OpenVPN established but no traffic routed
-
Hi everyone.
I'm relatively new to pfSense, just installed a box to replace my home router 2 weeks ago, but, I got a background of IT/Net (CCNA, Linux/FreeBSD admin long time ago). So far, I'm everyday more in love with pfSense, the power and level of flexibility is amazing, the latter is also my main concern as it could be challenging to achieve something that could be easier (but not optimal or secure) with out-pf-the-shelf routers. Anyway, I'm really engaged and motivated to keep working on it and I'm now sure that there's no way back to consumer routers for me!
So, for this case, I need to connect to a remote location where an OpenVPN server (pre-shared key) is configured. I can't access remote site (to review or change config there) but I'm sure config there works, maybe not the optimal one but works as my previous home router (another ASUS one) is still able to connect to the remote site and VPN works as expected with it.
I've managed to configure the OpenVPN client on my pfSense box and connection is established (Status, OpenVPN shows it's UP). I can ping the remote router LAN interface and even remote hosts LANs from the router BUT only using as the source the address assigned to the VPN interface. If I use the as a source the address used by the LAN interface, packets are not routed. Therefore, I can't access remote LAN from my local LAN.
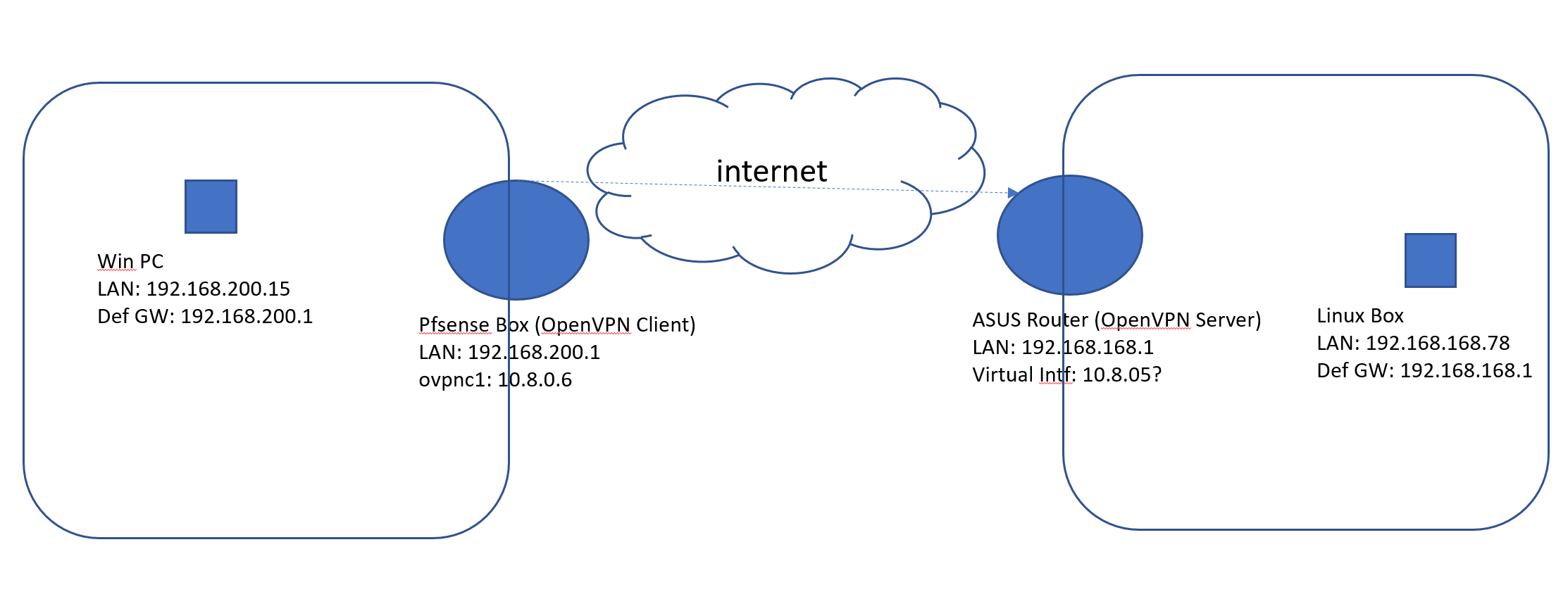
I've attached a quick network map:
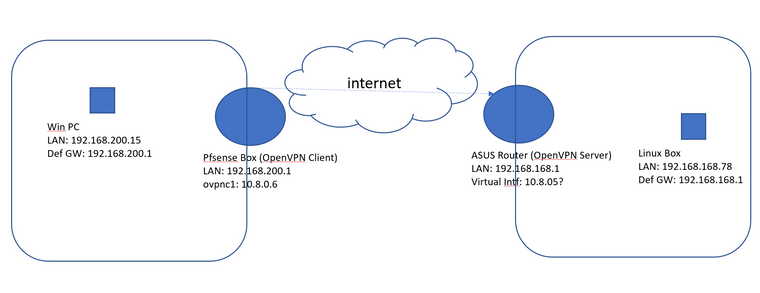
I can see on OpenVPN logs that routes are being created and in fact those are in place on my pfsense box:
[2.4.4-RELEASE][admin@mtrpfSense.localdomain]/root: netstat -nr Routing tables Internet: Destination Gateway Flags Netif Expire default 10.32.0.49 UGS pppoe1 10.8.0.1/32 10.8.0.5 UGS ovpnc1 10.8.0.5 link#9 UH ovpnc1 10.8.0.6 link#9 UHS lo0 10.32.0.49 link#8 UH pppoe1 127.0.0.1 link#4 UH lo0 190.XXXXXXXXXXX link#8 UHS lo0 192.168.168.0/24 10.8.0.5 UGS ovpnc1 192.168.200.0/24 link#2 U em1 192.168.200.1 link#2 UHS lo0I'm open to change /to improve) VPN parameters on the remote side, but I can't access remote site router in the following weeks, so I need to restore VPN operation that I used to have with the old basic router in order to resume backup syncs and then, I would be able to access remote router (via the VPN) and improve config.
I'm almost sure that I'm missing some simple of stupid thing here, as the PVN is already established and firewall can ping remote hosts. But I'm not able to see it now...}Any support will be highly appreciated.
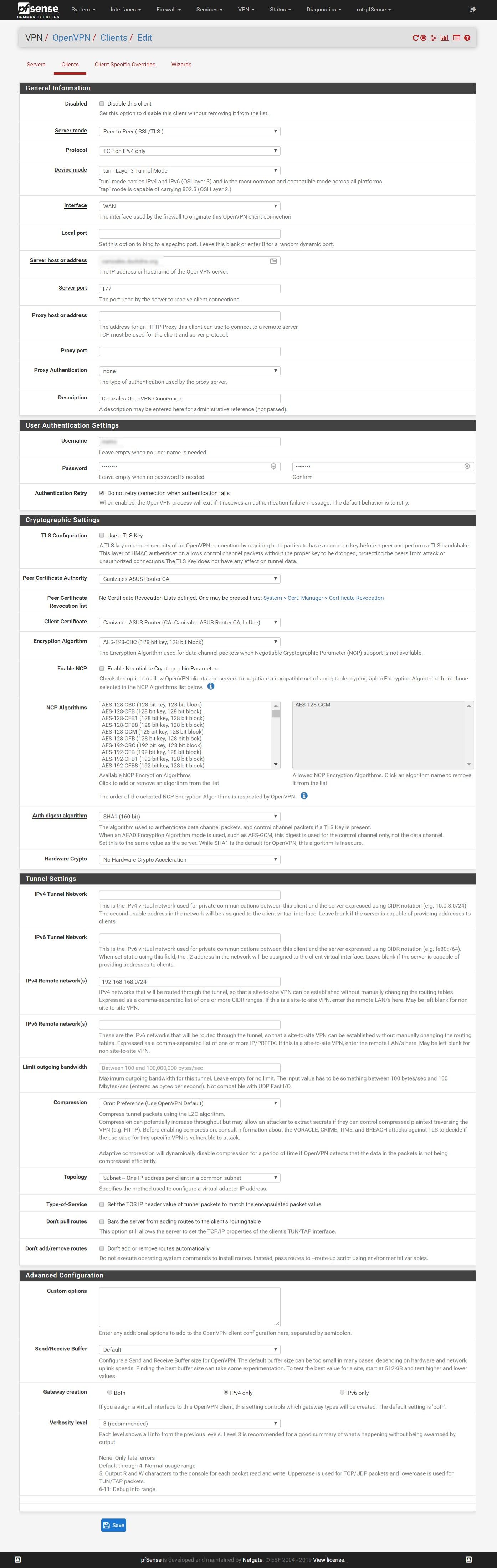
Attached OpenVPN client configuration. Please let me know if further details are needed to understand the issue.
