PFSense reporting asynchronous routing and blocking
-
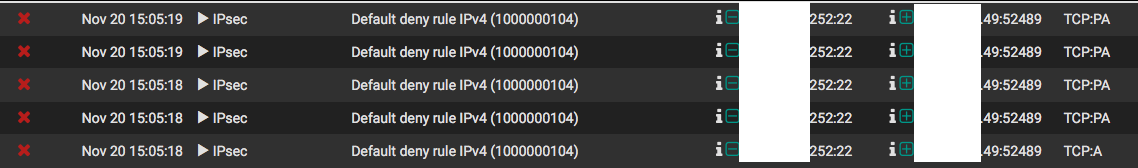
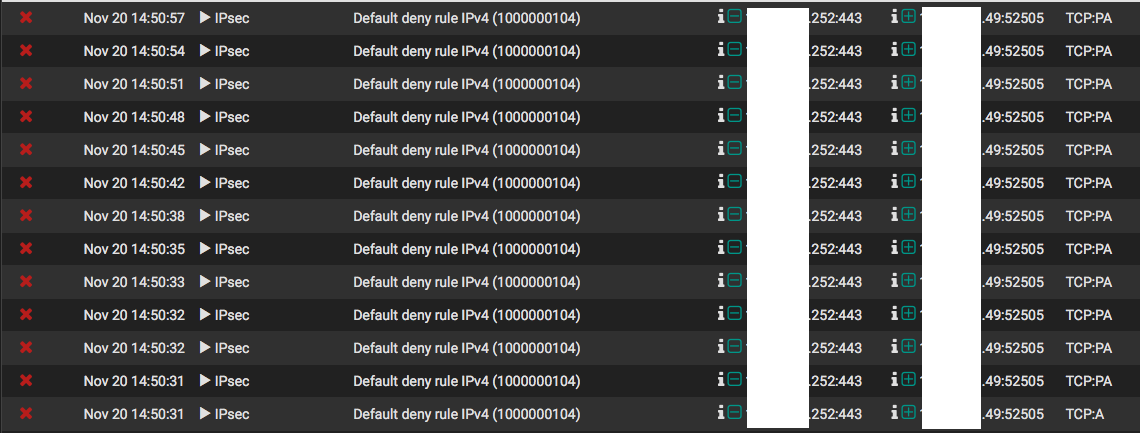
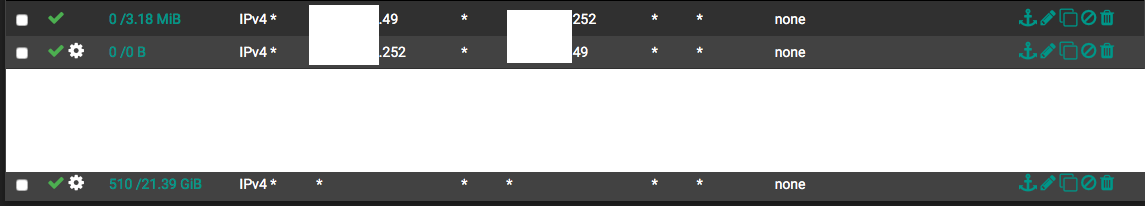
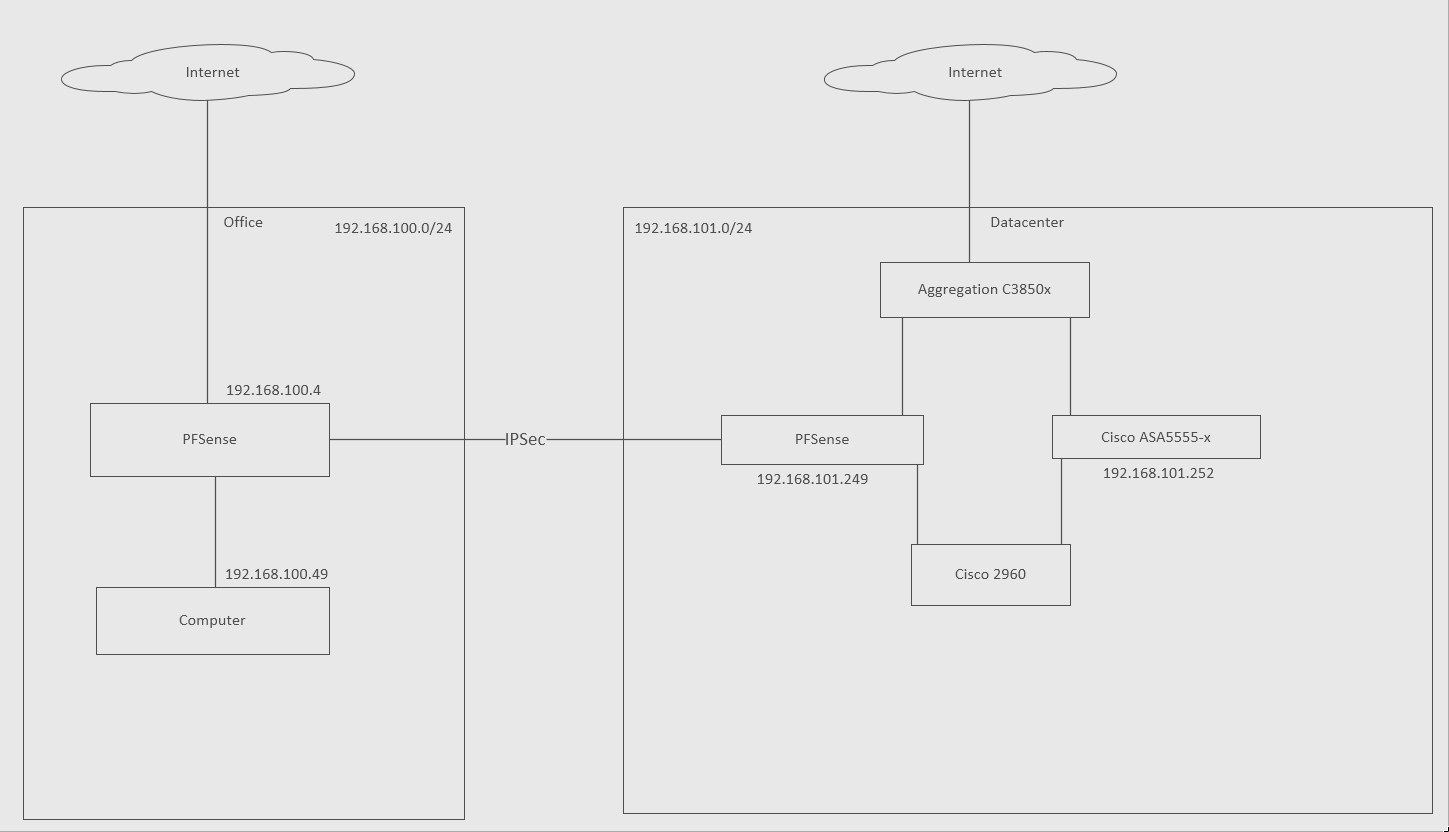
I have two networks, one office and one datacenter, with an IPSec connecting the two via PFSense on both sides. I have a Cisco ASA5555-x that I'm trying to access in the datacenter, about 3 weeks ago the datacenter PFSense(101.249) began blocking the return traffic(Source 101.252 to 100.49) on the IPSec interface, at the time I had a permit any any rule, at first it was all return traffic for port 443 which is the ASDM program to be used with the ASAs, which was annoying but I still had ssh access, so it wasn't something I stressed too much. As of Friday it began blocking all return traffic(Source 101.252 to 100.49) for port 22 after a minute or two of running ssh commands, so now I have very spotty remote access into it. I don't have a direct connection due to constraints on the available ports, so they're using a layer 2 vlan thats passing through a Cisco 2960. The protocol's on the 101.249 that its showing are "TCP:A" and "TCP:PA" This has worked consistently for about 2 years with no topology change, so I'm not sure why its suddenly starting to block these connections. I've tried specifying the two IPs in question with rules on the IPSec interface but its still blocking the return traffic. I've attached screenshots of the system logs from the PFSense doing the blocking showing whats happening, the rules I have on the interface that its referencing and a diagram depicting how the devices are connected to each other. I've had to so some scrubbing, but I tried to keep all of the information necessary for help with this issue intact.
