How to close Port 23, 53 and 80 on WAN?
-
So your testing to some public IP from a vpn connection.. How would you think that is forwarded down the tunnel to you? Does your vpn support port forwarding? Did you set up those ports to be forwarded down the tunnel to pfsense?
There are not many vpn services that even support port forwarding, and even the ones that do require you to set them up, and more than likely for sure would not support ports like 80 and 23..
-
If you packet capture while you are testing and the SYN packets do not arrive on the pfSense interface, it is not the pfSense firewall that is responding there. Again, look upstream for your "big security hole."
-
My VPN provider supports it, but I have not changed any settings on my VPN account, it is turned off by default.
PfSense is also mostly on default settings, only OpenVPN has been set up ...
-
Again, pcap on your OpenVPN. If the SYNs don't arrive, something upstream is responding there.
-
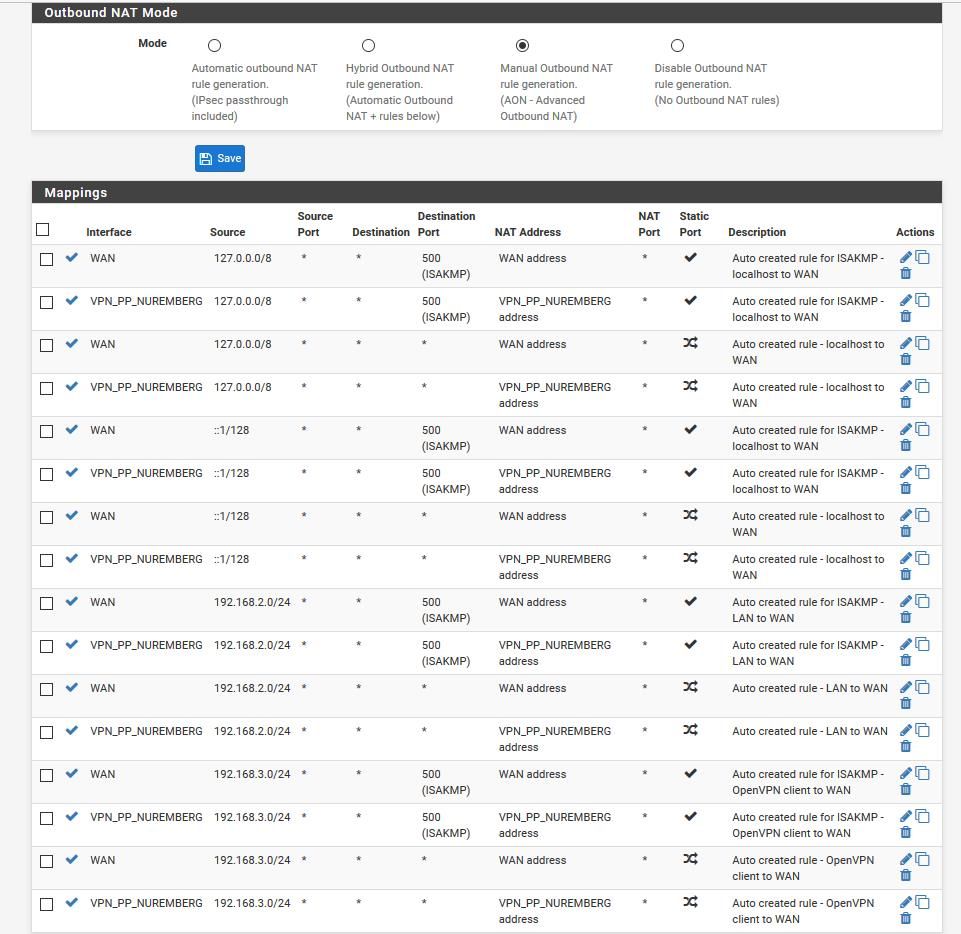
Any chance, that's the cause?
I'm at a loss -
DUDE what part do you not get here... If your testing to your VPN public IP... Its not Pfsense answering, or anything behind pfsense... Its your VPN service!!! No your outbound nat has ZERO to do with it!!
-
I've done tests with all the filters turned off by the VPN provider, that's the result.
It looks to me that the ping has gone through the pfSense.
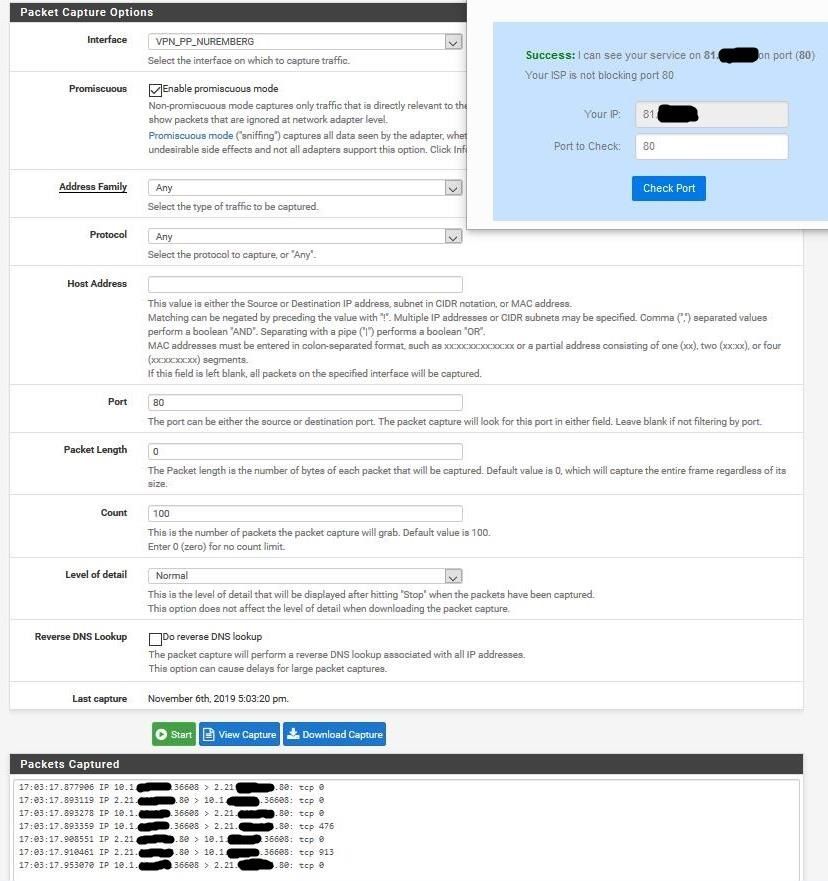
.
