Inter vlan routing issues
-
Hi all,
I have currently two vlans setup:
-
list item10.0.0.0/24 the default LAN
-
list item10.0.70.0/24 Wireless vlan
I am trying to prevent inter vlan routing but then allow an ip address to communicate between the vlans. The issue at the moment is that I can't even prevent inter vlan routing.
Firewall Rules:
LAN

Wireless

From what I understand the above should prevent all inter vlan routing but it is not working, I am still able to ping from 10.0.0.10 through to 10.0.70.6.
Could someone please show me the errors of my ways so that I can continue to build the other vlans I want.
Thanks in advance.
Blinky
-
-
This post is deleted! -
@blinkydamo said in Inter vlan routing issues:
m what I understand the above should prevent all inter vlan
Looks like the rules are wrong, bit hard to tell with the tiny screenshots.
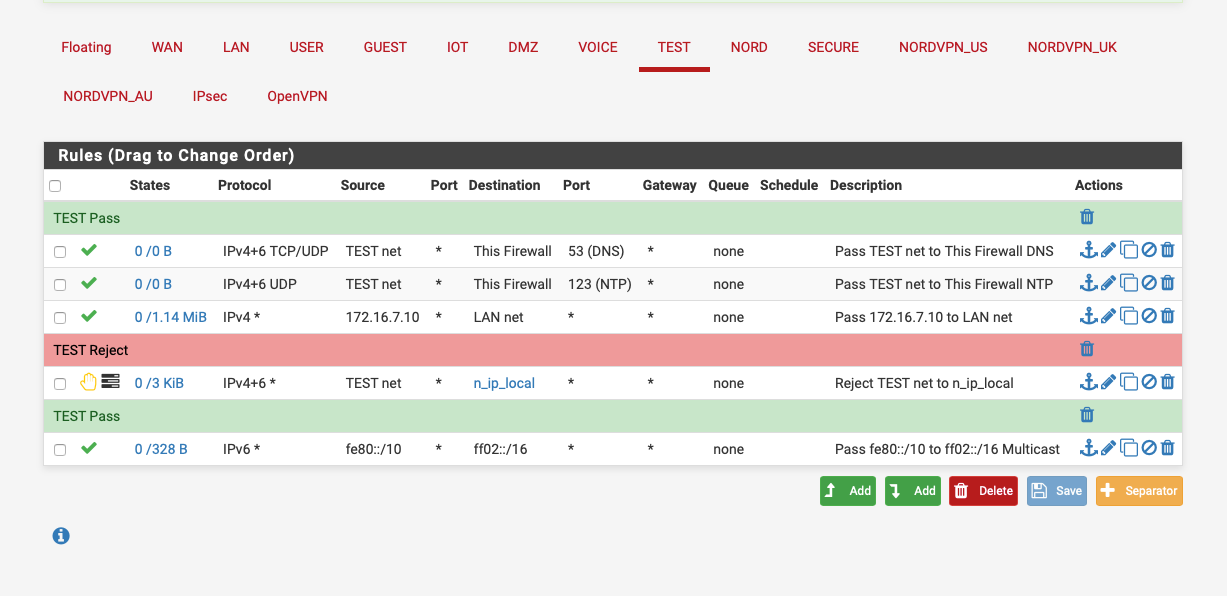
The 3rd rule would allow traffic from 172.16.7.10 to anything on the LAN net and everything else would be blocked.
n_ip_local is an alias with all my subnets in.
-
@blinkydamo said in Inter vlan routing issues:
list item10.0.0.0/16 the default LAN
list item10.0.70.0/24 Wireless vlanYou understand those overlap right.. 10.0.70/24 falls under 10.0/16
-
@johnpoz said in Inter vlan routing issues:
@blinkydamo said in Inter vlan routing issues:
list item10.0.0.0/16 the default LAN
list item10.0.70.0/24 Wireless vlanYou understand those overlap right.. 10.0.70/24 falls under 10.0/16
LOL didn't even spot that.
-
And yeah those rules are wrong as well, he has the other vlan listed as source in his rules.. Which will never happen - how could lan net be the source IP into vlan interface?
If you want to stop vlan from talking to lan, then on the vlan interface your block would be to lan net as the dest, not the source.
I don't see how pfsense would of even let him create those networks.. You can not create a vlan or interface with a network that overlaps another network on pfsense. So my guess is the info he as given is not correct - maybe they are both /24s Why anyone would use a /16 as a mask for a local network in the first place?? I can not think of a use case where that would ever make any sense. As a route, as a firewall rule source or dest - sure ok.. But actually on the interface - no.
-
Sorry all, mis-typed.
The LAN IP address is 10.0.0.0/24 and the Wireless is 10.0.70.0/24.
I am trying to upload better images but in the meantime am I understanding correctly that in the wireless vlan I need to place a block where the source is any and the destination is the LAN net? I have just placed a block source * and dest as LAN net into the wireless vlan and I can still ping a wireless device from the lan network.
Do both the LAN and Wireless vlans need to have blocks for each other?
-
Look at my example that blocks traffic from my TEST network to any other lan.
The rule above my reject rule allows a specific host to access my LAN network.
If you don't want LAN -> WIFI you'd also need a block rule on the LAN interface where the source is LAN net
https://www.netgate.com/resources/videos/
-
Post your rules!! They are evaluated top down, first rule to trigger wins, no other rules are evaluated.
Keep in mind that even when you add a new block rule that would block, if you have any existing states for that traffic - they would still be allowed.. You have to flush any existing states that would be allowing the traffic you are wanting to block.
And the source wouldn't be any, it would be the source network - any works, but its not as clean looking.