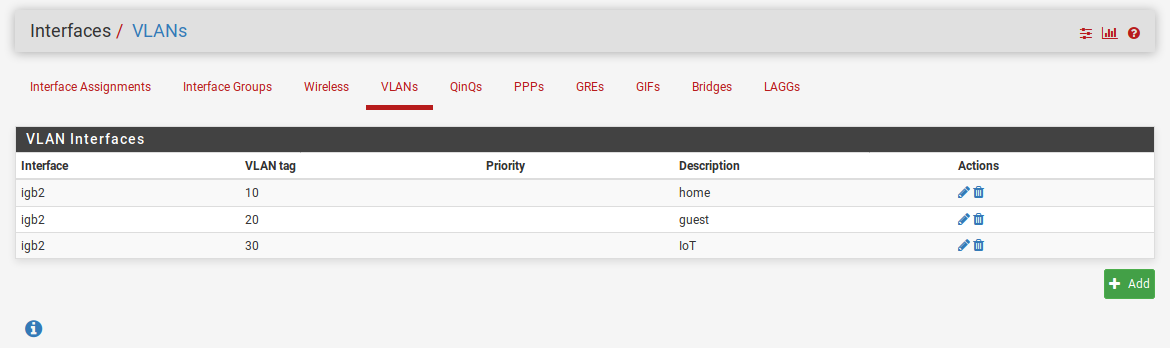
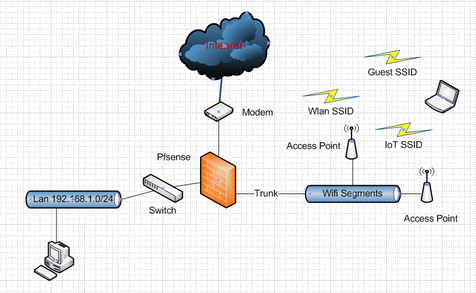
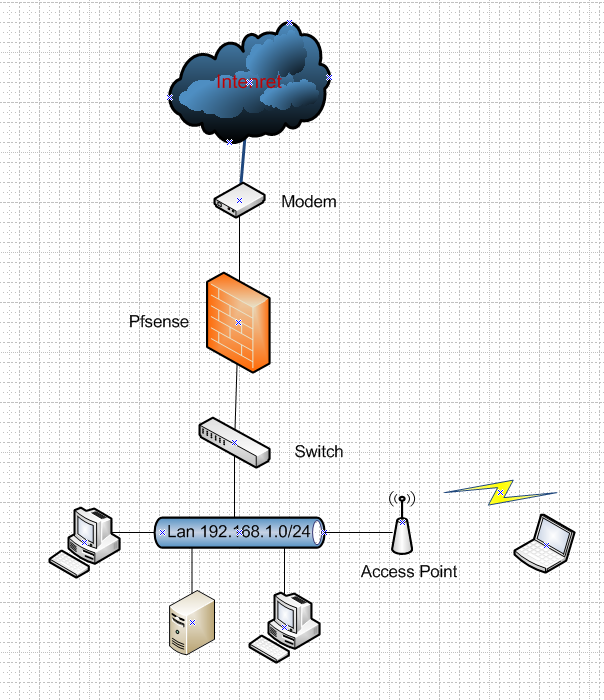
Setting up pfSense for VLAN and trunk port
-
typical unmanaged switch has a nominal MTU of 1500 bytes. So does a typical managed switch. Adding a vlan tag adds 4 bytes, making the frame 1504 bytes long, other stuff actually can makes the frame bigger,
It is the frame size that prevents the unmanaged switch from passing the traffic, not the content of the frame.
Unmanaged switches deal with this as: dropping the frames, truncating the frames, crashing entirely, and sometimes working.Why go to all that trouble to set the switch like this .. i can only speculate here, could be a hardware limitation sometimes or could be a marketing decision like when they was selling the same identical cd burner with different firmware to cap speed at x2 x4 x8 and selling it with different price
-
Doesn't matter pass or not pass.. That is NOT THE POINT!!
They don't understand them, so they don't actually isolate traffic... Every port will see broadcasts from every vlan you setup on your devices with tags.
There is zero security - and all it takes is someone smart enough to use google, and vague understanding what a vlan is to jump them...
Your also just promoting BAD HABITS and misunderstanding to new users that wanting to get into vlans....
If you as a long time guy in the biz, who fully understands vlans and think its ok for whatever chewing gum and rubber band network your throwing together is ok with it that is fine... But you suggesting to some new person to vlans that its possible or could do or whatever with their existing dumb switch is just wrong at every freaking level - PERIOD!!
If you want to run a network with vlans, then your infrastructure needs to understand them and be able to actually use them - not just pass the traffic be it tagged or not. If your ok with some jury rigged nonsense on your network have at it... But please don't even mention it when some new user asks how do I do vlans..
-
@kiokoman said in Setting up pfSense for VLAN and trunk port:
typical unmanaged switch has a nominal MTU of 1500 bytes. So does a typical managed switch. Adding a vlan tag adds 4 bytes, making the frame 1504 bytes long, other stuff actually can makes the frame bigger,
As I mentioned, frame expansion, to 1522 bytes, happened 21 years ago, with 802.3ac. Since then, there has been further frame expansion to where 9000 byte jumbo frames are now often used. Some gear goes to 16K or so. So, any gear that can't handle more than 1500 would have to be pretty old. If you do find some, then reduce the MTU on your network to 1496, which will leave room for the tag. A couple of messages up, I mentioned I hand wired some Ethernet controllers. Back in those days, there was a hard limit because hardware (discrete logic vs ASICs as used now) was so expensive. On the other hand, there is a limit with 802.3 frames, where the Ethertype/length field contains a maximum length of 1500. Even then the length field now follows after the VLAN tag.
-
@johnpoz said in Setting up pfSense for VLAN and trunk port:
Doesn't matter pass or not pass.. That is NOT THE POINT!!
The point I've been trying to make is that people have a lot of assumptions that are false. There has never been a reason for unmanaged switches to block VLANs. Think back to the original Ethernet, which ran over coax cable, without switches or even hubs. There was nothing to block anything. When hubs came along, they behaved exactly like the coax, in that they didn't block anything. Then came switches, which then again passed everything, though since they buffered frames, there was a limitation on how big the frames could be. Switches started to become popular back in the late 90s, around the time of 802.3ac. However, at no point was there ever any reason to block VLAN frames in an unmanaged switch. As for using VLANs on managed vs unmanaged switches, I agree managed switches should be used and have one on my home network. But that does not mean unmanaged switches can't be used, nor shouldn't be used on a small network as you might find in a home network. There are also many applications where VLANs and native LAN are used on the same wire. One common application is VoIP phones that have a computer port. With these, a computer is plugged into the phone, which then connects to the switch. Another would be WiFi access points, with multiple SSIDs.
If I were to build a network today and had a say in the equipment used, then I would always go with managed switches, but I often don't have that say and have built many networks, in small businesses, without them.