Dedicated VLAN+VAP for Openvpn client - no net for main network
-
My goal is to have a dedicated Virtual AP (named vpn bbc, in my case) for my openvpn client connection to vpnunlimited UK server.
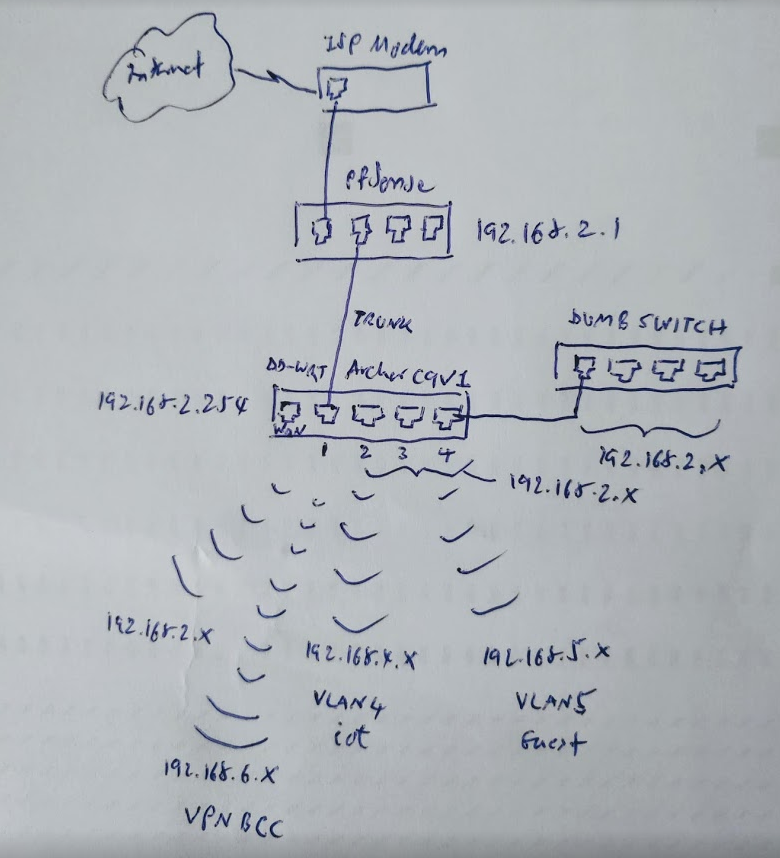
From the attached diagram, my pfSense connects to my dd-wrt AP with main network subnet 192.168.2.x. There are a number of VLANs and VAPs for my iot and guest devices. My main network can access the iot and guest devices, but not the other way. These are all working fine. DHCP/DNS/firewall rules for all of them are managed by pfSense.
I've created another VLAN (6) and VAP to support the VPN clients (I want to see BBC iplayer program). The VLAN/VAP itself without OpenVPN client is working fine as usual. But when I create the OpenVPN client by following the guide from vpnunlimited here:
https://www.vpnunlimitedapp.com/en/info/manuals/pfsense-configuration-guide
I have the following situation, when I connect my pfSense to Openvpn client:- the openvpn client connected successfully
- when I connected to my VAP which dedicated to the vpn (vpn_bcc), I have internet connection, and whatismyip reports my location as UK site. I can play BBC iPlayer video without problem
- but when I switch my connection to my main network (192.168.2.x, 192.168.4.x, 192.168.5.x), there is no internet
So in summary, whenever pfSense connects to openvpn client, no internet connection on all networks, except the VAP (vpn bbc) which I intend to. Any suggestion I have done something wrong or not enough?
If you would like to see more of my setup on PfSense, please let me know.
fyi, I also have openvpn server running (allow to securely connect to my local network from outside). I don't think it is relevant, though.Thanks.
