block network IPs off attackers in a portforwarding environment
-
Hello all,
Im having here a portforwarded environment and want to block attackers with a network alias and put it on every interface and trying a lot around but Im not able to block.
the rule that is triggered to allow:pass out log inet all flags S/SA keep state allow-opts label "let out anything IPv4 from firewall host itself"How can I block attackers- net.
Can someone help?tia
Stefan -
Where are you putting the rules?
Lets say you have a port forward setup for https 443 that gets sent to your lan IP 192.168.1.100
This will create an allow rule on your wan with access to dest 443.. Above that put a block rule to dest 443, with the source on this block rule use an alias that includes all the IP(s) you want to block from getting to your port forwards.
Here I thru together quick example.. In my alias bad guys I put 1.2.3.4 as same IP.
Now I just put a rule that blocks access - in this case to anything (works too) guessing you wouldn't want these IPs accessing any of your port forwards.
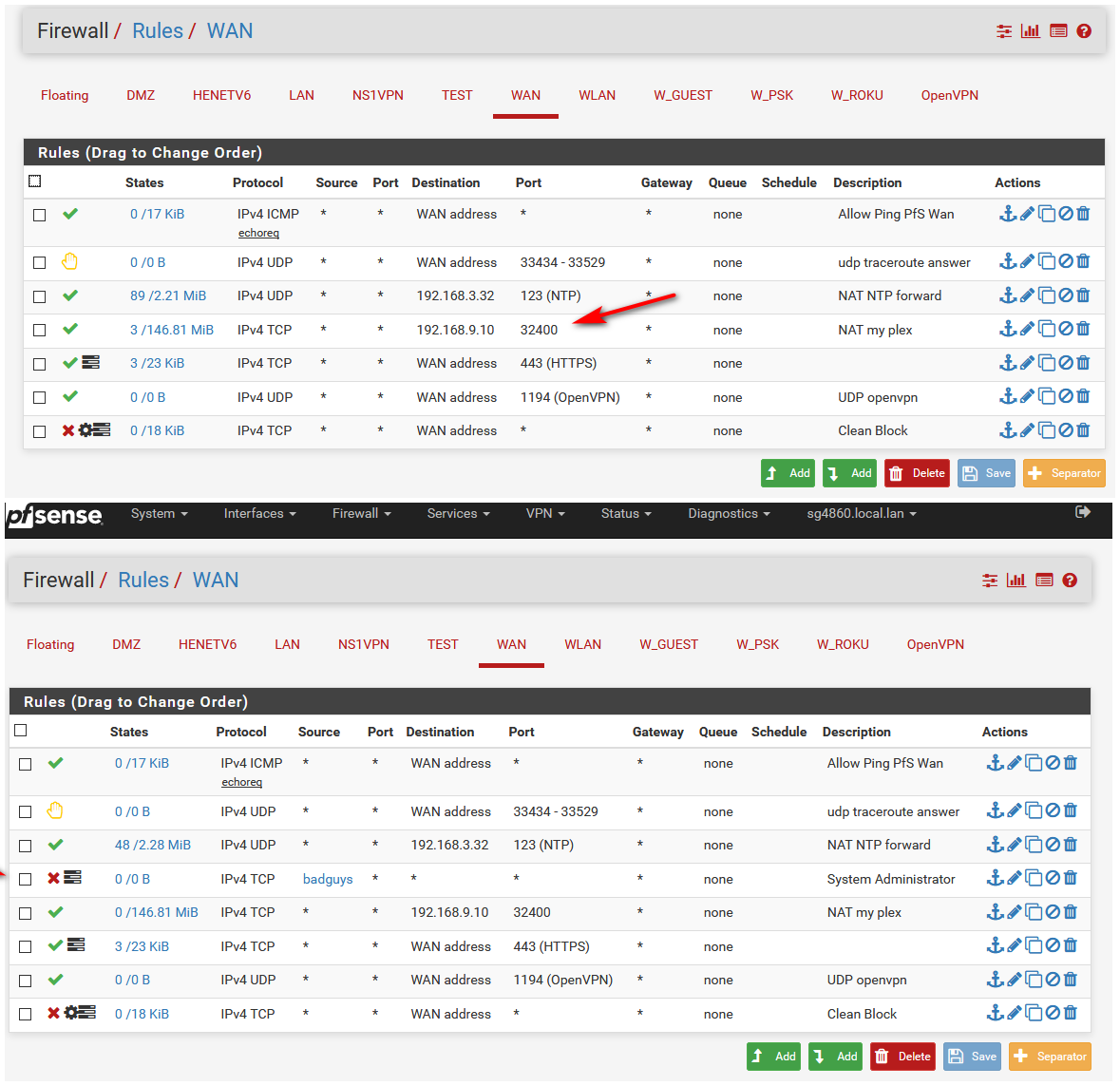
Rules are evaluated top down, first rule to trigger wins.. So if you have a rule that blocks above your allow then if the traffic matches that block it would be blocked before it can get to your allow rule.