-
fragmentation maybe?
did you try to set Firewall Optimization Options (under Advanced > Firewall/NAT) to conservative ?
packet capture / tcpdump/ wireshark would be helpful -
Yeah, I've changed it to conservative and even tried changing the state type on the two specific firewall rules to sloppy. I can do a packet capture on the .249 PFSense "IPSec" interface, but whats odd to me is that it traverses the LAN interface successfully and then blocks when it tries to leave the "IPSec" interface
-
Packet capture follows, just limited to traffic referencing 192.168.100.49 during an attempt to access port 22 and port 443
16:57:21.946095 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60425 > 192.168.101.252.22: tcp 0
16:57:21.946265 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.22 > 192.168.100.49.60425: tcp 0
16:57:22.952592 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60425 > 192.168.101.252.22: tcp 0
16:57:23.953929 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60425 > 192.168.101.252.22: tcp 0
16:57:24.959019 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60425 > 192.168.101.252.22: tcp 0
16:57:25.967803 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60425 > 192.168.101.252.22: tcp 0
16:57:26.972505 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60425 > 192.168.101.252.22: tcp 0
16:57:29.012658 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60425 > 192.168.101.252.22: tcp 0
16:57:33.098200 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60425 > 192.168.101.252.22: tcp 0
16:57:39.238429 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 0
16:57:39.238616 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 0
16:57:40.251019 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 0
16:57:40.251192 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 0
16:57:40.255340 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 0
16:57:40.317380 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 190
16:57:40.317529 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 0
16:57:40.318554 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 606
16:57:40.322681 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 0
16:57:40.349119 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 75
16:57:40.349947 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 0
16:57:40.361811 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 6
16:57:40.361926 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 0
16:57:40.389024 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 45
16:57:40.389147 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 0
16:57:40.389299 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 51
16:57:40.393282 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 0
16:57:40.399302 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 206
16:57:40.399415 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 0
16:57:40.399654 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 329
16:57:40.399686 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 0
16:57:40.403679 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 0
16:57:40.403694 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 0
16:57:40.405966 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 31
16:57:40.406049 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 0
16:57:40.407596 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60442 > 192.168.101.252.443: tcp 0
16:57:40.407710 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60442: tcp 0
16:57:40.414336 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 0
16:57:40.414488 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 0
16:57:41.243030 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60425 > 192.168.101.252.22: tcp 0
16:57:41.443831 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 0
16:57:41.443952 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 0
16:57:41.448196 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 0
16:57:41.452137 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 190
16:57:41.452254 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 0
16:57:41.453266 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 607
16:57:41.457303 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 0
16:57:41.462602 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 75
16:57:41.463420 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 0
16:57:41.467656 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 6
16:57:41.467773 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 0
16:57:41.467965 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 45
16:57:41.468087 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 0
16:57:41.468265 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 51
16:57:41.472209 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 0
16:57:41.473630 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 249
16:57:41.473744 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 0
16:57:41.474004 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 329
16:57:41.474031 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 0
16:57:41.478166 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 0
16:57:41.478180 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 0
16:57:41.478739 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 31
16:57:41.478750 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60444 > 192.168.101.252.443: tcp 0
16:57:41.478819 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 0
