FW: lan to wan
-
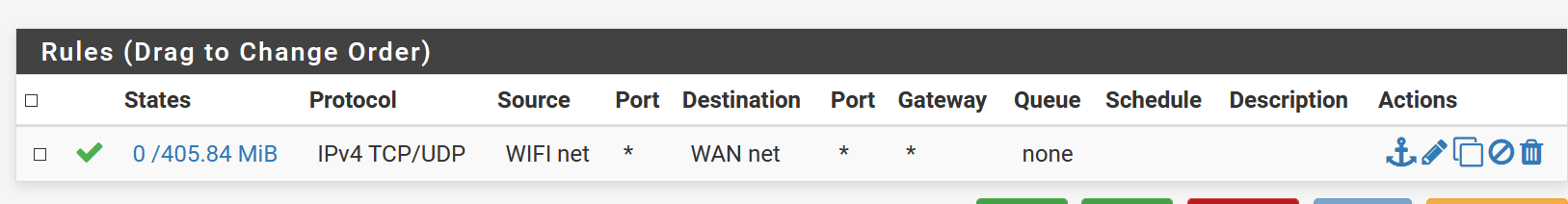
On other hw and sw firewalls doing lan to wan only works. I.e. a network card can only go to net and cant talk to other cards nor devices on same range. What am I doing wrong please?
-
Your Destination should be *. WAN net is literally just the network your WAN is on, not the entire Internet. If you want to limit WIFI net's local network access, put a block rule above the allow rule that blocks to destination LAN net, for example. You can also restrict WIFI net from accessing WebGUI:
https://docs.netgate.com/pfsense/en/latest/firewall/restrict-access-to-management-interface.html
-
Thanks Kom. Would that allow access to the entire net plus other devices on the same range plus other cards? My aim is to allow devices to get to certain external ports but not other devices on the range nor other e-cards.
-
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-basics.html
Yes, you can add firewall rules to restrict clients on the network from any destination. Rules are evaluated top-down, first match wins. Put your block rules above your allow rules.
-
