Cannot SSH into another Subnet
-
Hello guys,
before I start, I have to tell that I'm not sure if this is a firewall issue, so if its not an admin can feel free to move this into the proper category.
I'm very new to pfSense and I have some very basic networking knowledge.
I bought a server, installed Proxmox and virtualized pfSense.Now I want to create an enterprise ready network topology:
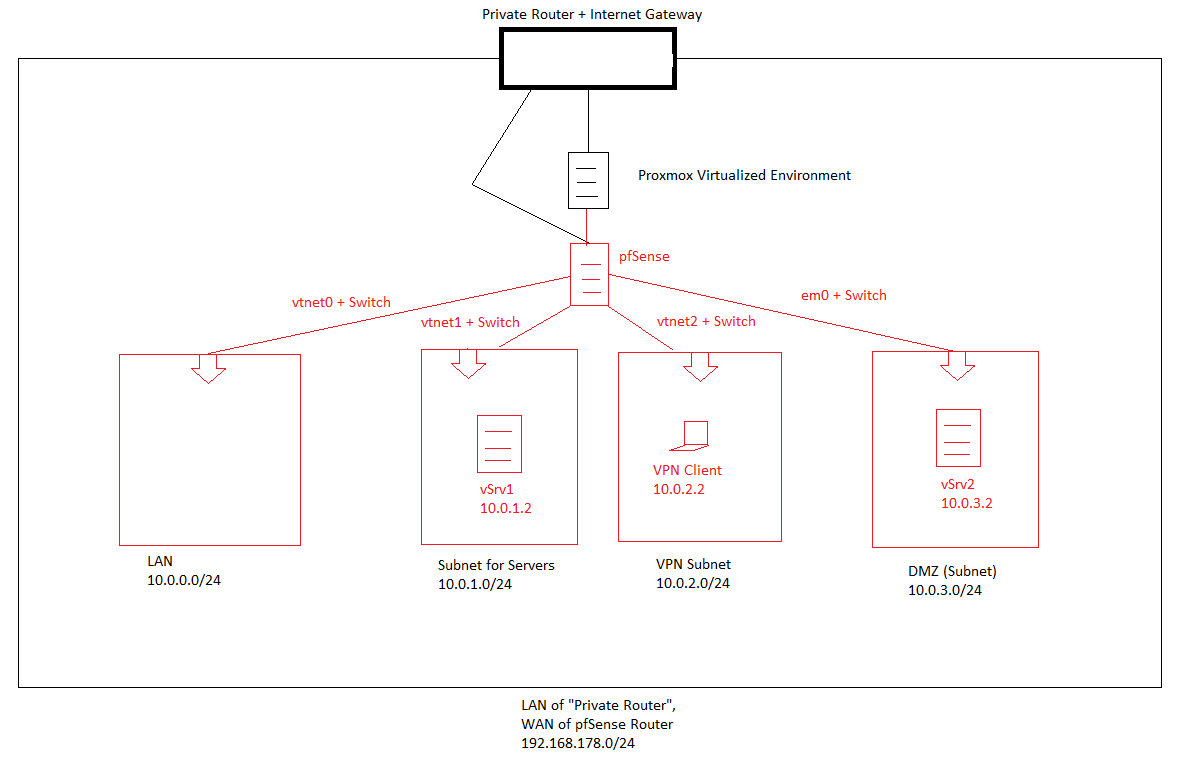
(everything in red is virtualized on the Proxmox machine)So I gave my pfSense-machine 5 NICs (WAN, LAN, SRV subnet for Servers, VPN subnet for VPN-connections and DMZ subnet). I managed to create those subnets according to the topology scetch.
- internet works from any of those subnets
- I can ping machine inside the subnet as well as the gateway
- OpenVPN works properly
But here comes the issue (by exmaple):
When connecting via VPN (I'm getting 10.0.2.2 from DHCP) I am able to ping the server in my server-subnet (running on 10.0.1.2) but i cannot SSH into it.The error I'm getting is a timeout but there is nothing in the log.