16:57:41.478889 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60444: tcp 0
16:57:41.479345 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 0
16:57:41.479478 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.508756 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 0
16:57:42.508924 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.512933 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 0
16:57:42.515433 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 190
16:57:42.515548 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.516567 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 606
16:57:42.520596 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 0
16:57:42.524682 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 75
16:57:42.525483 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.526753 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 6
16:57:42.526869 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.526885 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 45
16:57:42.527004 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.527179 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 51
16:57:42.531174 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 0
16:57:42.532588 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 275
16:57:42.532703 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.533025 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 352
16:57:42.537029 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 0
16:57:42.545859 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 327
16:57:42.545973 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.546235 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 216
16:57:42.550350 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 0
16:57:42.551611 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 288
16:57:42.551725 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.552100 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 1053
16:57:42.552150 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 153
16:57:42.556295 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 0
16:57:42.556308 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 0
16:57:42.694924 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 345
16:57:42.694942 (authentic,confidential): SPI 0xc47c23a9: IP 192.168.100.49.60446 > 192.168.101.252.443: tcp 110
16:57:42.695048 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.695088 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 0
16:57:42.721913 (authentic,confidential): SPI 0xc3d30395: IP 192.168.101.252.443 > 192.168.100.49.60446: tcp 1053 -
set "packet capture" to be more verbose, i think it's "level of details"
-
@kiokoman Couldn't set it to "verbose" in the "level of detail" best I could get was "Full"
14:36:59.265149 AF IPv4 (2), length 204: (tos 0x0, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 200)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0xa506 (correct), seq 464487249:464487409, ack 97171799, win 65535, length 160
14:36:59.265422 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 50352, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x632b (correct), seq 1, ack 160, win 32768, length 0
14:36:59.292169 AF IPv4 (2), length 92: (tos 0x0, ttl 254, id 33790, offset 0, flags [none], proto TCP (6), length 88)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x6891 (correct), seq 1:49, ack 160, win 32768, length 48
14:36:59.296238 AF IPv4 (2), length 44: (tos 0x0, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xe2fb (correct), seq 160, ack 49, win 65535, length 0
14:36:59.296536 AF IPv4 (2), length 124: (tos 0x0, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 120)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x8d4e (correct), seq 160:240, ack 49, win 65535, length 80
14:36:59.296642 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 53942, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x62ab (correct), seq 49, ack 240, win 32768, length 0
14:36:59.296697 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 35901, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x263b (correct), seq 49:113, ack 240, win 32768, length 64
14:36:59.300734 AF IPv4 (2), length 44: (tos 0x0, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xe26b (correct), seq 240, ack 113, win 65535, length 0
14:36:59.300932 AF IPv4 (2), length 540: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 536)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0xb35f (correct), seq 240:736, ack 113, win 65535, length 496
14:36:59.301045 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 60286, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x607b (correct), seq 113, ack 736, win 32768, length 0
14:36:59.301124 AF IPv4 (2), length 92: (tos 0x0, ttl 254, id 49017, offset 0, flags [none], proto TCP (6), length 88)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x41c0 (correct), seq 113:161, ack 736, win 32768, length 48
14:36:59.301174 AF IPv4 (2), length 92: (tos 0x0, ttl 254, id 45013, offset 0, flags [none], proto TCP (6), length 88)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x2378 (correct), seq 161:209, ack 736, win 32768, length 48
14:36:59.301541 AF IPv4 (2), length 156: (tos 0x0, ttl 254, id 37528, offset 0, flags [none], proto TCP (6), length 152)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x7c66 (correct), seq 209:321, ack 736, win 32768, length 112