Thanks a lot in advance!
-
Not sure if this will solve your problem, but looks like you are missing the "IPv4 Tunnel Network" setting under the Cryptographic Settings. See: https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/configuring-a-site-to-site-static-key-openvpn-instance.html
Also, most of the documentation I've seen seems to recommend UDP versus TCP due to retransmission of lost packets.
Hope this helps.
-
Hi there!
Thank you for your reply!@yumcheese said in OpenVPN established but no traffic routed:
Not sure if this will solve your problem, but looks like you are missing the "IPv4 Tunnel Network" setting under the Cryptographic Settings. See: https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/configuring-a-site-to-site-static-key-openvpn-instance.html
I'll review and try as soon as I get home, tks.
Also, most of the documentation I've seen seems to recommend UDP versus TCP due to retransmission of lost packets.
Yeah, I read about it on the NetGate guide and OpenVPN guides, and as soon as I can access the remote end, I'll try to create a new connection following the best practices.
Tks!
-
I've reviewed the guide and tried to add a "10.0.8.0/24" or a "10.0.8.0/30" as a "IPv4 Tunnel Network" Setting. It didn't work. Anyway, I understood this config was not mandatory if the system can agree an unused net for the interfaces.
The main point (for me anyway), is that the tunnel is indeed established and that traffic is going thru the tunnel without issues, but only from the Firewall (using the VPN interface):
[2.4.4-RELEASE][admin@mtrpfSense.localdomain]/root: ping 192.168.168.1 PING 192.168.168.1 (192.168.168.1): 56 data bytes 64 bytes from 192.168.168.1: icmp_seq=0 ttl=64 time=55.564 ms 64 bytes from 192.168.168.1: icmp_seq=1 ttl=64 time=25.067 ms 64 bytes from 192.168.168.1: icmp_seq=2 ttl=64 time=23.550 ms 64 bytes from 192.168.168.1: icmp_seq=3 ttl=64 time=29.059 ms 64 bytes from 192.168.168.1: icmp_seq=4 ttl=64 time=24.548 ms ^C --- 192.168.168.1 ping statistics --- 5 packets transmitted, 5 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 23.550/31.558/55.564/12.149 ms [2.4.4-RELEASE][admin@mtrpfSense.localdomain]/root: ping 192.168.168.78 PING 192.168.168.78 (192.168.168.78): 56 data bytes 64 bytes from 192.168.168.78: icmp_seq=0 ttl=63 time=21.725 ms 64 bytes from 192.168.168.78: icmp_seq=1 ttl=63 time=31.239 ms 64 bytes from 192.168.168.78: icmp_seq=2 ttl=63 time=30.095 ms 64 bytes from 192.168.168.78: icmp_seq=3 ttl=63 time=24.584 ms ^C --- 192.168.168.78 ping statistics --- 4 packets transmitted, 4 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 21.725/26.911/31.239/3.911 ms [2.4.4-RELEASE][admin@mtrpfSense.localdomain]/root: ping -S 10.8.0.6 192.168.168.1 PING 192.168.168.1 (192.168.168.1) from 10.8.0.6: 56 data bytes 64 bytes from 192.168.168.1: icmp_seq=0 ttl=64 time=29.731 ms 64 bytes from 192.168.168.1: icmp_seq=1 ttl=64 time=25.551 ms 64 bytes from 192.168.168.1: icmp_seq=2 ttl=64 time=22.431 ms ^C --- 192.168.168.1 ping statistics --- 3 packets transmitted, 3 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 22.431/25.904/29.731/2.991 