Testresults:
-
I can SSH into the machine in DMZ
-
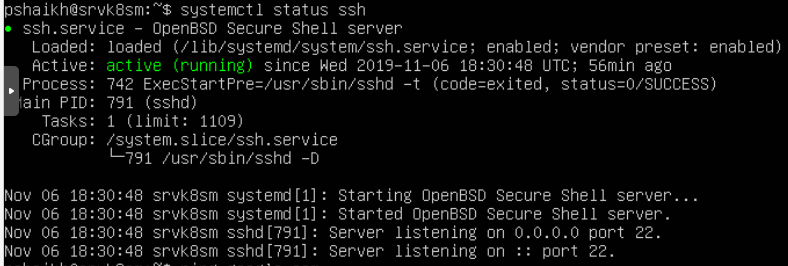
SSH is running on the machine I'm trying to connect to on port 22
-
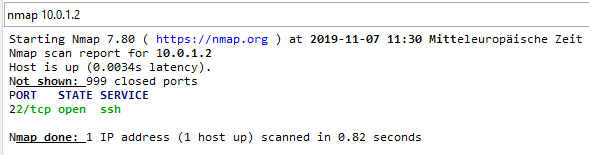
nmap shows the port is open
-
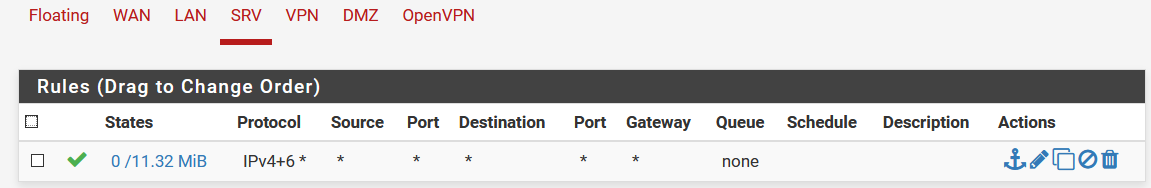
there is only one single firewall rule which basically passes everything through (temporarily)
-
tcpdump on 10.0.1.2
-
according to https://superuser.com/questions/543626/ssh-permission-denied-on-correct-password-authentication I should be able to SSH now, in fact when the machine is in the same subnet I am able to SSH
So after spending days (!) of trying to get it to work I'm out of ideas so maybe one of you can help me?
Thanks in advance.
EDIT 1:
Thanks to johnpoz, I found out that setting up a custom subnet with its own NIC for VPN is interferring with OpenVPN's self created subnet.
I deleted the custom subnet and its NIC.Paket capture for 10.0.1.0/24:
13:19:07.570885 ee:12:a6:6d:cd:94 > 66:17:6a:c5:85:0e, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 127, id 8191, offset 0, flags [DF], proto TCP (6), length 52) 10.0.2.2.2611 > 10.0.1.2.22: Flags [S], cksum 0xa8ce (correct), seq 4136874966, win 64240, options [mss 1358,nop,wscale 8,nop,nop,sackOK], length 0 13:19:07.571147 66:17:6a:c5:85:0e > ee:12:a6:6d:cd:94, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2611: Flags [S.], cksum 0x172a (incorrect -> 0xe948), seq 1234239071, ack 4136874967, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:19:08.592665 66:17:6a:c5:85:0e > ee:12:a6:6d:cd:94, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2611: Flags [S.], cksum 0x172a (incorrect -> 0xe948), seq 1234239071, ack 4136874967, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:19:10.572196 ee:12:a6:6d:cd:94 > 66:17:6a:c5:85:0e, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 127, id 8192, offset 0, flags [DF], proto TCP (6), length 52) 10.0.2.2.2611 > 10.0.1.2.22: Flags [S], cksum 0xa8ce (correct), seq 4136874966, win 64240, options [mss 1358,nop,wscale 8,nop,nop,sackOK], length 0 13:19:10.572481 66:17:6a:c5:85:0e > ee:12:a6:6d:cd:94, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2611: Flags [S.], cksum 0x172a (incorrect -> 0xe948), seq 1234239071, ack 4136874967, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:19:12.593426 66:17:6a:c5:85:0e > ee:12:a6:6d:cd:94, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2611: Flags [S.], cksum 0x172a (incorrect -> 0xe948), seq 1234239071, ack 4136874967, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:19:16.574240 ee:12:a6:6d:cd:94 > 66:17:6a:c5:85:0e, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 