-
That looks like you connecting out.
It's certainly not ping since ping is ICMP not TCP.
-
This post is deleted! -
Dude you have been given the info... There is NO issue with pfsense... You not understanding basic concepts is not pfsense problem.
Out of the box pfsense doesn't allow anything unsolicited inbound to its wan... If you create some tunnel and then force traffic down that tunnel to pfsense no matter what it is - those rules would be on your tunnel interface..
And yeah that traffic your showing is clearly OUTBOUND to port 80...
-
Thanks for the help so far, so it's definitely the VPN, you say?
I wrote a ticket to my VPN provider, to be honest, I would be surprised if they answer at all.
-
It is something else upstream responding.
-
They have actually responded, but I'm not so sure what to think of it.
Sounds like the "it's a feature" excuse ..."That's a misunderstanding. The scan was based on the currently used IP address of our VPN server. There are necessarily a lot of open ports, otherwise the server could not offer the necessary services."
-
@Bernd6560 said in How to close Port 23, 53 and 80 on WAN?:
"That's a misunderstanding. The scan was
Err are they saying the run their VPN using ports 23, 53 and 80 to try and anonymise what the servers look like from the internet ?
-
@NogBadTheBad I asked what you wrote, here is the response ...
"I have already written that it is running on the VPN server services."
-
It's possible they run vpn services themselves on the 53 and 80 ports to try and circumvent outbound restrictions for some locations. That would explain also say the 465 port.. 23 seems odd.. That is normally not going to be allowed outbound from anywhere..
Doesn't matter why to be honest, The point is this whole thread has been complete an utter waste of everyone's time.. Since what some host on the internet answers to has zero to do with the pfsense wan rules.
Its a akin to omg, www.google.com answers to 80 and 443.
-
Just to complete the info : what are the rules on your OpenVPN interface ?
That's the interface being used when you use your VPN service.
It's the OpenVPN that acts as your WAN interface now (the real WAN interface just transports the VPN tunnel outside - initiated from the inside iof your network - pfSense itself or some other device).Your VPN service probable NAT's standard 'usual' ports to you, like 23,53,80 443 etc.
That's no big deal actually, up to you to block all incoming non solicited traffic.On a default pfSense with no rules added by you - no VPN (client) setup, just the minimal "click and online" setup, there will be no security issues.
Do not take my word for it, just do the test.Now, when you find issues after adding things like 'OpenVPN client' I tend to say : finish your setup first - or check what "unknown facilities" you added to your setup .
This question is easy to answer :
@Bernd6560 said in How to close Port 23, 53 and 80 on WAN?:
That's a big security hole, so how can I close these ports?
Shut down the VPN connection - and you'll be fine.
-
Those ports are not going to be sent down the tunnel to his box... Not unless his vpn supports them and he set them up... I would be LARGE sums of money that there is no vpn service on the planet that would forward those down.. For them to do that they would need an IP for every single client..
-
@johnpoz said in How to close Port 23, 53 and 80 on WAN?:
Those ports are not going to be sent down the tunnel to his box...
I asked about it, you're right.
I would bet LARGE sums of money that there is no vpn service on the planet that would forward those down.. For them to do that they would need an IP for every single client..
You would probably lose that bet, they do just that.
If anyone is interested, here is the full conversation ->
[me]
Why are LESS services running with your filters?[staff]
Presumably because the tests were done with different IP addresses (of the VPN server). Some of the services do not run on all IP addresses, or there are different services behind the ports depending on the IP address.[me]
Is port 23 and 80 NORMAL?[staff]
Yes, depending on the IP address of the VPN server this is normal. These are IP addresses that you share with other other companies, and in addition to which some ports are used for services of the server. That there are ports open and in use is, as already written perfectly normal. Sure, we could close down all ports, then just none of the services on the VPN servers would work anymore. ;)[me]
Does INBOUND (port 23, 80) get through to me?[staff]
No, I had already written several times. What is passed through are the ports of the port forwarding, of which we offer two different types, both of which can be configured on the corresponding configuration page in the customer area of our website. -
@Bernd6560 said in How to close Port 23, 53 and 80 on WAN?:
[staff]
No, I had already written several times.There's a lot of that going around. Plenty of explaining going on but not a lot of listening.
What is passed through are the ports of the port forwarding, of which we offer two different types, both of which can be configured on the corresponding configuration page in the customer area of our website.
Exactly. If they offer port forwarding (some do) you have to configure it. Then you have to pass that traffic on the OpenVPN or assigned interface tab for the connection to be passed into the firewall.