Pfsense as client to PiVPN problem
-
Hi,
Sorry for my english i don't use it much.
I was install OpenVPN from that command: "curl -L https://install.pivpn.io | bash", on my RaspberryPi, configure router. And its works great from my Android phone, I have access to web and my computers inside RaspberryPi LAN. But cant configure pfsense as a client.
I was import certificate on pfsense and configure as client like as below on screenshot. But cant connect to VPN server. Anyone can help?pfsense logs
Oct 25 16:53:56 openvpn 9764 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info. Oct 25 16:53:56 openvpn 9764 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Oct 25 16:53:56 openvpn 9764 TCP/UDP: Preserving recently used remote address: [AF_INET]`ip address:1194 Oct 25 16:53:56 openvpn 9764 UDP link local (bound): [AF_INET][undef]:0 Oct 25 16:53:56 openvpn 9764 UDP link remote: [AF_INET]`ip address`:1194 Oct 25 16:54:56 openvpn 9764 [UNDEF] Inactivity timeout (--ping-restart), restarting Oct 25 16:54:56 openvpn 9764 SIGUSR1[soft,ping-restart] received, process restartingMy Server log
Oct 25 16:22:32 raspberrypi ovpn-server[767]: tls-crypt unwrap error: packet authentication failed Oct 25 16:22:32 raspberrypi ovpn-server[767]: TLS Error: tls-crypt unwrapping failed from [AF_INET]`ip address`:45583That my server.conf
dev tun proto udp port 1194 ca /etc/openvpn/easy-rsa/pki/ca.crt cert /etc/openvpn/easy-rsa/pki/issued/raspberrypi_cc7360f7-51c2-4f3d-83d3-e22ef31aeec7.crt key /etc/openvpn/easy-rsa/pki/private/raspberrypi_cc7360f7-51c2-4f3d-83d3-e22ef31aeec7.key dh none topology subnet server 10.8.0.0 255.255.255.0 # Set your primary domain name server address for clients push "dhcp-option DNS 1.1.1.1" push "dhcp-option DNS 1.0.0.1" # Prevent DNS leaks on Windows #push "block-outside-dns" # Override the Client default gateway by using 0.0.0.0/1 and # 128.0.0.0/1 rather than 0.0.0.0/0. This has the benefit of # overriding but not wiping out the original default gateway. push "redirect-gateway def1" client-to-client keepalive 1800 3600 remote-cert-tls client tls-version-min 1.2 tls-crypt /etc/openvpn/easy-rsa/pki/ta.key cipher AES-256-CBC auth SHA256 user nobody group nogroup persist-key persist-tun crl-verify /etc/openvpn/crl.pem status /var/log/openvpn-status.log 20 status-version 3 syslog verb 3 #DuplicateCNs allow access control on a less-granular, per user basis. #Remove # if you will manage access by user instead of device. #duplicate-cn # Generated for use by PiVPN.ioMy client.ovpn.
client dev tun proto udp remote lu******.net 1194 resolv-retry infinite nobind persist-key persist-tun remote-cert-tls server tls-version-min 1.2 verify-x509-name raspberrypi_cc7360f7-51c2-4f3d-83d3-e22ef31aeec7 name cipher AES-256-CBC auth SHA256 auth-nocache verb 3 <ca> -----BEGIN CERTIFICATE----- * * * -----END CERTIFICATE----- </ca> <cert> -----BEGIN CERTIFICATE----- * * * -----END CERTIFICATE----- </cert> <key> -----BEGIN PRIVATE KEY----- * * * -----END PRIVATE KEY----- </key> <tls-crypt> # # 2048 bit OpenVPN static key # -----BEGIN OpenVPN Static key V1----- * * * -----END OpenVPN Static key V1----- </tls-crypt>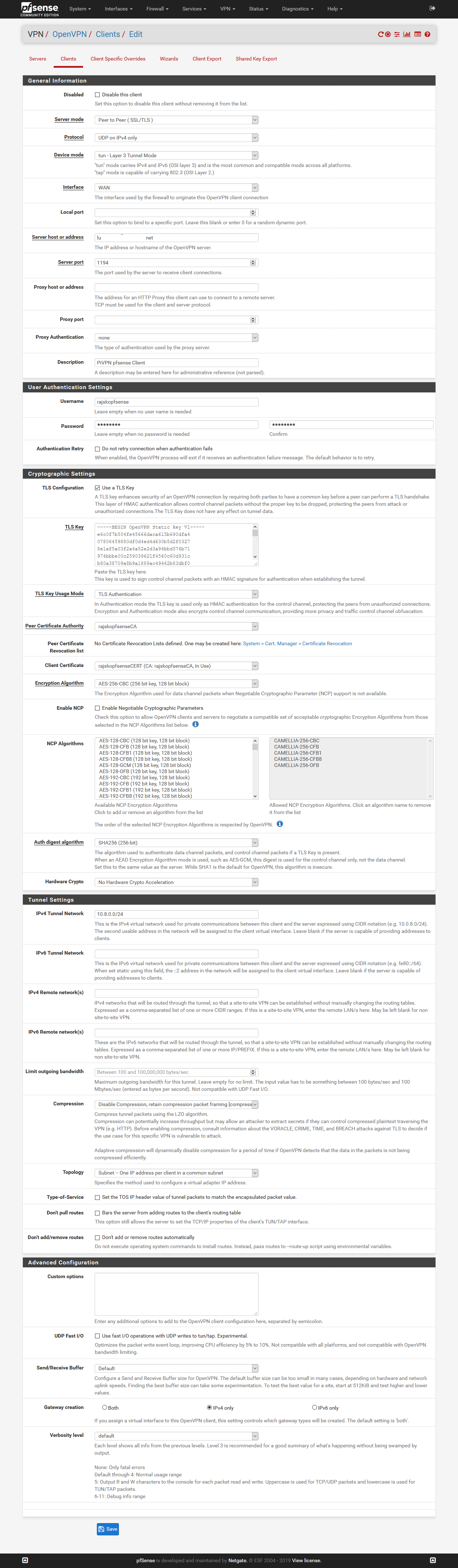
-
I am quite late to reply and I suspect your knowledge will prove me wrong but I got my pfsense to connect to my UK PiVPN (RPI3b+) by having the following different:
TLS Key Usage Mode - TLS Encryption and Authentication
Verbosity level - 3 (but with default I suspect it will also run)I get the connection, pfSense connects as a client, and the new interface gets the tunnel IP but I cannot get the gateway up and I am stuck on it working on it as of a week. Maybe you will be able to help me with that step.
As said, I am self taught and I have no education background in all of this so my apologies if my reply seems a bit too simple.
-
Of course mark also don't add/remove routes or don't pull routes. Otherwise you will kill the lan connection (don't understand why but it does).