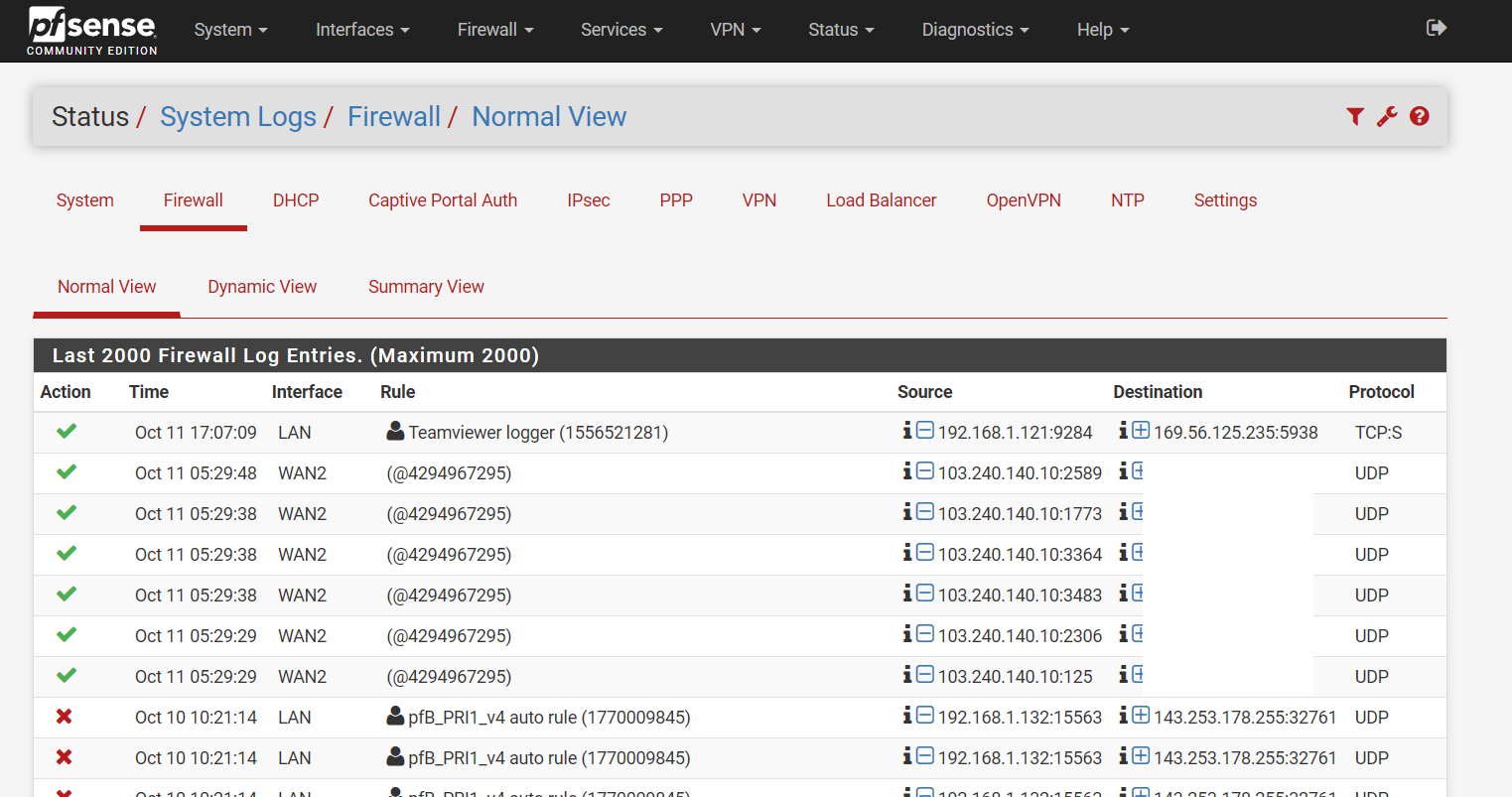
Had my pfSense been compromised?
-
I can't remember the last time I saw one marked
short. It might be a fragment. -
But the question is why is marked pass?
