Issues in setting up OpenVPN between 2 pfsense
-
Hello Experts ,
This is my lab topology . I have pfsense connected to two wireless routers as upstream devices that is connected to the ISP and reaches out to the Internet. Since the lab is being setup in my home , I don't have direct WAN connection to the ISP. Further, one interface LAN is connected to the wireless router by wireless bridge ---> switch---->pfsense . However other interface OPT is connected directly to the LTE based wireless router leading to internet. There is proper communication between all the devices since they are on the same VLAN.
My objective is to access my network devices on my home network from the outside through OpenVPN.
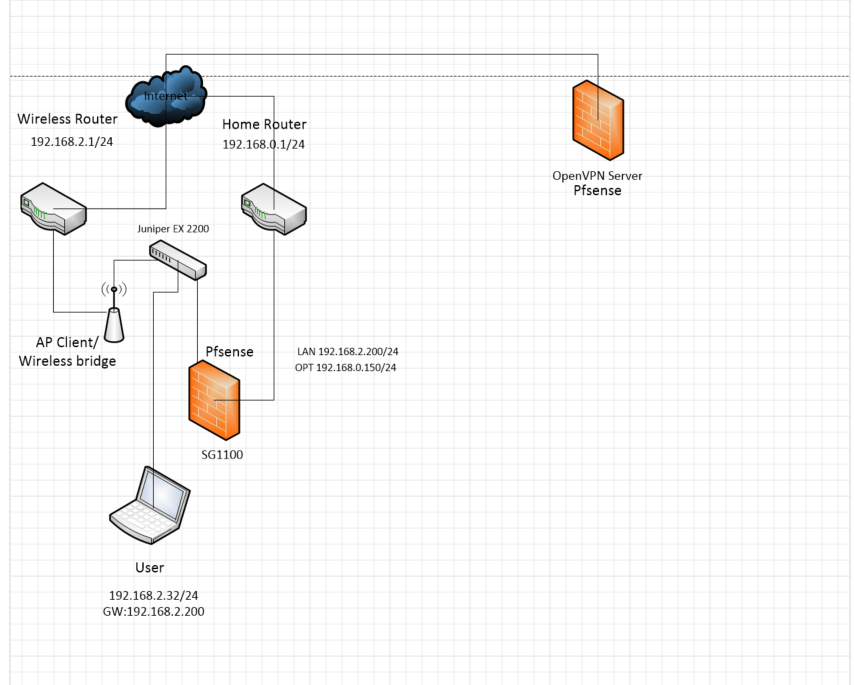
I made the pfsense SG1100 as open VPN client and other pfsense as OpenVPN server. This is because I run the other Pfsense on cloud with static public, which makes it easier to setup VPN.
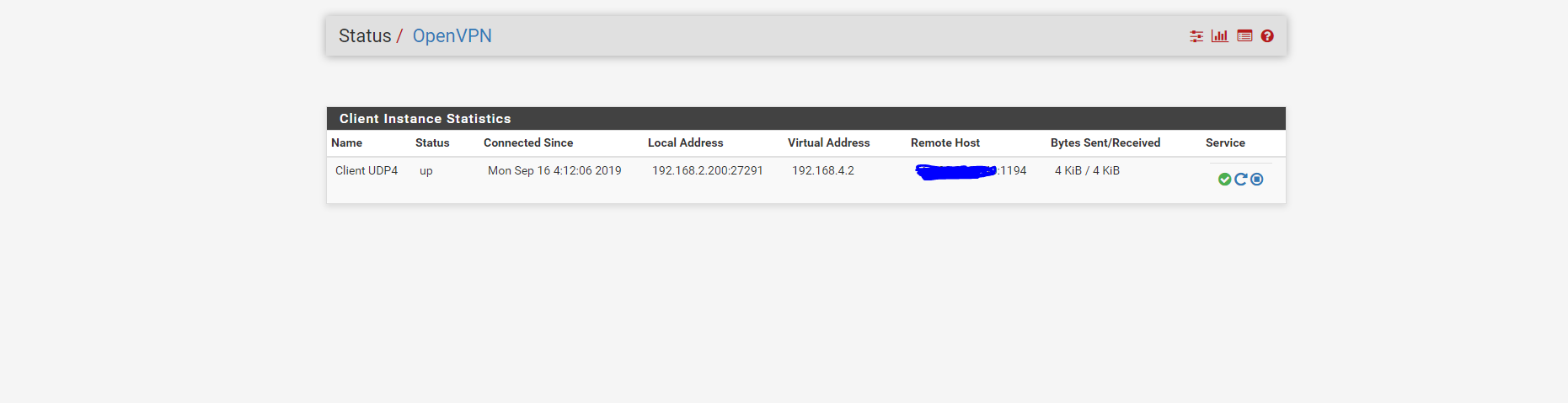
From the pfsense SG1100, I see that the OpenVPN is up
At the Pfsense /OpenVPN server, I see the VPN is up
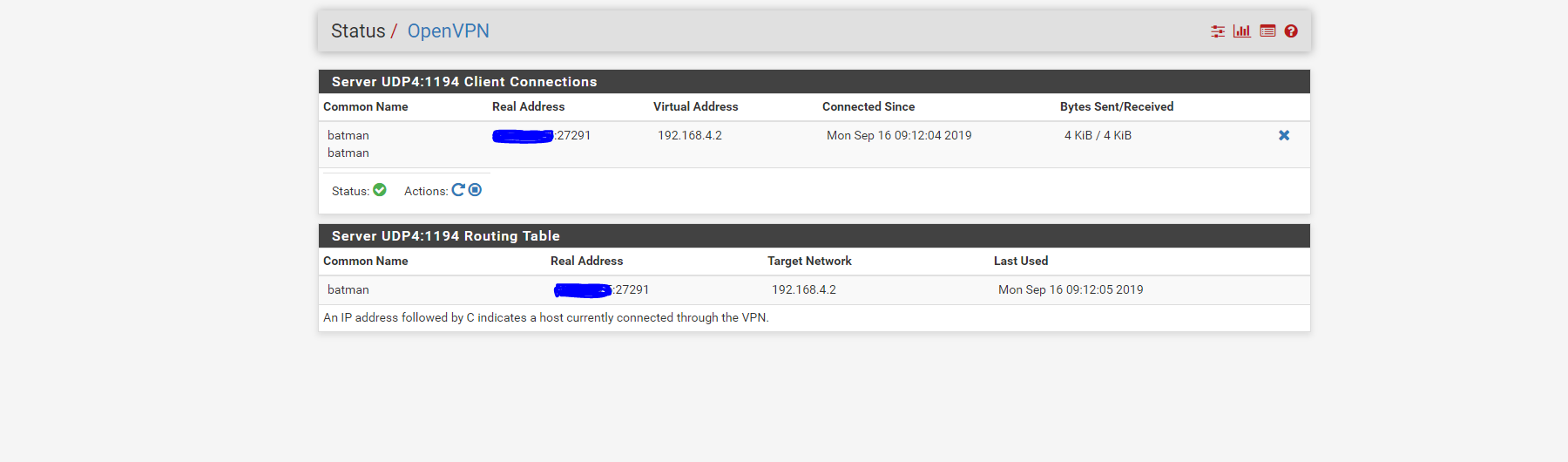
I tried to ping the tunnel IP 192.168.4.2 from the server , it wasn't successful. However I have the 192.168.4.1 reachable from OpenVPN server . I think I am missing routes but I am not entirely sure.