Here is my setup on pfSense:
Interface:
No rule for the Openvpn client
Rules for the VLAN6 which dedicated to vpn_bbc
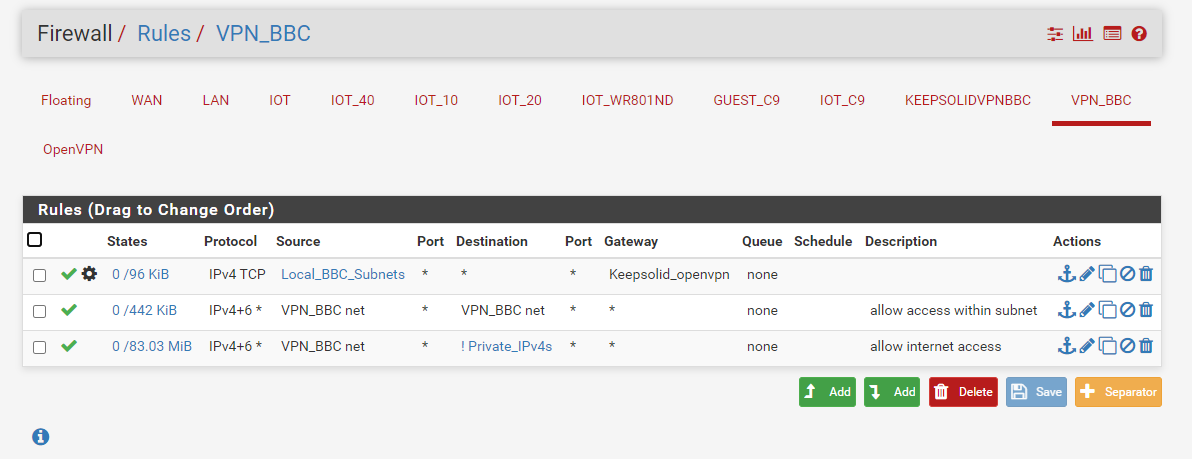
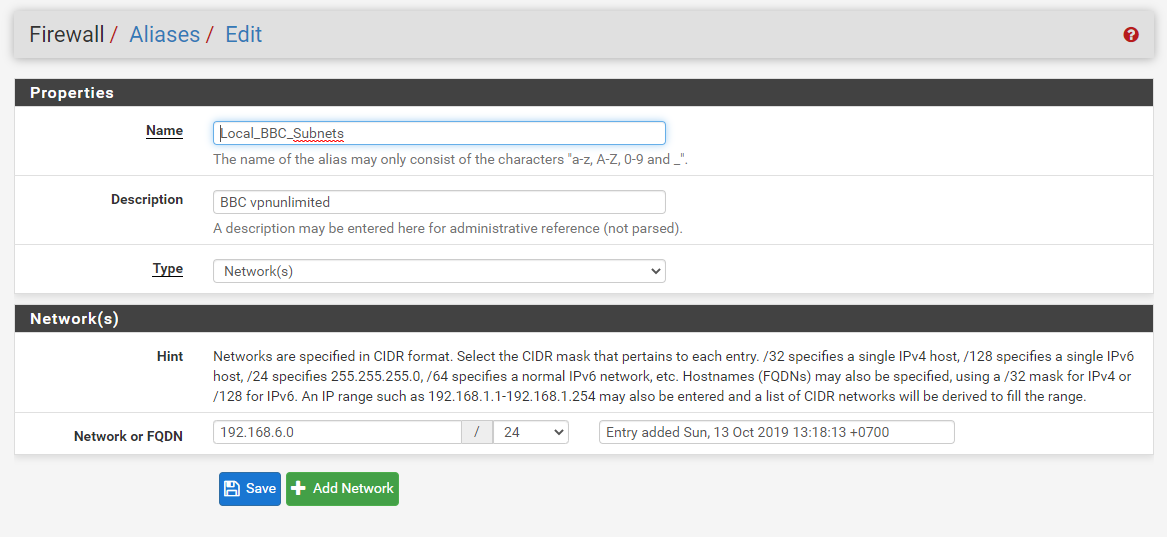
Alia
outbound NAT part 1
outbound NAT part 2
VPN client setting:
