PFSense single interface (WAN) OpenVPN TAP Bridge to internal DHCP server not getting IP
-
Hi All,
I need some help from you smart peeps.
My current test is to do the following:
Have a device with OpenVPN client connect to a pfsense server with 1 interface only (WAN) and get DHCP from the internal server.
Thus far I get everything to connect ( OpenVPN ). but I still cant get a DHCP address and still get stuck with a default 169 IP and no gateway on the client.
What can I post here for your assistance?
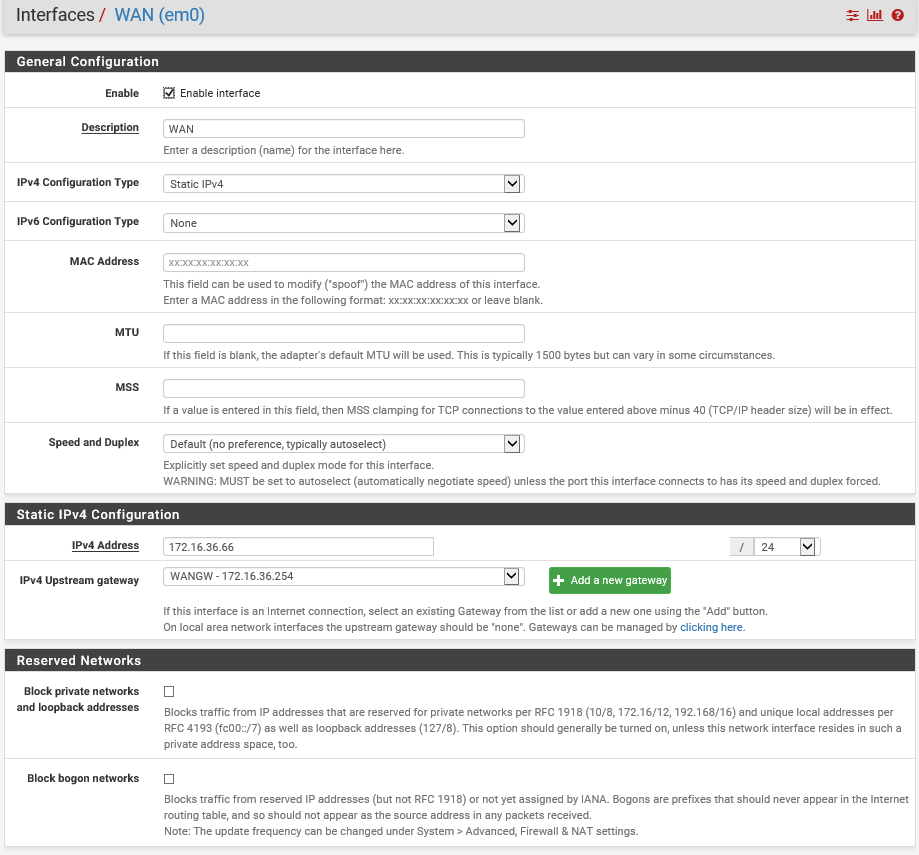
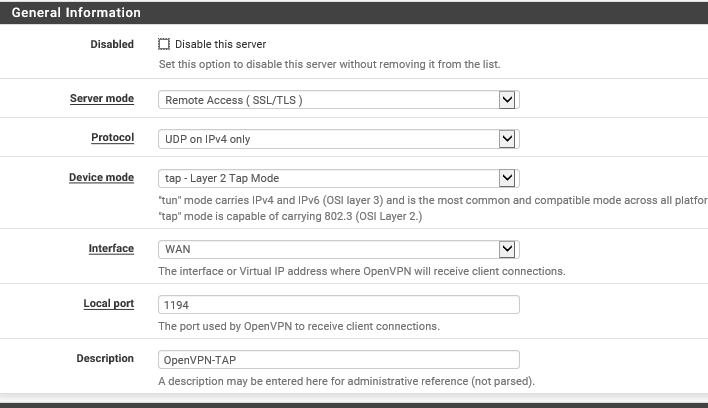
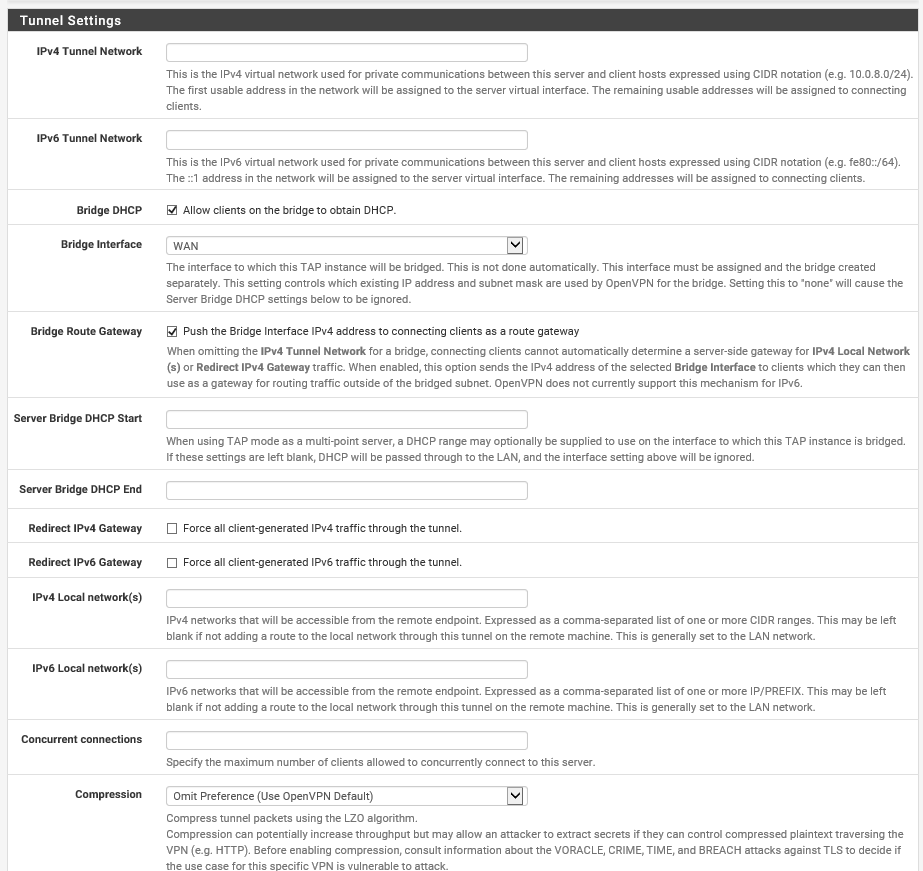
/var/etc/openvpn/server1.conf
dev ovpns1
verb 3
dev-type tap
dev-node /dev/tap1
writepid /var/run/openvpn_server1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp4
cipher AES-256-CBC
auth SHA256
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
local 172.16.36.66
tls-server
mode server
push "route-gateway 172.16.36.66"
tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'ServCert' 1"
lport 1194
management /var/etc/openvpn/server1.sock unix
push "dhcp-option DOMAIN xxxxxxxxxx.co.za"