-
If it's a fragment that is part of an existing connection, it would be passed. It might be that the state recently expired or was purged for some other reason so it was passed in but NAT didn't get applied, for example.
-
I doubt its frag, since that is a different counter - see my output from
pfctl -s infoabove.
From the logs he lists I doubt its part of an existing connection.. From everything I find short should be dropped, so why is it logged as if it passed?
-
I'm not sure, unless it's being misinterpreted by
filterlog.If you can reproduce it reliably, you could capture the
pflogoutput directly and pipe it throughtcpdump(as described on https://www.openbsd.org/faq/pf/logging.html ) and see if that agrees. -
I can not tried to reporduce it, but you could prob for sure feed short packets via packet creation tool to try and duplicated the problem.
But seems a few users are seeing a bunch of them - as you can see from my counters I have only ever seen 2 of them... But don't recall ever seeming in the the log as pass.. will keep an eye if that counter goes up and see what my log says since feeding all logs to syslog now for retention.. But if get a chance will try and duplicate a short to pfsense and see if can try and see what it logs.
-
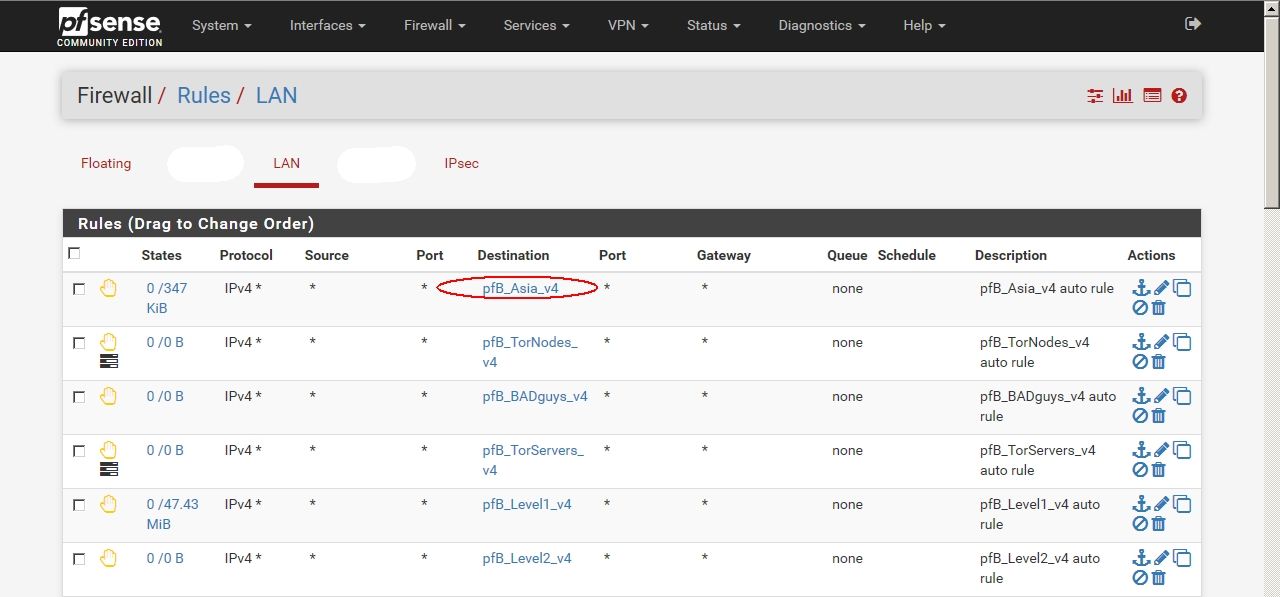
@jimp I have PfBlockerNG installed, and GeoIP Asia IP list, which includes 103.240.140.10, and it is applied as denied outbound connections on LAN, so there cannot be any existing connection to that IP.