14:36:59.301596 AF IPv4 (2), length 188: (tos 0x0, ttl 254, id 54921, offset 0, flags [none], proto TCP (6), length 184)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x8c8e (correct), seq 321:465, ack 736, win 32768, length 144
14:36:59.301670 AF IPv4 (2), length 204: (tos 0x0, ttl 254, id 56530, offset 0, flags [none], proto TCP (6), length 200)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x119d (correct), seq 465:625, ack 736, win 32768, length 160
14:36:59.305188 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xe04b (correct), seq 736, ack 161, win 65535, length 0
14:36:59.305202 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xe01b (correct), seq 736, ack 209, win 65535, length 0
14:36:59.305484 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xdfab (correct), seq 736, ack 321, win 65535, length 0
14:36:59.305496 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xdf1b (correct), seq 736, ack 465, win 65535, length 0
14:36:59.305513 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xde7b (correct), seq 736, ack 625, win 65535, length 0
14:36:59.328326 AF IPv4 (2), length 156: (tos 0x0, ttl 254, id 41931, offset 0, flags [none], proto TCP (6), length 152)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0xfc9d (correct), seq 625:737, ack 736, win 32768, length 112
14:36:59.328402 AF IPv4 (2), length 124: (tos 0x0, ttl 254, id 37833, offset 0, flags [none], proto TCP (6), length 120)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x8ec4 (correct), seq 737:817, ack 736, win 32768, length 80
14:36:59.332417 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xde0b (correct), seq 736, ack 737, win 65535, length 0
14:36:59.332429 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xddbb (correct), seq 736, ack 817, win 65535, length 0
14:37:00.321290 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0xc90f (correct), seq 736:800, ack 817, win 65535, length 64
14:37:00.321443 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 44579, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x5d7b (correct), seq 817, ack 800, win 32768, length 0
14:37:00.321523 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 37773, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x9193 (correct), seq 817:881, ack 800, win 32768, length 64
14:37:00.325711 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xdd3b (correct), seq 800, ack 881, win 65535, length 0
14:37:00.399119 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x9df0 (correct), seq 800:864, ack 881, win 65535, length 64
14:37:00.399235 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 54547, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x5cfb (correct), seq 881, ack 864, win 32768, length 0
14:37:00.399311 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 46984, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0xec45 (correct), seq 881:945, ack 864, win 32768, length 64
14:37:00.403361 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xdcbb (correct), seq 864, ack 945, win 65535, length 0
14:37:00.493570 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0xeee4 (correct), seq 864:928, ack 945, win 65535, length 64
14:37:00.493675 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 34495, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x5c7b (correct), seq 945, ack 928, win 32768, length 0
14:37:00.493732 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 51509, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x6364 (correct), seq 945:1009, ack 928, win 32768, length 64
14:37:00.497683 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xdc3b (correct), seq 928, ack 1009, win 65535, length 0
14:37:00.520289 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 57649, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x6219 (correct), seq 1009:1073, ack 928, win 32768, length 64
14:37:00.524513 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xdbfb (correct), seq 928, ack 1073, win 65535, length 0
14:37:01.618605 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x9668 (correct), seq 928:992, ack 1073, win 65535, length 64
14:37:01.618735 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 33214, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x5bbb (correct), seq 1073, ack 992, win 32768, length 0
14:37:01.618807 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 36649, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0xd406 (correct), seq 1073:1137, ack 992, win 32768, length 64
14:37:01.622863 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xdb7b (correct), seq 992, ack 1137, win 65535, length 0
14:37:01.916696 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x5174 (correct), seq 992:1056, ack 1137, win 65535, length 64
14:37:01.916814 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 47232, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x5b3b (correct), seq 1137, ack 1056, win 32768, length 0
14:37:01.916883 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 64694, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0xbbad (correct), seq 1137:1201, ack 1056, win 32768, length 64
14:37:01.920979 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xdafb (correct), seq 1056, ack 1201, win 65535, length 0
14:37:02.094039 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x29a1 (correct), seq 1056:1120, ack 1201, win 65535, length 64
14:37:02.094132 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 36541, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x5abb (correct), seq 1201, ack 1120, win 32768, length 0