push "dhcp-option DNS 10.0.3.2"
client-to-client
duplicate-cn
ca /var/etc/openvpn/server1.ca
cert /var/etc/openvpn/server1.cert
key /var/etc/openvpn/server1.key
dh /etc/dh-parameters.2048
tls-auth /var/etc/openvpn/server1.tls-auth 0
ncp-disable
persist-remote-ip
floatClient Config File:
#-- Config Auto Generated By pfSense for Viscosity --#
#viscosity startonopen false
#viscosity dhcp true
#viscosity dnssupport true
#viscosity name OpenVPN-TAPdev tap
persist-tun
persist-key
cipher AES-256-CBC
auth SHA256
tls-client
client
resolv-retry infinite
remote xxx.xxx.xxx.xxx 1194 udp
lport 0
verify-x509-name "ServCert" name
remote-cert-tls serverca ca.crt
tls-auth ta.key 1
cert cert.crt
key key.keyverb 3
log openvpn.log
log-append openvpn.logWed Nov 20 10:58:07 2019 OpenVPN 2.3.6 i686-w64-mingw32 [SSL (OpenSSL)] [LZO] [PKCS11] [IPv6] built on Dec 1 2014
Wed Nov 20 10:58:07 2019 library versions: OpenSSL 1.0.1j 15 Oct 2014, LZO 2.08
Wed Nov 20 10:58:07 2019 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Wed Nov 20 10:58:07 2019 Need hold release from management interface, waiting...