ms [2.4.4-RELEASE][admin@mtrpfSense.localdomain]/root: ping -S 10.8.0.6 192.168.168.78 PING 192.168.168.78 (192.168.168.78) from 10.8.0.6: 56 data bytes 64 bytes from 192.168.168.78: icmp_seq=0 ttl=63 time=25.620 ms 64 bytes from 192.168.168.78: icmp_seq=1 ttl=63 time=25.499 ms 64 bytes from 192.168.168.78: icmp_seq=2 ttl=63 time=24.130 ms 64 bytes from 192.168.168.78: icmp_seq=3 ttl=63 time=25.924 ms ^C --- 192.168.168.78 ping statistics --- 4 packets transmitted, 4 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 24.130/25.293/25.924/0.689 ms [2.4.4-RELEASE][admin@mtrpfSense.localdomain]/root: ping -S 192.168.200.1 192.168.168.1 PING 192.168.168.1 (192.168.168.1) from 192.168.200.1: 56 data bytes ^C --- 192.168.168.1 ping statistics --- 11 packets transmitted, 0 packets received, 100.0% packet lossI can't access remote router nor remote hosts now, but so I can't review if there is a route to my local LAN that is missing on the remote firewall. I'm sure remote hosts have remote router as default gateway.
So, I'm still thinking that maybe it's some routing configuration in the pfsense box? A config that (IMHO) should be applied automatically anyway as I didn't found any reference to this on the guides I've following.
Any ideas?
Thanks!
-
Just an additional comment to highlight my point that there must be "something" on the pfsense box (client) configuration that I should missed: I've configured the same OpenVPN connection on a Synology NAS. It worked on the first try (as it was working on the old router) and at least the backups can be resumed now.
The OpenVPN config file was imported from Synology DSM, I've fill user and passwd and that's it. I'm aware pfsense is a lot more powerfull and flexible but in case like this one I would like to have a "Basic" view of the configurations options so any default one can be assumed and VPN could be established like on the other two (consumer) devices.
OpenVPN config file shows that the amount of parameters expected by remote router are really few:
remote XXXXXXXXXXX.com 177 float nobind proto tcp-client dev tun sndbuf 0 rcvbuf 0 keepalive 15 60 auth-user-pass client auth SHA1 cipher AES-128-CBC ns-cert-type server <ca> -----BEGIN CERTIFICATE----- XXXXXXXXXXX.... -----END CERTIFICATE----- </ca> <cert> -----BEGIN CERTIFICATE----- XXXXXXXXXXX.... -----END CERTIFICATE----- </cert> <key> -----BEGIN PRIVATE KEY----- XXXXXXXXXXX.... -----END PRIVATE KEY----- </key>Any idea of can I replicate this on the pfsense box as a OpenVPN client?
Thanks!
-
@metro said in OpenVPN established but no traffic routed:
I've reviewed the guide and tried to add a "10.0.8.0/24" or a "10.0.8.0/30" as a "IPv4 Tunnel Network" Setting. It didn't work.
According to your diagram, it is the 10.8.0.0 network. Maybe you have a typo somewhere? I'm not sure if it is required or not. I've just seen sample configs use it. The proper route does seem to show up from your netstat -nr.
-
Might be a bit late and you probably already fixed it but try and take a peek at firewall -> rules -> openvpn.
You do have a rule to actually allow openvpn traffic through the firewall right?