Layer 3 Switch to pfSense - What Am I Missing?
-
So I have this setup:
Router with two interfaces:
WAN Public IP
LAN Private IP (192.168.1.1)pfSense box with three interfaces:
WAN (connected to Router LAN Interface) 192.168.1.2 (DHCP from Router)
LAN (Connected to Cisco SG350) 10.20.92.1/24
OPT1 not configured
Default route to WAN, Static route to 10.20.0.0/16 to 10.20.92.2Cisco GS350 Switch with six VLANs:
10.20.20.1/24 (MGMT)
10.20.21.1/24 (Clients -default route for all traffic from other switches)
10.20.23.1/24 (Phones)
10.20.24.1/24 (Wireless)
10.20.29.1/24 (Utility)
10.20.92.2/24 (External Gateway)
Default Route on this switch set to 10.20.92.1 (pfSense LAN interface)
There are seven other SG350 switches connected to this switch. Each has an interface in the 10.20.2x.0 VLANs. Their default gateways point to 10.20.21.1.From the switch we can ping to 8.8.8.8 or any IP address in any of the VLANs. From a client we can ping to any VLAN ip, even to 10.20.92.2, but we cannot ping to 10.20.92.1 or any external IP. From the pfSense box we can ping any internal IP address, client or switch if we use Auto-select or LAN as our source. Id we select WAN we cannot ping to any IP except 10.20.92.2.
I know this has to be something simple I am missing. We did have this setup using a single LAN IP address range and the setup passed traffic without issue. So, can anyone tell me what I've overlooked?
Thank you!
-
So you created a gateway in pfsense point to your downstream cisco at 10.20.92.2 and then created your route(s) to your downstream networks.
And you modified your lan rules to allow for for the downstream networks not just lan net.
When you create the gateway and routes in pfsense, if using auto outbound nat it will autocreate the outbound nats for your downstream networks.
-
Yes, I created a gateway on the LAN interface pointing to 10.20.92.2 and then added a static route for 10.20.0.0/16 pointing to that gateway.
I will have to wait to double-check the LAN rules but I am pretty sure there is a any-any rule applied there. Once I get to the site again and I can double-check I will let you know.
Thank you!
-
yeah its prob any rule for lan net as the source.
So your not going to have any devices/users on the lan net right? If so you going to run into asymmetrical routing issues. Your just going to use lan as your transit to your downstream router.
-
The more I work on this the more I think the issue is in the switch and not pfSense. The switch can ping out and get replies but systems on the VLANs cannot. I will work on this some more and detail what I find. The pfSense part is simple, but hey - Firewall! - so that's where I started.

-
What are the rules on your lan?
You have this..

So 10.20.92/24 is the transit (lan on pfsense)..
Default route on your default router is 10.20.92.1Default gateways on your clients in downstream networks would be the .1 SVI on your switch.
Where you could have issue is firewall rules on your lan (transit) interface saying only LAN NET... which would only be that 10.20.92/24 network... So pinging from 10.20.20 would not work..
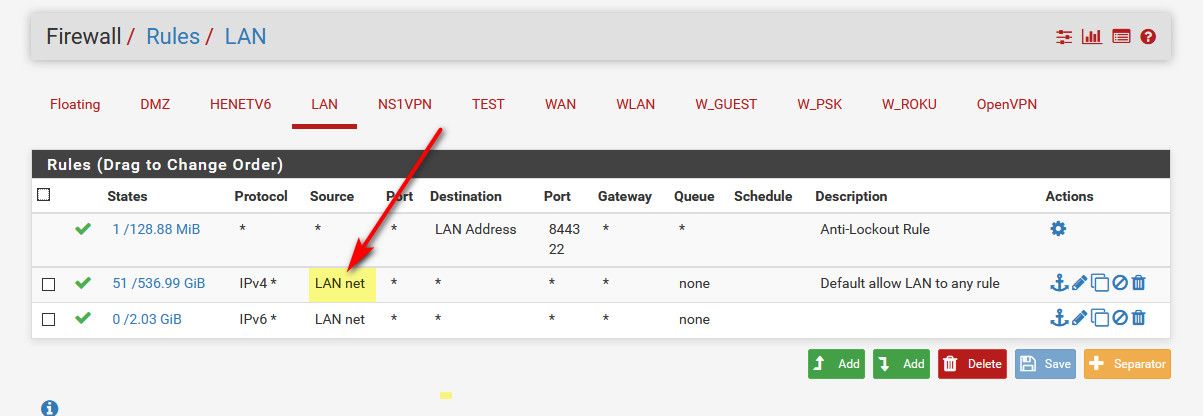
You need a gateway on pfsense pointing to 10.20.92.2, and then routes using that gateway to get to your downstream - say 10.20.20/24
-
NAT - I was missing NAT. By default, the NAT rule covers the LAN Net, but there was no NAT specified for the other VLANs in the 10.20.0.0/16 Supernet. I added NAT for them and suddenly everything was happy and working.
Thank you very much for reading this and taking the time to respond. It really is appreciated.
-
-
@average_joe said in Layer 3 Switch to pfSense - What Am I Missing?:
the NAT rule covers the LAN Net, but there was no NAT specified for the other VLANs in the 10.20.0.0/16 Supernet.
