Don't understand this firewall log (vpn client hitting vpn server firewall rule)
-
Hi,
I have a OpenVPN client configured that connects to NordVPN (ovpnc1) and a OpenVPN server (ovpnc2) that I use to remote into my LAN.
The other day I started playing around with Elasticsearch to monitor and I noticed something weird in the logs. The firewall rule blocking this event is assigned to the ovpnc2 interface but the IP belongs to the ovpnc1 interface.
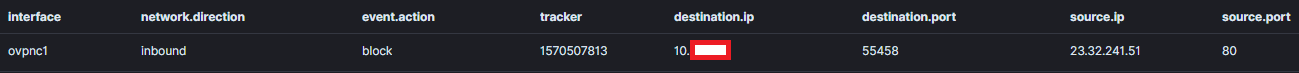
How is this possible?
-
As your popup blocks view of the other rules, how about showing them? Also a 10.x address is hardly public so you don't have to white it out. Source IP 23.xy would be a better place ;)
-
Protocol is ipv4 for both allowed rules and ipv4 + ipv6 for the blocked rule. Everything else is *.
-
You are still blanking the log entry. Also why not posting to complete log from pfSense? I suppose that is some monitoring dashboard like Grafana as source and destination are swapped and no TCP flags are shown. Check your firewall logs for that block and show that, as it would give way more info as your monitoring now e.g. TCP flags SEW etc. could point to asymmetric routing or a routing flaw somewhere.
-
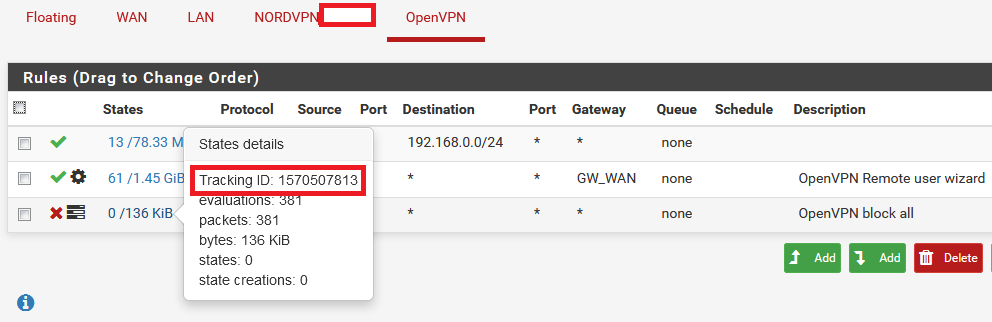
@JeGr Is the syslog entry for the block rule sufficient? I don't thing the GUI allows me to easily search for the relevant log entry?
<134>Oct 14 20:14:57 filterlog: 10,,,1000000104,ovpns2,match,block,out,4,0x0,,82,22380,0,DF,6,tcp,100,157.240.3.55,172.16.0.2,443,49150,48,A,2482124958:2482125006,2272804108,113,,nop;nop;TS172.16.0.2 is the IP of the vpn client. I cannot find a rule with tracker 1000000104, however on the ovpns2 interface I do have a block all rule that appears to be ignored.
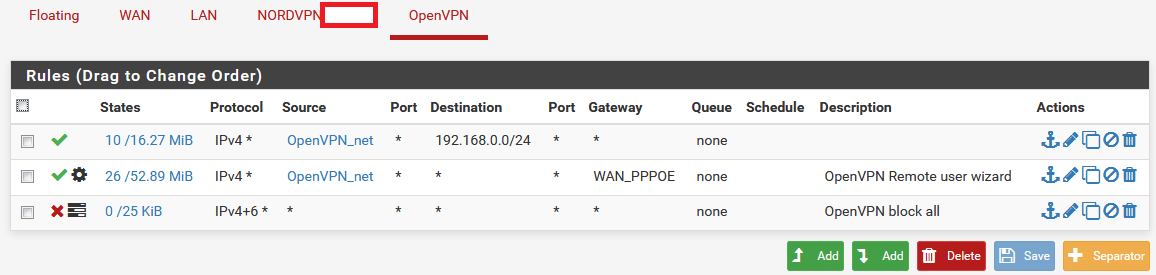
OpenVPN_net is 172.16.0.0/29. The tracker ID of the block all rule is 1570507813. No log entry on the ovpns2 interfaces matches that ID.
However, I do see matches for rule 1570507813 however they are for the ovpnc1 interface (NordVPN).
<134>Oct 14 18:44:34 filterlog: 57,,,1570507813,ovpnc1,match,block,in,4,0x0,,54,37736,0,DF,17,udp,311,78.130.254.59,10.8.8.42,51413,44994,291The NordVPN interface only has a block all rule, no other rules. I do not see any entries for that block rule.