Here are my questions
After I setup VPN , is the communication bidirectional , meaning can I reach the network behind pfsense sg1100 from the server?.
what configuration do I need to access the network devices behind the OpenVPN client from the OpenVPN server ?.
Do I need virtual interface to make this work ?.I am pretty new to pfsense but quite passionate to learn about it. My apologies if my question seems to be simple
-
Is it me or do you have a circle in your network ? The Wireless router and Home router are both connected to the net ?
pfSense has a WAN ?
Why not putting pfSense upfront ? -
Thank you for your response . I rent a room in a house , the landlord isn't tech savy and doesn't want me doing any changes to the home router. ISP has provided residential internet connection unlike the enterprise/business connection with static public IP . That's why I cant put my pfsense upfront . Further home router is on a different subnet and pfsense only uses Wireless router since its the default gateway. The other router is LTE based home router , which was connected to the OPT interface during my attempts to configure redundant gateway. There is no circle or loop in the network
-
You need to add Firewall Rules in the OpenVPN tab to allow communication.
-Rico
-
Show via screenshot the bottom half (where it shows remote network) of your OpenVPN setup pages..
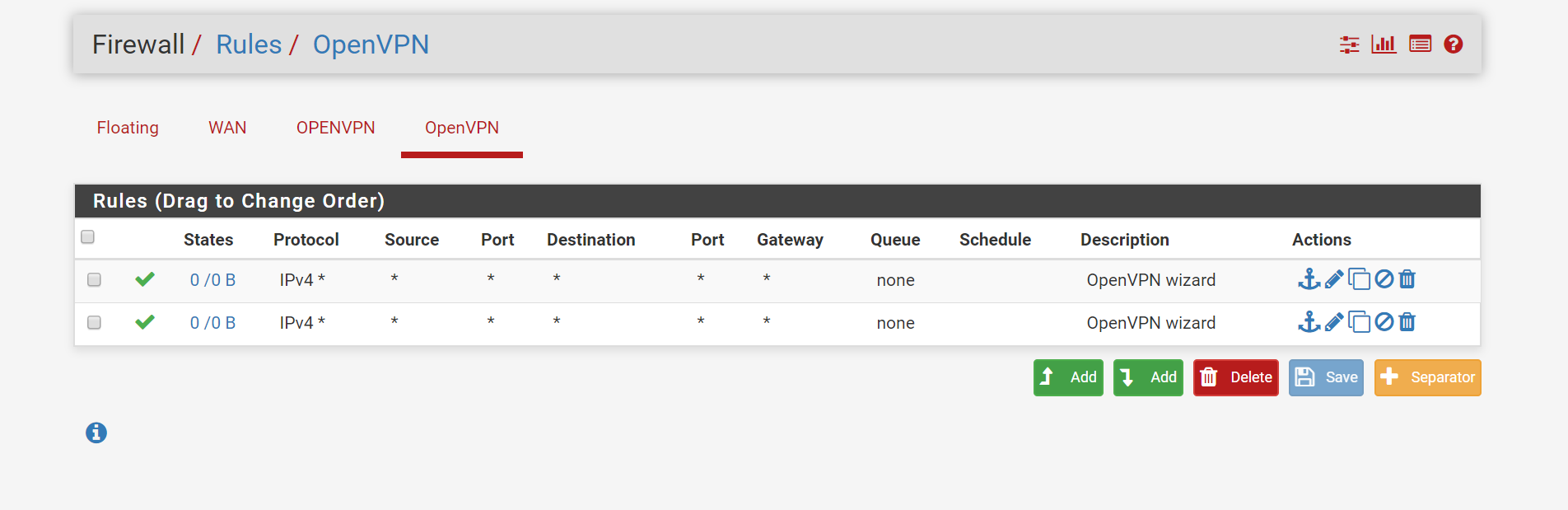
Show your OpenVPN firewall rules.
