OpenVPN Multi WAN Connection Problem
-
Hello pfsense community,
i hope you can help us with our problem, i did several trys to fix the problem but nothing fixed it so far.
We have a Multi WAN CARP Setup with two pfsense pcs (2.4.3-RELEASE-p1).
- OpenVPN Server bound to 127.0.0.1 / localhost
- UDP Port 1995
- Port Forwards for both WAN Interfaces (with associtated firewall rules
Example client config:
dev tun
persist-tun
persist-key
cipher AES-256-CBC
auth SHA1
tls-client
client
resolv-retry infinite
remote xxx 1195 udp
remote xxx 1195 udp
verify-x509-name "xxx" name
auth-user-pass
pkcs12 xxx.p12
tls-auth xxx.key 1
remote-cert-tls serverThe problem is the following:
Client tries first to connect to isp 2 (backup isp) --> TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
TLS Error: TLS handshake failedor
TCP/UDP: Incoming packet rejected from [AF_INET]xxx:1195[2], expected peer address: [AF_INET]xxy:1195 (allow this incoming source address/port by removing --remote or adding --float)
After 60 Secs client connect to isp1 -> Connection established.
It seems that the "reply-to" doesnt work anymore. Openvpn use always the active gateway from failover group but doesn't use the same interface from which the traffic came in.
But it worked a time ago, nothing changed (no update, no configuration change. Only add new users for vpn for example)
Tried so far:
- Reboot master pfsense
- recreated the port forward for the backup wan
- rebooted openvpn server
Kind regards and thanks for your help
Marc
-
Consider that "reply-to" doesn't work on floating rules and also doesn't work on rules defined on an interface group.
So the firewall rules allowing the incoming OpenVPN packets must be set on WAN1 and WAN2 interface tab directly. -
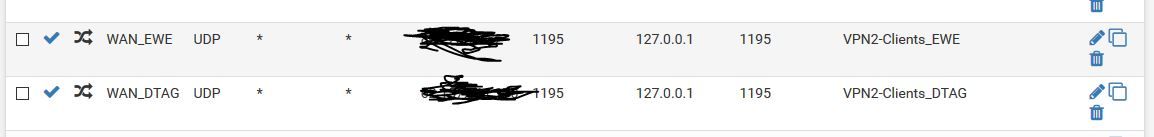
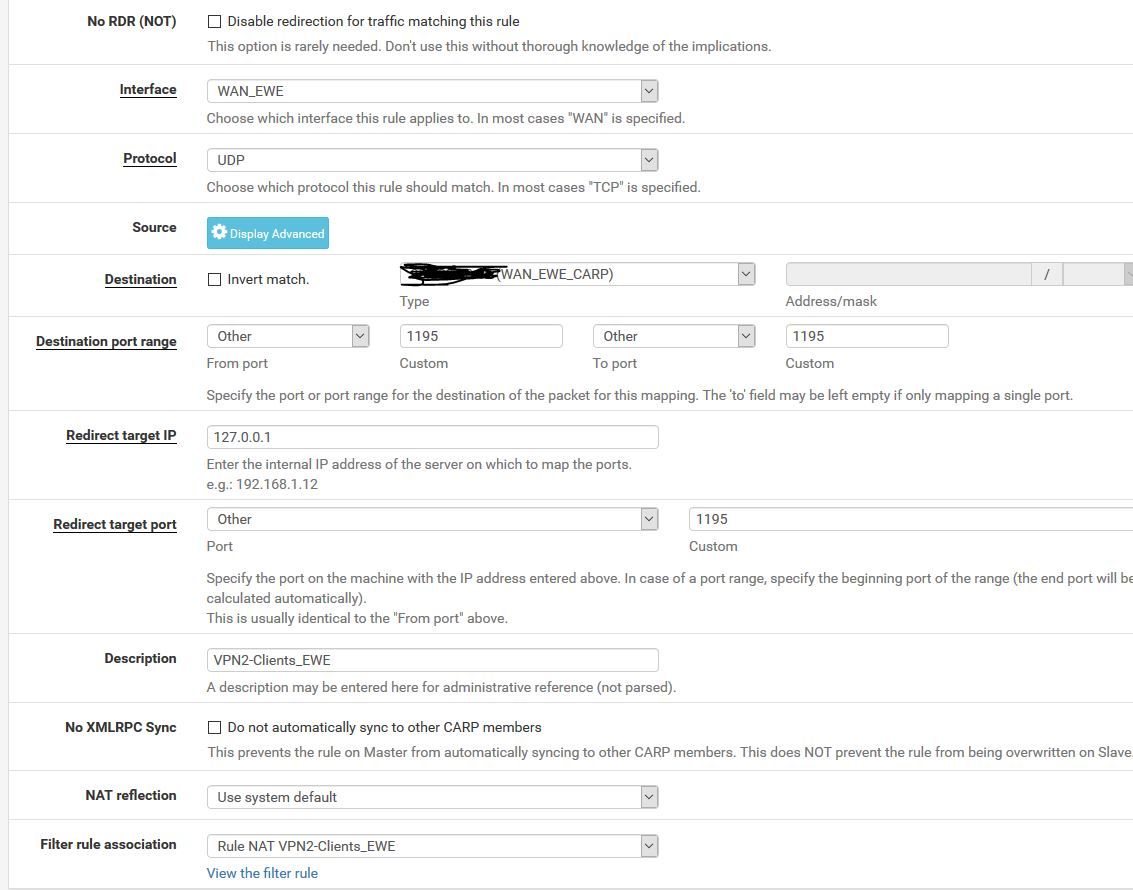
Hi Viragomann,
thats already done. See screenshot. Port Forward was created for every singline wan interface.