That could be a lot of rules. Is there not a single rule which says lan to net and then i add a default deny?
-
Everything not explicitly allowed is blocked by default. Imagine that there is a hidden rule at the very bottom that blocks everything. The rules above it allow specific access. Also by default, LAN gets a rule that allows all traffic to everywhere. Additional LANs like OPT1, OPT2 etc have no default rules and must have at least one added to allow access.
What is it exactly that you are trying to do?
-
There are four NICs.
LAN is one PC and should be allowed to talk over 80,443/tcp only to internet. Other NICs should block it. I am used to other firewalls, having a lan to net rule.
Thanks -
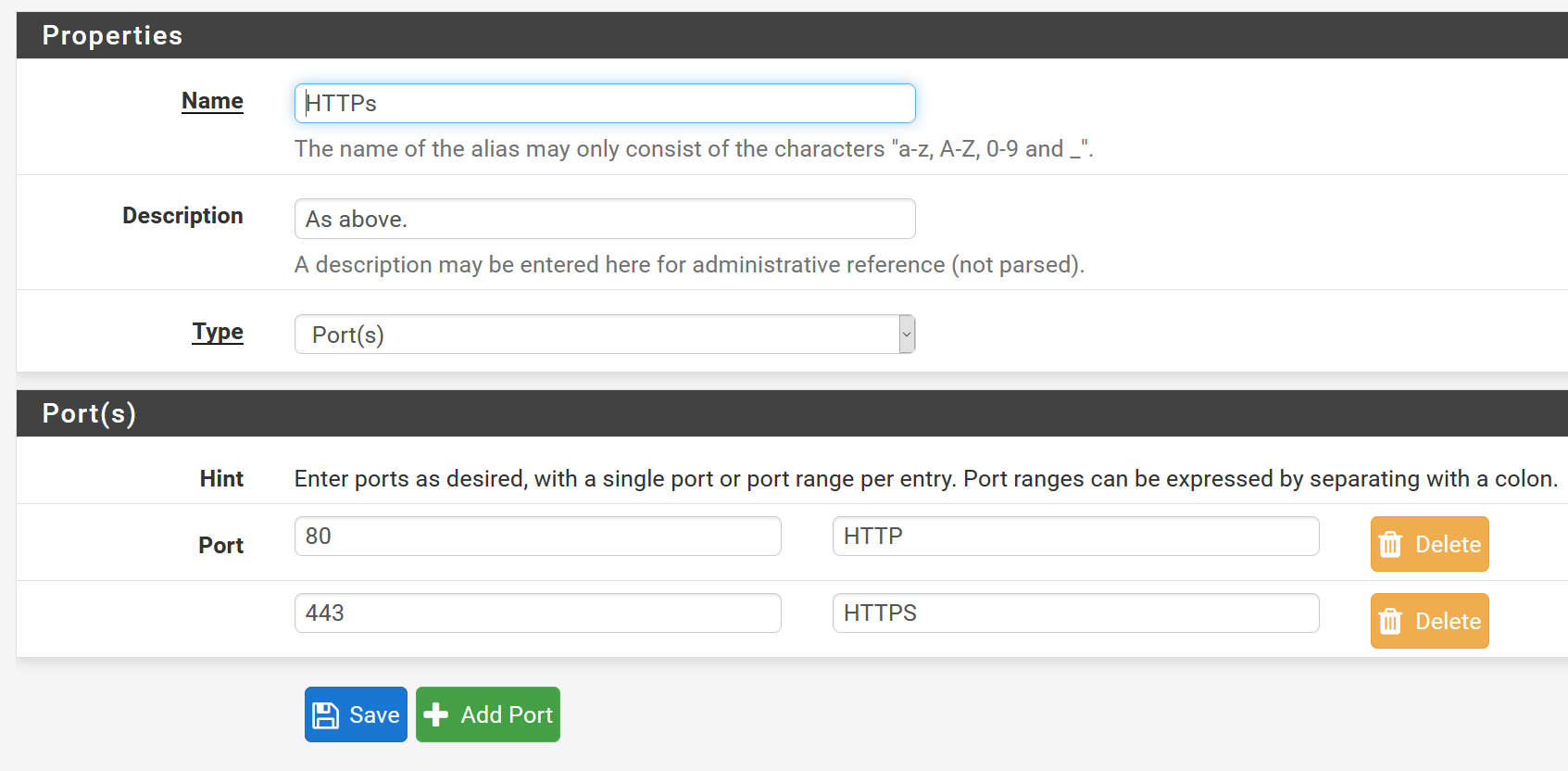
Go to Firewall - Aliases and create a port alias like this:
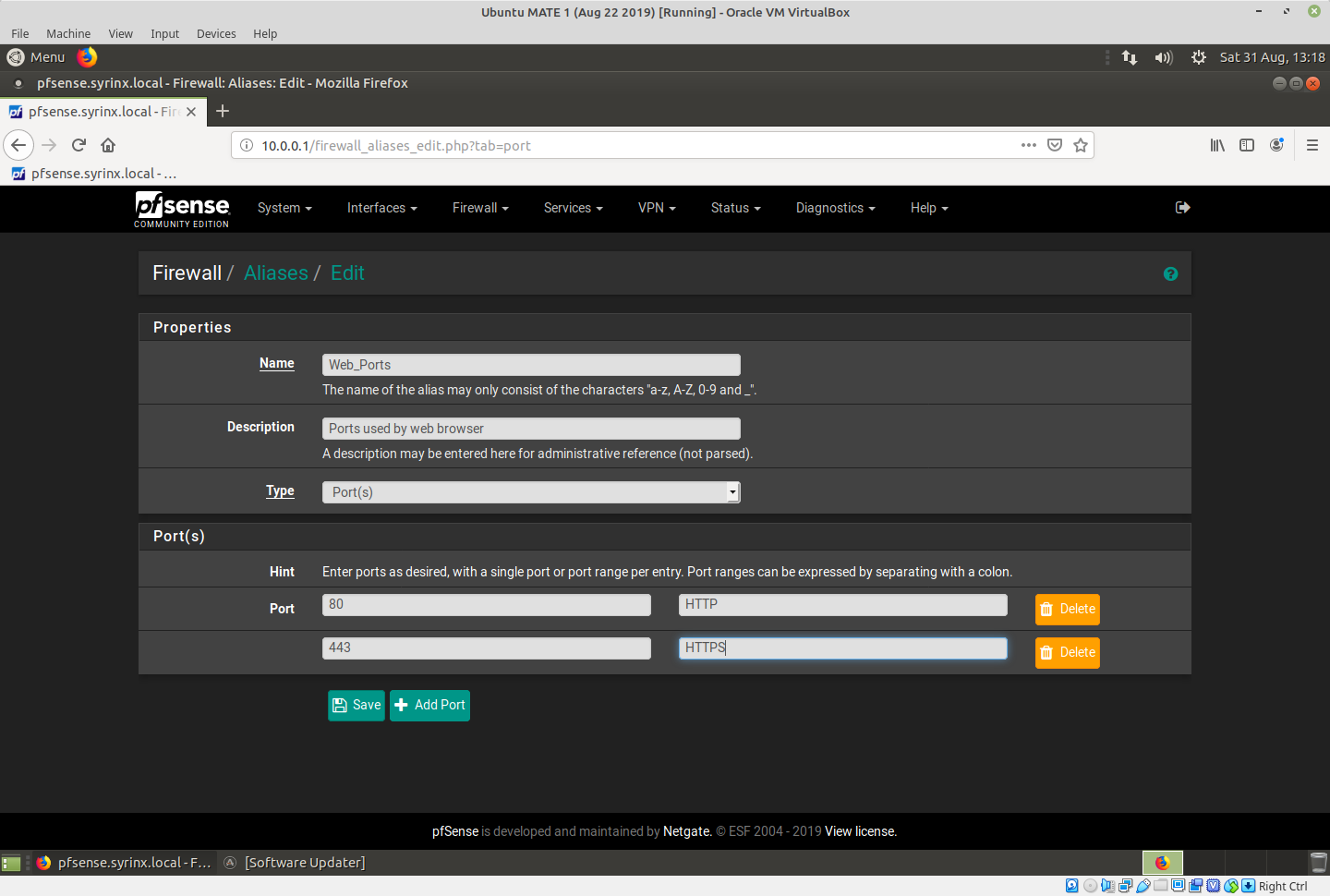
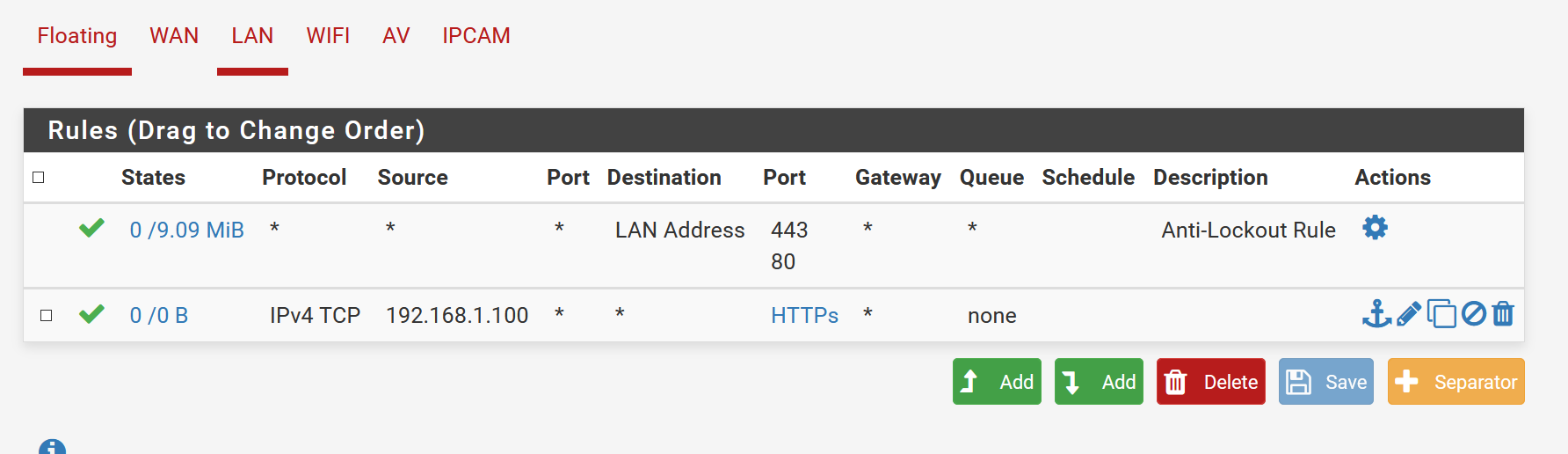
Then go to Firewall - Rules - LAN and make it like this:
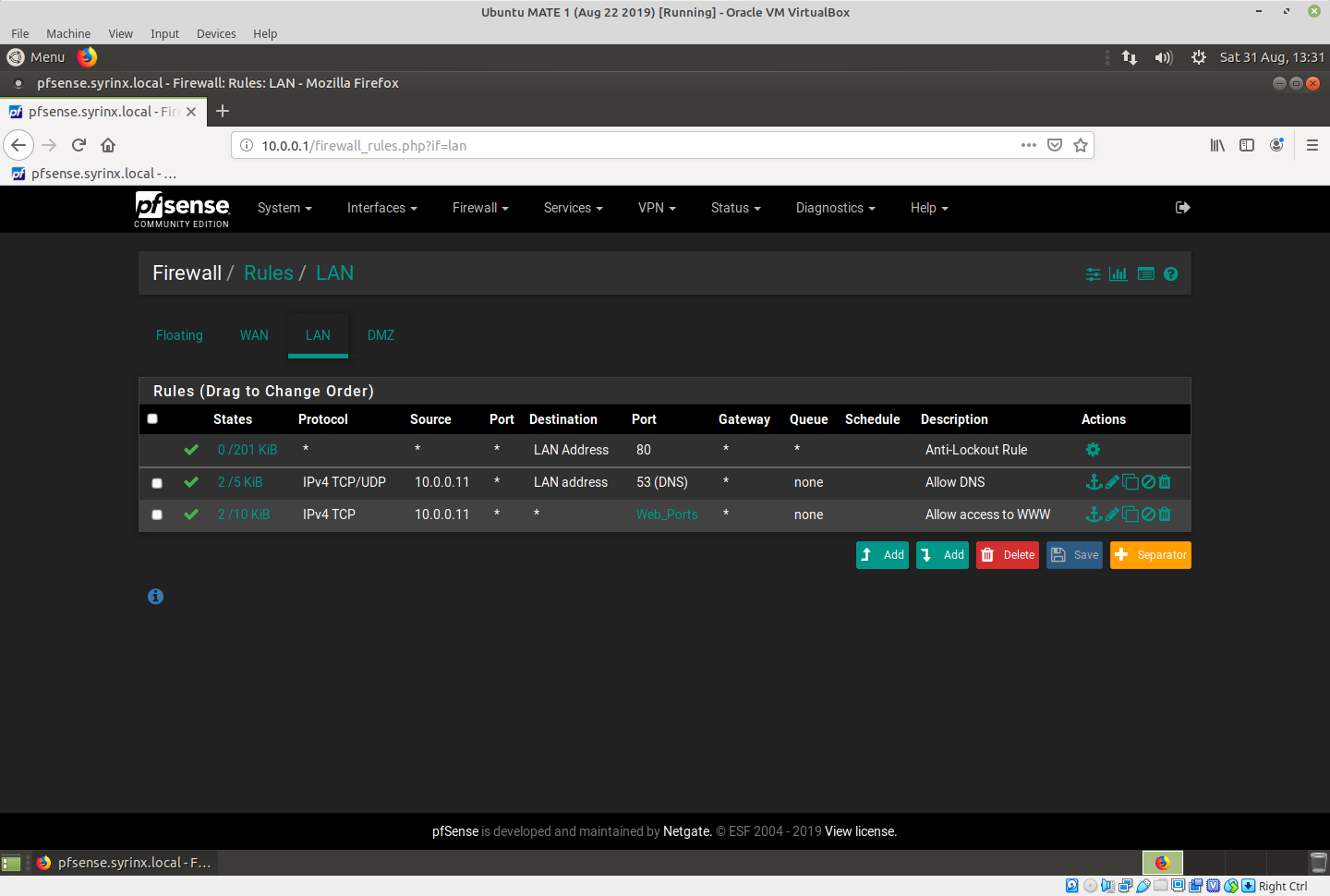
In those rules, my client is 10.0.0.11.
Now what you have are three rules:
- Top rule allows anyone on LAN access to WebGUI.
