OpenVPN Site to Site with 3 locations
-
Hi,
I've been trying to figure this out by myself but I just can't find the (probably easy) solution for this.
I basically have to connect 3 locations which all need to communicate with each other.
I've attached the layout as a paint drawing.
The thing I haven't been able to make work is the connection between location B-C.
From A->B, B->A, A->C, C->A everything works fine, i just can't reach anything from B->C or C->B.I have 2 OpenVPN Servers running on location A with two different ports and shared keys and different tunnel networks and location B has a client running connecting to UDP 1196 and location C a client connecting to UDP 1197.
Basically everything is set up as described in the documentation with A as server and B+C as clients:
https://docs.netgate.com/pfsense/en/latest/book/openvpn/site-to-site-example-configuration-shared-key.htmlCan anybody help me out to get this working?
Thanks already
Cheers
Michael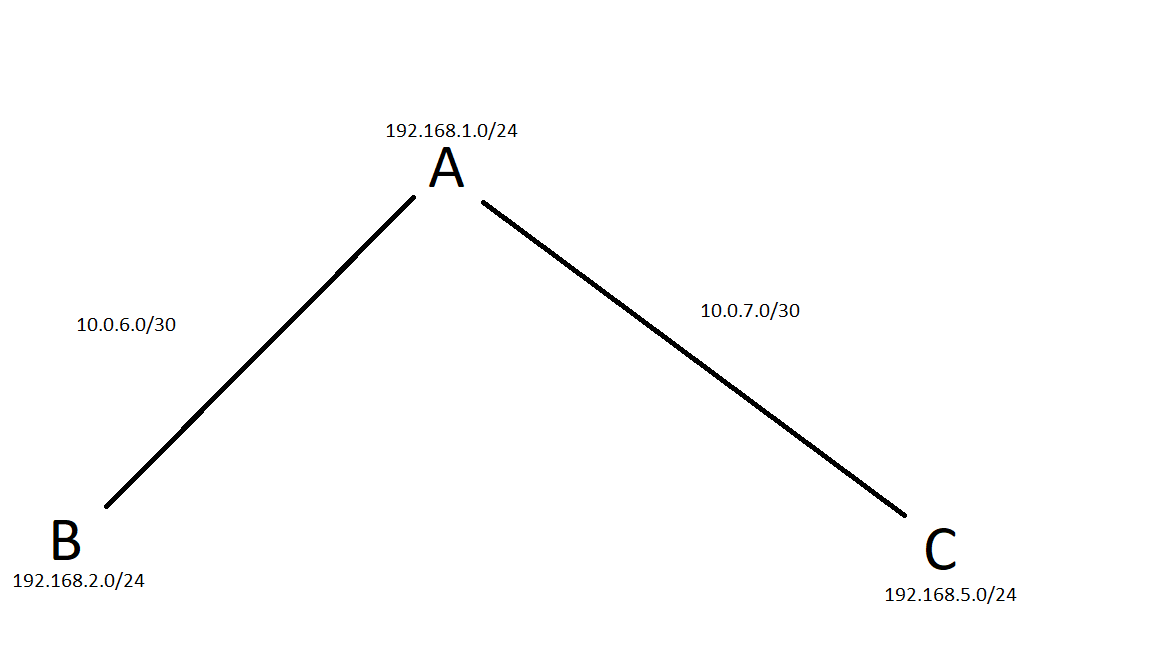
-
In the client settings at B add the LAN network of C 192.168.5.0/24 to the "IPv4 Remote Network/s". At C add 192.168.2.0/24 to the "IPv4 Remote Network/s", comma-separated.
So at B the box should look like "192.168.1.0/24,192.168.5.0/24", at C "192.168.1.0/24,192.168.2.0/24".
This adds routes to the respective other site when the connection is established. -
This is actually one of the things I've already tried, but the behaviour didn't change with those settings.
I just put this in again and restarted all OpenVPN services but it still doesn't work unfortunately.
I've also tried adding push "route 192.168.5.0 255.255.255.0" and push "route 192.168.2.0 255.255.255.0" at the VPN Server settings with no luck.
-
The "push route" option is for pushing routes from a OpenVPN server to a client. You have to add routes for the remote networks to the clients, so you will rather use a "route" command on the client here. However, the "IPv4 Remote Network/s" does the same and is the recommended way on pfSense.
So if your routes work, maybe you need to add firewall rules on one of the involved pfSense boxes or on the destination devices to allow the access.
Without knowing more details it's hard to say what's wrong. -
You can't push routes with shared-key. You have to use TLS/Certs if you want to push routes. Else you have to put the proper remote networks at B (192.168.1.0/24,192.168.5.0/24) and C (192.168.1.0/24,192.168.2.0/24).
-
edit - deleted this line.
OpenVPN Firewall rule at site "A" has to also allow B and C ips through.
-
@chpalmer said in OpenVPN Site to Site with 3 locations:
Remote Networks on "A" would need to be (192.168.2.0/24,192.168.5.0/24).
Sort of. They would need to each be on the proper server going to that site.
-
@Derelict said in OpenVPN Site to Site with 3 locations:
Sort of. They would need to each be on the proper server going to that site.
I did misspeak that...
The A-B link would be "remote networks" 192.168.2.0/24 on the A side
and
The A-C link would be "remote networks" 192.168.5.0/24 on the A side.
But since I apparently need new glasses I missed the part where the OP said he had those links working... DOH!