Failover Internet - Just for two clients on the network.
-
Lately our internet provider has been going down a lot, though we have two lines coming in, its off of the same provider (one for static IP's and slower internet, the other for normal traffic faster internet).
Because of this, we do have two clients on the network that always need an internet connection.
We do have a 4G Hotspot lying around with an Eithernet LAN port on it that we manually switch over to. But I want to make this a seamless transition.
I would like to know how you would set this up? I have only have part of an idea: It would be to set up a VLAN with DHCP that these devices can connect to, but then past that, I am not sure how to tell the router that when there is no internet to failover just this VLAN only to this hotspot connection device, but only allow the devices on the VLAN to be able to use this hotspot.
Suggestions?
-
Usually failover is accomplished with gateway groups made up of 2 or more WANs, but I don't know of any way to dynamically restrict user access based on gateway status.
-
Just make a failover gateway group that does whatever you want these hosts to have and place rule(s) higher in the inside rule set that policy route traffic sourced from these two hosts to that group.
-
OK I get it. You have the existing default gateway, and then you create a gateway group with the default and the 4G hotspot in it. I was stuck thinking about it from the point of only one gateway.
-
This post is deleted! -
@Derelict Here is what I did:
- Went to Interface > AssignmentsAdded my interface (an empty port now connected to my 4G modem), called this Backup4G
- Then went to System > Routing > Gateway Groups > Created a new Gateway:
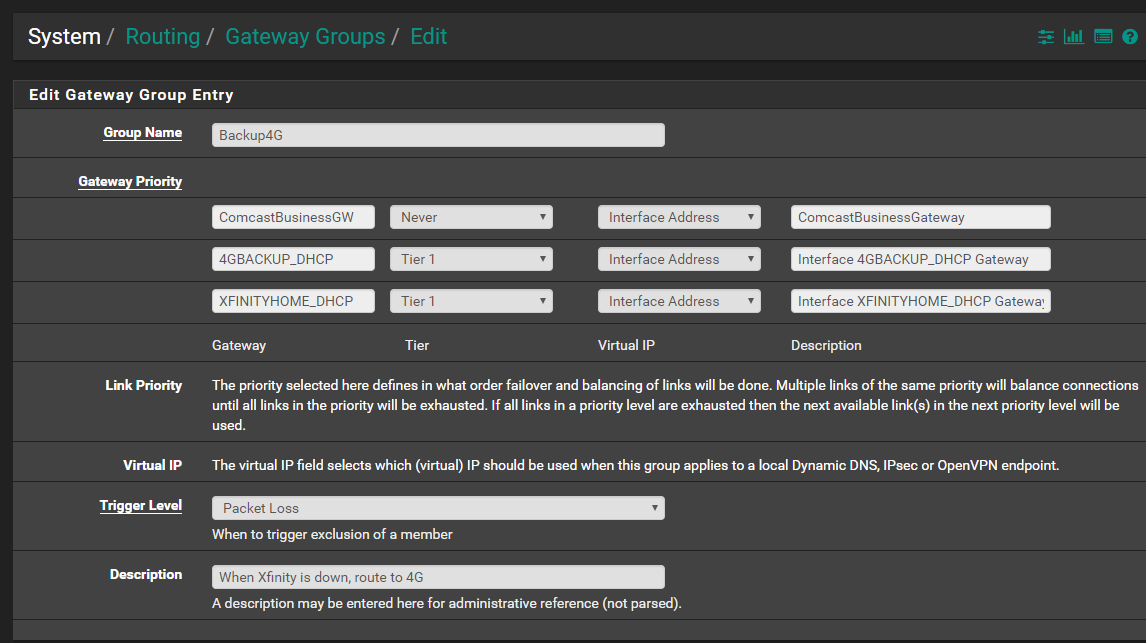
- Went to Firewall > Rules > Add (at the top) >
- Interface: Lan
- Protocol: Any
- Source: Single host or alias: Selected a PC's IP in my network
- Destination: Any
- Advanced Options: Gateway: "Backup4G - When Xfinity is down, route to 4G" (The Gateway Group that I created)
Is this correct? When I turn off the Xfinity modem, it does not fail over.
-
With both WANs on Tier 1 you have create a Load Balanced gateway group, not a failover.
https://docs.netgate.com/pfsense/en/latest/book/multiwan/index.html
-
@Derelict not really sure what you mean.
-
The guide says:
Gateways that are load balanced will automatically failover between each other. When a gateway fails it is removed from the group, so in this case if any one of A, B, or C went down, the firewall would load balance between the remaining online gateways.
which would lead me to believe that it should failover to the other member and remove the bad member.
-
https://docs.netgate.com/pfsense/en/latest/book/multiwan/index.html
-
@KOM said in Failover Internet - Just for two clients on the network.:
The guide says:
Gateways that are load balanced will automatically failover between each other. When a gateway fails it is removed from the group, so in this case if any one of A, B, or C went down, the firewall would load balance between the remaining online gateways.
which would lead me to believe that it should failover to the other member and remove the bad member.