127, id 8193, offset 0, flags [DF], proto TCP (6), length 52) 10.0.2.2.2611 > 10.0.1.2.22: Flags [S], cksum 0xa8ce (correct), seq 4136874966, win 64240, options [mss 1358,nop,wscale 8,nop,nop,sackOK], length 0 13:19:16.574495 66:17:6a:c5:85:0e > ee:12:a6:6d:cd:94, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2611: Flags [S.], cksum 0x172a (incorrect -> 0xe948), seq 1234239071, ack 4136874967, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:19:20.754914 66:17:6a:c5:85:0e > ee:12:a6:6d:cd:94, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2611: Flags [S.], cksum 0x172a (incorrect -> 0xe948), seq 1234239071, ack 4136874967, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:19:28.948385 66:17:6a:c5:85:0e > ee:12:a6:6d:cd:94, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2611: Flags [S.], cksum 0x172a (incorrect -> 0xe948), seq 1234239071, ack 4136874967, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0and for 10.0.2.0/24:
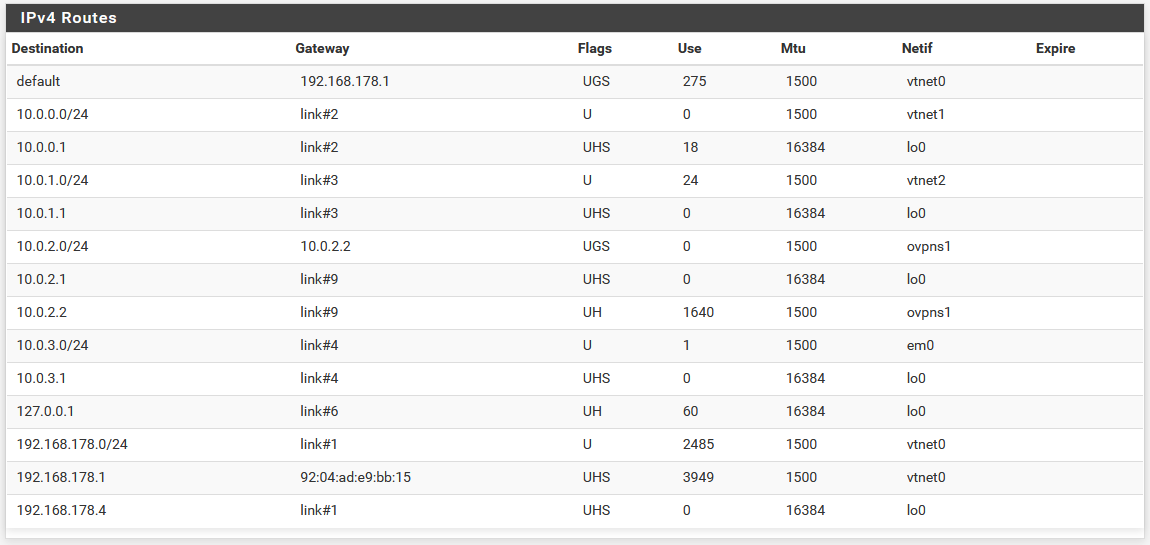
13:20:52.900921 AF IPv4 (2), length 56: (tos 0x0, ttl 128, id 8194, offset 0, flags [DF], proto TCP (6), length 52) 10.0.2.2.2616 > 10.0.1.2.22: Flags [S], cksum 0x94da (correct), seq 151434579, win 64240, options [mss 1358,nop,wscale 8,nop,nop,sackOK], length 0 13:20:52.901130 AF IPv4 (2), length 56: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2616: Flags [S.], cksum 0x172a (incorrect -> 0x0c54), seq 2048038622, ack 151434580, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:20:53.921345 AF IPv4 (2), length 56: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2616: Flags [S.], cksum 0x172a (incorrect -> 0x0c54), seq 2048038622, ack 151434580, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:20:55.901897 AF IPv4 (2), length 56: (tos 0x0, ttl 128, id 8195, offset 0, flags [DF], proto TCP (6), length 52) 10.0.2.2.2616 > 10.0.1.2.22: Flags [S], cksum 0x94da (correct), seq 151434579, win 64240, options [mss 1358,nop,wscale 8,nop,nop,sackOK], length 0 13:20:55.902123 AF IPv4 (2), length 56: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2616: Flags [S.], cksum 0x172a (incorrect -> 0x0c54), seq 2048038622, ack 151434580, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:20:57.921835 AF IPv4 (2), length 56: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2616: Flags [S.], cksum 0x172a (incorrect -> 0x0c54), seq 2048038622, ack 151434580, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:21:01.904146 AF IPv4 (2), length 56: (tos 0x0, ttl 128, id 8196, offset 0, flags [DF], proto TCP (6), length 52) 10.0.2.2.2616 > 10.0.1.2.22: Flags [S], cksum 