- Second rule allows access to DNS from pfSense so client can do name lookups
- Third rule allows access anywhere via tcp80,443 which is web only
All other access is denied. No other clients except 10.0.0.11 can go anywhere.
-
Much appreciate the reply.
It seems to do something however ftp://ftp.dlptest.com/ loads which is 21/tcp. Alias has 80,443 only.
-
Go to Diagnostics - States - Reset States and reset them then try your test again. Connections that are already established are not affected by a rule change. A packet capture (Diagnostics - Packet Capture) can confirm what's going out the WAN to that address.
-
After rest dns, http and https works plus possibly others but i can still get to another nic's ip.
-
Do you have any floating rules? From your above rules, nothing on LAN should be able to access anything other than tcp80 and 443. Is this other server on LAN or Internet?
-
I appreciate the past assistance - in the end I have moved on to a commercial product I have used before.
-
@graeme said in FW: lan to wan:
On other hw and sw firewalls doing lan to wan only works.
Any LAN bound device (PC, Phone, visitor, etc) can access the WAN == most often the Internet.
Typically, non trusted devices should be connected to other 'LAN' interfaces = OPTx interfacers as they are called by pfSense - special firewall rules can now be set up for these type of devices.Basic rule : on LAN you should connect only trusted devices.
@graeme said in FW: lan to wan:
I.e. a network card can only go to net and cant talk to other cards ....
Again, devices LAN, by default, can 'talk' to anybody on every interface WAN(s) or LAN(s).
@graeme said in FW: lan to wan:
... nor devices on same range. What am I doing wrong please?
Any device connected to a LAN can connect to another device on the same LAN.
Guess what : because traffic goes through one or more local LAN switch(s), and never even touches or uses (the firewall of) pfSense.
Proof : my LAN, with about 45 devices on it, works very well for local (device to device) communication, even with pfSense shut down.pfSense, by default, does not behave any different as any other firewall/router, soho or pro.
Why should it ?What makes the difference : the guy in front of the keyboard.