-
Pfsense as OpenVPN server
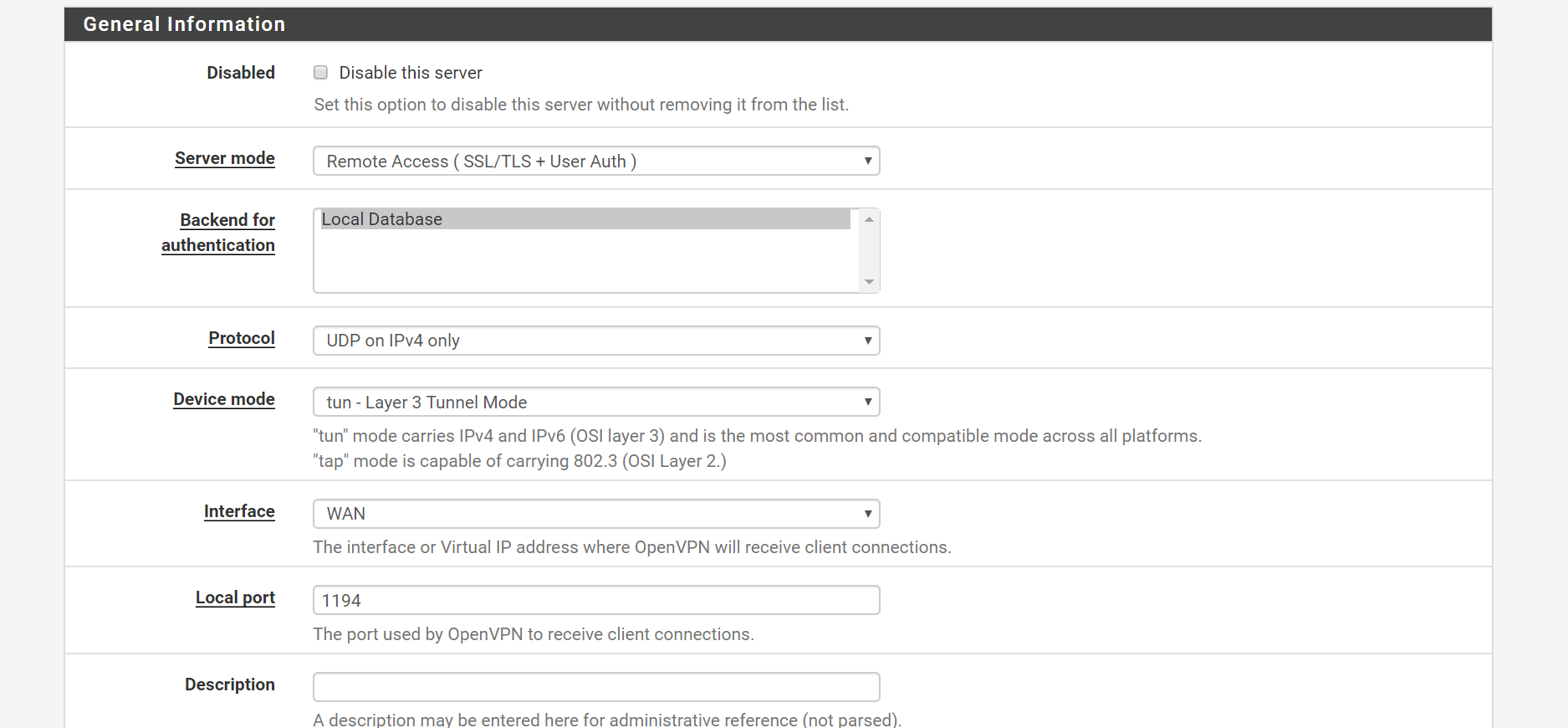
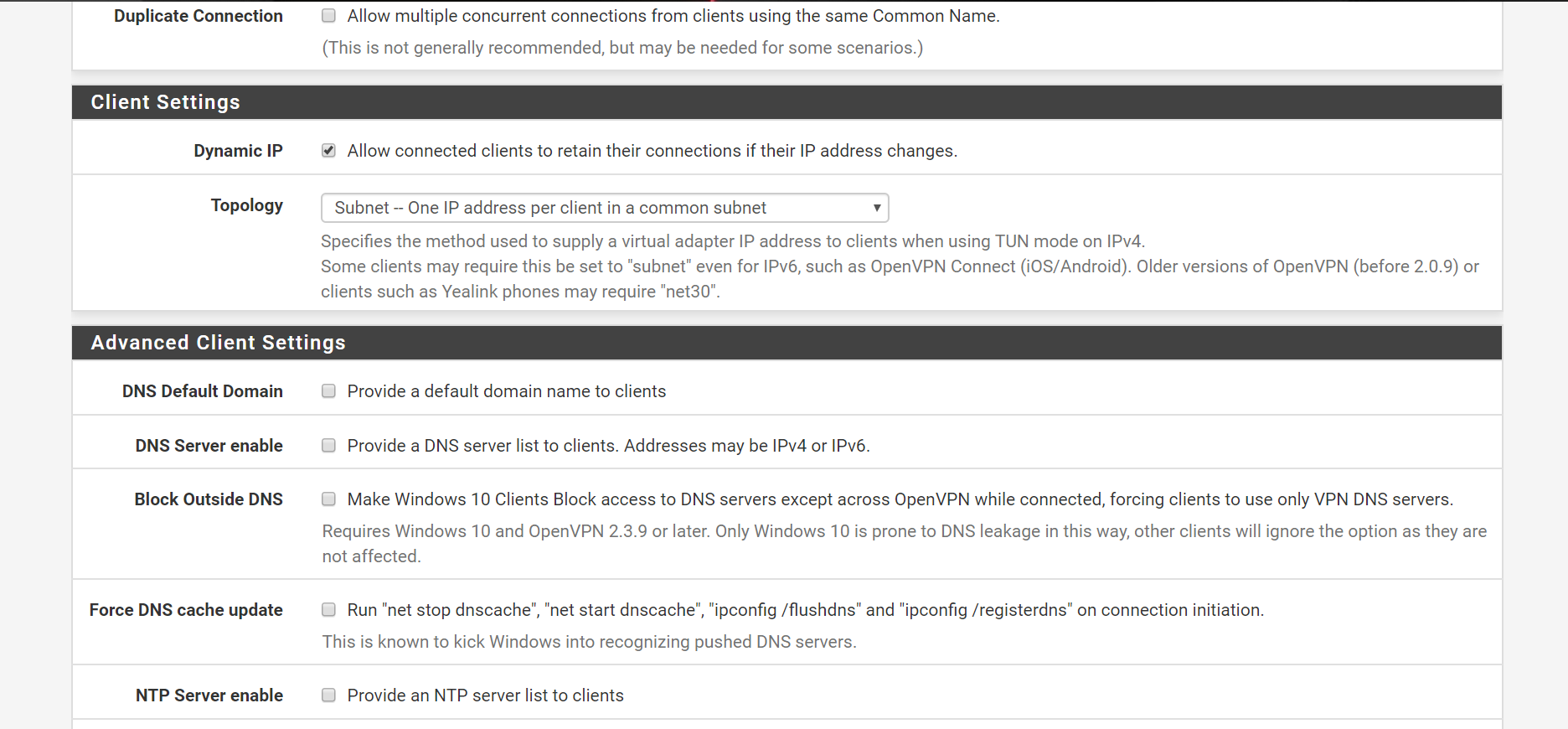
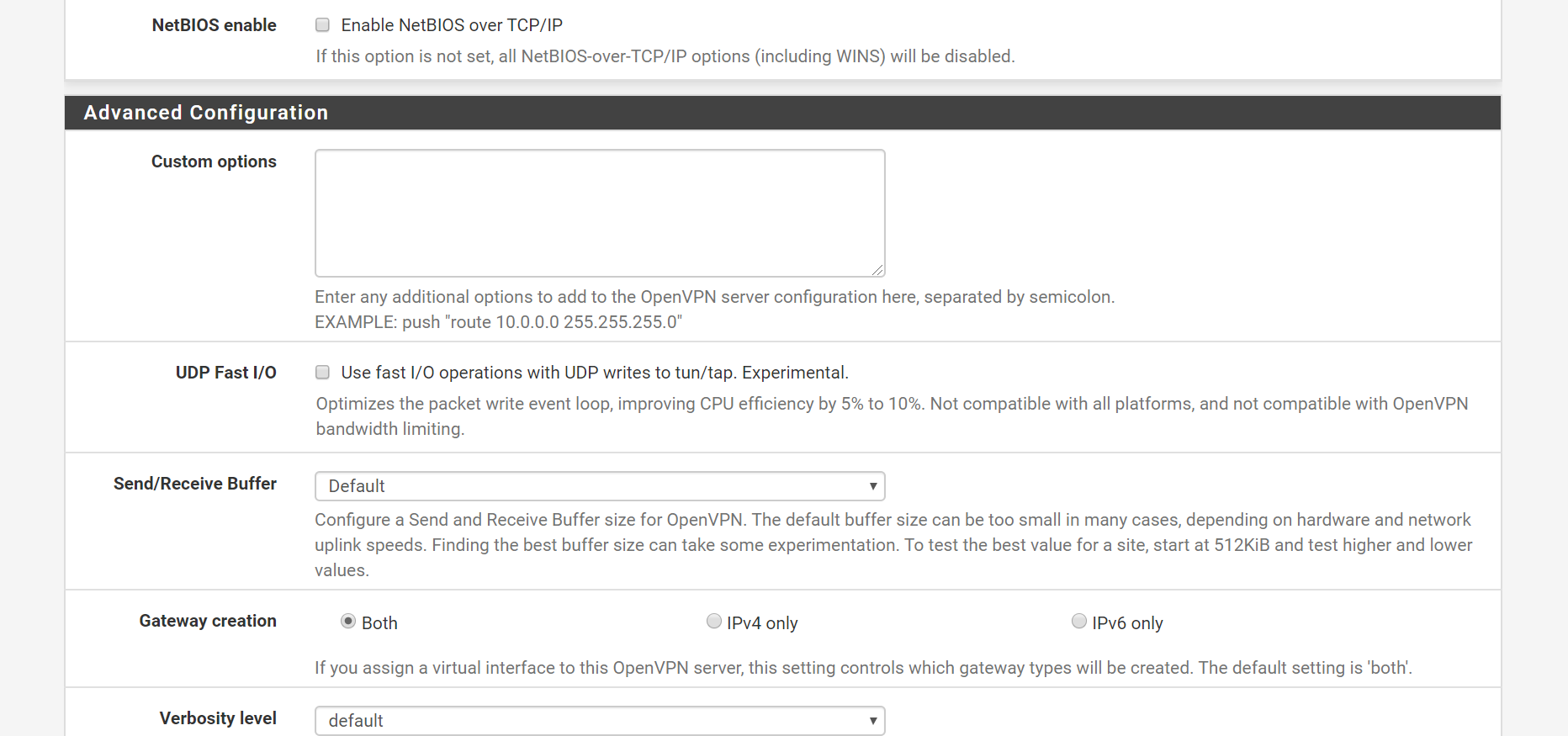
OpenVPN setup page