That would assume that the gateway monitors would accurately represent what can pass traffic.
When OP posts he wants failover and presents load balance, I have to question the solution.
-
@billsecond Anything in the System log or Gateway log that confirms the bad gateway was detected as down? If you really want it to primarily use the Xfinity link and failover to the 4G, then set the 4G tier to 2.
-
@KOM @Derelict, Thanks for all of your help, I took a combination of what you said and applied! For future reference, here is what I ended up doing...
- Interface > Assignments > Added my new 4G modem, kept everything as the defaults:
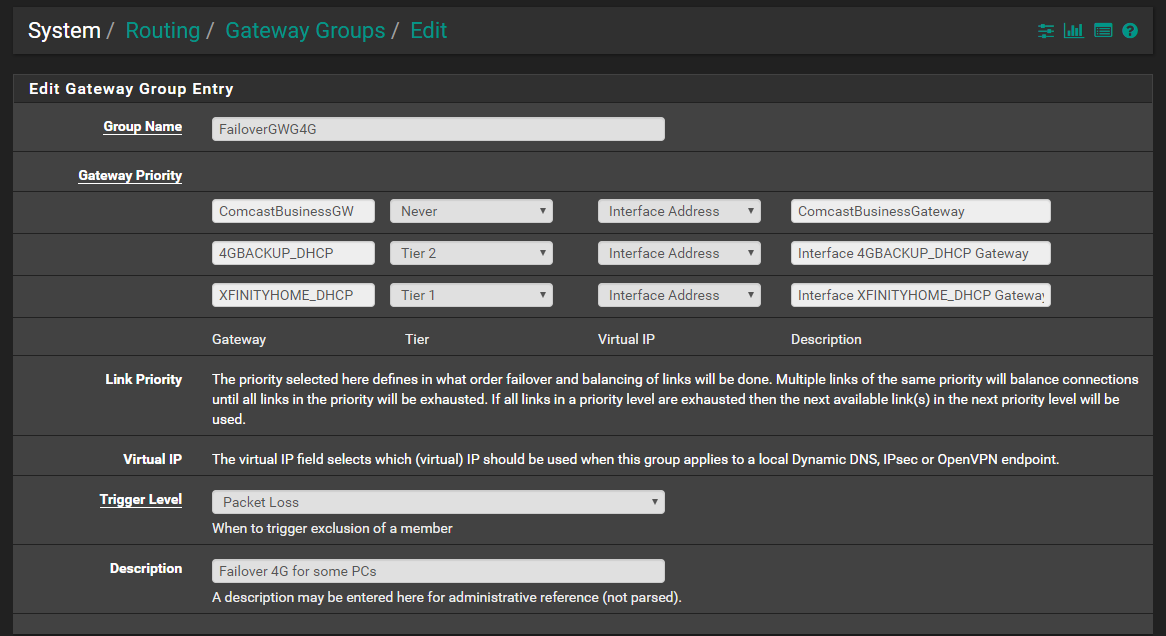
- System > Routing > Gateway Groups > Created a new Gateway Group, Set a Tier 1, and Tier 2 (this is priority based on what I was reading, let me know if it is incorrect, it is working)
- Firewall > Rules > Lan > Add (top or bottom, we have to adjust it later)
- Interface: Lan
- Protocol: Any
- Source: Single host or alias: Selected a PC's IP in my network
- Direction: Any
- Advanced Options
- Gateway: Added my new Failover Gateway Group
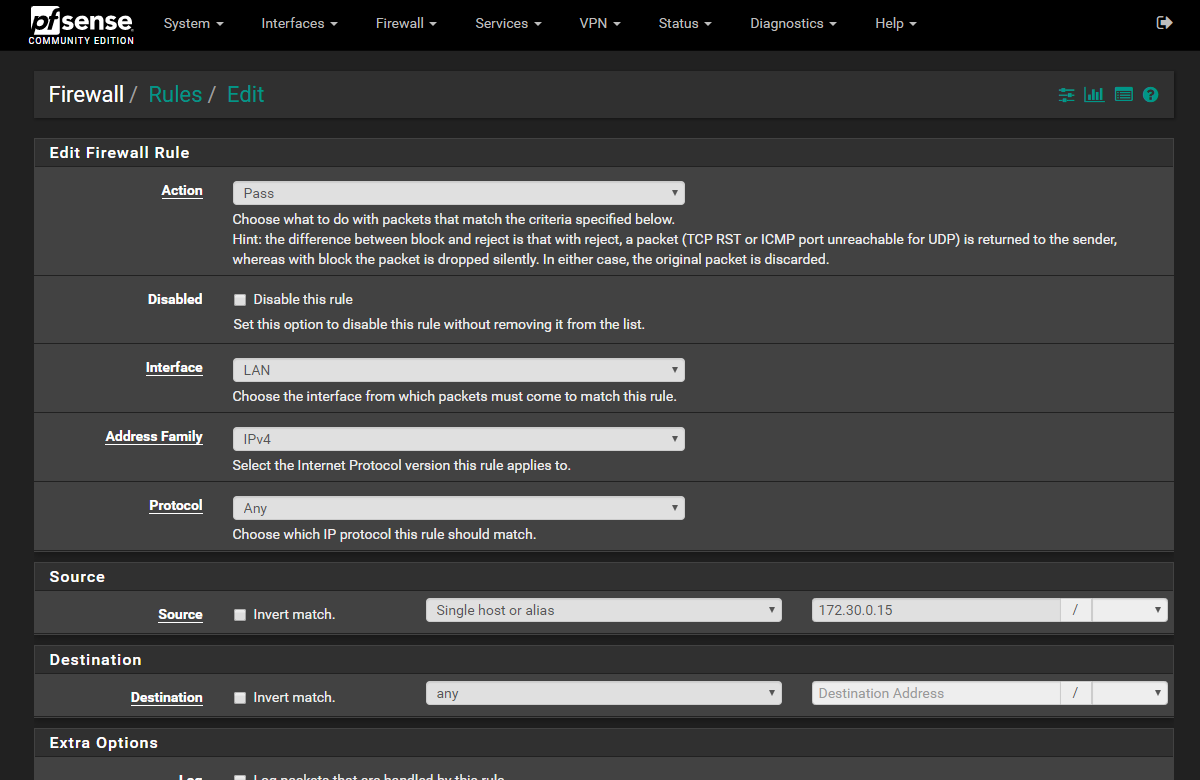
- Ordered the priority of the Failover PC's above the other traffic, but set the other traffic to go over the normal fast default gateway
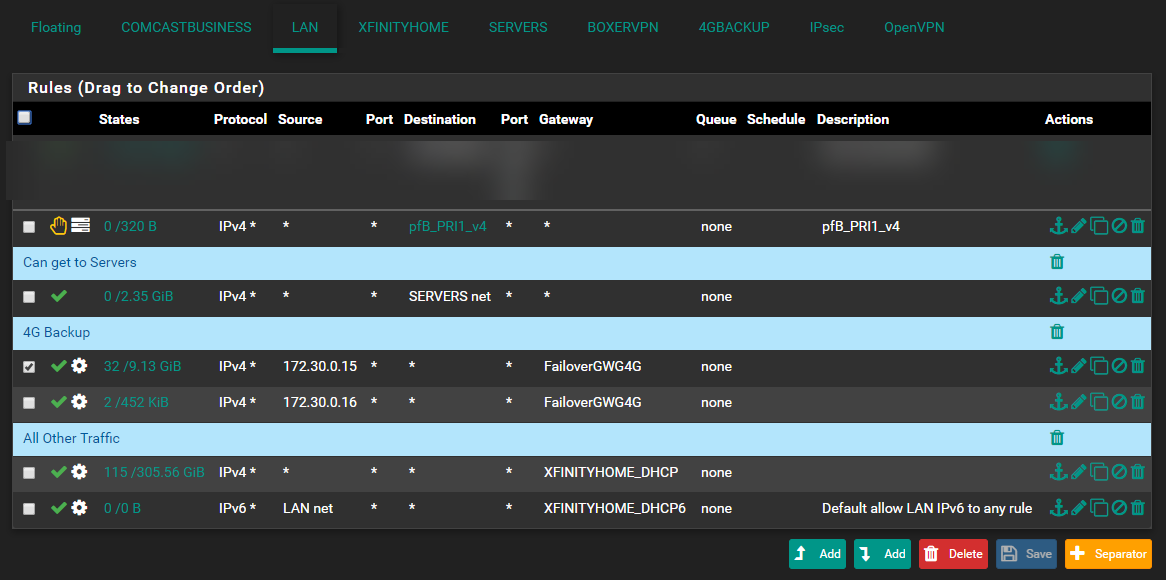
Please validate that I did this right and didn't screw anything up. It does work!
- Interface > Assignments > Added my new 4G modem, kept everything as the defaults:
-
Looks good to me. One thing to note IIRC is that if a failover happens and the tier 1 member comes back online, it won't switch back automatically.
-
@KOM How do I switch it back automatically?
-
I'm not aware of any way to do it in the GUI. I've read about some scripts that you can configure to run on a gateway up event but I've never tried them. I think I have a copy of them floating around somewhere, maybe at work. Google it and maybe you will find something. Or I could be entirely wrong and giving you old information. Test it and see what happens.
-
It WILL switch back automatically but it will not kill states that were established over the Tier 2 WAN so that traffic will continue to flow there.
New states will use the Tier 1 WAN.
-
Thanks for the clarification.
-
@Derelict said in Failover Internet - Just for two clients on the network.:
It WILL switch back automatically but it will not kill states that were established over the Tier 2 WAN so that traffic will continue to flow there.
Other than manually resetting states - how can one do so in a less intrusive way? Especially VoIP is bound to stay glued to the failover connection as the state should never expire? ;)
-
There are homebrew solutions floating around:
https://github.com/mk-fg/pfsense-scripts
No idea if they work, no idea if they will give you Space AIDS, YMMV.