-
@ASIC said in Had my pfSense been compromised?:
103.240.140.10
Are you blocking Hong Kong ?
andy@mac-pro ~ % whois 103.240.140.10
% IANA WHOIS server
% for more information on IANA, visit http://www.iana.org
% This query returned 1 objectrefer: whois.apnic.net
inetnum: 103.0.0.0 - 103.255.255.255
organisation: APNIC
status: ALLOCATEDwhois: whois.apnic.net
changed: 2011-02
source: IANAwhois.apnic.net
% [whois.apnic.net]
% Whois data copyright terms http://www.apnic.net/db/dbcopyright.html% Information related to '103.240.140.1 - 103.240.142.255'
% Abuse contact for '103.240.140.1 - 103.240.142.255' is 'abuse@clear-ddos.com'
inetnum: 103.240.140.1 - 103.240.142.255
netname: CTCL-HK
descr: ClearDDoS Technologies
country: HK
admin-c: CTCL1-AP
tech-c: CTCL1-AP
status: ASSIGNED NON-PORTABLE
mnt-by: MAINT-CTCL-HK
mnt-irt: IRT-CTCL-HK
last-modified: 2014-09-28T08:41:28Z
source: APNICirt: IRT-CTCL-HK
address: Flat C, 23/F, Lucky Plaza,, 315-321 Lockhart Road, Wan Chai, Hong Kong, Hongkong Hongkong 999999
e-mail: abuse@clear-ddos.com
abuse-mailbox: abuse@clear-ddos.com
admin-c: CTCL1-AP
tech-c: CTCL1-AP
auth: # Filtered
mnt-by: MAINT-CTCL-HK
last-modified: 2013-08-06T10:03:29Z
source: APNICrole: CLEARDDOS TECHNOLOGY CO LIMITED administrator
address: Flat C, 23/F, Lucky Plaza,, 315-321 Lockhart Road, Wan Chai, Hong Kong, Hongkong Hongkong 999999
country: HK
phone: +86 755 8453 0553
fax-no: +86 755 8453 0553
e-mail: abuse@clear-ddos.com
admin-c: CTCL1-AP
tech-c: CTCL1-AP
nic-hdl: CTCL1-AP
mnt-by: MAINT-CTCL-HK
last-modified: 2013-08-06T10:03:28Z
source: APNIC% This query was served by the APNIC Whois Service version 1.88.15-46 (WHOIS-UK4)
andy@mac-pro ~ %
-
@NogBadTheBad said in Had my pfSense been compromised?:
@ASIC said in Had my pfSense been compromised?:
103.240.140.10
Are you blocking Hong Kong ?
Yes, I am.
-
Just thought I'd check as some people think Hong Kong is China

-
Its also interesting that we all saw clear DDOS technologies as passed in our logs and no-one else.
Ive not seen any other IP addresses associated with this problem.
-
I've looked through the pf source code and any place I see where
PFRES_SHORT(short) reason gets set is only associated with thePF_DROP(block) action. So I'm not quite sure why it is being logged as a pass. The only difference is that whenscrubis enabled, the code path that does packet normalization sets things slightly differently, so maybe that affects how the log entry is interpreted, but the packet is still dropped on that code path. -
Is there anyway to make sure they are logged as blocked vs pass?
Yeah everything I was reading is short should be blocked, so not sure why they are logged as pass either.. Odd.. While I do have some hits in the counter for short via the info command.. I can not find anything in the logs on my syslog showing them... But then again those might of been before sending to syslog, and the counter has not gone up in the week since last did, still showing only 2.
If someone is seeing a lot of them, possible they could turn off scrub for testing to see if they are now logged blocked.
-
@johnpoz ive not seen anymore since the day three of us all saw them.
-
@hulleyrob said in Had my pfSense been compromised?:
@johnpoz ive not seen anymore since the day three of us all saw them.
I saw them on 11 & 14Oct and then not anymore.
-
maybe there is an explanation here @johnpoz
http://openbsd-archive.7691.n7.nabble.com/pf-logs-def-short-pass-in-but-should-say-block-td192809.html -
@bchan was only on the 13th for me. But reading the link below from 2012 it looks like it is just a issue that it is being displayed as a pass and was actually blocked which is the best scenario for what we are seeing.
-
That clearly seems some how related for sure, but no responses and its quite old from 2012.. But yeah good find..
-
@kiokoman Poor Leonardo. Unappreciated in his own time.
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on