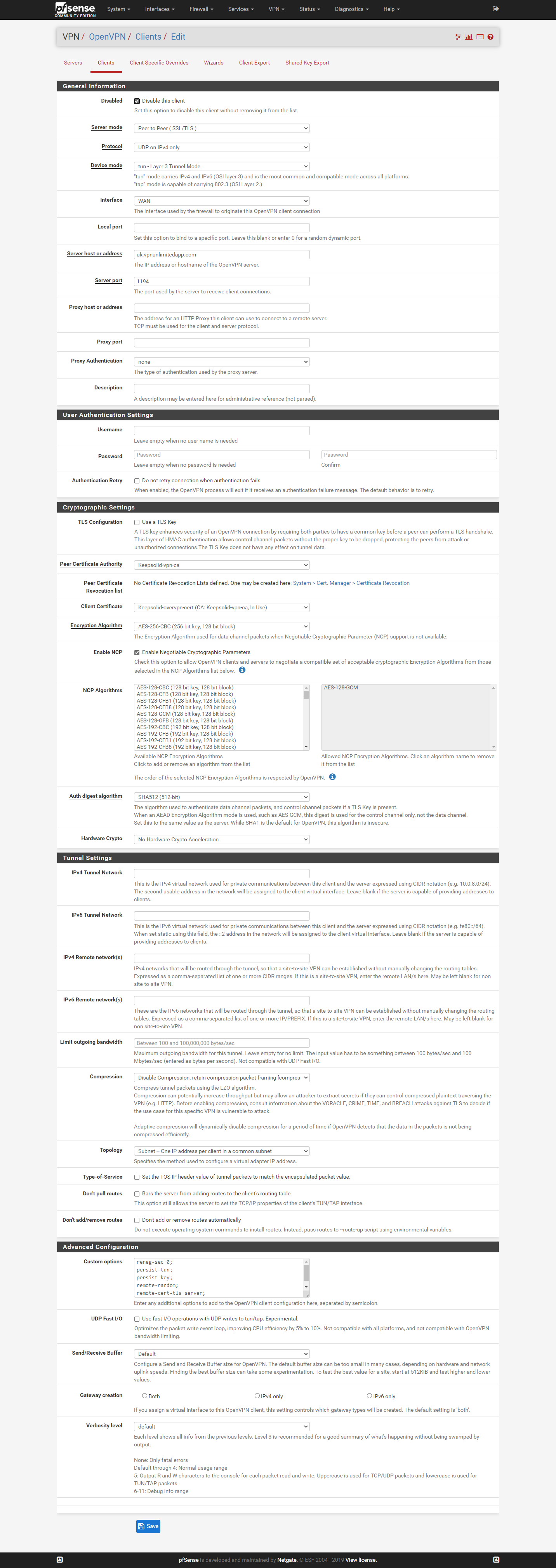
Interface assignment:
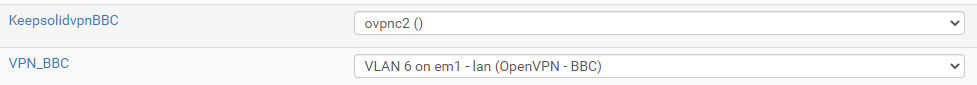
-
additional LAN rule
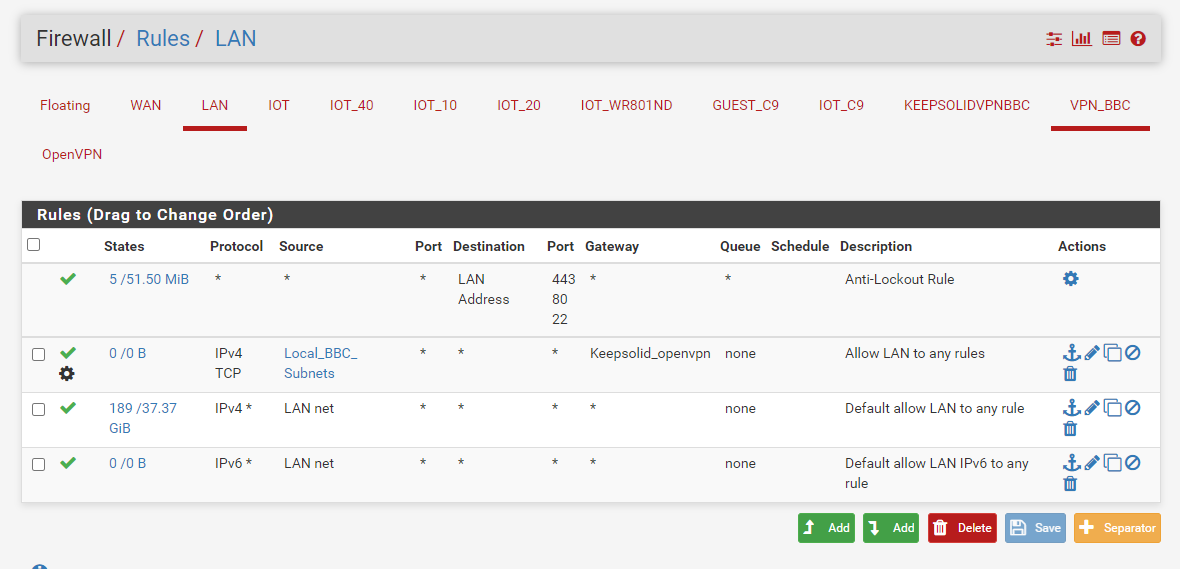
-
Update:
Thanks to this guide: https://blog.monstermuffin.org/tunneling-specific-traffic-over-a-vpn-with-pfsense/