0x94da (correct), seq 151434579, win 64240, options [mss 1358,nop,wscale 8,nop,nop,sackOK], length 0 13:21:01.904390 AF IPv4 (2), length 56: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2616: Flags [S.], cksum 0x172a (incorrect -> 0x0c54), seq 2048038622, ack 151434580, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:21:05.987112 AF IPv4 (2), length 56: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2616: Flags [S.], cksum 0x172a (incorrect -> 0x0c54), seq 2048038622, ack 151434580, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0 13:21:14.180356 AF IPv4 (2), length 56: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 52) 10.0.1.2.22 > 10.0.2.2.2616: Flags [S.], cksum 0x172a (incorrect -> 0x0c54), seq 2048038622, ack 151434580, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0My entries under Diagnostics - Routes are:
-
uhm MTU or try to disable compression
did you check with tcpdump ? -
@kiokoman
MTU is at 1500 (default)
Disabling compression results in not beeing able to even ping the gateway, so I enabled it again.
tcpdump result is in the post. -
You can just sniff on pfsense with the diag menu, packet capture.. Validate when you send your connection from ssh that the other end is actually getting it, and answering.
Can you ping the device in the other vlan? From the device in your source vlan?
So all your vlans have those same firewall rules? And you have no rules in floating?
-
@johnpoz
There are no VLANs included, just subnets.
Yes i can ping as pointed out.
No only the server-subnet has the rules.Packet capture result:
12:10:43.732248 IP 10.0.2.2.2134 > 10.0.1.2.22: tcp 0
12:10:43.732444 IP 10.0.1.2.22 > 10.0.2.2.2134: tcp 0
12:10:44.738626 IP 10.0.1.2.22 > 10.0.2.2.2134: tcp 0
12:10:45.410660 ARP, Request who-has 10.0.1.1 tell 10.0.1.2, length 28
12:10:45.410671 ARP, Reply 10.0.1.1 is-at ee:12:a6:6d:cd:94, length 28
12:10:46.733465 IP 10.0.2.2.2134 > 10.0.1.2.22: tcp 0
12:10:46.733749 IP 10.0.1.2.22 > 10.0.2.2.2134: tcp 0
12:10:48.739200 IP 10.0.1.2.22 > 10.0.2.2.2134: tcp 0
12:10:52.734762 IP 10.0.2.2.2134 > 10.0.1.2.22: tcp 0
12:10:52.735027 IP 10.0.1.2.22 > 10.0.2.2.2134: tcp 0 -
what is all the noise to the 6443 port, that is not answering?
But you can see that your ssh got an answer.. Maybe it was a RST? Open up the capture in wireshark or something or turn up the verbosity of your capture.
12:10:46.733465 IP 10.0.2.2.2134 > 10.0.1.2.22: tcp 0 12:10:46.733749 IP 10.0.1.2.22 > 10.0.2.2.2134: tcp 0Also the term vlan is interchangeable with network segment.. Be it tagged or not, the term vlan is common to use to talk about a different network.