Dedicated VLAN for network devices (switch, APs, Pfsense)?
-
Hi
I'm setting up a new pfsense box with a few switches and access points from Unifi and Netgear (getting rid of the USG) -
my plan was to run 3 or maybe 4 VLANS-
SAFE: This is the VLAN for all my PCs and Servers
-
IOT: VLAN for IOT devices
-
GUEST: VLAN for guests
So now I'm wondering if I need another VLAN where I place my network equipment - things like network switches, access points and the PFSENSE box itself?
What is best practice? Wouldn't that be the so-called Management VLAN? In a Ffsense setup would LAN = Management VLAN?
Thanks for your help.
Regards
-
-
That depends entirely on your situation. While I have set up separate management VLANs, I haven't done it a lot. It is more secure however. Bear in mind, not all equipment supports management on a VLAN.
-
I wouldn't bother doing it that way - another VLAN for that stuff.
Is this at work, or at home? If at work, is there some type of INFOSEC policy you're trying to stick to? Then it makes sense.
Jeff
-
Think I may have gone a bit OTT

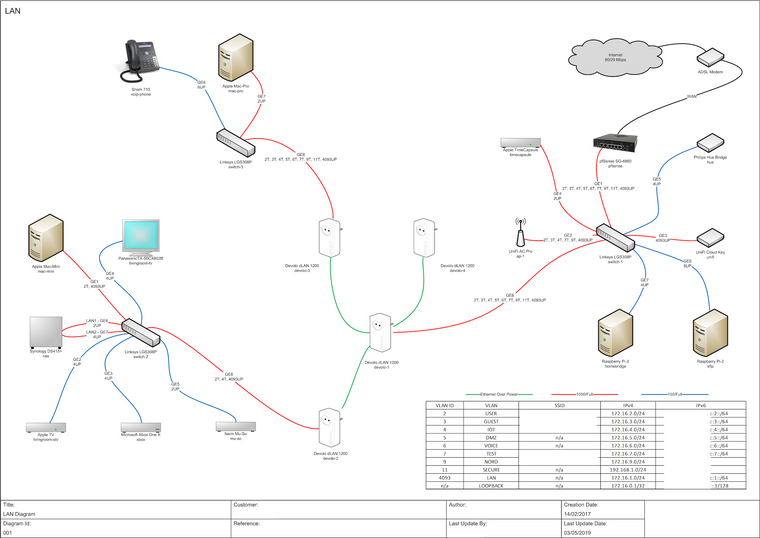
-
It's for a set up at home - so maybe enough to have 3 VLAN then (SAFE, IOT, GUEST).
I still don't quite understand the purpose of PFSENSE's VLAN1/native LAN (according https://docs.netgate.com/pfsense/en/latest/book/vlan/vlans-and-security.html?highlight=vlan1)
Why is it there? And what should we use it for?
Thanks
-
It has been a long standing practice, especially in the corp world to not use the default vlan of a switch.
Doesn't mean you can not use it.. You just need to be aware that all ports default to being in this vlan.. So you should change the vlans of all ports is all.
You wouldn't normally run the management of the switch in the default vlan, on the chance that you forget a switch port in this vlan and now some device that plugs in would be on the management vlan, etc.
As long as you pay attention, and make sure only the devices you want in vlan 1 are in vlan 1 there is not a problem with using it..
Common practice of moving all ports to a unused vlan, and then shutting them down if not used should prevent any unwanted access to vlan 1.
@NogBadTheBad why do you have your nas in 2 different vlans? Also why not leverage some of the other ports on your 4860 for vlan uplinks... You have all your vlans sharing the same physical link, so your intervlan traffic is going to be bottlenecked by the limit of that physical port. Why not create a lagg and put all the vlans on the lagg, or just split the vlans across the different physical ports manually?
-
The 2 ports in the nas is down to the Naim Muso player that’s controllable via DNLA from my iPhone / iPad that sit on the USER VLAN and the Apple-TV, TVs that sit on the IOT VLAN, it’s not ideal I know but the firewall on the NAS only allows SMB traffic.
Also the Macs backup to the nas and Timecapsule.
The non LAG on the router is due to all the ports on switch-1 being used, nearly all the traffic doesn’t go cross VLAN anyhow.
-
Time for a switch upgrade then ;) seems..
If your not doing any sort of real intervlan traffic not big issues no.. Just seems like the 4860 with all its interfaces a bit oversized..
-
When the Timecapsule dies I’ll LAG the router :)