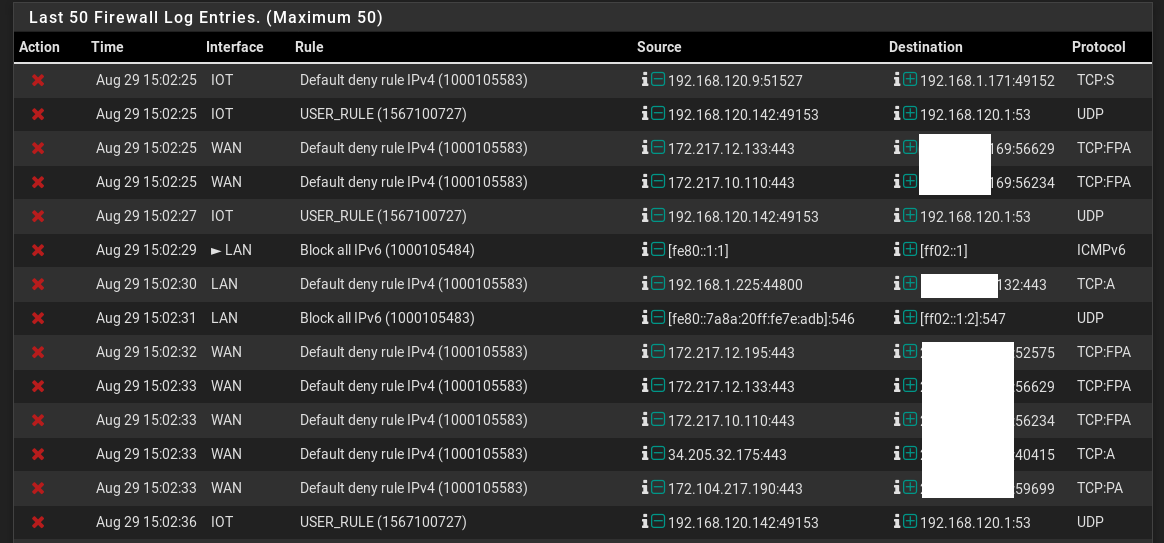
Second, fitht and last line.
Sorry I blocked my wan ip since many more people might be seeing this message.
Might be time to look at this company if it requires the plugs to have internet access.
Thanks for all the help.
-
@KOM iot rules here
sorry didn't post before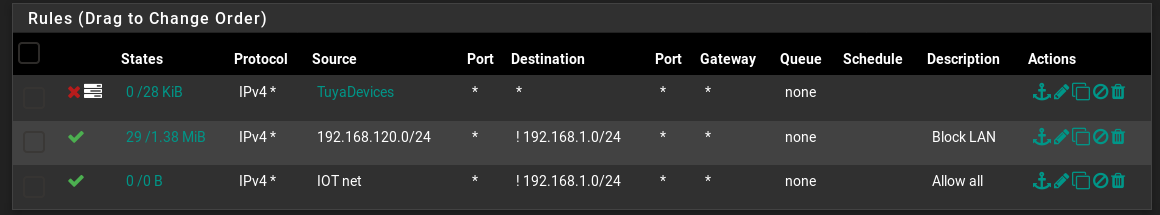
-
Your last rule is irrelevant since the second rule will pass all traffic from the subnet except to LAN.
I might suggest that you replace your Allow rule with a negator (!) with an explicit block rule. It's much easier to read that way and is less confusing.
Block Tunya to *
Block IoT_net to LAN_net
Allow IoT_net to * -
@KOM Thank you sir.
Will have to try that in just a bit as I am stepping out but will tackle this when I get back.
Thank you, you have been most helpful.
-
I'm guessing your "smart" plugs are talking to a mother ship somewhere. If they are Alexa or Google Home enabled, they need to get their commands to function from some AI server out in the cloud. If you have severed or blocked that access/path... they aren't going to work. This is the way Apple's Siri environment works. You speak commands or questions to the device, it sends that voice data to the cloud to be AI processed, then the server(s) send the data back to your device.
Am I thinking of this the right way?
They probably have to have internet access to function properly, maybe even at all. Why don't you just setup pfsense to allow them to bounce around in your IOT network, block them from all other internal LAN networks, and allow them to talk (maybe with limited port traffic stuff) out to the web/internet. @KOM suggested above essentially this setup.
Jeff