Wed Nov 20 10:58:08 2019 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
Wed Nov 20 10:58:08 2019 MANAGEMENT: CMD 'state on'
Wed Nov 20 10:58:08 2019 MANAGEMENT: CMD 'log all on'
Wed Nov 20 10:58:08 2019 MANAGEMENT: CMD 'hold off'
Wed Nov 20 10:58:08 2019 MANAGEMENT: CMD 'hold release'
Wed Nov 20 10:58:08 2019 Control Channel Authentication: using 'ta.key' as a OpenVPN static key file
Wed Nov 20 10:58:08 2019 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Wed Nov 20 10:58:08 2019 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication
Wed Nov 20 10:58:08 2019 Socket Buffers: R=[65536->65536] S=[65536->65536]
Wed Nov 20 10:58:08 2019 UDPv4 link local (bound): [undef]
Wed Nov 20 10:58:08 2019 UDPv4 link remote: [AF_INET]172.16.36.66:1194
Wed Nov 20 10:58:08 2019 MANAGEMENT: >STATE:1574240288,WAIT,,,
Wed Nov 20 10:58:08 2019 MANAGEMENT: >STATE:1574240288,AUTH,,,
Wed Nov 20 10:58:08 2019 TLS: Initial packet from [AF_INET]172.16.36.66:1194, sid=b14a1c9f 99833975
Wed Nov 20 10:58:08 2019 VERIFY OK: depth=1, CN=ServCA, C=ZA, ST=WC, L=Cape Town, O=MyOrg
Wed Nov 20 10:58:08 2019 Validating certificate key usage
Wed Nov 20 10:58:08 2019 ++ Certificate has key usage 00a0, expects 00a0
Wed Nov 20 10:58:08 2019 VERIFY KU OK
Wed Nov 20 10:58:08 2019 Validating certificate extended key usage
Wed Nov 20 10:58:08 2019 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Wed Nov 20 10:58:08 2019 VERIFY EKU OK
Wed Nov 20 10:58:08 2019 VERIFY X509NAME OK: CN=ServCert, C=ZA, ST=WC, L=Cape Town, O=MyOrg
Wed Nov 20 10:58:08 2019 VERIFY OK: depth=0, CN=ServCert, C=ZA, ST=WC, L=Cape Town, O=MyOrg
Wed Nov 20 10:58:08 2019 Data Channel Encrypt: Cipher 'AES-256-CBC' initialized with 256 bit key
Wed Nov 20 10:58:08 2019 Data Channel Encrypt: Using 256 bit message hash 'SHA256' for HMAC authentication
Wed Nov 20 10:58:08 2019 Data Channel Decrypt: Cipher 'AES-256-CBC' initialized with 256 bit key
Wed Nov 20 10:58:08 2019 Data Channel Decrypt: Using 256 bit message hash 'SHA256' for HMAC authentication
Wed Nov 20 10:58:08 2019 Control Channel: TLSv1, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-SHA, 2048 bit RSA
Wed Nov 20 10:58:08 2019 [ServCert] Peer Connection Initiated with [AF_INET]172.16.36.66:1194
Wed Nov 20 10:58:09 2019 MANAGEMENT: >STATE:1574240289,GET_CONFIG,,,
Wed Nov 20 10:58:10 2019 SENT CONTROL [ServCert]: 'PUSH_REQUEST' (status=1)
Wed Nov 20 10:58:10 2019 PUSH: Received control message: 'PUSH_REPLY,route-gateway 172.16.36.66,dhcp-option DOMAIN xxxxxxxxx.co.za,dhcp-option DNS 10.0.3.2,ping 10,ping-restart 60,peer-id 0'
Wed Nov 20 10:58:10 2019 OPTIONS IMPORT: timers and/or timeouts modified
Wed Nov 20 10:58:10 2019 OPTIONS IMPORT: route-related options modified
Wed Nov 20 10:58:10 2019 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Wed Nov 20 10:58:10 2019 OPTIONS IMPORT: peer-id set
Wed Nov 20 10:58:10 2019 open_tun, tt->ipv6=0
Wed Nov 20 10:58:10 2019 TAP-WIN32 device [Ethernet 6] opened: \.\Global{75484DF4-3D11-4FE5-B0FC-F25C7B8EB0DF}.tap
Wed Nov 20 10:58:10 2019 TAP-Windows Driver Version 9.9
Wed Nov 20 10:58:10 2019 Successful ARP Flush on interface [24] {75484DF4-3D11-4FE5-B0FC-F25C7B8EB0DF}
Wed Nov 20 10:58:15 2019 TEST ROUTES: 0/0 succeeded len=0 ret=1 a=0 u/d=up
Wed Nov 20 10:58:15 2019 Initialization Sequence Completed
Wed Nov 20 10:58:15 2019 MANAGEMENT: >STATE:1574240295,CONNECTED,SUCCESS,,172.16.36.66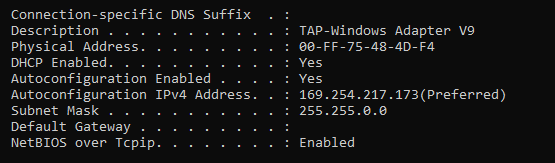
-
What is actually happening? For example, if you run Packet Capture, do you see DHCP traffic from the remote device? To it? That would give some clues as to where the problem is.
-
I can see on wireshark my pc tries to get a DHCP address.
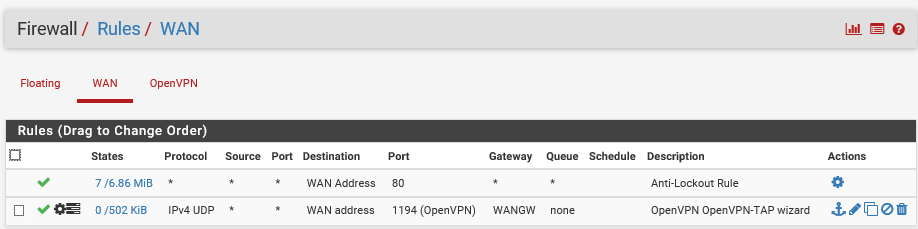
But I think it is my bridge that is the problem and possibly my firewall rules.
bare in mind I only have 1 interface.
All I want is fo the OpenVPN to connect and the pc is on the network.
-
Also run Packet Capture on pfSense, to determine if it's getting that far. It's hard to solve a problem when we don't know the details.