14:37:02.094201 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 64433, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x78bd (correct), seq 1201:1265, ack 1120, win 32768, length 64
14:37:02.098222 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xda7b (correct), seq 1120, ack 1265, win 65535, length 0
14:37:02.235478 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0xf75b (correct), seq 1120:1184, ack 1265, win 65535, length 64
14:37:02.235617 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 57788, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x5a3b (correct), seq 1265, ack 1184, win 32768, length 0
14:37:02.235683 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 62526, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0xd7df (correct), seq 1265:1329, ack 1184, win 32768, length 64
14:37:02.239563 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd9fb (correct), seq 1184, ack 1329, win 65535, length 0
14:37:02.357594 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x4845 (correct), seq 1184:1248, ack 1329, win 65535, length 64
14:37:02.357716 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 35731, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x59bb (correct), seq 1329, ack 1248, win 32768, length 0
14:37:02.357767 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 49484, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x4a83 (correct), seq 1329:1393, ack 1248, win 32768, length 64
14:37:02.361771 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd97b (correct), seq 1248, ack 1393, win 65535, length 0
14:37:02.435869 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x16d7 (correct), seq 1248:1312, ack 1393, win 65535, length 64
14:37:02.435976 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 48335, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x593b (correct), seq 1393, ack 1312, win 32768, length 0
14:37:02.436038 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 45973, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x5a70 (correct), seq 1393:1457, ack 1312, win 32768, length 64
14:37:02.440091 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd8fb (correct), seq 1312, ack 1457, win 65535, length 0
14:37:02.682889 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x13d0 (correct), seq 1312:1376, ack 1457, win 65535, length 64
14:37:02.683003 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 48587, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x58bb (correct), seq 1457, ack 1376, win 32768, length 0
14:37:02.683070 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 59267, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x9528 (correct), seq 1457:1521, ack 1376, win 32768, length 64
14:37:02.687139 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd87b (correct), seq 1376, ack 1521, win 65535, length 0
14:37:02.822569 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0xefc6 (correct), seq 1376:1440, ack 1521, win 65535, length 64
14:37:02.822676 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 63851, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x583b (correct), seq 1521, ack 1440, win 32768, length 0
14:37:02.822737 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 50257, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0xb52c (correct), seq 1521:1585, ack 1440, win 32768, length 64
14:37:02.827012 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd7fb (correct), seq 1440, ack 1585, win 65535, length 0
14:37:02.969709 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0xa9c2 (correct), seq 1440:1504, ack 1585, win 65535, length 64
14:37:02.969826 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 53302, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x57bb (correct), seq 1585, ack 1504, win 32768, length 0
14:37:02.969872 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 47700, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x0d54 (correct), seq 1585:1649, ack 1504, win 32768, length 64
14:37:02.973872 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd77b (correct), seq 1504, ack 1649, win 65535, length 0
14:37:03.239520 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x5090 (correct), seq 1504:1568, ack 1649, win 65535, length 64
14:37:03.239637 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 54413, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x573b (correct), seq 1649, ack 1568, win 32768, length 0
14:37:03.239705 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 40140, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x7f2f (correct), seq 1649:1713, ack 1568, win 32768, length 64
14:37:03.243917 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd6fb (correct), seq 1568, ack 1713, win 65535, length 0
14:37:03.426647 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x7ec2 (correct), seq 1568:1632, ack 1713, win 65535, length 64
14:37:03.426759 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 39782, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x56bb (correct), seq 1713, ack 1632, win 32768, length 0
14:37:03.426860 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 58274, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x6a1f (correct), seq 1713:1777, ack 1632, win 32768, length 64
14:37:03.431042 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd67b (correct), seq 1632, ack 1777, win 65535, length 0
14:37:03.501564 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0x076a (correct), seq 1632:1696, ack 1777, win 65535, length 64
14:37:03.501666 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 56591, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x563b (correct), seq 1777, ack 1696, win 32768, length 0