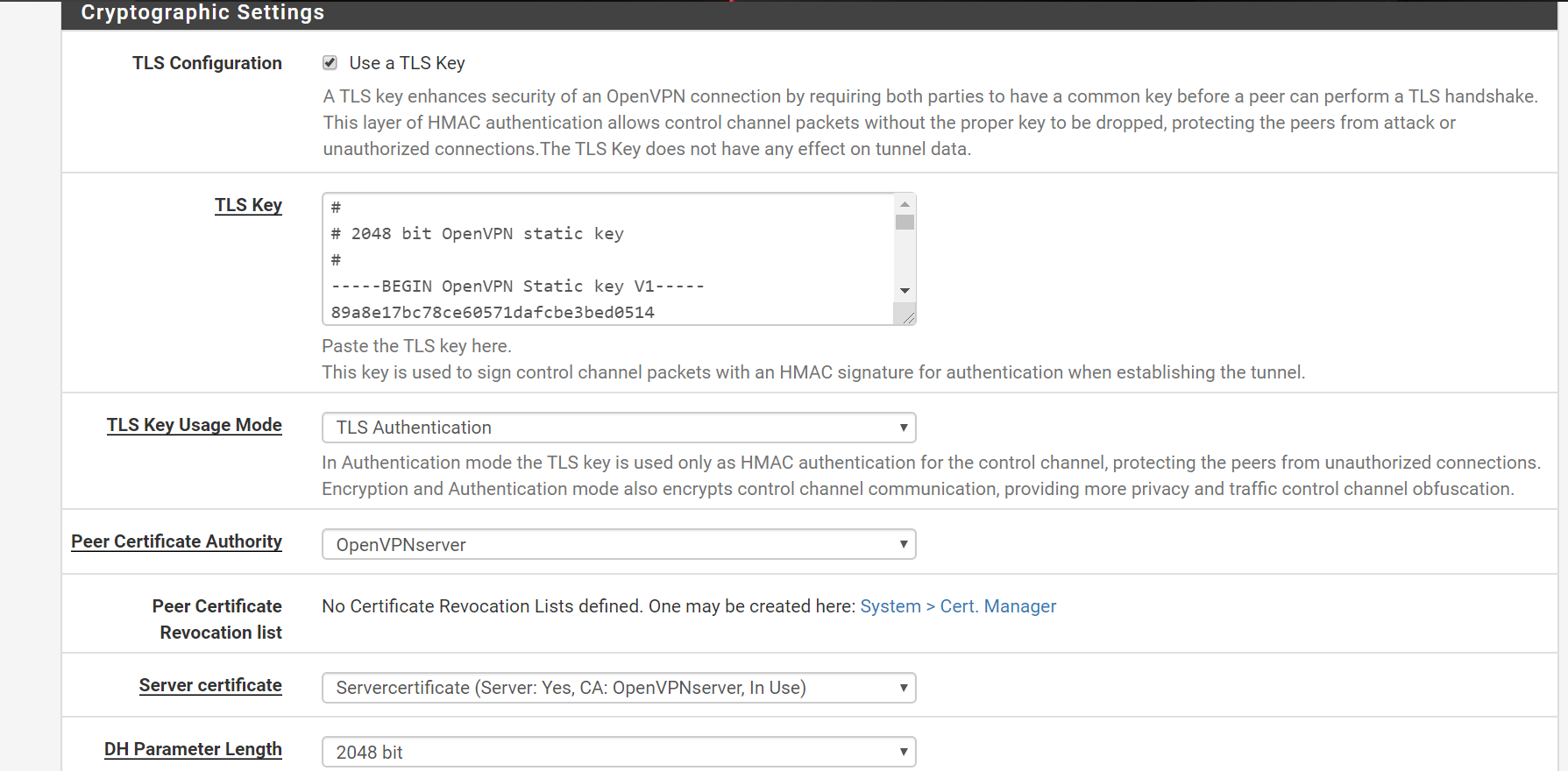
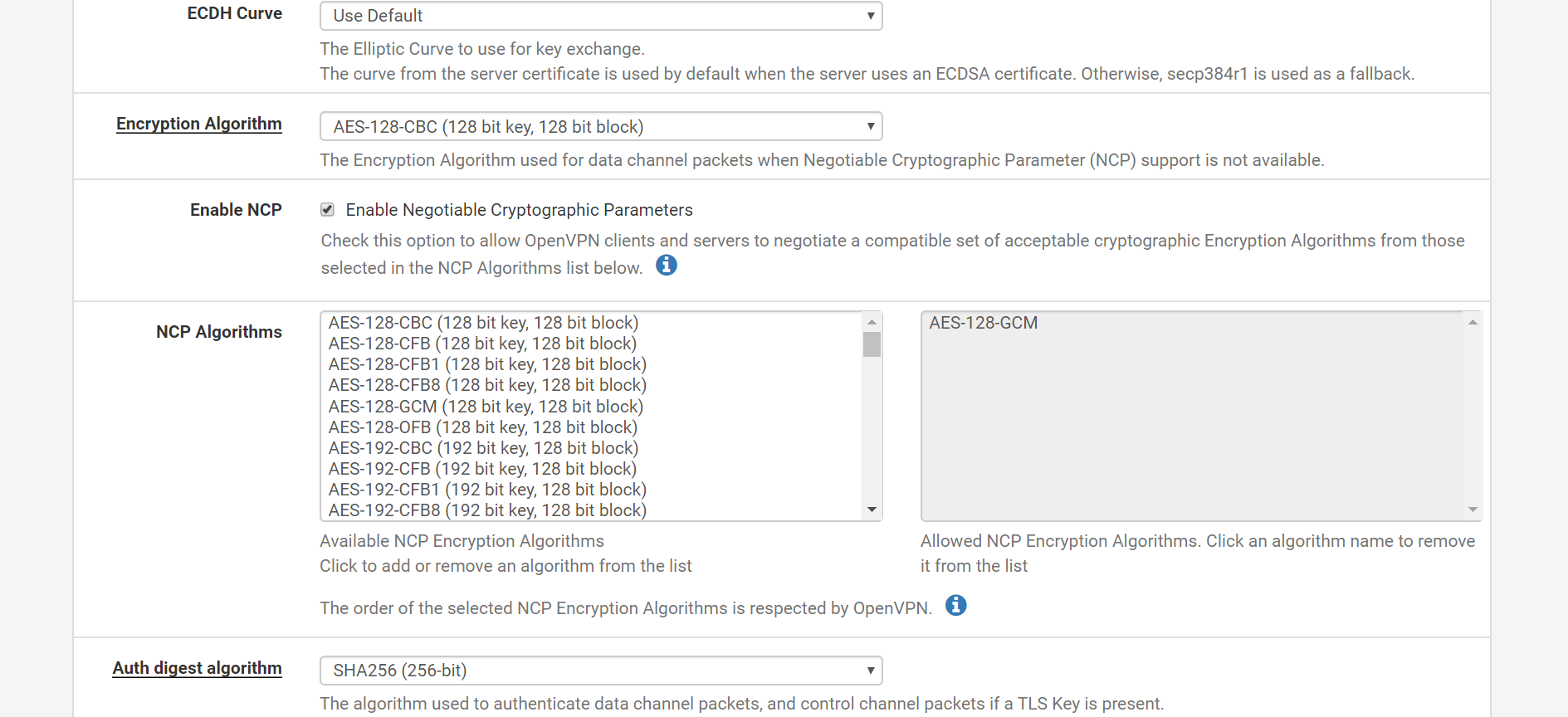
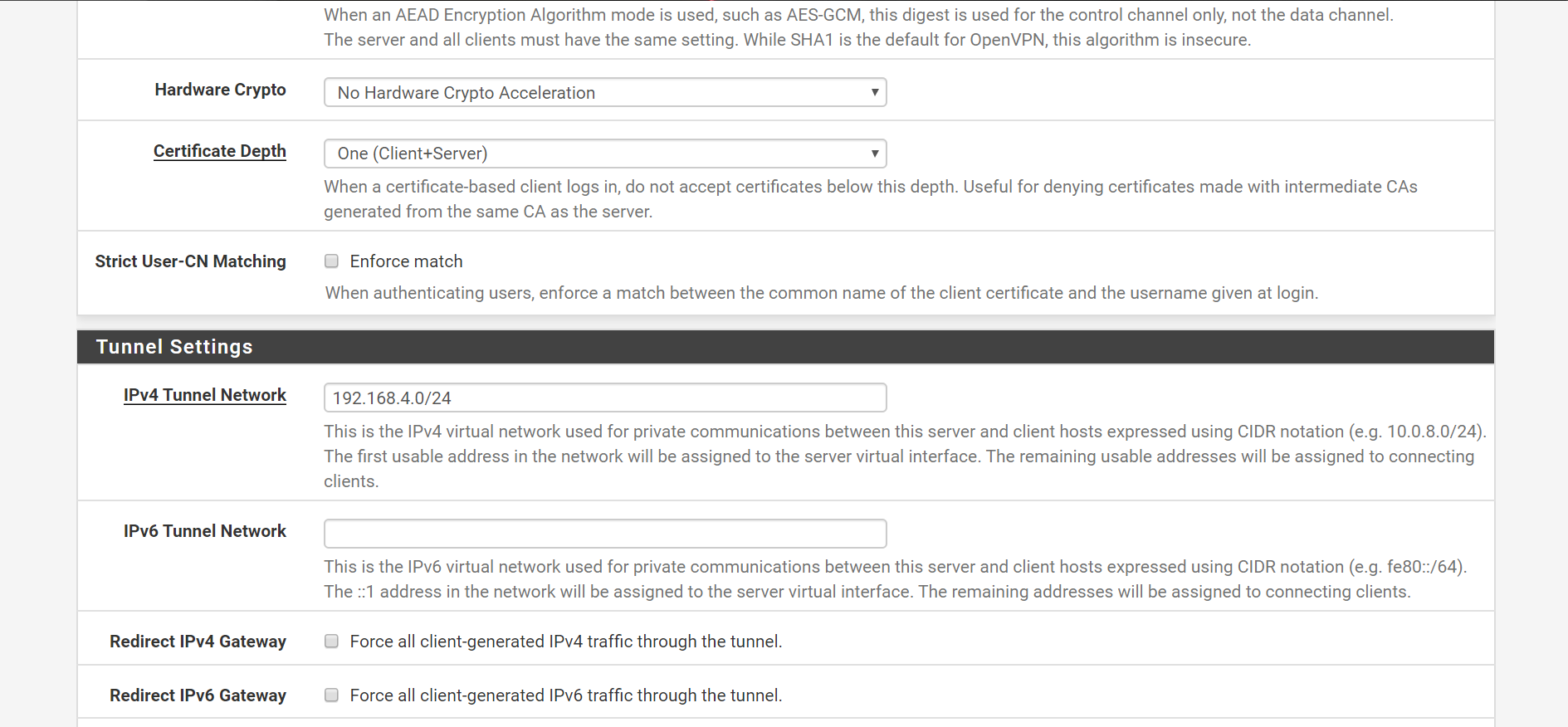
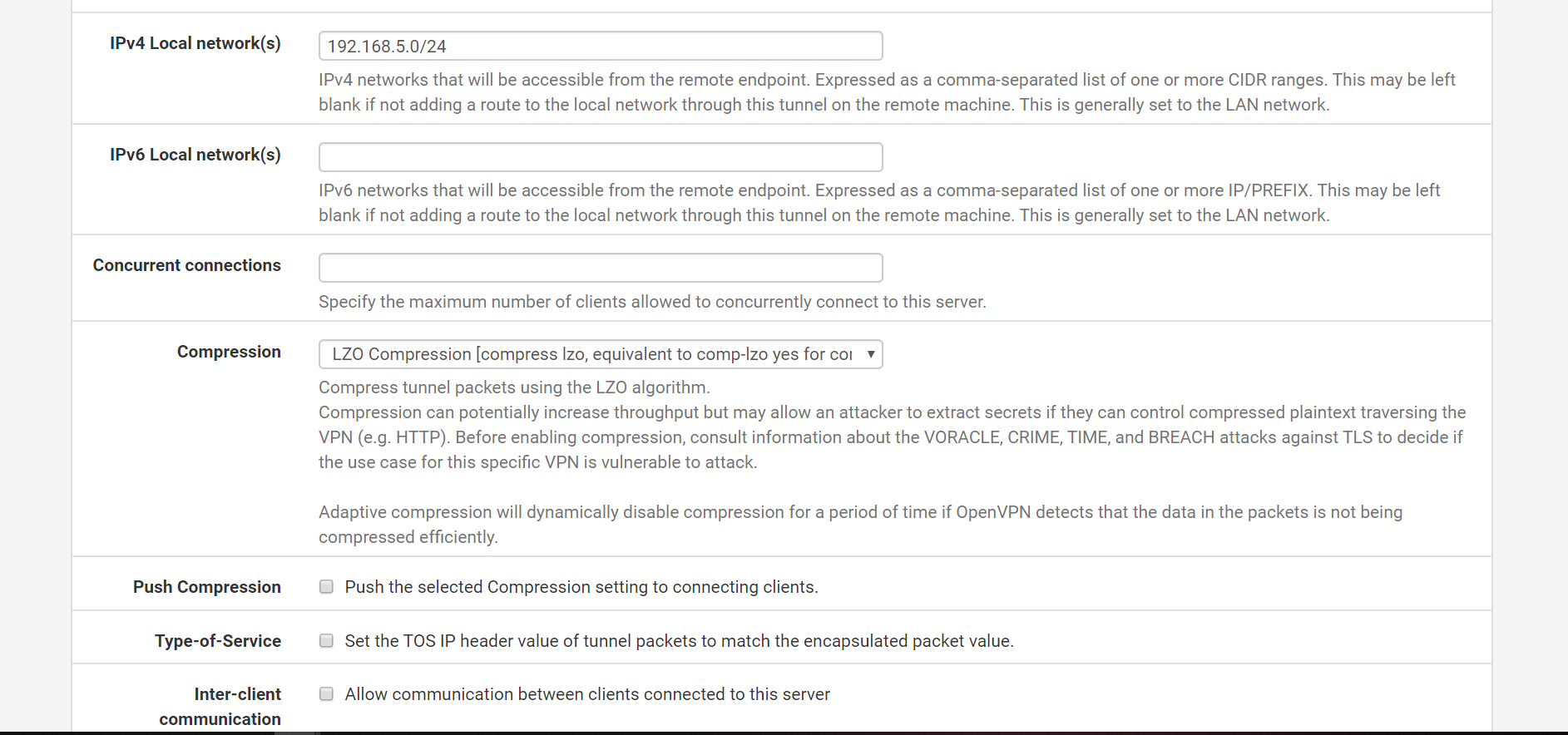
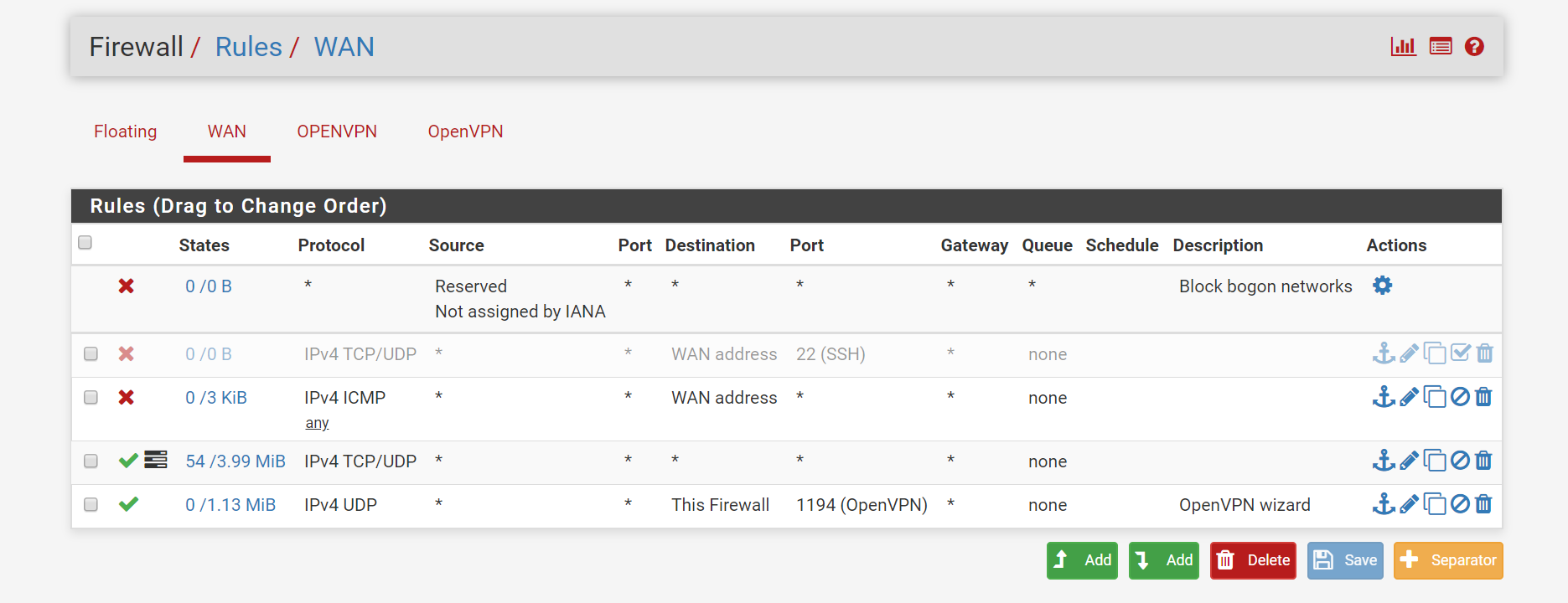