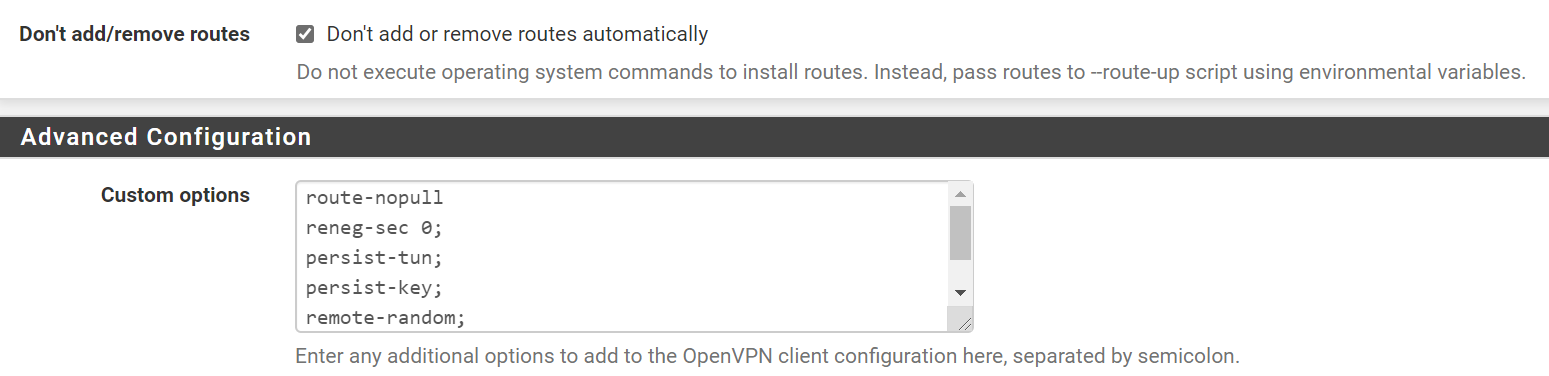
I need to do two more things on the vpn client settings:- check the "Don't add/remove routes"
- add "route-nopull" in the Custom options
Now it works as it should be, i.e., my virtual AP VPN_BBC has 7/24 vpn whilst my other subnets have normal internet traffic.