pfsense - TLS error TLS handshake failed
-
I have configured openVPN in pfsense server and trying to connect from windows 10 and i am getting this ERROR
TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)i have configured my pfsense with only one NAT ip address(WAN) no LAN ip address, i was shared the internet from WAN internet to local area network
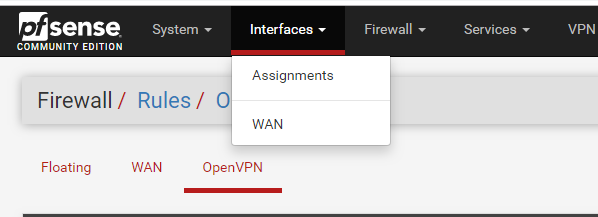
i have created rules correctly...
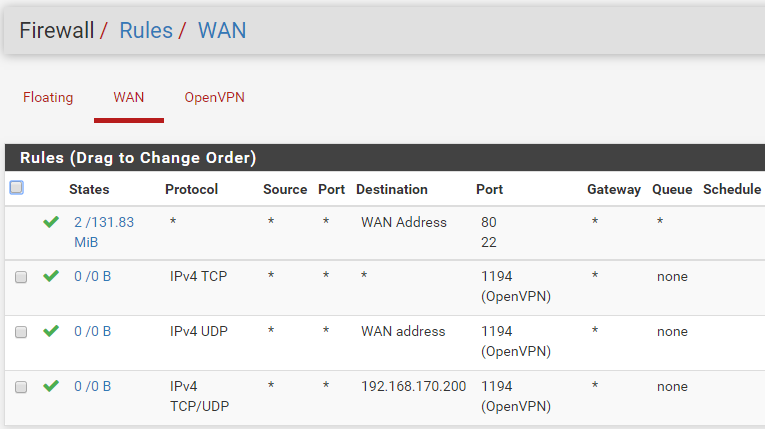
i have checked the logs also...
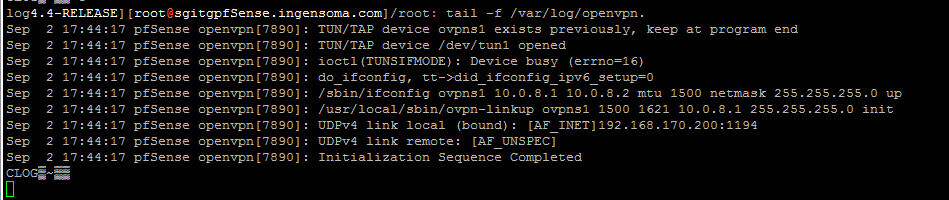
not sure what is the issue, everthing look's ok but i am not able to connect the openvpn... Need public ip address to configure the openvpn in my case.
Please help me to resolve this issue....
-
So you're on a double NAT scenario?
Then you first need to forward Port 1194 UDP from the Router upstream pfSense to the pfSense WAN IP.
Second you need to disable Block private networks and loopback addresses (Interfaces > WAN)-Rico
-
@Rico said in pfsense - TLS error TLS handshake failed:
Second you need to disable Block private networks and loopback addresses (Interfaces > WAN)
Not needed, since the source would be public - unless the nat router in front of pfsense was doing source natting? Which normally not the case.
As you can see from actually looking at the rules
block drop in quick on igb1 inet from 10.0.0.0/8 to any label "Block private networks from WAN block 10/8" block drop in quick on igb1 inet from 127.0.0.0/8 to any label "Block private networks from WAN block 127/8" block drop in quick on igb1 inet from 172.16.0.0/12 to any label "Block private networks from WAN block 172.16/12" block drop in quick on igb1 inet from 192.168.0.0/16 to any label "Block private networks from WAN block 192.168/16"They are only block when source matches rfc1918, not dest.. So forwarding the case of double nat to pfsense wan IP that is rfc1918 is not an issue with the default block private networks rule that is on wan. So no need to disable it - unless the source is going to be rfc1918.