WAN Interface firewall rules
NAT rules on the interface
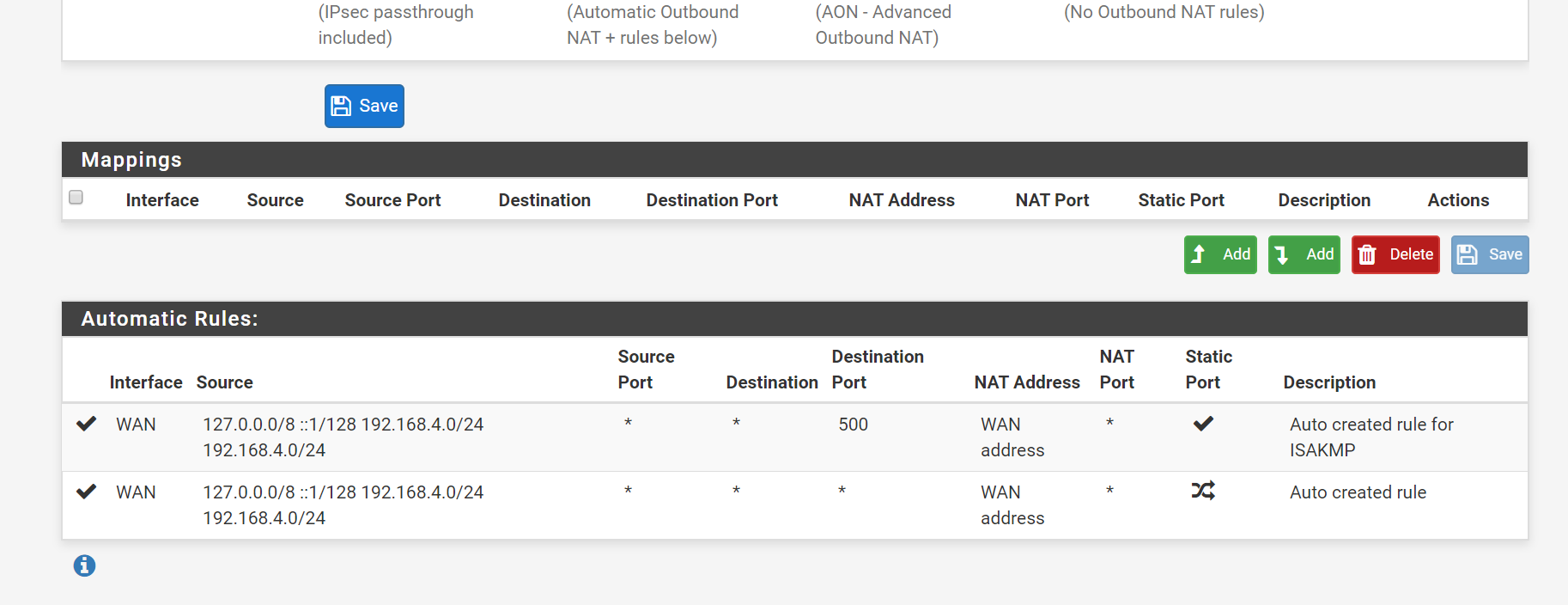
I have enabled openVPN on WAN interface rather than a virtual interface. Do you think that might be causing issues?
-
@Rico The rules were automatically added when during the OpenVPN wizard. Added few NAT rules . I am not sure if that could have caused the problem . I would appreciate if you could have quick look at the rules I have added . I have attached screenshots on my comment.
-
@chpalmer Please find the screenshots on my comment .
