Certificat Front End/ Back End
-
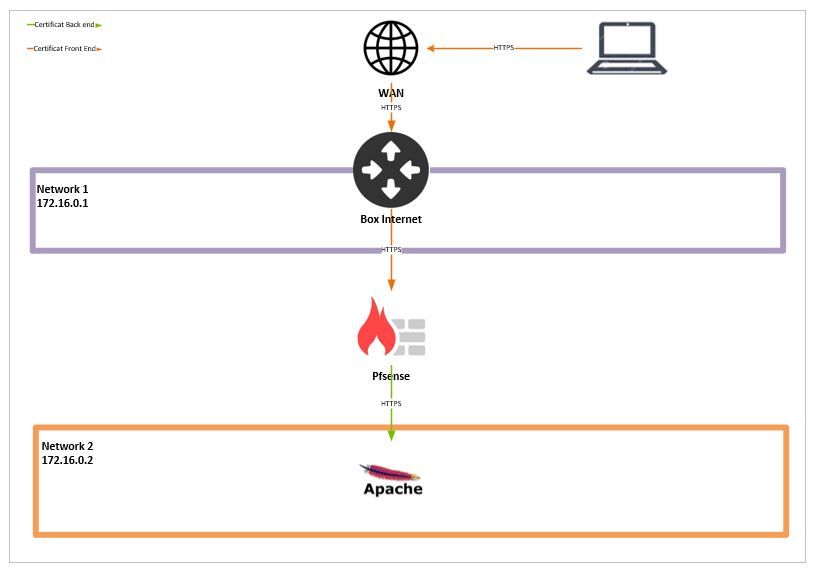
-
From your drawing your putting the same network on both sides of pfsense.. You want this to be a transparent bridge firewall? How exactly do you expect that to be a proxy then for your backend?
You understand that changing the very act of changing cert (ssl/tls) anywhere in the middle between server and client actually makes the system less secure.. because now there is a device in the middle that will see the traffic in the clear.
What do you think changing the cert in the middle gets from a security standpoint?
-
@johnpoz said in Certificat Front End/ Back End:
From your drawing your putting the same network on both sides of pfsense.. You want this to be a transparent bridge firewall? How exactly do you expect that to be a proxy then for your backend?
You understand that changing the very act of changing cert (ssl/tls) anywhere in the middle between server and client actually makes the system less secure.. because now there is a device in the middle that will see the traffic in the clear.
What do you think changing the cert in the middle gets from a security standpoint?
Thanks for your response.
I want use the reverse proxy for analyse data beetween client and reverse proxy(front end) and after encrypt the data to webserver(back end).
It is possible to do this with pfsense ?
-
Sure you can.. But you wouldn't do it with a transparent bridge like your showing.
The HA proxy package of pfsense can do this quite easy.. So you want to MITM the connection - which has zero to do with actual security ;) If your on the backend or the frontend of this connection you already have the means to see the data.
You can ssl offload the to the ha proxy, and then have it send the data on to your backend either clear or over ssl. Using whatever cert you want to use.
-
@johnpoz said in Certificat Front End/ Back End:
Sure you can.. But you wouldn't do it with a transparent bridge like your showing.
The HA proxy package of pfsense can do this quite easy.. So you want to MITM the connection - which has zero to do with actual security ;) If your on the backend or the frontend of this connection you already have the means to see the data.
You can ssl offload the to the ha proxy, and then have it send the data on to your backend either clear or over ssl. Using whatever cert you want to use.
When I read the recommendation from ANSSI( https://www.ssi.gouv.fr/guide/recommandations-de-securite-concernant-lanalyse-des-flux-https/), they recommand :
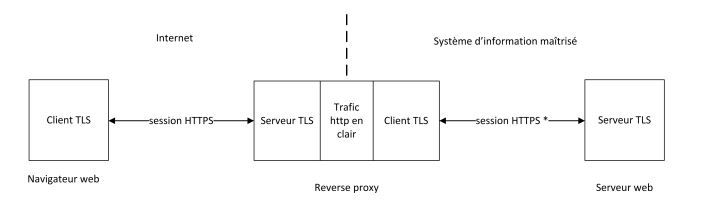 You think is not a good idea ?
You think is not a good idea ? -
No I don't.. MITM is breaking the designed security of ssl/tls. Which is meant to be end-end client to server. And sure doesn't meet PCI compliance for example..
Just ask the internet what they think about MITM - which is what Kazakhstan gov is doing ;)
https://blog.mozilla.org/blog/2019/08/21/mozilla-takes-action-to-protect-users-in-kazakhstan/If your goal is "spying" then sure its a great idea!
Is your goal to spy on you users - you know intercept their back logins, medial record access, etc. There technical reasons why you would offload the ssl connection to a different box - security would not be one of them. Other than say the end server doesn't support or can not run https, so you offload that sort of thing.
At any point you intercept the stream and decode it (so you can view it).. .How does that make the end user feel more secure?
Is your backend not secure? If what you want is to offload the ssl to something else, and put your server behind a reverse proxy ok sure.. Its your server - but what is the pointy of ssl to the backend then - unless your backend is not secure? But yes you can do what your describing -- I do it for my plex server actually? and my ombi server (I just offload the ssl to the ha proxy) the connection to the backend is just then http. With my plex, since behind a cloudflare reverse proxy, and then my ha proxy to be able to share the 443 port it is technically doing mitm... But its just easier - its using whatever cert plex is serving up, etc. And its my server sort of thing.. So the reasons its being done is pure technical in the case of plex.
While the case of ombi in my case its more secure because now the traffic is encrypted over the public internet via ssl, but not on my backend because my backend is secure and the ombi system doesn't have native ssl support, etc.
I didn't not put i a reverse proxy and do mitm on it because its "more" secure then just direct connections to the server - I did the mitm to be able to share the 443 port with other services, etc.