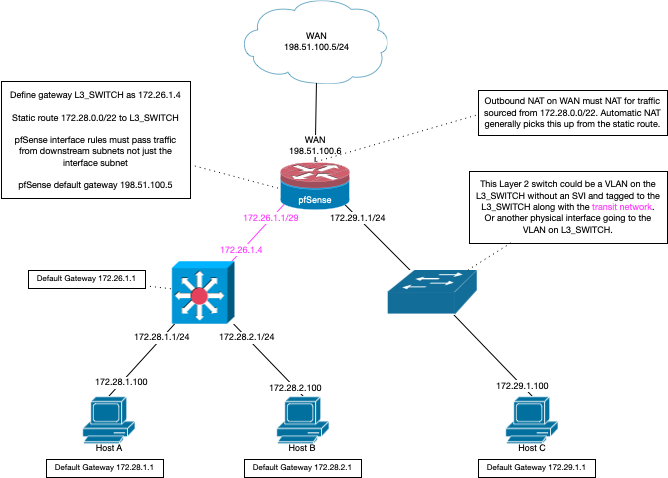
They would be if you were on automatic nat.. Had you changed this to manual? If so why? Once you create a gateway and create routes to the downstream nats they are automatically added for your outbound nat.
edit: Here you can see my auto outbound.. I then created a new downstream gateway off my dmz interface to 192.168.3.32.. I then created a route to downstream 172.16.0/24 network using that gateway and the outbound nats were auto added.
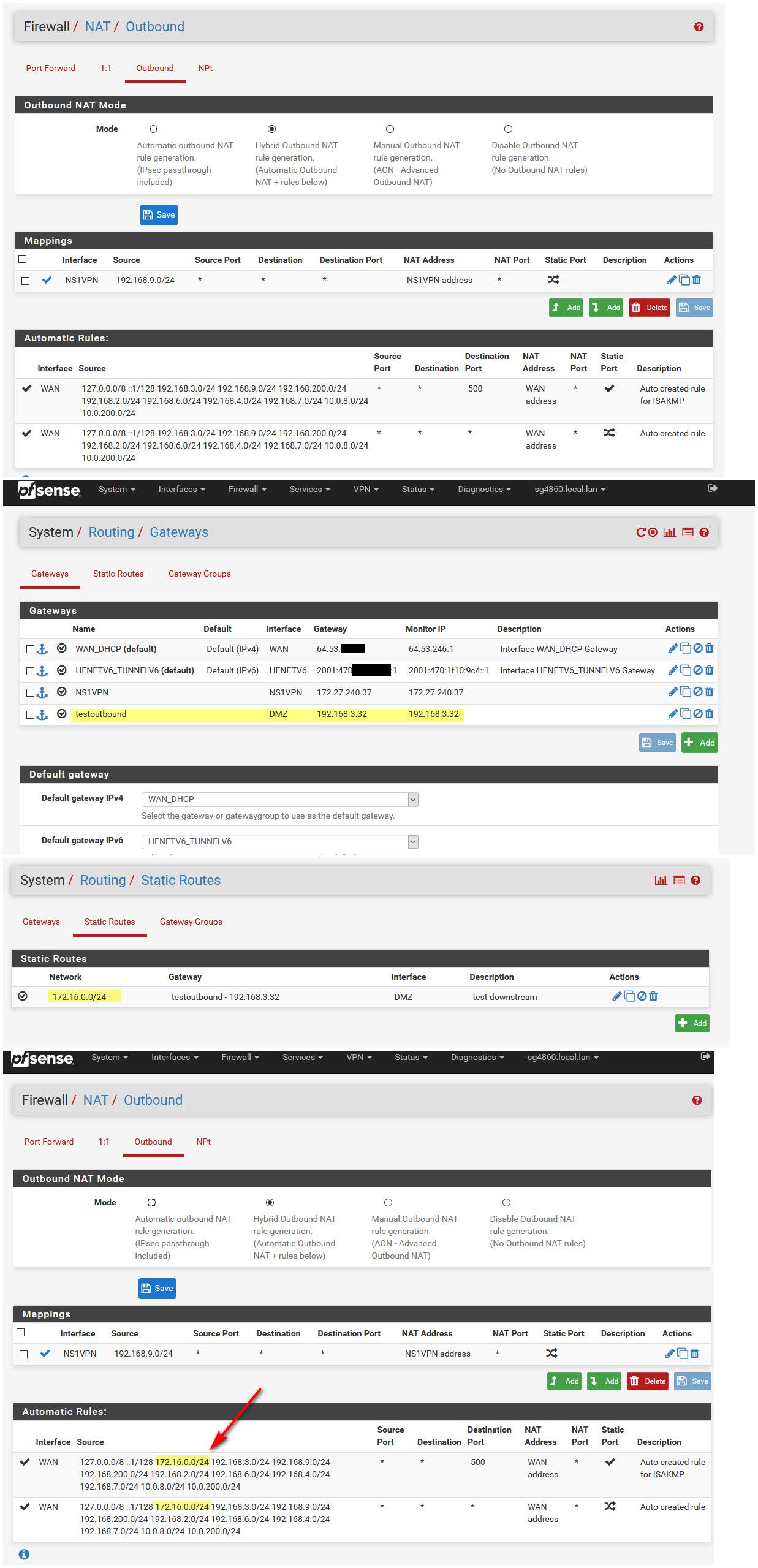
You can see that the outbound nats now include the 172.16.0/24 network to be be natted outbound.
That drawing Derelict posted - been around for many years that drawing ;) gives you all the info you would need for doing downstream networks with pfsense.
But yes you would need to modify the rules on your now transit network to allow the downstream network(s) on your firewall rules.