Optimizing P2P (Shared key) VPN speed
-
Hi guys,
I have an Open VPN P2P (Shared key) up and running.
The problem is that the connexion is very slow, making it almost unusable.
Each office has a 1000 mbps (up), 1000 mbps (down), optic fiber internet connection.
On one side there is a SG-3100 (headquarters)
On the side there is a SG-1100 (remote office)We're using the VPN mostly to connect to SMB shares.
With 1000/1000 connections on both side, I was expecting to have a speed similar to what we were experiencing locally.
The reality is that every day, we experience such slow speed that it is impossible to work, so I really need to fix this and improve the speed. Any help would be greatly appreciated.
I posted my configuration below.
My questions :
- What parameters can I tweak to make the whole experience faster?
- Encryption Algorithm : right now set to AES-128-CBC
- NCP Algorithms : right now set to AES-128-CGm
- Auth digest algorithm : right now set to SHA256
- Hardware Crypto : right now enabled
- Compression : right now set to LZ4 v2
- UDP fast I/O : right now enabled
- Anything else??
- Is there any way to prioritize the VPN (ex: QoS)? I tried running the trafic shaper wizard but I couldn't find anything regarding OpenVPN
- Any other tips would be greatly appreciated
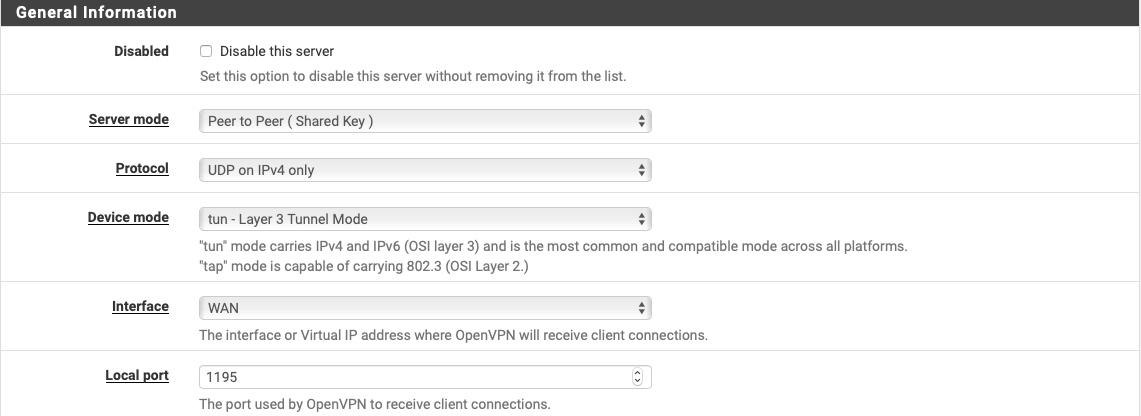
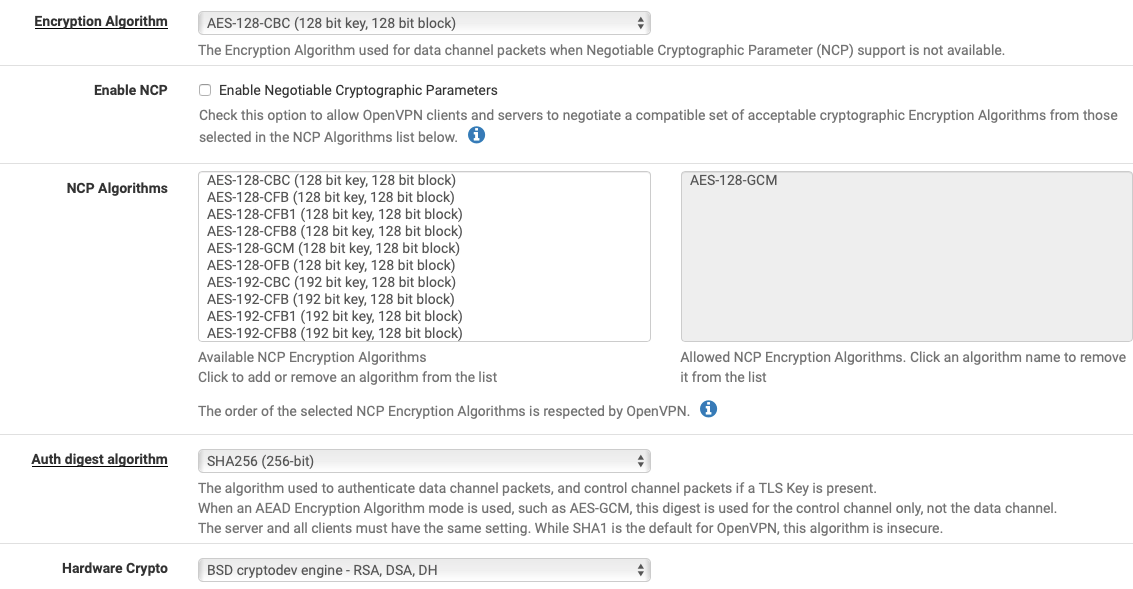
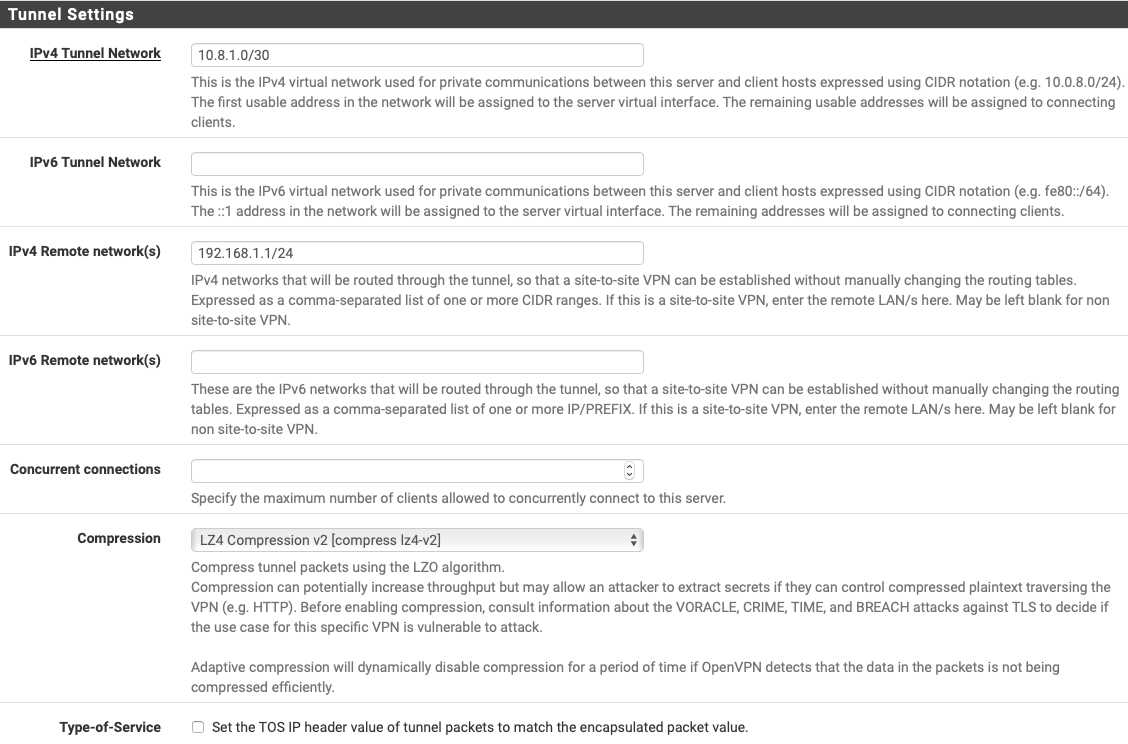
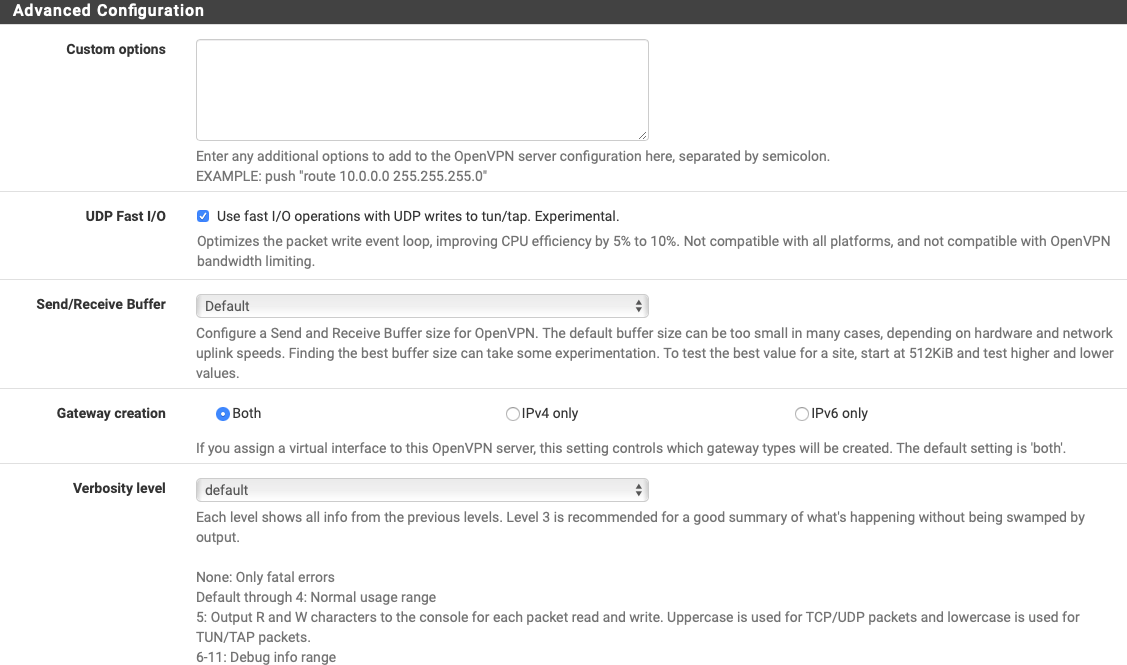
- What parameters can I tweak to make the whole experience faster?
-
Something is definitely wrong. I have pfSense virtualized under ESXi at work, and an SG-1100 at home. Work link is 100/100, home is 150/15. OpenVPN is smooth as butter. The only difference in my settings as compared to your is Enable NCP checked, and the Compression which I have set to Adaptive LZO Compression [Legacy style, comp-lzo-adaptive].
-
So I just read this:
https://community.openvpn.net/openvpn/wiki/VORACLE
And therefore disabled compression altogether.I'd still like to know if there's any way I can prioritize VPN trafic in pfSense (via trafic shaper or else).
Thanks!
-
It shouldn't make that much difference unless your link is being pounded all the time, and you have gigabit links on both sides which makes that scenario less likely. Have you done any tests to determine what is normal for the route between those two units?
-
@KOM said in Optimizing P2P (Shared key) VPN speed:
It shouldn't make that much difference unless your link is being pounded all the time, and you have gigabit links on both sides which makes that scenario less likely. Have you done any tests to determine what is normal for the route between those two units?
No and I wouldn't know how to make such tests.
But I would love to test everything I can if you have any recommendation!
-
Do not select any Hardware Crypto on server and client side.
Addmssfix 1400to the Custom options field and try again.
AES-128-CBC/SHA256/AES-128-GCM is fine, it will use AES-128-CBC/SHA256 in your case because you did not select NCP.
Fast I/O is fine.You can also play with Send/Receive Buffer value up to 512K, anything above that makes no difference in my experience.
-
@BlazeStar Install the iperf package on both pfSense nodes. Run one as client and the other as server. This will test the throughput from WAN to WAN.
https://www.youtube.com/watch?v=D4KVh5sId54