-
Part of your image :
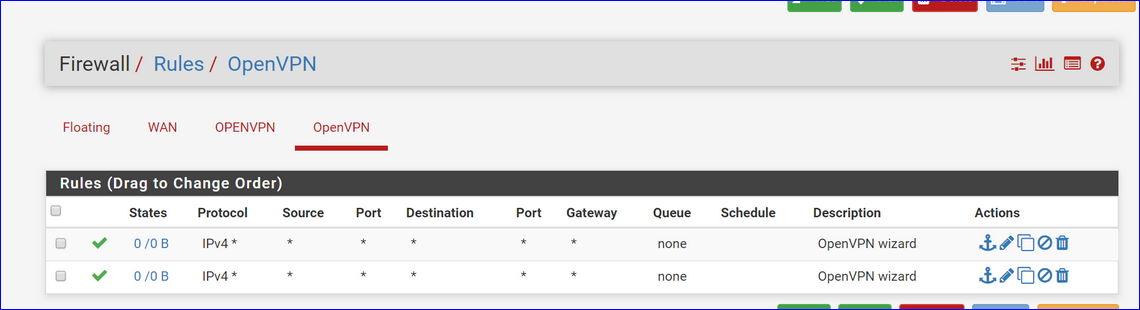
Check out carefully the principal OpenVPN server video from Netgate (Youtube - the Netgate channel)
You assigned an Interface to OPENVPN from the auto created OpenVPN :
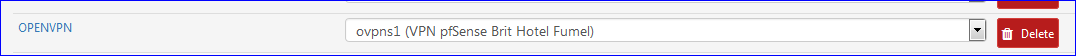
In that case, you can leave OpenVPN empty - it won't be used anymore, like
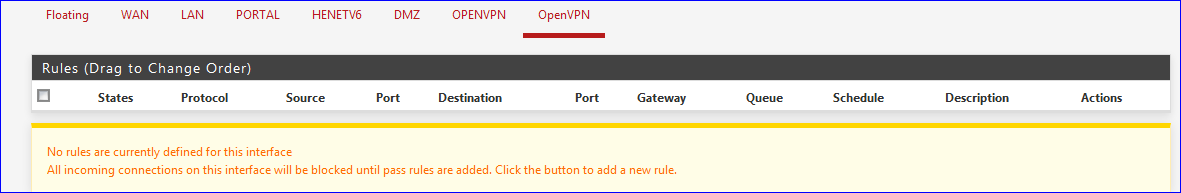
Place (copy) the Open VPN Wizard general 'pass' rule from the OpenVPN to the OPENVPN interface.
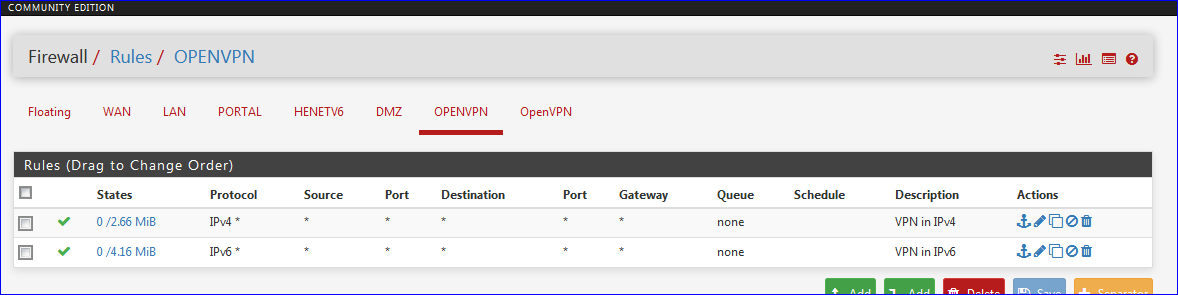
No need to have two identical fire wall rules on the same interface.
I have two rules : one for IPv4 and one for IPv6. -
@Gertjan Thanks for the reply . In my OpenVPN setup , only WAN interface is enabled . However I assigned the ovpns1 to OPENVPN , i thought this deployment requires that . I removed them now. I am able to connect and VPN is up but cant connect to the Open VPN client from the server
-
@Sid1584 said in Issues in setting up OpenVPN between 2 pfsense:
am able to connect and VPN is up but cant connect to the Open VPN client from the server
You, from the outside, using some openvpn App, are the client. You connect to the server, running on your pfSense.
It's the client that takes action to connect to the server, not the other way around.Can you confirm that you see the connection in the pfSense GUI like this :
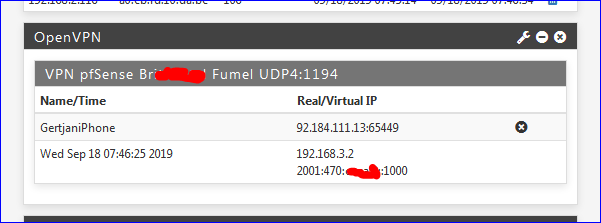
So, now, you don't have the OPENVPN any more ?
There is only the OpenVPN interface ? With the - just one - Wizard rule like :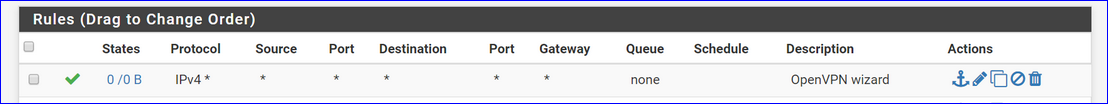
?
Your client VPN logs while connecting ?
pfSense server logs while connecting ?In what is your setup different as the 'default' Netgate OenVPN video ?
On your WAN interface, remove this :
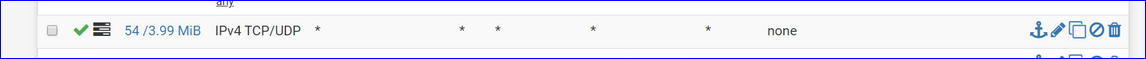
It's an open bar rule : let every body in. Happily enough, connections are using IPv4, so they are state based. In the future (IPv6 ) you just opened up your entire LAN network to the Internet. You might as well remove pfSense (the firewall) all together.
-
@Gertjan I am not using OpenVPN client app rather I have made Pfsense SG1100 as the OpenVPN client and its server is the pfsense on the cloud which is depicted on the right of the topology diagram. Yeah I agree , the rules on WAN interface is open to my LAN network , its pretty bad but I dont have any LAN devices or LAN network on the cloud . In the logs I see the user is authenticated and the tunnel interface is up with its virtual IP. Do you think having one PFsense as a client and other Pfsense as a server is a feasible implementation?.
-
@Sid1584 said in Issues in setting up OpenVPN between 2 pfsense:
Do you think having one PFsense as a client and other Pfsense as a server is a feasible implementation?.
Never did so myself, but thousands are doing just that.
Mostly it's about tunnelling one company's site to another - interconnection company's LAN's. -
@Gertjan I am planning to setup the OpenVPN server as the central VPN gateway and expand the network if needed. If I fix this , I am pretty sure I can.
-
This post is deleted!