You prob want to put that block rule at the very top above any port forwards you have.
See the forward that allows access to my plex... This block rule above it would block any traffic coming from 1.2.3.4 from accessing my plex or anything below where that rule is...
-
Hello johnpoz,
yes I thought this too. But it seems I do something wrong:
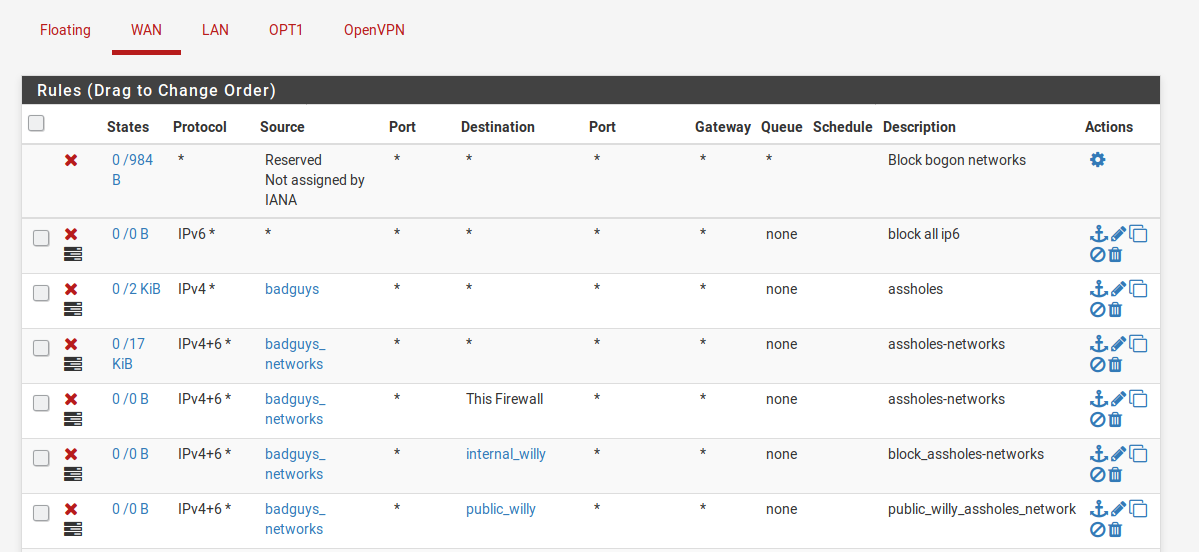
The traffic goes trough.
Can you help?
Tia
Stefan -
Those rules have hits..
That doesn't stop your client from talking to someone that is on the bad list, that just stops them from hitting your port forwards. Also if there is an existing state those would be allowed.
You can see some of them have hits on them.
Do you have any rules in floating that would allow what your trying to block. That rule is to allow nats to go out, and the firewall to talk, etc.. if you want to stop clients from creating traffic to something bad, then you put the block rules on the interface the clients first hit pfsense on, ie lan.
-
okay, seems I have it:
It was set "pass" in portforward table. Now I did
"create new assiociated filter rule"
Put in the correct Location. Attakers block!Super!
Thanks for great help!
Stefan -
Why would you have done that? The default of create rule is there for a reason ;)