14:37:03.501728 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 54021, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x64f6 (correct), seq 1777:1841, ack 1696, win 32768, length 64
14:37:03.505873 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd5fb (correct), seq 1696, ack 1841, win 65535, length 0
14:37:03.648296 AF IPv4 (2), length 108: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 104)
192.168.100.49.55017 > 192.168.101.252.22: Flags [P.], cksum 0xb73f (correct), seq 1696:1760, ack 1841, win 65535, length 64
14:37:03.648422 AF IPv4 (2), length 44: (tos 0x0, ttl 254, id 62111, offset 0, flags [none], proto TCP (6), length 40)
192.168.101.252.22 > 192.168.100.49.55017: Flags [.], cksum 0x55bb (correct), seq 1841, ack 1760, win 32768, length 0
14:37:03.648499 AF IPv4 (2), length 108: (tos 0x0, ttl 254, id 61725, offset 0, flags [none], proto TCP (6), length 104)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x5d2a (correct), seq 1841:1905, ack 1760, win 32768, length 64
14:37:03.652541 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd57b (correct), seq 1760, ack 1905, win 65535, length 0
14:37:03.675183 AF IPv4 (2), length 124: (tos 0x0, ttl 254, id 49149, offset 0, flags [none], proto TCP (6), length 120)
192.168.101.252.22 > 192.168.100.49.55017: Flags [P.], cksum 0x3fbe (correct), seq 1905:1985, ack 1760, win 32768, length 80
14:37:03.679289 AF IPv4 (2), length 44: (tos 0x10, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 40)
192.168.100.49.55017 > 192.168.101.252.22: Flags [.], cksum 0xd52b (correct), seq 1760, ack 1985, win 65535, length 0
14:39:01.558723 AF IPv4 (2), length 102: (tos 0x0, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 98)
192.168.100.49.55032 > 192.168.101.249.443: Flags [P.], cksum 0x915f (correct), seq 1717342412:1717342458, ack 4192580823, win 4096, options [nop,nop,TS val 2082755550 ecr 2475673005], length 46
14:39:01.558776 AF IPv4 (2), length 56: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.249.443 > 192.168.100.49.55032: Flags [.], cksum 0x4617 (correct), seq 1, ack 46, win 509, options [nop,nop,TS val 2475799912 ecr 2082755550], length 0
14:39:01.558811 AF IPv4 (2), length 87: (tos 0x0, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 83)
192.168.100.49.55032 > 192.168.101.249.443: Flags [P.], cksum 0x044d (correct), seq 46:77, ack 1, win 4096, options [nop,nop,TS val 2082755550 ecr 2475673005], length 31
14:39:01.558836 AF IPv4 (2), length 56: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.249.443 > 192.168.100.49.55032: Flags [.], cksum 0x45f8 (correct), seq 1, ack 77, win 509, options [nop,nop,TS val 2475799912 ecr 2082755550], length 0
14:39:01.558908 AF IPv4 (2), length 56: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.249.443 > 192.168.100.49.55032: Flags [F.], cksum 0x45f6 (correct), seq 1, ack 77, win 510, options [nop,nop,TS val 2475799912 ecr 2082755550], length 0
14:39:01.561306 AF IPv4 (2), length 56: (tos 0x0, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 52)
192.168.100.49.55032 > 192.168.101.249.443: Flags [F.], cksum 0x27af (correct), seq 77, ack 1, win 4096, options [nop,nop,TS val 2082755552 ecr 2475673005], length 0
14:39:01.561339 AF IPv4 (2), length 56: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
192.168.101.249.443 > 192.168.100.49.55032: Flags [F.], cksum 0x45f1 (correct), seq 1, ack 78, win 510, options [nop,nop,TS val 2475799914 ecr 2082755552], length 0
14:39:01.562679 AF IPv4 (2), length 56: (tos 0x0, ttl 62, id 0, offset 0, flags [DF], proto TCP (6), length 52)
192.168.100.49.55032 > 192.168.101.249.443: Flags [F.], cksum 0x37f0 (correct), seq 77, ack 2, win 4096, options [nop,nop,TS val 2082755553 ecr 2475799912], length 0 -
there is nothing/i don't see anything strange here, ..push and ack ..
the block on the firewall are there because they are out of state. idk .. maybe someone else have a better suggestion -
Yeah, that was what I was afraid of. I did some looking around to see if I saw the "TCP:PA" and TCP:A" with a root cause of anything but asynchronous routing, but thats all I could find. This sucks too, cause I had almost talked everyone into buying the equipment and support for PFSense and talked up how stable it was.
-
uhm based on this https://docs.netgate.com/pfsense/en/latest/firewall/troubleshooting-blocked-log-entries-for-legitimate-connection-packets.html
This happens because on occasion a packet will be lost, and the retransmits will be blocked because the firewall has already closed the connection.did you try MTU or MSS related settings?
-
No I've left both default, should I try increasing them? I thought we didn't see any fragmentation going on through the packet capture?
-
yeah right.. i'm also trying to keep the discussion active to see if someone else has any ideas ...
in this type of forum information is the key to a solution ... the more you test and report back the more information we have -
I've changed the MTU size to 1600 on the IPSec interface it was blocking on. It seems to have stopped blocking on that interface. I have everything set to 1500 MTU, and we saw no fragmentation, but it seems to be stable so far, been about 3 hours now.
-
is it still working?
...network's mistery? -
Yeah, its still working, about 23 hours so far stable. Still can't really explain why it happened. I didn't make any changes that would necessitate an MTU change. I was making acl changes on a machine farther into the network when it started happening.